20231302邱之釗密碼系統(tǒng)設(shè)計(jì)實(shí)驗(yàn)一第一
1.參考云班課相關(guān)教學(xué)視頻,在Ubuntu或openEuler中(推薦openEuler)中實(shí)踐課程思維導(dǎo)圖中OpenSSL相關(guān)內(nèi)容,使用Markdown記錄詳細(xì)記錄實(shí)踐過程,每完成一項(xiàng)gitcommit一次。(5分)
qzz@qzz-virtual-machine:~/command_history_repo$ openssl version
OpenSSL 3.0.2 15 Mar 2022 (Library: OpenSSL 3.0.2 15 Mar 2022)
qzz@qzz-virtual-machine:~/command_history_repo$ openssl list -help
Usage: list [options]
General options:
-help Display this summary
Output options:
-1 List in one column
-verbose Verbose listing
-select val Select a single algorithm
-commands List of standard commands
-standard-commands List of standard commands
-digest-commands List of message digest commands (deprecated)
-digest-algorithms List of message digest algorithms
-kdf-algorithms List of key derivation and pseudo random function algorithms
-random-instances List the primary, public and private random number generator details
-random-generators List of random number generators
-mac-algorithms List of message authentication code algorithms
-cipher-commands List of cipher commands (deprecated)
-cipher-algorithms List of cipher algorithms
-encoders List of encoding methods
-decoders List of decoding methods
-key-managers List of key managers
-key-exchange-algorithms List of key exchange algorithms
-kem-algorithms List of key encapsulation mechanism algorithms
-signature-algorithms List of signature algorithms
-asymcipher-algorithms List of asymmetric cipher algorithms
-public-key-algorithms List of public key algorithms
-public-key-methods List of public key methods
-store-loaders List of store loaders
-providers List of provider information
-engines List of loaded engines
-disabled List of disabled features
-options val List options for specified command
-objects List built in objects (OID<->name mappings)
Provider options:
-provider-path val Provider load path (must be before 'provider' argument if required)
-provider val Provider to load (can be specified multiple times)
-propquery val Property query used when fetching algorithms
qzz@qzz-virtual-machine:~/command_history_repo$ openssl -help
help:
Standard commands
asn1parse ca ciphers cmp
cms crl crl2pkcs7 dgst
dhparam dsa dsaparam ec
ecparam enc engine errstr
fipsinstall gendsa genpkey genrsa
help info kdf list
mac nseq ocsp passwd
pkcs12 pkcs7 pkcs8 pkey
pkeyparam pkeyutl prime rand
rehash req rsa rsautl
s_client s_server s_time sess_id
smime speed spkac srp
storeutl ts verify version
x509
Message Digest commands (see the `dgst' command for more details)
blake2b512 blake2s256 md4 md5
rmd160 sha1 sha224 sha256
sha3-224 sha3-256 sha3-384 sha3-512
sha384 sha512 sha512-224 sha512-256
shake128 shake256 sm3
Cipher commands (see the `enc' command for more details)
aes-128-cbc aes-128-ecb aes-192-cbc aes-192-ecb
aes-256-cbc aes-256-ecb aria-128-cbc aria-128-cfb
aria-128-cfb1 aria-128-cfb8 aria-128-ctr aria-128-ecb
aria-128-ofb aria-192-cbc aria-192-cfb aria-192-cfb1
aria-192-cfb8 aria-192-ctr aria-192-ecb aria-192-ofb
aria-256-cbc aria-256-cfb aria-256-cfb1 aria-256-cfb8
aria-256-ctr aria-256-ecb aria-256-ofb base64
bf bf-cbc bf-cfb bf-ecb
bf-ofb camellia-128-cbc camellia-128-ecb camellia-192-cbc
camellia-192-ecb camellia-256-cbc camellia-256-ecb cast
cast-cbc cast5-cbc cast5-cfb cast5-ecb
cast5-ofb des des-cbc des-cfb
des-ecb des-ede des-ede-cbc des-ede-cfb
des-ede-ofb des-ede3 des-ede3-cbc des-ede3-cfb
des-ede3-ofb des-ofb des3 desx
rc2 rc2-40-cbc rc2-64-cbc rc2-cbc
