Securing Your DevOps Pipelines - 2
Securing Your DevOps Pipelines
DevSecOps Tools
3.1 Learn about SAST
Static Application Security Testing
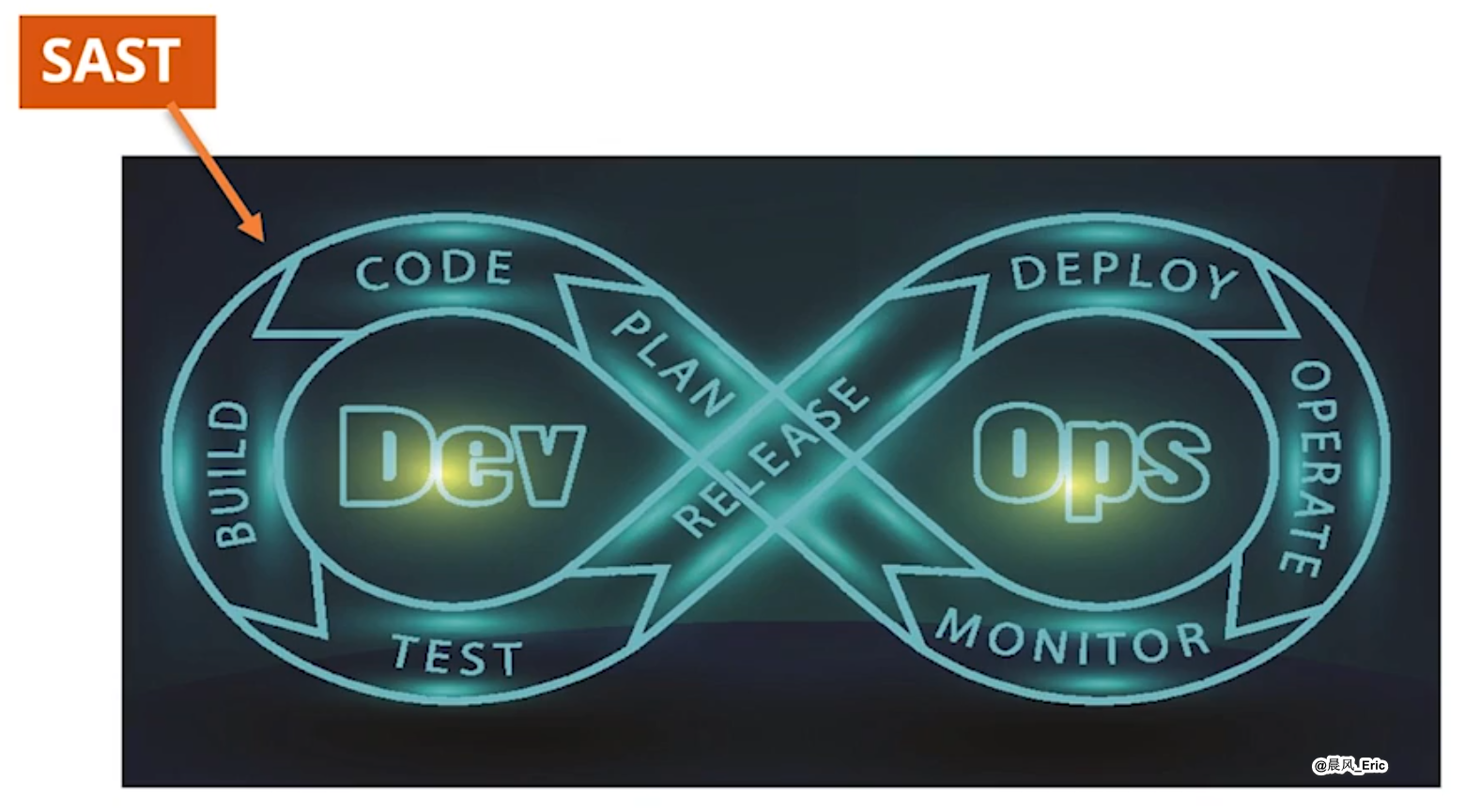
Also known as source code analysis.
The program doesn't have to be running.
Detect issues during software development.
Highlights bad code, by filename, location, line number.
White box testing method that lets you test before code runs.
SAST can used at any stage of the pipeline.
There are a number of questions you need to ask:
- How do I manage false positives?
- How do I triage the results?
