SAP Role Matrix
SAP Role Matrix
Segregation of Duties can be represented over a role matrix. Role Matrix is a two dimensional matrix.
All the roles responsibilites and functions/processes in an enterprise are recognized and they are represented over each axis of matrix.
Then it is identified by putting a flag, across each set of roles/responsibilities and function/processes, over x and y - axis, whether they are conflicting or not.
Here is a sample role matrix. This role matrix has been identified for a set six processes and a set of six responsibilities, one for each process.
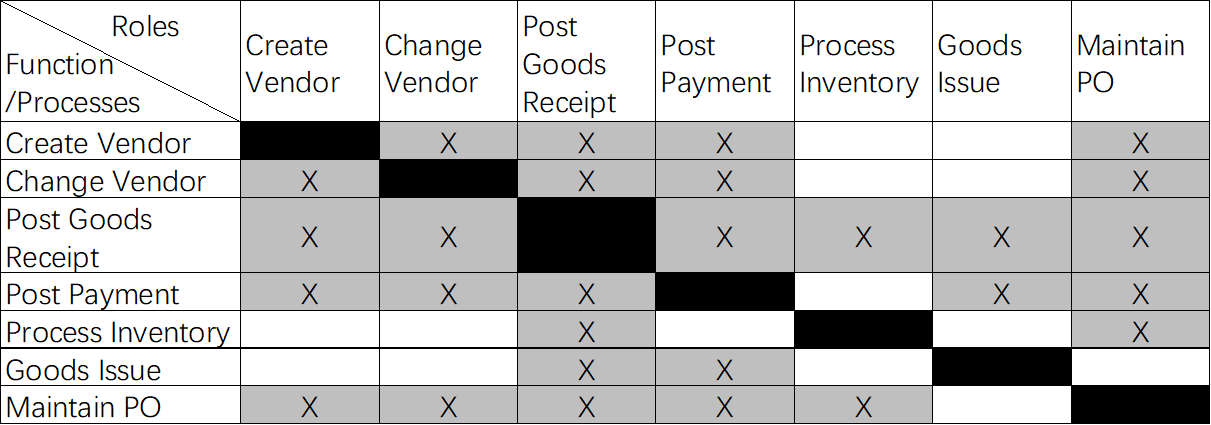
X-Exisktence of Conflict
SOX is an US Accounting law that deals with the financial accounting of the companies. In order to comply with SOX requirements, it is required that there should be well documented IT Processes. Over each of the IT Processes there should be well designed and documented internal controls and these controls should be well implemented and tracked and monitored. There should be effective controls over the key security and financial processes.
The SOX IT audit tries to identify that there are processes and controls in place and are being followed and tracked. In case of large and geographical organizations, it is not adequate for manual or paper-based processes and controls to be sufficient. There needs to be a proof that these processes are well followed and tracked.
In oder to comply with section 404 of SOX, we should:
- Identify and document processes and SoD controls across key IT Security and financial processes.
- Design mitigating controls and document then, where appropriate SoD cannot be implemented.
- Design monitoring controls for critical processes and critical roles.
- Implement SoD and mitigating controls
- Ensure continuous compliance by monitoring and tracking of controls.
SoD Implementation
For implementing SoD Controls across an enterprise, we need to do a heavy exercise. Therefore implementation SoD is done in form of a project. The implementation can be done by outlining the following steps as described below:
- Identify what is the objective of organizaion, hierarchy and nature of Organizaion, and job profiles in the organization, by doing an Organizaton scan.
- Identify the processes that are being followed in organization.
- Identify the current state of roles/responsibilities and authorization in the enterprise.
- Create the Role Matrix. Mark roles on one axis of Matrix and functions on other axis. Identify will there be any SoD conflict if role access to particular function is given to a single individual. Yes or No, flag the position in matrix accordingly, clearly.
- After analyzing the SoD conflict from role matrix, discuss with management and make the required changes in order to resolve SoD conflicts.
- In role matrix at position where SoD Conflicts cannot be resolved, designed the mitigating controls.
- According to findings in role matrix, generate the roles and mitigating controls within the enterprise system.
- Create a document that will well-define the changes required in a simple and organized manner.
- Document various roles, processes and mitigating controls for auditing and reporting.
- Inform and report the changes required to management and as well as to those affected, to make sure changes are implemented in well organized and smooth manner.
SoD is critical in helping managing risks. SoD issues and controls come up frequently when there are audits and reviews. SoD controls can be use as step to measure and resolve the risks associated with different roles and access to functions. To resolve he conflicts, we can design roles as per the business needs of various function/processes being executed in enterprise.



 浙公網安備 33010602011771號
浙公網安備 33010602011771號