rc2-cfb rc2-ecb rc2-ofb rc4
rc4-40 seed seed-cbc seed-cfb
seed-ecb seed-ofb sm4-cbc sm4-cfb
sm4-ctr sm4-ecb sm4-ofb
qzz@qzz-virtual-machine:~/command_history_repo$ echo 123 | openssl sm3
SM3(stdin)= e95001aed4b6f7de59169913997dace404f05091ed49c37133a9950a69405a9c
qzz@qzz-virtual-machine:~/command_history_repo$ echo "123" | openssl sm3
SM3(stdin)= e95001aed4b6f7de59169913997dace404f05091ed49c37133a9950a69405a9c
qzz@qzz-virtual-machine:~/command_history_repo$ echo "obase=16;123" | bc
7B
qzz@qzz-virtual-machine:~/command_history_repo$ echo -n -e "\x7B" > 123.bin
qzz@qzz-virtual-machine:~/command_history_repo$ openssl sm3 -file 123.bin
SM3(123.bin)= 2ed59fea0dbe4e4f02de67ee657eb6be8e22a7db425103402d8a36d7b6f6d344
qzz@qzz-virtual-machine:~/command_history_repo$ echo -ne "\x7B" | openssl sm3
SM3(stdin)= 2ed59fea0dbe4e4f02de67ee657eb6be8e22a7db425103402d8a36d7b6f6d344
qzz@qzz-virtual-machine:~/command_history_repo$ openssl prime -help
Usage: prime [options] [number...]
General options:
-help Display this summary
-bits +int Size of number in bits
-checks +int Number of checks
Output options:
-hex Hex output
-generate Generate a prime
-safe When used with -generate, generate a safe prime
Provider options:
-provider-path val Provider load path (must be before 'provider' argument if required)
-provider val Provider to load (can be specified multiple times)
-propquery val Property query used when fetching algorithms
Parameters:
number Number(s) to check for primality if not generating
qzz@qzz-virtual-machine:~/command_history_repo$ openssl prime 3
3 (3) is prime
qzz@qzz-virtual-machine:~/command_history_repo$ openssl prime 33
21 (33) is not prime
qzz@qzz-virtual-machine:~/command_history_repo$ openssl prime -checks 10 33
21 (33) is not prime
qzz@qzz-virtual-machine:~/command_history_repo$ openssl prime -hex 4F
4F (4F) is prime
qzz@qzz-virtual-machine:~/command_history_repo$ openssl prime -generate -bits 10
877
qzz@qzz-virtual-machine:~/command_history_repo$ openssl prime 877
36D (877) is prime
qzz@qzz-virtual-machine:~/command_history_repo$ openssl prime -generate -bits 10
971
qzz@qzz-virtual-machine:~/command_history_repo$ openssl prime 971
3CB (971) is prime
qzz@qzz-virtual-machine:~/command_history_repo$ openssl prime -generate -bits 10 -hex
0313
qzz@qzz-virtual-machine:~/command_history_repo$ openssl prime -hex 0377
377 (0377) is prime
qzz@qzz-virtual-machine:~/command_history_repo$ openssl prime -hex 0313
313 (0313) is prime
qzz@qzz-virtual-machine:~/command_history_repo$ openssl rand -help
Usage: rand [options] num
General options:
-help Display this summary
-engine val Use engine, possibly a hardware device
Output options:
-out outfile Output file
-base64 Base64 encode output
-hex Hex encode output
Random state options:
-rand val Load the given file(s) into the random number generator
-writerand outfile Write random data to the specified file
Provider options:
-provider-path val Provider load path (must be before 'provider' argument if required)
-provider val Provider to load (can be specified multiple times)
-propquery val Property query used when fetching algorithms
Parameters:
num Number of bytes to generate
qzz@qzz-virtual-machine:~/command_history_repo$ openssl rand 10
o???x?%P?qzz@qzz-virtual-machine:~/command_history_repo$ openssl rand 10 | od -topenssl rand 10 | od -tx1
0000000 ea 19 ae eb fe 36 ff 40 05 9e
0000012
qzz@qzz-virtual-machine:~/command_history_repo$ openssl rand 10 | xxd -p
bbd20d9f5b43bc284676