- What happens to new issues come up?
- What do I do if the scan takes hours?
The first few test runs will throw a ton of errors.
Can't use this to test on staging or in production.
3.2 Use SAST tools
-
Horusec
-
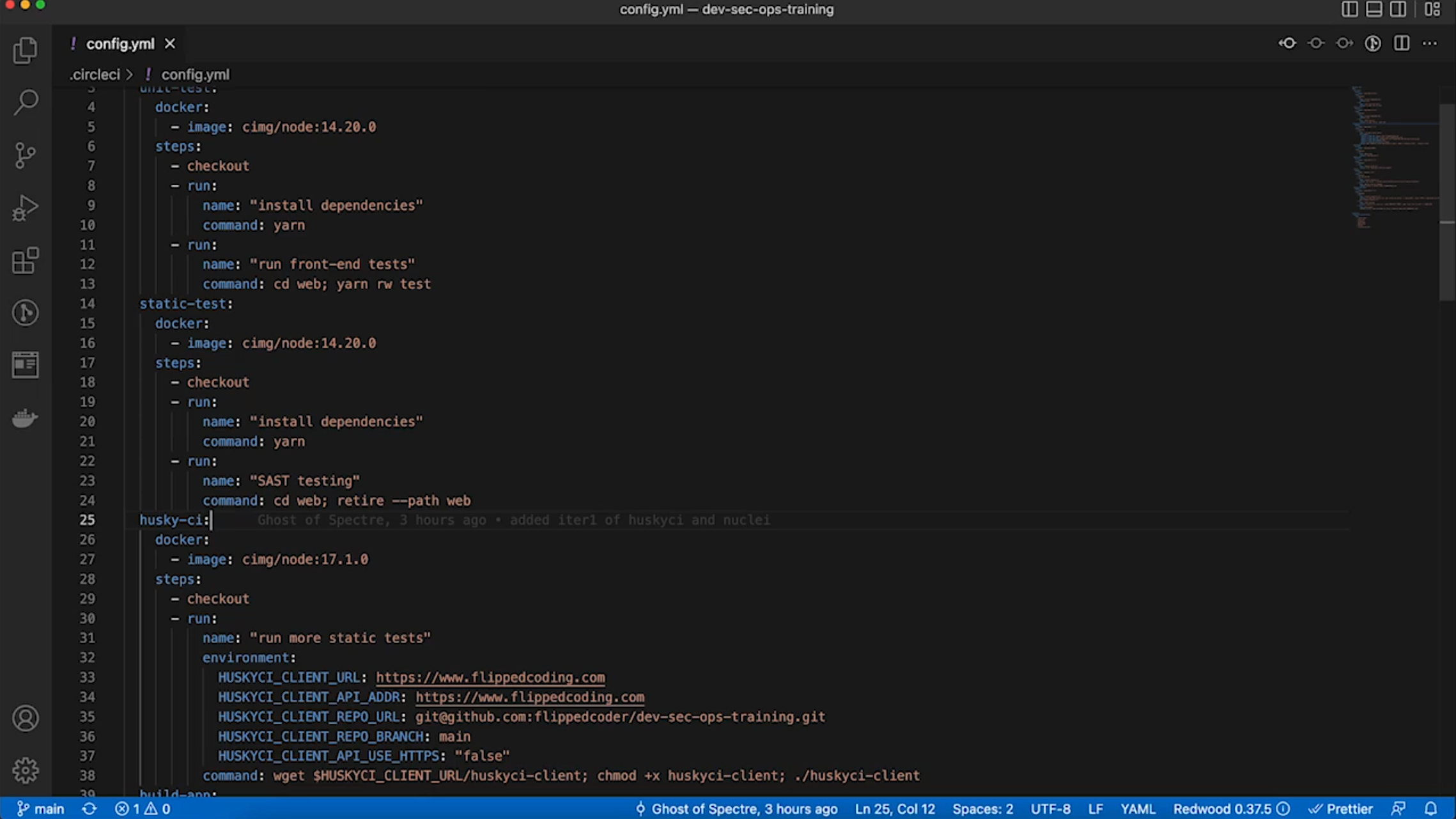
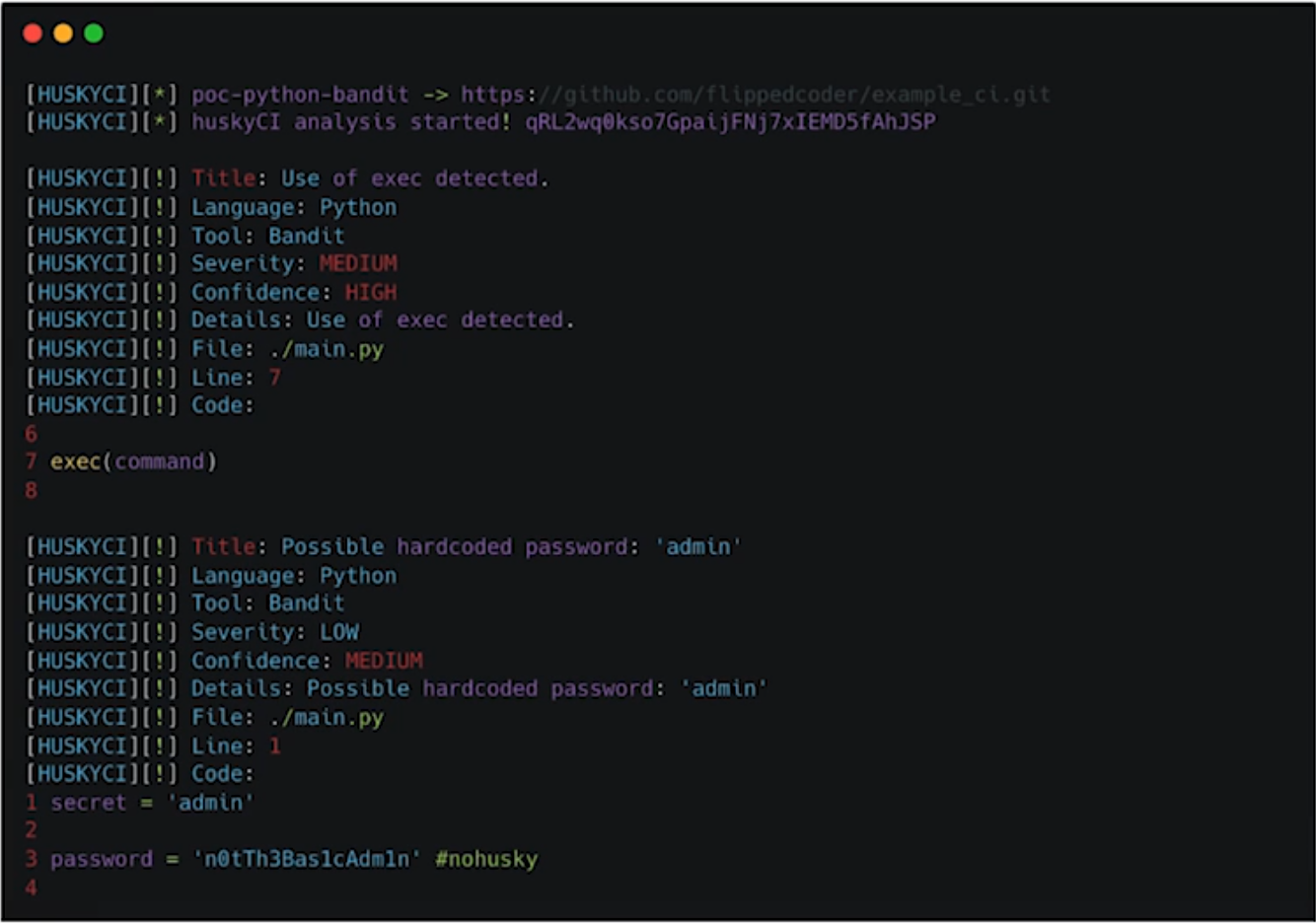
HuskyCI
![image-20251022180547560]()
-
Snyk
-
Semgrep
-
SonarCloud
-
Insider
-
LGTM
You need to set the rules for what the tools will check for
- Determine if dangerous APIs are in the code
- Scan config files for potential security credentials
