根證書的普通用途
根證明普通的情況用途為對標志和發行傳遞的證明,再標志和問題終端證明由傳遞的證明(服務器,客戶端)。
自建根證書步驟
在自建根證書之前需要安裝openssl
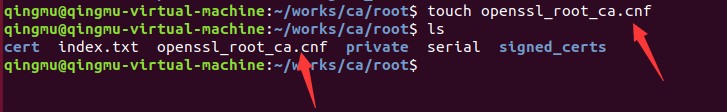
sudo apt-get install openssl1、創建一個目錄,存放所有證書有關資料
ca的路徑可自選,并在ca路徑下創建root文件夾,用來存放根證書
命令:
mkdir ca
mkdir ca/root創建ca文件夾,存放所有有關文件
創建root文件夾存放根證書

2、進入根證書目錄,創建相關目錄和檔案
2.1、進入根證書目錄
cd ca/root2.2、創建相關目錄
- private :存放根證書的私鑰
- cert :存放根證書
- signed_certs :放置的根證明簽了字和被發布的證明副本。
mkdir private cert signed_certs
2.3、更改private目錄存取權限
chmod 700 private
2.4、創建index.txt文件
每次簽署和發行證明OpenSSL的根證明可能自動地更新這個文件建立index.txt,這個文件能為紀錄使用根證明簽署和發布證明紀錄。(具體沒什么用,但必須要有)
touch index.txt
2.5、建立serial
建立serial,并在文件中填入0001,被簽發的證書都會有序號和位置,記錄這份證明在早先簽署的和發布的單位簽字并且發布的證明號碼,這個文件能使用為記錄簽署和發布證明號碼的根證明,每次簽署和發行證明OpenSSL的根證明可能自動地更新這個文件。(具體沒什么用,但必須要有)
echo 0001 > serial

3、填寫OpenSSL
填寫OpenSSL的配置文件,文件名是openssl_root_ca.cnf,并放置在root目錄下
填充內容
使用vim打開,然后復制進去即可
[ ca ]
default_ca = CA_default
[ CA_default ]
# 放置相關的文件和目錄.
dir = /home/qingmu/works/ca/root
certs = $dir/cert
new_certs_dir = $dir/signed_certs
database = $dir/index.txt
serial = $dir/serial
RANDFILE = $dir/private/.rand
# 放置私鑰和證書的路徑.
private_key = $dir/private/root_ca.key.pem
certificate = $dir/cert/root_ca.cert.pem
default_md = sha256
name_opt = ca_default
cert_opt = ca_default
default_days = 365
preserve = no
policy = policy_defualt
[ policy_defualt ]
# 簽發證書文件資料的檢查 (和根證書必須一樣).
countryName = optional
stateOrProvinceName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ req ]
# req 工具需要的參數.
default_bits = 2048
distinguished_name = req_distinguished_name
string_mask = utf8only