qzz@qzz-virtual-machine:~/command_history_repo$ openssl rand -hex 10
34344ab32e42e7d9f888
qzz@qzz-virtual-machine:~/command_history_repo$ openssl rand -base64 10
p5ne+RAmbK+J1g==
qzz@qzz-virtual-machine:~/command_history_repo$ openssl rand -out r1.bin 10
qzz@qzz-virtual-machine:~/command_history_repo$ od -tx1 r1.bin
0000000 4e f8 ca d4 57 79 73 b2 2f ae
0000012
qzz@qzz-virtual-machine:~/command_history_repo$ openssl rand 10 > r2.bin
qzz@qzz-virtual-machine:~/command_history_repo$ cat r2.bin | xxd -p
0a911f8a6cf15ab255ad
qzz@qzz-virtual-machine:~/command_history_repo$ openssl base64 -help
Usage: base64 [options]
General options:
-help Display this summary
-list List ciphers
-ciphers Alias for -list
-e Encrypt
-d Decrypt
-p Print the iv/key
-P Print the iv/key and exit
-engine val Use engine, possibly a hardware device
Input options:
-in infile Input file
-k val Passphrase
-kfile infile Read passphrase from file
Output options:
-out outfile Output file
-pass val Passphrase source
-v Verbose output
-a Base64 encode/decode, depending on encryption flag
-base64 Same as option -a
-A Used with -[base64|a] to specify base64 buffer as a single line
Encryption options:
-nopad Disable standard block padding
-salt Use salt in the KDF (default)
-nosalt Do not use salt in the KDF
-debug Print debug info
-bufsize val Buffer size
-K val Raw key, in hex
-S val Salt, in hex
-iv val IV in hex
-md val Use specified digest to create a key from the passphrase
-iter +int Specify the iteration count and force use of PBKDF2
-pbkdf2 Use password-based key derivation function 2
-none Don't encrypt
-* Any supported cipher
Random state options:
-rand val Load the given file(s) into the random number generator
-writerand outfile Write random data to the specified file
Provider options:
-provider-path val Provider load path (must be before 'provider' argument if required)
-provider val Provider to load (can be specified multiple times)
-propquery val Property query used when fetching algorithms
qzz@qzz-virtual-machine:~/command_history_repo$ echo ljp | openssl base64
bGpwCg==
qzz@qzz-virtual-machine:~/command_history_repo$ echo ljp | openssl base64 -e
bGpwCg==
qzz@qzz-virtual-machine:~/command_history_repo$ echo bGpwCg== | openssl base64 -d
ljp
qzz@qzz-virtual-machine:~/command_history_repo$ echo -ne "\x11\x22\x33" | openssl base64
ESIz
qzz@qzz-virtual-machine:~/command_history_repo$ echo ESIz | openssl base64 -d | xxd -p
112233
qzz@qzz-virtual-machine:~/command_history_repo$ echo -ne "\x11\x22\x33\x44" | openssl base64
ESIzRA==
qzz@qzz-virtual-machine:~/command_history_repo$ echo ESIzRA== | openssl base64 -d | xxd -p
11223344
qzz@qzz-virtual-machine:~/command_history_repo$ echo ljp > ljp.txt
qzz@qzz-virtual-machine:~/command_history_repo$ openssl base64 -in ljp.txt -out ljp.b64
qzz@qzz-virtual-machine:~/command_history_repo$ cat ljp.b64
bGpwCg==
qzz@qzz-virtual-machine:~/command_history_repo$ openssl base64 -d -in ljp.b64 -out ljp2.txt
qzz@qzz-virtual-machine:~/command_history_repo$ diff ljp.txt ljp2.txt
qzz@qzz-virtual-machine:~/command_history_repo$ cat ljp2.txt
ljp
qzz@qzz-virtual-machine:~/command_history_repo$ openssl asn1parse -help
Usage: asn1parse [options]
General options:
-help Display this summary
-oid infile file of extra oid definitions
I/O options:
-inform PEM|DER input format - one of DER PEM
-in infile input file
-out outfile output file (output format is always DER)
-noout do not produce any output
-offset +int offset into file