- Check for different authentication patterns
- Look for all exposed routes
Example of SAST implementation with HuskyCI
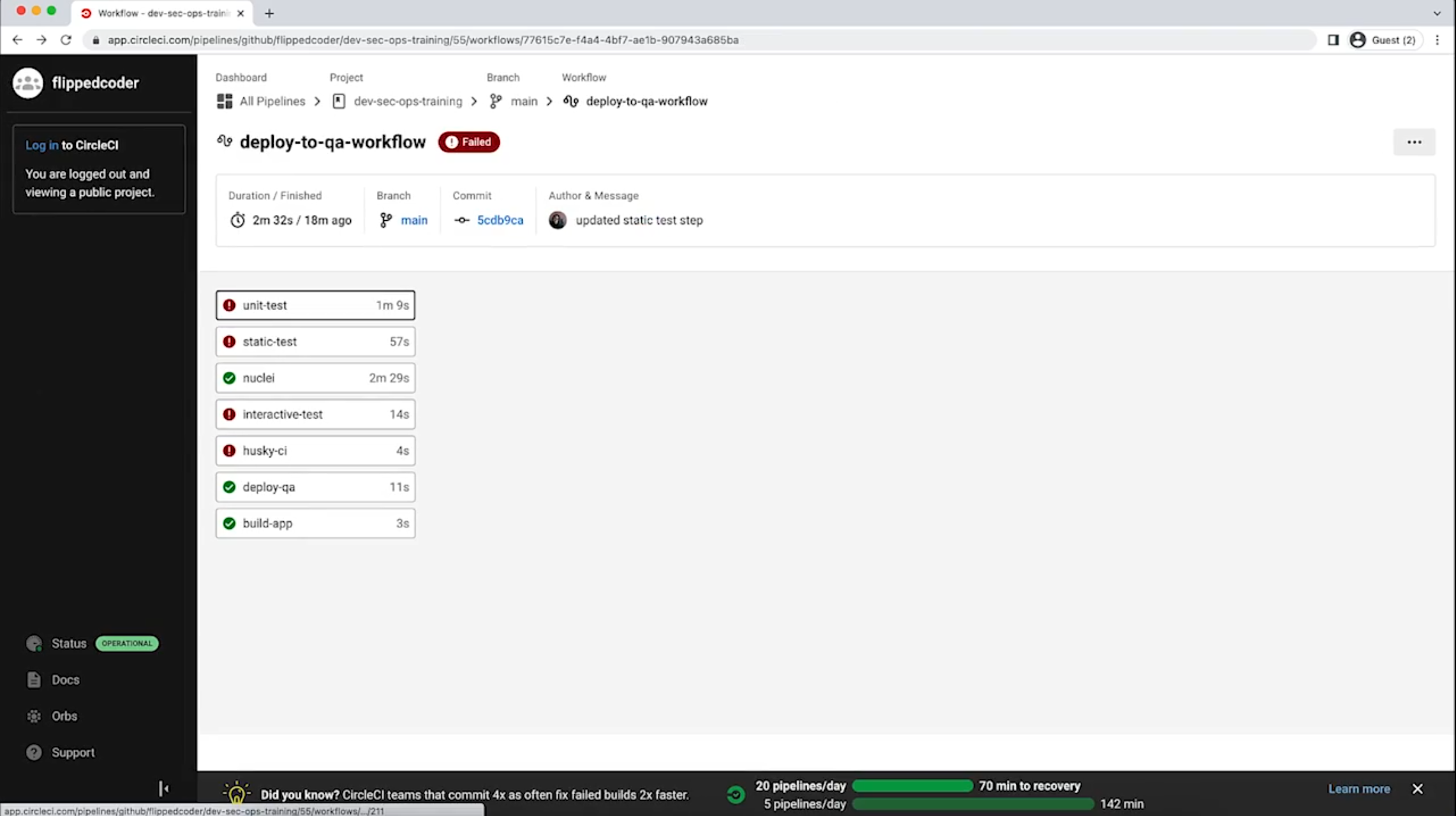
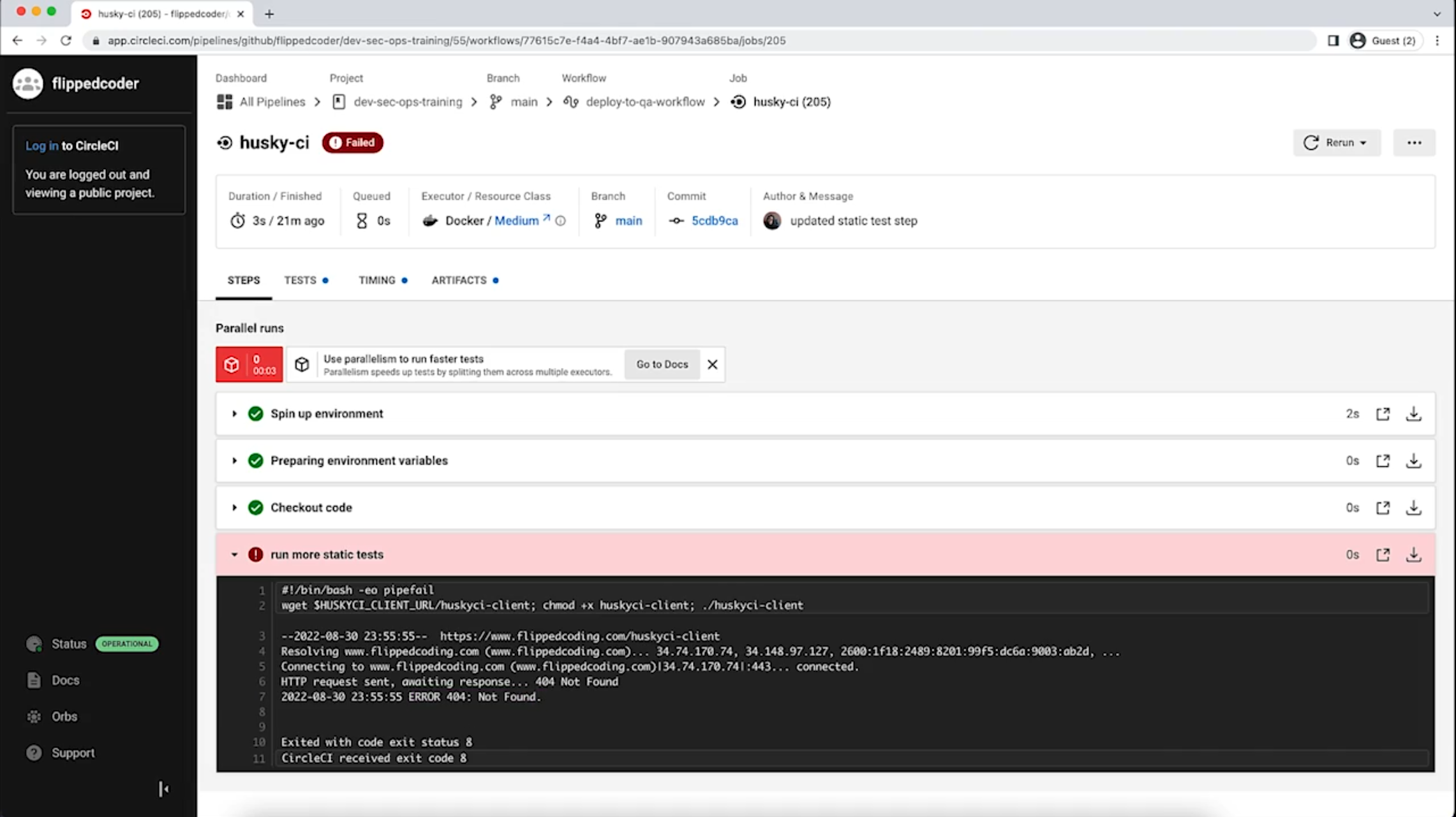
3.3 Learn about DAST

Black box testing method that lets you test code as it runs.
Applied on staging or in production.
Finds ways attackers could break into your system.
Tests all HTTP/HTTPS requests going into the application.
Find risks like cross-site scripting and SQL injections.
Commonly paired with a bug tracking system.
Running tests can take a long time.