default_md = sha256
[ req_distinguished_name ]
# 生成證書是要輸入的一些說明信息
countryName = Country Name (2 letter code)
stateOrProvinceName = State or Province Name
localityName = Locality Name
0.organizationName = Organization Name
organizationalUnitName = Organizational Unit Name
commonName = Common Name
emailAddress = Email Address
[ root_ca ]
# 簽發根證書時使用
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always,issuer
basicConstraints = critical, CA:true
keyUsage = critical, digitalSignature, cRLSign, keyCertSign
[ intermediate_ca ]
# 簽發和發布時使用
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always,issuer
basicConstraints = critical, CA:true, pathlen:0
keyUsage = critical, digitalSignature, cRLSign, keyCertSign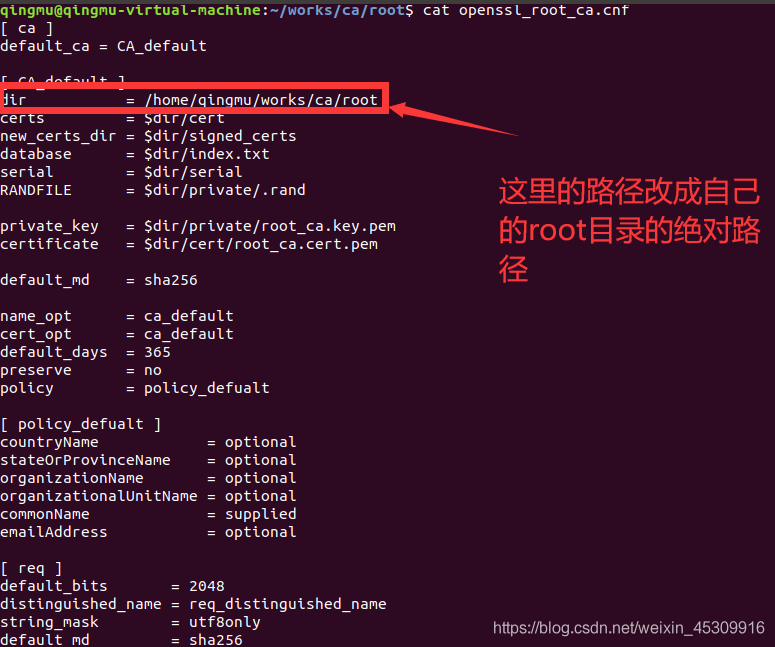
4、生成私鑰
在private目錄下生成私鑰, 文件名時 root_ca.key.pem
openssl genrsa -aes256 -out private/root_ca.key.pem 4096提示輸入信息:
會提示輸入私鑰使用的密碼,例如:alice123
(密碼不會顯示)
Enter pass phrase for private/root_ca.key.pem:alice123
再次輸入密碼:
Verifying - Enter pass phrase for private/root_ca.key.pem:alice123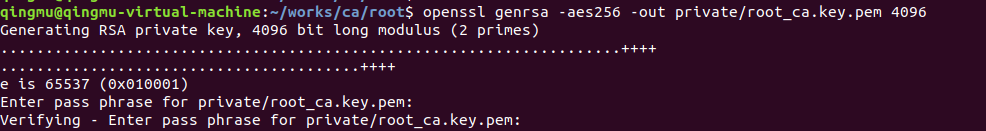
5.用私鑰來簽發證書
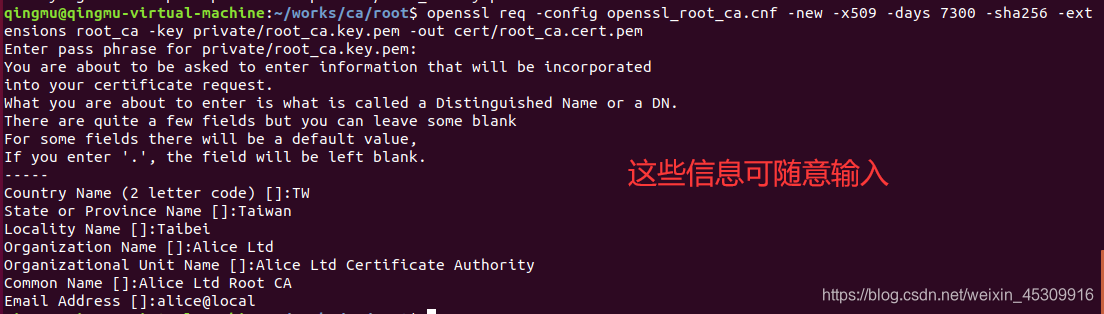
文件名是root_ca.cert.pem
openssl req -config openssl_root_ca.cnf -new -x509 -days 7300 -sha256 -extensions root_ca -key private/root_ca.key.pem -out cert/root_ca.cert.pem會提示輸入一些信息:
# 會提示輸入根證書的私鑰密碼, 也就是 alice123
Enter pass phrase for private/root_ca.key.pem:alice123
# 接著需要輸入根證書擁有者的信息.
You are about to be asked to enter information that will be incorporated into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