-length +int length of section in file
-strparse +int offset; a series of these can be used to 'dig'
-genstr val string to generate ASN1 structure from
into multiple ASN1 blob wrappings
-genconf val file to generate ASN1 structure from
-strictpem do not attempt base64 decode outside PEM markers
-item val item to parse and print
(-inform will be ignored)
Formatting options:
-i indents the output
-dump unknown data in hex form
-dlimit +int dump the first arg bytes of unknown data in hex form
qzz@qzz-virtual-machine:~/command_history_repo$ echo -ne "\x03\x02\x04\x90" >bitstring.der
qzz@qzz-virtual-machine:~/command_history_repo$ openssl asn1parse -inform der -i -in bitstring.der
0:d=0 hl=2 l= 2 prim: BIT STRING
qzz@qzz-virtual-machine:~/command_history_repo$ openssl base64 -in bitstring.der -out bitstring.pem
qzz@qzz-virtual-machine:~/command_history_repo$ ls bitstring.pem
bitstring.pem
qzz@qzz-virtual-machine:~/command_history_repo$ openssl asn1parse -inform PEM -in bitstring.pem
0:d=0 hl=2 l= 2 prim: BIT STRING
qzz@qzz-virtual-machine:~/command_history_repo$ openssl dgst -help
Usage: dgst [options] [file...]
General options:
-help Display this summary
-list List digests
-engine val Use engine e, possibly a hardware device
-engine_impl Also use engine given by -engine for digest operations
-passin val Input file pass phrase source
Output options:
-c Print the digest with separating colons
-r Print the digest in coreutils format
-out outfile Output to filename rather than stdout
-keyform format Key file format (ENGINE, other values ignored)
-hex Print as hex dump
-binary Print in binary form
-xoflen +int Output length for XOF algorithms
-d Print debug info
-debug Print debug info
Signing options:
-sign val Sign digest using private key
-verify val Verify a signature using public key
-prverify val Verify a signature using private key
-sigopt val Signature parameter in n:v form
-signature infile File with signature to verify
-hmac val Create hashed MAC with key
-mac val Create MAC (not necessarily HMAC)
-macopt val MAC algorithm parameters in n:v form or key
-* Any supported digest
-fips-fingerprint Compute HMAC with the key used in OpenSSL-FIPS fingerprint
Random state options:
-rand val Load the given file(s) into the random number generator
-writerand outfile Write random data to the specified file
Provider options:
-provider-path val Provider load path (must be before 'provider' argument if required)
-provider val Provider to load (can be specified multiple times)
-propquery val Property query used when fetching algorithms
Parameters:
file Files to digest (optional; default is stdin)
qzz@qzz-virtual-machine:~/command_history_repo$ openssl dgst -list
Supported digests:
-blake2b512 -blake2s256 -md4
-md5 -md5-sha1 -ripemd
-ripemd160 -rmd160 -sha1
-sha224 -sha256 -sha3-224
-sha3-256 -sha3-384 -sha3-512
-sha384 -sha512 -sha512-224
-sha512-256 -shake128 -shake256
-sm3 -ssl3-md5 -ssl3-sha1
-whirlpool
qzz@qzz-virtual-machine:~/command_history_repo$ echo ljp | openssl dgst -sm3
SM3(stdin)= a4f888920807c7502ca20d027486dfe20be6259bf9287713f7744b120f282589
qzz@qzz-virtual-machine:~/command_history_repo$ echo ljp | openssl sm3
SM3(stdin)= a4f888920807c7502ca20d027486dfe20be6259bf9287713f7744b120f282589
qzz@qzz-virtual-machine:~/command_history_repo$ echo ljp | openssl sm3 -hex
SM3(stdin)= a4f888920807c7502ca20d027486dfe20be6259bf9287713f7744b120f282589
qzz@qzz-virtual-machine:~/command_history_repo$ echo ljp | openssl sm3 -binary
t???P,?