Security experience is needed to understand the results.
It doesn't report where in the source code the issue is coming from.
Can be run in any environment that the app is in
3.4 Use DAST tools
- Veracode
- PortSwigger
- Burp Suite
- Tenable.io
- HCL AppScan
- Nuclei
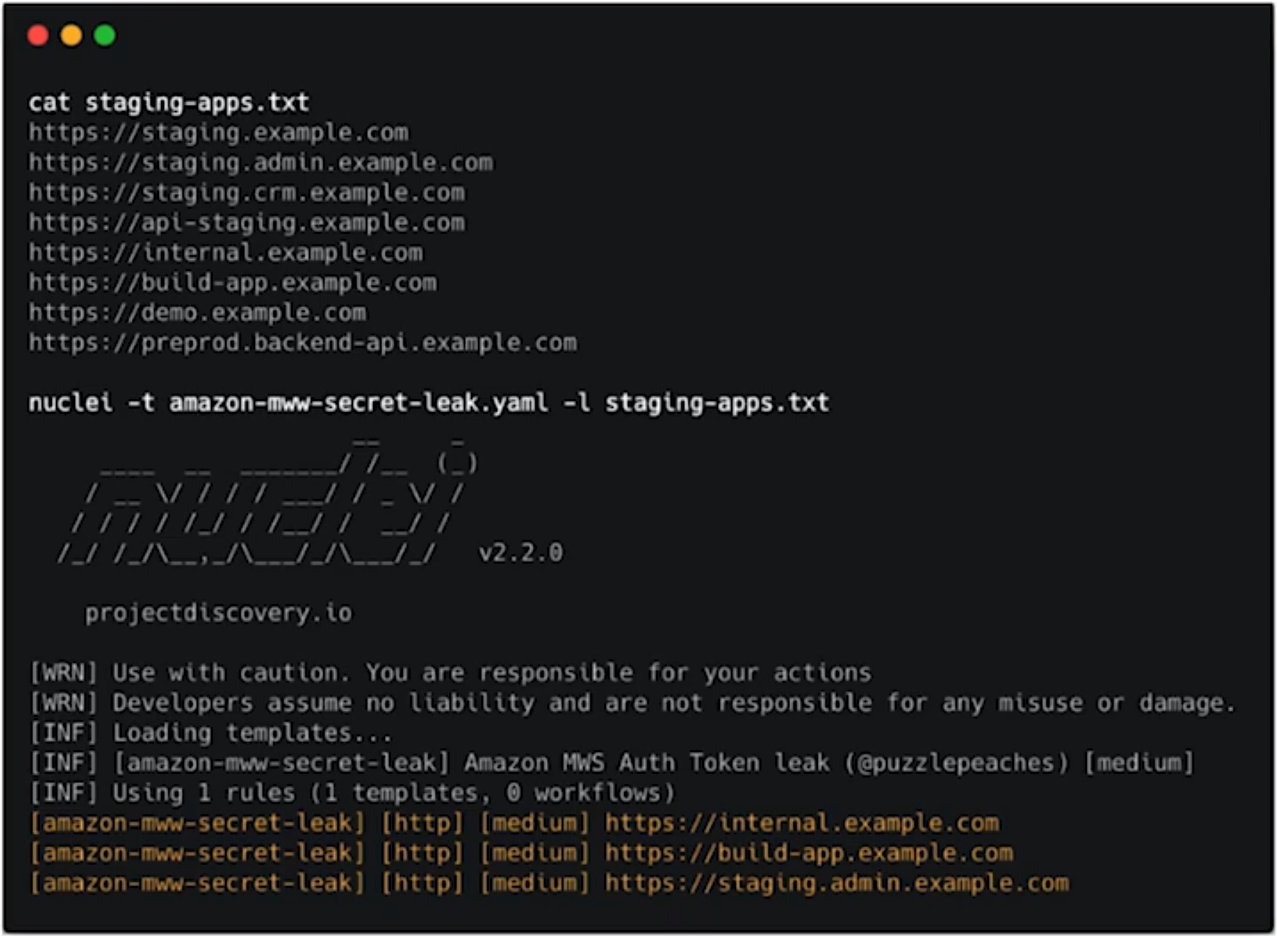
- OWASP ZAP
Example of DAST implementation with Nuclei
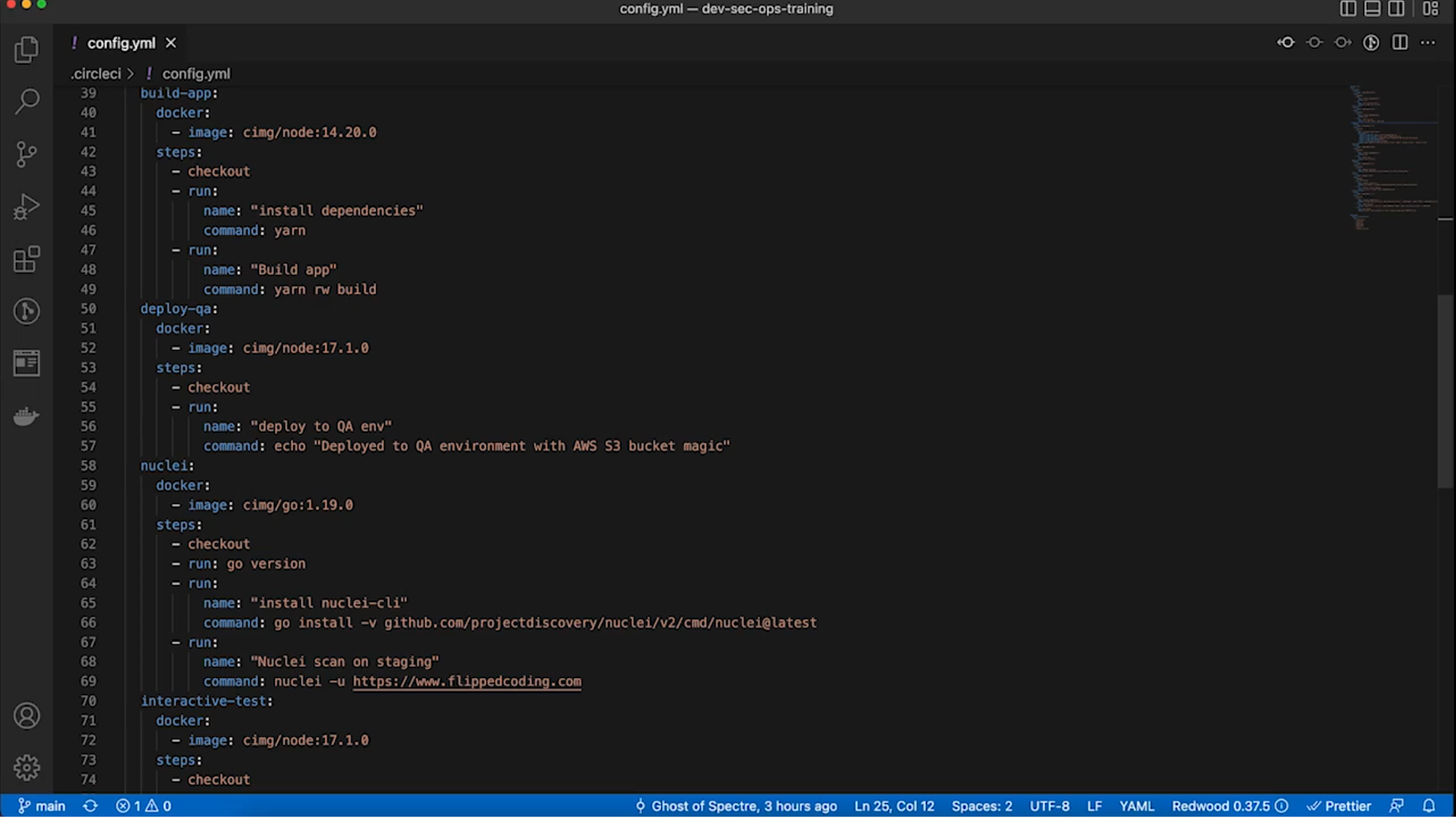
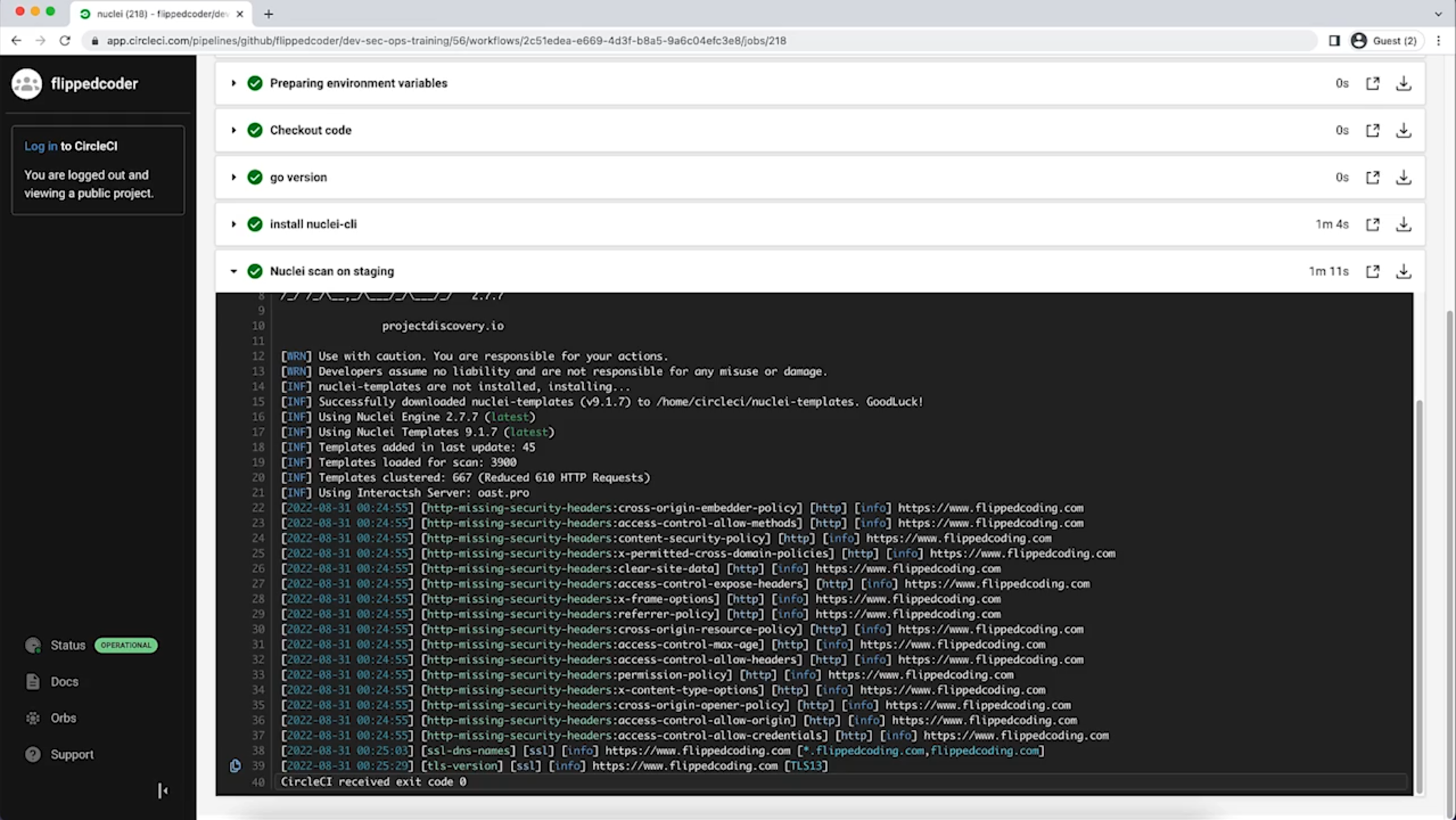
3.5 Learn about IAST
Interactive Application Security Testing

2 types of IAST
Passive
Passive IAST is like an extension of SAST.