# 所在國家的縮寫, 2 個字母, 例如 Taiwan = TW, Unit State = US.
Country Name (2 letter code) []:TW
# 所在的州或省.
State or Province Name []:Taiwan
# 所在的城市.
Locality Name []:Taipei
# 所在的公司.
Organization Name []:Alice Ltd
# 所在的公司的單位.
Organizational Unit Name []:Alice Ltd Certificate Authority
# 證書名稱
Common Name []:Alice Ltd Root CA
# 郵箱.
Email Address []:alice@local- 1
把證書的權限改為只讀權限
chmod 444 cert/root_ca.cert.pem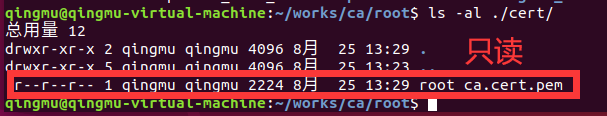
6、檢查生成的根證書是否正確
openssl x509 -noout -text -in cert/root_ca.cert.pem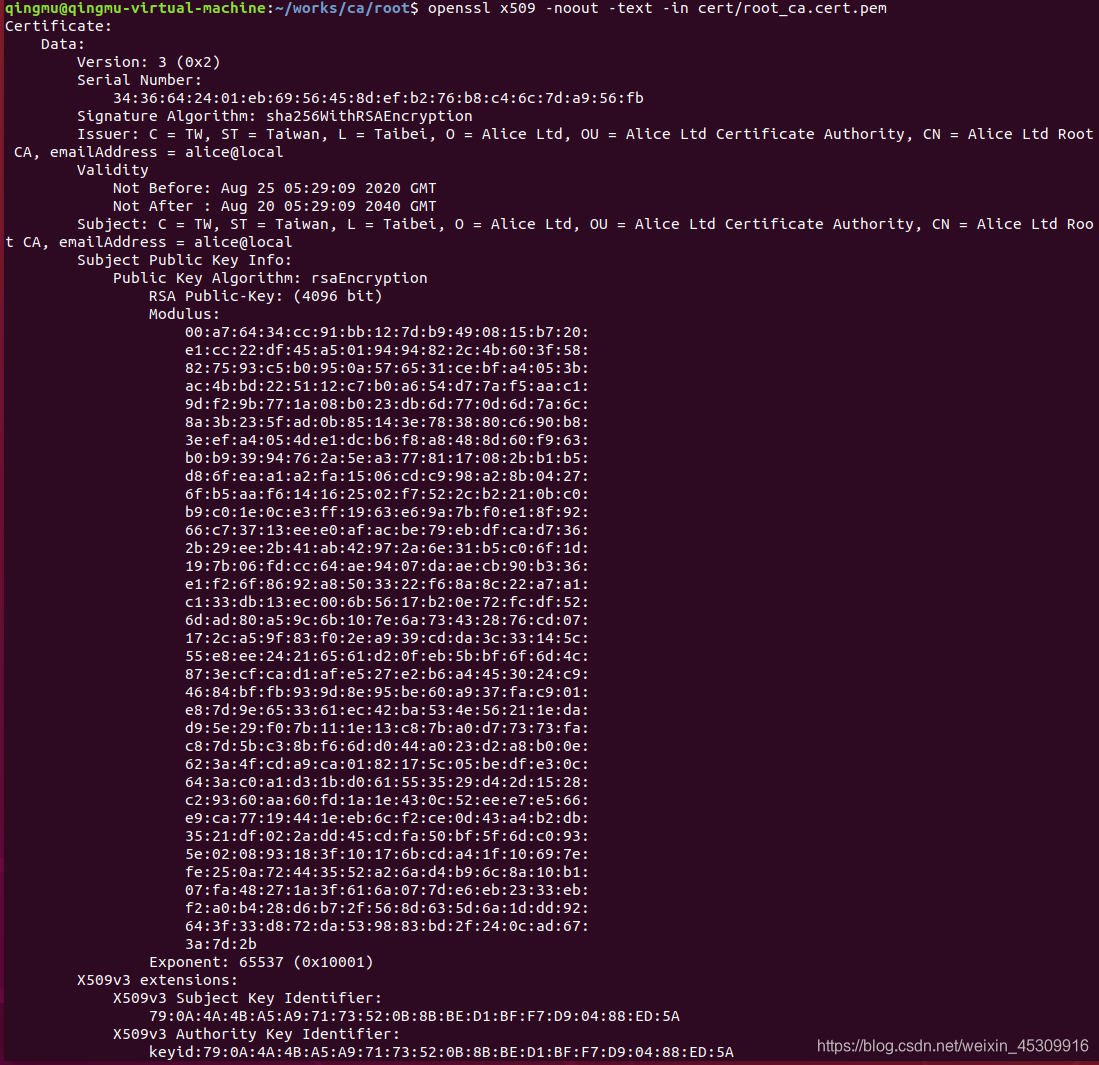




 浙公網安備 33010602011771號
浙公網安備 33010602011771號