qzz@qzz-virtual-machine:~/command_history_repo$ echo ljp | openssl sm3 -binary | xxd -p-binary | xxd -p
a4f888920807c7502ca20d027486dfe20be6259bf9287713f7744b120f28
2589
qzz@qzz-virtual-machine:~/command_history_repo$ echo ljp > ljp.txt
qzz@qzz-virtual-machine:~/command_history_repo$ openssl sm3 ljp.txt
SM3(ljp.txt)= a4f888920807c7502ca20d027486dfe20be6259bf9287713f7744b120f282589
qzz@qzz-virtual-machine:~/command_history_repo$ echo ljp | openssl sm3
SM3(stdin)= a4f888920807c7502ca20d027486dfe20be6259bf9287713f7744b120f282589
qzz@qzz-virtual-machine:~/command_history_repo$ openssl enc -help
Usage: enc [options]
General options:
-help Display this summary
-list List ciphers
-ciphers Alias for -list
-e Encrypt
-d Decrypt
-p Print the iv/key
-P Print the iv/key and exit
-engine val Use engine, possibly a hardware device
Input options:
-in infile Input file
-k val Passphrase
-kfile infile Read passphrase from file
Output options:
-out outfile Output file
-pass val Passphrase source
-v Verbose output
-a Base64 encode/decode, depending on encryption flag
-base64 Same as option -a
-A Used with -[base64|a] to specify base64 buffer as a single line
Encryption options:
-nopad Disable standard block padding
-salt Use salt in the KDF (default)
-nosalt Do not use salt in the KDF
-debug Print debug info
-bufsize val Buffer size
-K val Raw key, in hex
-S val Salt, in hex
-iv val IV in hex
-md val Use specified digest to create a key from the passphrase
-iter +int Specify the iteration count and force use of PBKDF2
-pbkdf2 Use password-based key derivation function 2
-none Don't encrypt
-* Any supported cipher
Random state options:
-rand val Load the given file(s) into the random number generator
-writerand outfile Write random data to the specified file
Provider options:
-provider-path val Provider load path (must be before 'provider' argument if required)
-provider val Provider to load (can be specified multiple times)
-propquery val Property query used when fetching algorithms
qzz@qzz-virtual-machine:~/command_history_repo$ openssl enc -list
Supported ciphers:
-aes-128-cbc -aes-128-cfb -aes-128-cfb1
-aes-128-cfb8 -aes-128-ctr -aes-128-ecb
-aes-128-ofb -aes-192-cbc -aes-192-cfb
-aes-192-cfb1 -aes-192-cfb8 -aes-192-ctr
-aes-192-ecb -aes-192-ofb -aes-256-cbc
-aes-256-cfb -aes-256-cfb1 -aes-256-cfb8
-aes-256-ctr -aes-256-ecb -aes-256-ofb
-aes128 -aes128-wrap -aes192
-aes192-wrap -aes256 -aes256-wrap
-aria-128-cbc -aria-128-cfb -aria-128-cfb1
-aria-128-cfb8 -aria-128-ctr -aria-128-ecb
-aria-128-ofb -aria-192-cbc -aria-192-cfb
-aria-192-cfb1 -aria-192-cfb8 -aria-192-ctr
-aria-192-ecb -aria-192-ofb -aria-256-cbc
-aria-256-cfb -aria-256-cfb1 -aria-256-cfb8
-aria-256-ctr -aria-256-ecb -aria-256-ofb
-aria128 -aria192 -aria256
-bf -bf-cbc -bf-cfb
-bf-ecb -bf-ofb -blowfish
-camellia-128-cbc -camellia-128-cfb -camellia-128-cfb1