Dynamic
Active IAST is like DAST in your code.
Operates as an gent inside the application.
Continually analyzes a running application.
Can slow down the operation of the application.
Analyzes the complied code, any requests, third party interactions.
Advantage over DAST by running in CI/CD
Great for API testing
Eliminates almost all false-positive results.
Only runs on the code you want it to.
3.6 Use IAST tools
- Veracode
- Acunetix
- Synopsys
- Snyk
- Hdiv Detection
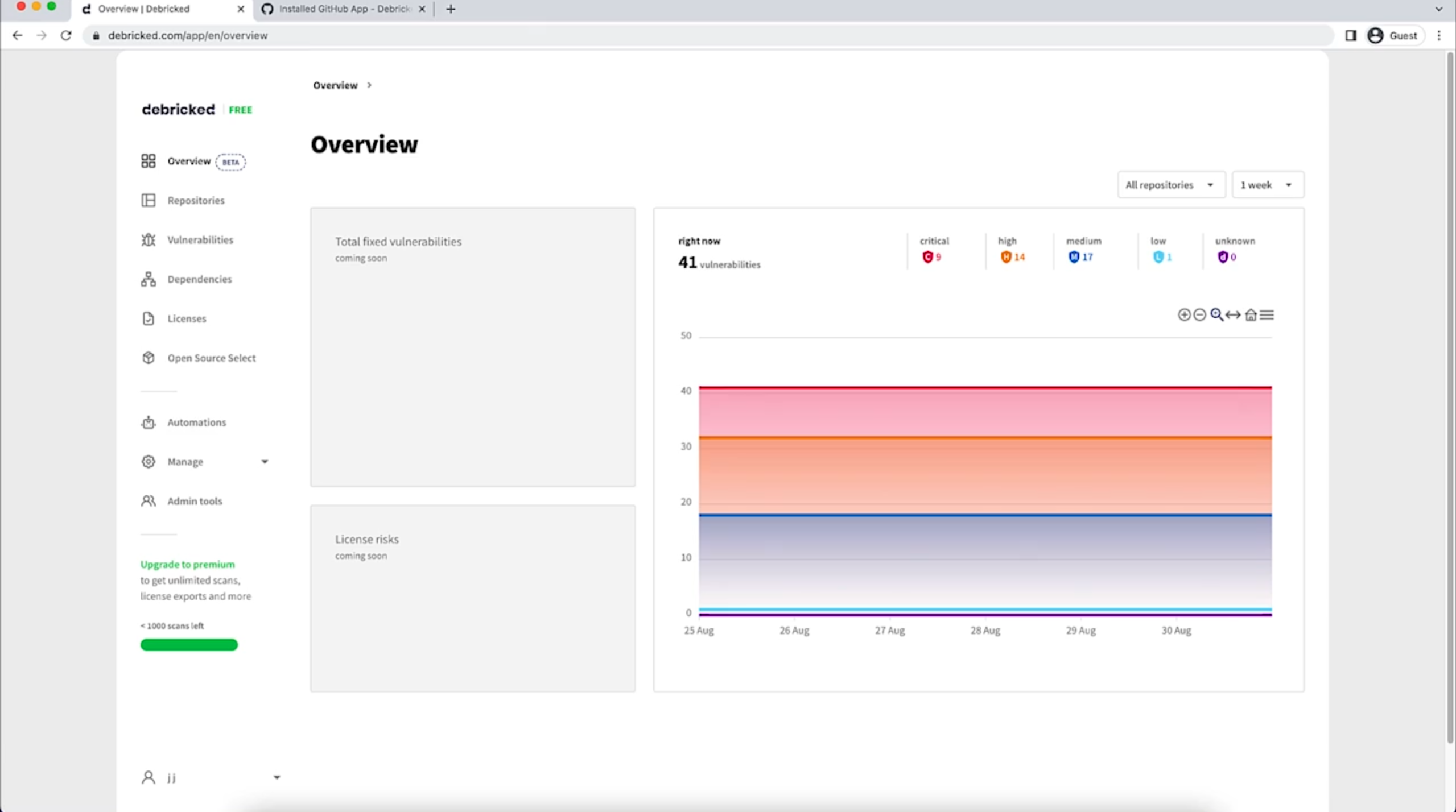
- Debricked
Best of both SAST and DAST
Example of IAST implementation with Debricked.
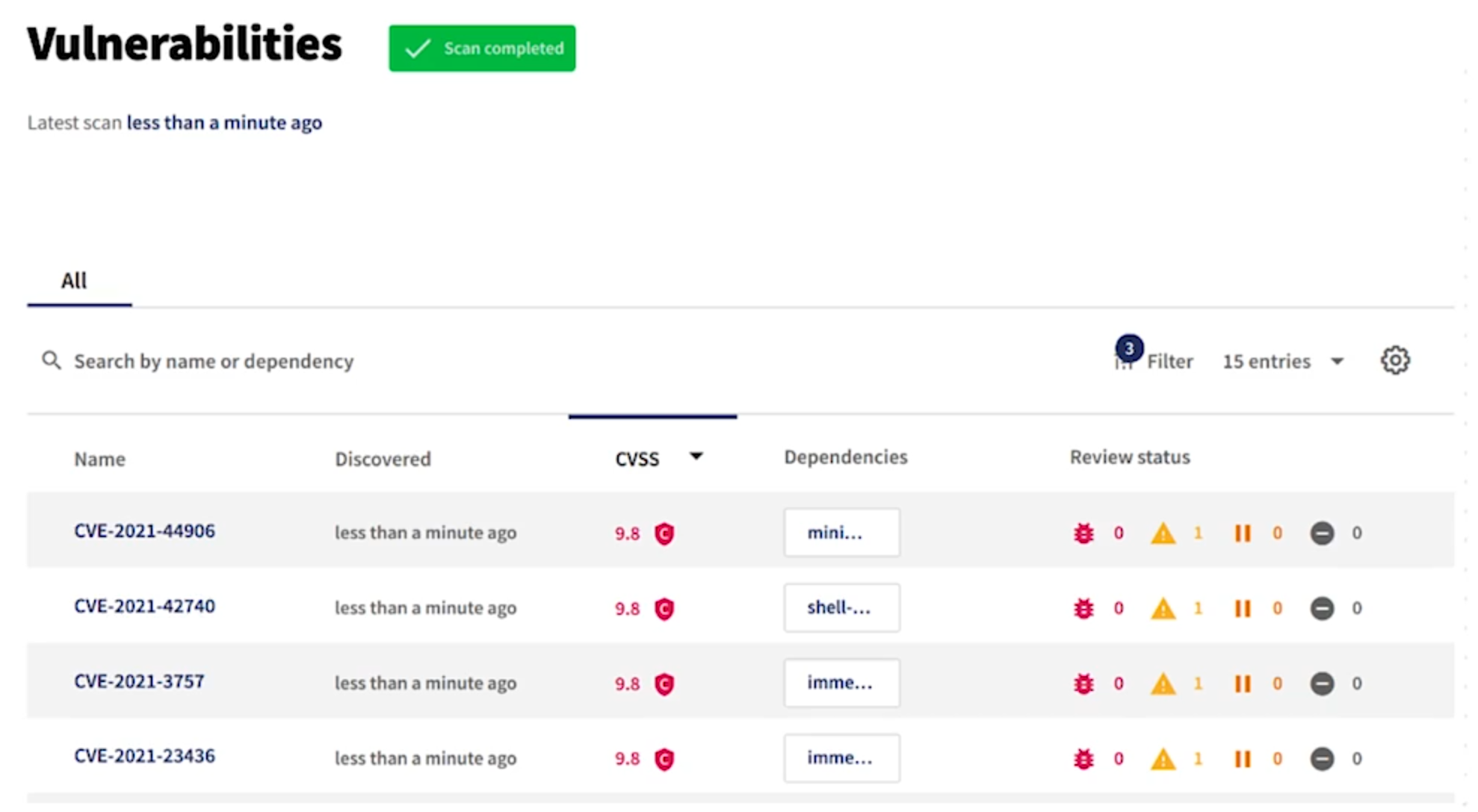
3.7 Learn about OAST
Expansion on top of DAST.
