在Ubuntu上使用Certbot申請Let’s Encrypt SSL證書
1 引言
要使用HTTPS就必須得有SSL證書。理論上,證書是可以通過像OpenSSL這樣得工具生成的。不過這種證書只能自己測試用,瀏覽器上面是不認的,會提示用戶不安全。也就是說,瀏覽器只接受一些特定的證書頒發機構(CA)發布的證書。正規的商業應用上,這些證書是需要像這些機構購買的。不過好在還是有像Let’s Encrypt這樣開放的證書頒發機構,可以免費向其申請SSL證書,不過缺點是證書有效期只能有90天。
2 詳敘
2.1 安裝
Certbot是一個免費、自動化、開源的工具,可以用于向Let’s Encrypt申請SSL證書。在Ubuntu下使用如下指令安裝Certbot:
sudo apt install certbot
如果提示不識別Certbot,那么可能需要添加Certbot的官方PPA源:
sudo apt install software-properties-common
sudo add-apt-repository universe
sudo add-apt-repository ppa:certbot/certbot
sudo apt update
另外,使用Snap也可以安裝Certbot:
sudo snap install --classic certbot
2.2 域名
一般來說,我們申請到的域名都是主域名,例如筆者申請的charlee44.com。除此之外,泛域名:*.charlee44.com也很常用。比如使用charlee44.com建了一個網站,隨著功能的擴充,你就有了建立子網站sub.charlee44.com的需求了。因此最好是讓主域名和泛域名合用同一個證書,以避免重復申請。
2.3 步驟
在終端中執行如下指令:
certbot certonly -d charlee44.com -d *.charlee44.com --manual --preferred-challenges dns
這個指令的意思是給charlee44.com和*.charlee44.com一起申請一個證書。此時會有如下提示:
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Requesting a certificate for charlee44.com and *.charlee44.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please deploy a DNS TXT record under the name:
_acme-challenge.charlee44.com.
with the following value:
xxxxxxxxxxxxxxxxxxxxxxxxxxxx
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Press Enter to Continue
這段命令提示的意思是將xxxxxxxxxxxxxxxxxxxxxxxxxxxx這段字符串設置成域名_acme-challenge.charlee44.com的TXT類型解析結果。這個步驟需要在域名服務商的后臺中進行配置。
點擊回車:
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please deploy a DNS TXT record under the name:
_acme-challenge.charlee44.com.
with the following value:
xxxxxxxxxxxxxxxxxxxxxxxxxxxx
(This must be set up in addition to the previous challenges; do not remove,
replace, or undo the previous challenge tasks yet. Note that you might be
asked to create multiple distinct TXT records with the same name. This is
permitted by DNS standards.)
Before continuing, verify the TXT record has been deployed. Depending on the DNS
provider, this may take some time, from a few seconds to multiple minutes. You can
check if it has finished deploying with aid of online tools, such as the Google
Admin Toolbox: https://toolbox.googleapps.com/apps/dig/#TXT/_acme-challenge.charlee44.com.
Look for one or more bolded line(s) below the line ';ANSWER'. It should show the
value(s) you've just added.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Press Enter to Continue
因為我們是給兩個域名生成證書,因此需要將之前的步驟再來一遍。注意,主域名和泛域名是將不同的xxxxxxxxxxxxxxxxxxxxxxxxxxxx字符串,設置成相同域名_acme-challenge.charlee44.com的TXT類型解析結果。在阿里云域名后臺中,就是給_acme-challenge.charlee44.com域名解析提供兩個結果,如下所示:
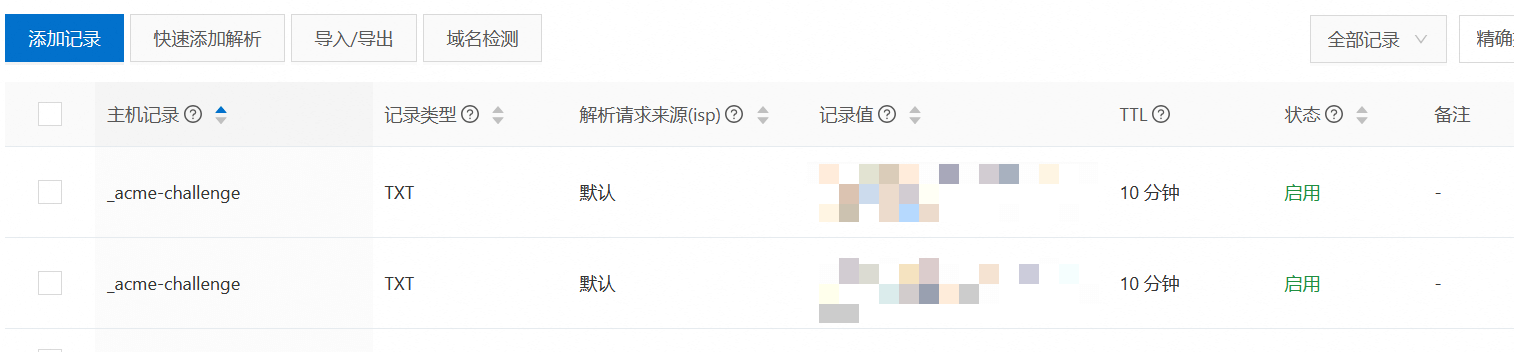
點擊回車:
Successfully received certificate.
Certificate is saved at: /etc/letsencrypt/live/charlee44.com-0001/fullchain.pem
Key is saved at: /etc/letsencrypt/live/charlee44.com-0001/privkey.pem
This certificate expires on 2025-09-29.
These files will be updated when the certificate renews.
NEXT STEPS:
- This certificate will not be renewed automatically. Autorenewal of --manual certificates requires the use of an authentication hook script (--manual-auth-hook) but one was not provided. To renew this certificate, repeat this same certbot command before the certificate's expiry date.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
If you like Certbot, please consider supporting our work by:
* Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
* Donating to EFF: https://eff.org/donate-le
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
可以看到生成了兩個SSL證書文件:
- /etc/letsencrypt/live/charlee44.com-0001/fullchain.pem:服務器需要發送給客戶端的完整證書鏈。
- /etc/letsencrypt/live/charlee44.com-0001/privkey.pem:證書私鑰,與證書一起使用,以證明擁有該證書對應的公鑰。
一般的HTTPS使用這兩個證書文件即可。



 浙公網安備 33010602011771號
浙公網安備 33010602011771號