-camellia-128-cfb8 -camellia-128-ctr -camellia-128-ecb
-camellia-128-ofb -camellia-192-cbc -camellia-192-cfb
-camellia-192-cfb1 -camellia-192-cfb8 -camellia-192-ctr
-camellia-192-ecb -camellia-192-ofb -camellia-256-cbc
-camellia-256-cfb -camellia-256-cfb1 -camellia-256-cfb8
-camellia-256-ctr -camellia-256-ecb -camellia-256-ofb
-camellia128 -camellia192 -camellia256
-cast -cast-cbc -cast5-cbc
-cast5-cfb -cast5-ecb -cast5-ofb
-chacha20 -des -des-cbc
-des-cfb -des-cfb1 -des-cfb8
-des-ecb -des-ede -des-ede-cbc
-des-ede-cfb -des-ede-ecb -des-ede-ofb
-des-ede3 -des-ede3-cbc -des-ede3-cfb
-des-ede3-cfb1 -des-ede3-cfb8 -des-ede3-ecb
-des-ede3-ofb -des-ofb -des3
-des3-wrap -desx -desx-cbc
-id-aes128-wrap -id-aes128-wrap-pad -id-aes192-wrap
-id-aes192-wrap-pad -id-aes256-wrap -id-aes256-wrap-pad
-id-smime-alg-CMS3DESwrap -rc2 -rc2-128
-rc2-40 -rc2-40-cbc -rc2-64
-rc2-64-cbc -rc2-cbc -rc2-cfb
-rc2-ecb -rc2-ofb -rc4
-rc4-40 -seed -seed-cbc
-seed-cfb -seed-ecb -seed-ofb
-sm4 -sm4-cbc -sm4-cfb
-sm4-ctr -sm4-ecb -sm4-ofb
qzz@qzz-virtual-machine:~/command_history_repo$ openssl sm4-cbc -K "2851fa25211a48023794ae9515909603" -iv
sm4-cbc: Option -iv needs a value
sm4-cbc: Use -help for summary.
qzz@qzz-virtual-machine:~/command_history_repo$ openssl sm4-cbc -K "2851fa25211a48023794ae9515909603" -iv "da80e405a4998c351b0717093cbe86ab" -in ftr.txt -out ftr.enc
Can't open "ftr.txt" for reading, No such file or directory
4047E8FB66700000:error:80000002:system library:BIO_new_file:No such file or directory:../crypto/bio/bss_file.c:67:calling fopen(ftr.txt, rb)
4047E8FB66700000:error:10000080:BIO routines:BIO_new_file:no such file:../crypto/bio/bss_file.c:75:
qzz@qzz-virtual-machine:~/command_history_repo$ openssl sm4-cbc -K "2851fa25211a48023794ae9515909603" -iv "da80e405a4998c351b0717093cbe86ab" -in ftr.txt -out ftr.enc
qzz@qzz-virtual-machine:~/command_history_repo$ openssl sm4-cbc -d -K "2851fa25211a48023794ae9515909603" -iv "da80e405a4998c351b0717093cbe86ab" -in ftr.enc -out ftr2.txt
qzz@qzz-virtual-machine:~/command_history_repo$ diff ftr.txt ftr2.txt
qzz@qzz-virtual-machine:~/command_history_repo$ cat ftr2.txt
aaaa
qzz@qzz-virtual-machine:~/command_history_repo$ openssl genpkey -algorithm RSA -out private_key.pem
...+.....+......+...+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*.....+......+...+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*...............+.......+.....+......+..........+........+...................+......+..+.............+.....+....+...+...+......+......+...+..............+......+....+..+................+...+..+...............+...+.+........+.+.....+.+........+............+......+...+.+..............+.......+.....+...+....+........+....+.....+....+............+........+....+...+...+.....+.+.....+..........+...+..+.+..+......+....+..+....+..+..........+...+.........+...........+.........+..........+..+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