Vulnerabilities that can't be detected by regular HTTP request-response interaction.
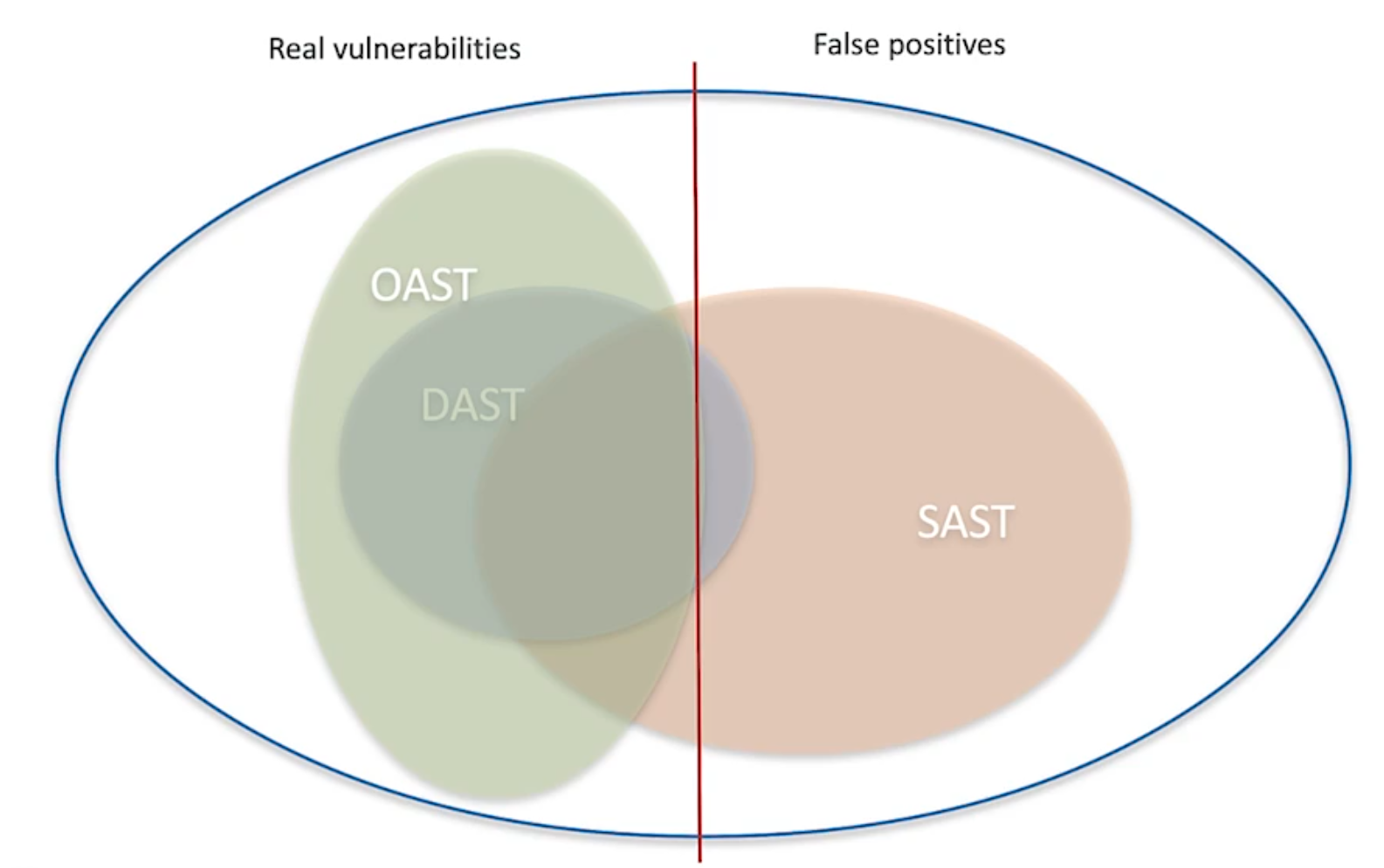
Improves on async responses.
Detects blind SQL injections, blind XSS attacks.
Response isn't returned directly to the request.
A different server handles the response.
Helps find security risks like the Log4j incident.
Injects data through an email and read through a web interface.
DNS is commonly used.
3.8 Use OAST tools
-
Portswigger
-
OWASP ZAP
Another layer on top of DAST.
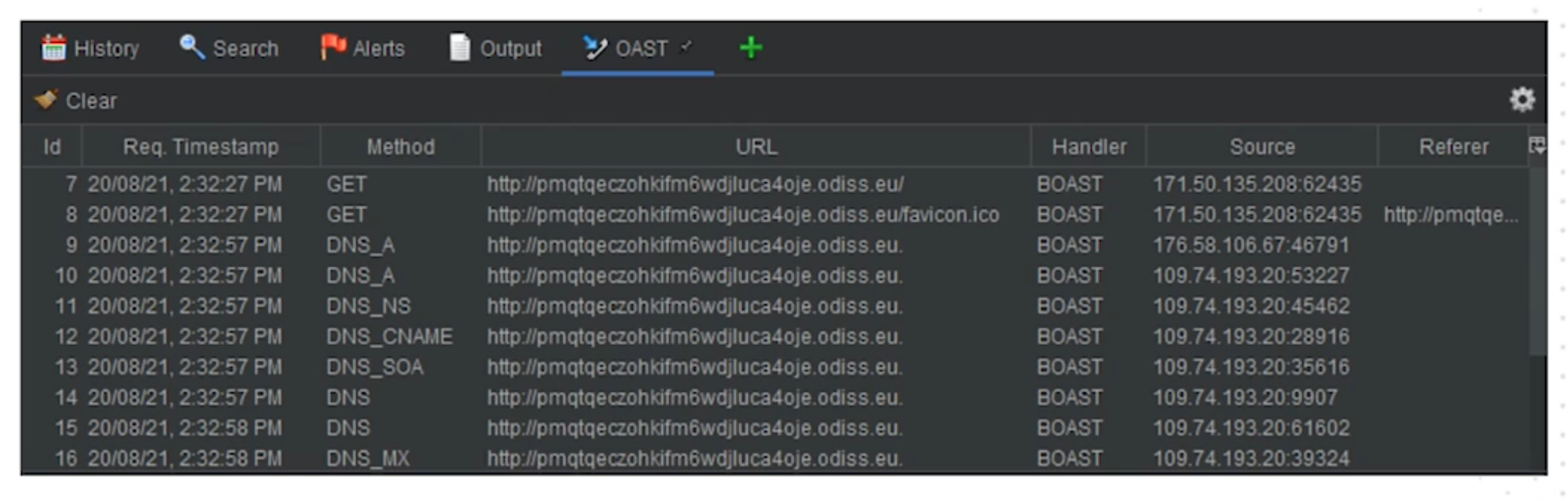
Example of OAST implementation with OWASP ZAP.
