1.檢查
查看定時任務文件發現有兩個異常定時任務
[root@manage ~]# cat /etc/crontab
# * * * * * user-name command to be executed
#*/1 * * * * root /etc/cron.hourly/ssh_deny.sh
#*/3 * * * * root /etc/cron.hourly/gcc4.sh
注釋掉定時任務
通過top命令查看會有隨機字符串的進程,殺掉進程后又會起來另外一個隨機字符串的進程,字符串長度10
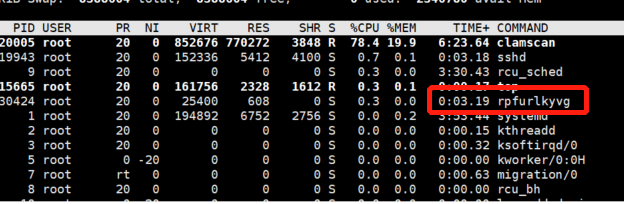
2.安裝clamav掃描并刪除感染文件
yum install -y epel-release
yum install clamav-server clamav-data clamav-update clamav-filesystem clamav clamav-scanner-systemd clamav-devel clamav-lib clamav-server-systemd -y
freshclam #更新數據庫
clamscan -r / --max-dir-recursion=5 -l /root/clamav.log #掃描目錄
rm -rf `cat clamav.log | grep FOUND | awk -F':' '{print $1}' ` # 刪除感染的文件
3.應用被破壞,刪除感染文件后重新安裝應用
yum -y reinstall procps lsof iproute net-tools psmisc
4.查看進程樹,紅色為之前殺掉進程后新生成的進程
[root@manage ~]# pstree
systemd─┬─.sshd───{.sshd}
├─qhhpivnzdw───3*[{qhhpivnzdw}]
├─rsyslogd───2*[{rsyslogd}]
├─sshd─┬─sshd───bash───pstree
│ └─sshd───bash
5.查找文件位置,進程號
[root@manage ~]# find / -name qhhpivnzdw
/etc/rc.d/init.d/qhhpivnzdw
/tmp/qhhpivnzdw
[root@manage ~]# pidof /tmp/qhhpivnzdw
7560
6.從定時任務中查看定時腳本內容,破壞病毒文件
[root@manage ~]# cat /etc/cron.hourly/gcc4.sh #路徑在定時任務文件中
#!/bin/sh
PATH=/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin:/usr/local/sbin:/usr/X11R6/bin
cp /lib/libudev4.so /lib/libudev4.so.6
/lib/libudev4.so.6
[root@manage ~]# echo aa> /lib/libudev4.so #破壞文件
[root@manage ~]# rm /lib/libudev4.so.6 #刪除拷貝文件
7.刪除開機啟動項
[root@manage ~]# chkconfig --list | grep on
Note: This output shows SysV services only and does not include native
systemd services. SysV configuration data might be overridden by native
systemd configuration.
If you want to list systemd services use 'systemctl list-unit-files'.
To see services enabled on particular target use
'systemctl list-dependencies [target]'.
gijhcyyfle 0:off 1:on 2:on 3:on 4:on 5:on 6:off
netconsole 0:off 1:off 2:off 3:off 4:off 5:off 6:off
network 0:off 1:off 2:on 3:on 4:on 5:on 6:off
qhhpivnzdw 0:off 1:on 2:on 3:on 4:on 5:on 6:off
tmsppnlzmg 0:off 1:on 2:on 3:on 4:on 5:on 6:off
vimzhvunzi (deleted) 0:off 1:on 2:on 3:on 4:on 5:on 6:off
[root@manage ~]# chkconfig --del gijhcyyfle
[root@manage ~]# chkconfig --del qhhpivnzdw
[root@manage ~]# chkconfig --del tmsppnlzmg
8.殺掉進程,這時候沒有其他隨機字符串進程起來了
[root@manage ~]# kill -9 7560



 浙公網安備 33010602011771號
浙公網安備 33010602011771號