.+..+.......+......+........+....+............+........+...+...+.+......+............+.....+.+............+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*..+.....+.......+.....+.............+...+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*....+...+.........+...+..........+...+..+...+..........+.........+.....+.+...+.........+.....................+..+...+......+.+.................+......+....+.....+......+....+...+.................+...+.........+.+........+.......+...+...............+..+...............+............+...+............+.+.....+.+......+.....+....+...+........+...+.+......+...+.....+....+..+......+.......+..+...+..........+...+...+.....+.+......+....................+.......+........+...+.+.........+.....+....+.....+...+.......+.....+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
qzz@qzz-virtual-machine:~/command_history_repo$ ls private_key.pem
private_key.pem
qzz@qzz-virtual-machine:~/command_history_repo$ cat private_key.pem
-----BEGIN PRIVATE KEY-----
MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQC/++0IYgo6cnoQ
s16ns39SakytA82UuZtm8qxj5Q657EAEJ5/G4NQompmo1Cn+xrKRKJaPGWwkd9bV
JhCoxwQiGKzt+RXlsOGeLrb/+kcylQOKXmZO36G6ZzFVEguivBna3FU+CQKpjKGU
KMDd80sStdETlQVdSE4Gf3QEFPa6Jl/pmlhgKG/Km+Xh2KSH4eo7KGShAtGVn4UN
BaC5Z8ewhffmP1PMnjL+N7ovQt/OMRGfz7ut2QnF+1DFMFJhsyxqGSqy9O7YYdwc
AsXHNBU8vXVCUkKBgjRkv09I5on2WGHYLhy3qHDx3p3jWoUcjUBCXDfPzzTYE5ol
wo1Sw1r7AgMBAAECggEALCSkCuJoEapS0NY9dHf8VZnliX6vXXwT9GbmJo37hdqB
mbL2tQbrIW7y1/P4uAE9+8yGWd7xk60Oc7It8HDaTXC5CnrUgxzZs8JwB4mnp0TG
LKGqCoa3LCIgILxmeoOfukghPYNa3ltcp7F7L02KvIGb0lHYiuteLXZO2cVsOb7E
9fS8XZundBxiVf6tIuBGuyatBIrDT5jN/o9/yK6NjMV/Sil/eLroZPP7gEIixtLK
ParVyR1uzpsEcwmrHcNDK1V/EbpAxm4HrblMeb9AbMxFS7RMC9UFLMkX/nweJbCj
7U28YjCysOKSHgTM9mFVDZqU5pIYm66fcGlFjnBuIQKBgQDQKGtF+aLtJs/1S8Ux
gF/Rppc6KT59322hTkz9wrsRFxk1LbStW0pAHw+YwuYJxEJaEnyOArqJpEu2a8uU
r0+XBprZ8ArMoTPNw62oWK2tcnxzg8wKZ/rOJ9TICi9BOLBDSECU7KoEAiDbhRGK
rvPMue0zSfGfMU87ISgITl9+SwKBgQDsG9+t1u8pLqnexpyp0y0xrp7bE6hDs9CE
tHxa/0PfiUA/6kDtHG4KfPTrYPPYsJAxGN4I7FE/Hamjlwr4lrVRBEdIZjPoAFPJ
I1QkqwaZDlCrK9F/37/0OzZ0KDRKu1U4z3h8H4KmMePdTVT48nHTo1mExEOzFE4c
rV9ZYOjoEQKBgDYg7JRLsBRfLWCqDWMr8L7BxT14kCmHOijiBZ9PTfnJueJcOkmC
HbLC4PlmZQ9RG7f0arM6/mrgcFfFfDDzzYyGSSo3A3fmy2PMaJIITVF3Hemj8iEa
nNuS+//wtg0NwrgcR77yM9vK+eRbnA4mJHuuNYJKziwJVIMZwiE20Bo1AoGANpHe
qcQSdJc3ZajLzqhjOqdcSdAKRNOLbxBz6Wg0HLcRJXST2vmGKWBmDvzSfxOXz/Eq
aC+OO6M0cP3Y6EmU0IvHmeEdQBLLSqKisPLiTH+1f0paWk6xg9YnqMMeCuOvN7kj
5LQ3swe23ZAhAoSucDbB2uCtsPcRcqlTb0npqrECgYEAoo2SHKP/8rbBvsGi8cZK
hpw6J7infcV4J0Z7VNLVa0XrX9Nc9pZziCFYbu2ZqJHDMnkzMBGFL9IlFZ7kk9T2
pEeGDo9BkQjA55GzIGsGFOJyZaOIRDExXul+cj1W1djWIV6KQYO2nRc2ifCWYKXT
6dHq2DhdKWRnC/CXHj8OZbc=
-----END PRIVATE KEY-----