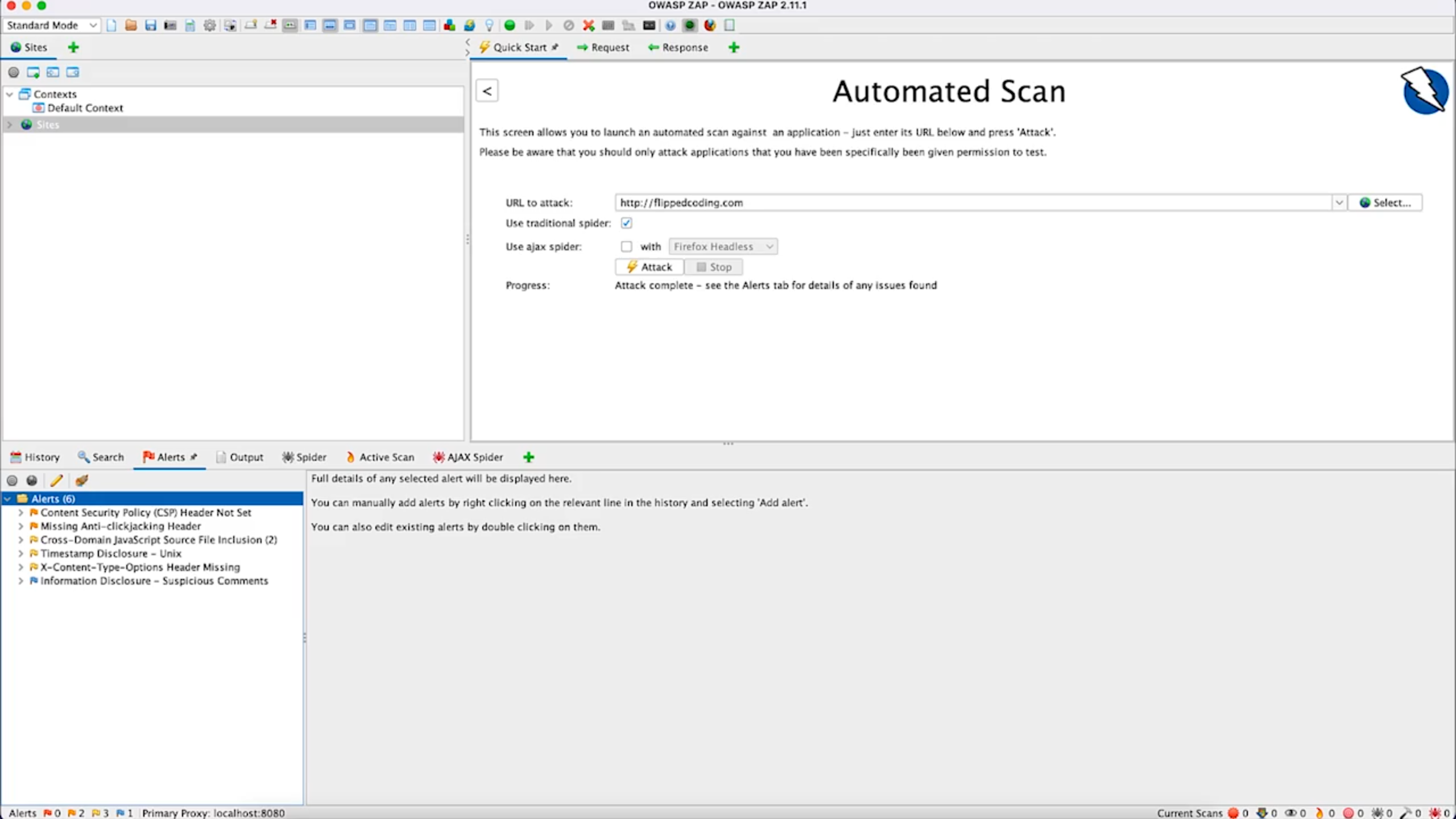
Setting up a DevSecOps Pipeline
4.1 Set up the project
Clone the repo
Install dependencies
yarn
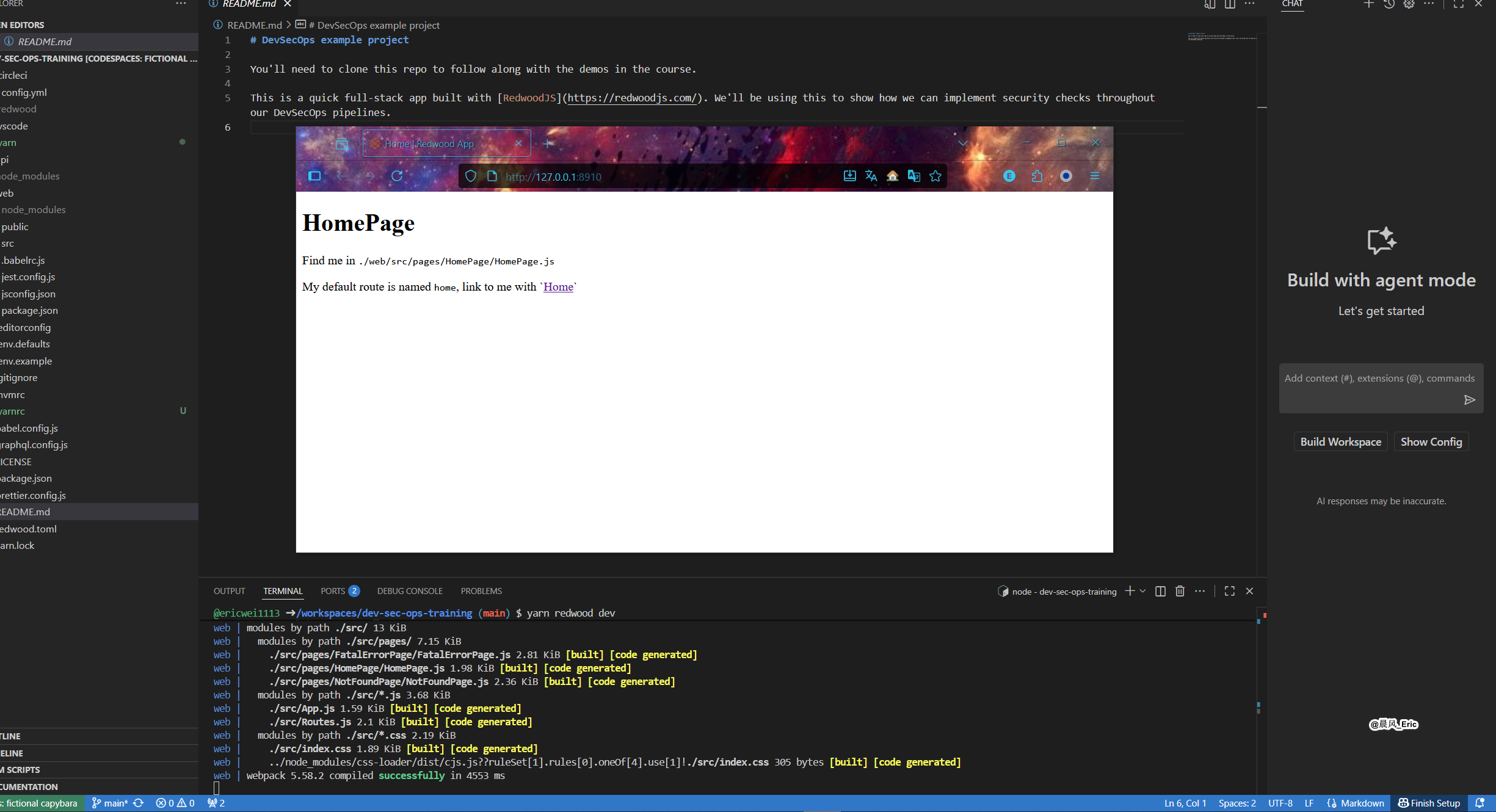
Run the app
yarn redwood dev
4.2 Set up CircleCI
Got to circleci.com
Connect with GitHub
Authorize repo
4.3 Write the CircleCI config
Go back to app
Add CircleCI yaml
4.4 Break down the pipeline steps
Walk through each part of the pipeline and run it
4.5 Add security to each step
Edit yaml file to have new security tests.
Walk through each security test and run.
The following config.yml is just for reference. Need adjustment for real CI/CD environment.
version: 2.1
jobs:
unit-tests:
docker:
- image: cimg/node:14.20.0
steps:
- checkout
- run:
name: "install dependencies"
command: yarn
- run:
name: "run project unit tests"
command: yarn redwood test
sast:
docker:
- image: cimg/node:14.20.0
steps:
- checkout
- run:
name: "install dependencies"
command: yarn
- run:
name: "execute retire.js"
command: cd web; retire --path web
build-app:
docker:
- image: cimg/node:14.20.0
steps:
- checkout
- run:
name: "install dependencies"
command: yarn
- run:
name: "build deploy artifact"
command: yarn redwood build
deploy-feature:
docker:
- image: cimg/node:17.1.0
steps:
- checkout
- run:
name: "deploy to feature env"
command: echo "Deployed to feature environment with AWS S3 bucket magic or Azure container magic"
dast:
docker:
- image: cimg/go:1.19.0
steps:
- checkout
- run: go version
- run:
name: "install nuclei-cli"
command: go install -v github.com/projectdiscovery/nuclei/v2/cmd/nuclei@latest
- run:
name: "Nuclei scan on QA"
command: nuclei -u https://flippedcoding.com
workflows:
deploy-to-qa:
jobs:
- unit-tests
- sast
- build-app
- deploy-feature
- dast
Final Security Checks
5.1 Learn how pen-testing works
An ethical hacker attempts to find any vulnerabilities.
External Network Penetration Testing
? Try to use public and private data gathered from leaked data breaches.
Internal Network Penetration Testing
? Someone pretending to be a staff member attempts a hack from the inside.
Application Penetration Testing
? Look for flaws in an application's security measure.
Social Engineering Testing
? See how susceptible employees are to exposing confidential information.
Stages of pen-testing
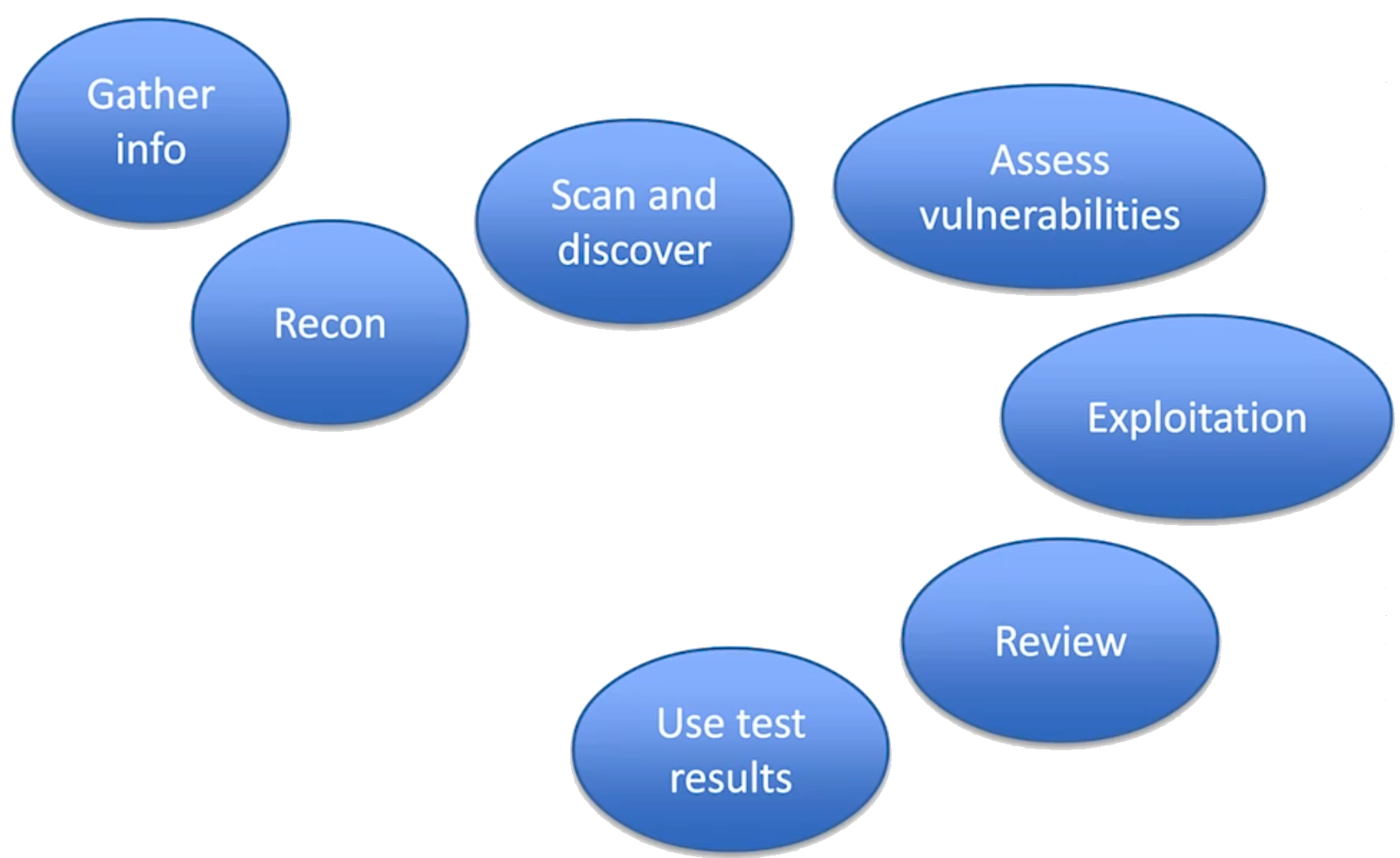
Gives feedback on how an app could be improved.
5.2 Use Kali Linux tools
Linux distro specifically made for ethical hacking.
Tools in Kali Linux: https://www.kali.org/tools/
-
WIRESHAEK
-
Burp Suite
-
SQLMAP
-
NIKTO
-
JOHN
5.3 Use bug bounties
A way to crowd-source your pen-testing.
Companies post challenges and offer a payout for successful reports.
Gives more realistic feedback on what attackers can do.
https://www.bugcrowd.com/bug-bounty-list/
https://www.hackerone.com/product/bug-bounty-platform
https://security.apple.com/bounty/
5.4 Perform compliance audits
Full review to see if an organization meets regulatory guidelines.
- HIPPA
Implement a means of access control.
Introduce activity logs and audit controls.
Implement tools for encryption and decryption.
Conducting regular risk assessments.
- PCI
Appropriate password protection.
Encryption of transmitted cardholder data.
Create and monitor access logs.
Implement firewalls to protect data.
- GDPR
Encrypt data wherever possible.
Customers can easily request and receive the data you have about them.
Customers can request to have all of their data deleted.
Conduct an audit to see who has access to your data.
Specialty tools exist for compliance audits in different industries.
Securing Your DevOps Pipelines Summary
- Background on DevOps
- Security in DevOps or DevSecOps
- DevSecOps Tools
- Setting up a DevSecOps Pipeline
- Final Security Checks



 浙公網安備 33010602011771號
浙公網安備 33010602011771號