qzz@qzz-virtual-machine:~/command_history_repo$ openssl genpkey -help
Usage: genpkey [options]
General options:
-help Display this summary
-engine val Use engine, possibly a hardware device
-paramfile infile Parameters file
-algorithm val The public key algorithm
-quiet Do not output status while generating keys
-pkeyopt val Set the public key algorithm option as opt:value
-config infile Load a configuration file (this may load modules)
Output options:
-out outfile Output file
-outform PEM|DER output format (DER or PEM)
-pass val Output file pass phrase source
-genparam Generate parameters, not key
-text Print the in text
-* Cipher to use to encrypt the key
Provider options:
-provider-path val Provider load path (must be before 'provider' argument if required)
-provider val Provider to load (can be specified multiple times)
-propquery val Property query used when fetching algorithms
Order of options may be important! See the documentation.
qzz@qzz-virtual-machine:~/command_history_repo$ openssl rsa -pubout -in private_key.pem -out public_key.pem
writing RSA key
qzz@qzz-virtual-machine:~/command_history_repo$ ls public_key.pem
public_key.pem
qzz@qzz-virtual-machine:~/command_history_repo$ cat public_key.pem
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAv/vtCGIKOnJ6ELNep7N/
UmpMrQPNlLmbZvKsY+UOuexABCefxuDUKJqZqNQp/saykSiWjxlsJHfW1SYQqMcE
Ihis7fkV5bDhni62//pHMpUDil5mTt+humcxVRILorwZ2txVPgkCqYyhlCjA3fNL
ErXRE5UFXUhOBn90BBT2uiZf6ZpYYChvypvl4dikh+HqOyhkoQLRlZ+FDQWguWfH
sIX35j9TzJ4y/je6L0LfzjERn8+7rdkJxftQxTBSYbMsahkqsvTu2GHcHALFxzQV
PL11QlJCgYI0ZL9PSOaJ9lhh2C4ct6hw8d6d41qFHI1AQlw3z8802BOaJcKNUsNa
+wIDAQAB
-----END PUBLIC KEY-----
qzz@qzz-virtual-machine:~/command_history_repo$ openssl pkeyutl -encrypt -inkey public_key.pem -pubin -in ljp.txt -out ljprsaenc.bin
qzz@qzz-virtual-machine:~/command_history_repo$ openssl pkeyutl -decrypt -inkey private_key.pem -in ljprsaenc.bin -out ljprsadec.txt
qzz@qzz-virtual-machine:~/command_history_repo$ ls
123.bin bitstring.pem ljp2.txt ljp.txt public_key.pem
123.txt ftr2.txt ljp.b64 log_1_hezuo.log r1.bin
1.txt ftr.enc ljprsadec.txt log.log r2.bin
bitstring.der ftr.txt ljprsaenc.bin private_key.pem
qzz@qzz-virtual-machine:~/command_history_repo$ diff ljp.txt ljprsadec.txt
qzz@qzz-virtual-machine:~/command_history_repo$ openssl pkeyutl -help
Usage: pkeyutl [options]
General options:
-help Display this summary
-engine val Use engine, possibly a hardware device
-engine_impl Also use engine given by -engine for crypto operations
-sign Sign input data with private key
-verify Verify with public key
-encrypt Encrypt input data with public key
-decrypt Decrypt input data with private key
-derive Derive shared secret
-config infile Load a configuration file (this may load modules)
Input options:
-in infile Input file - default stdin
-rawin Indicate the input data is in raw form
-pubin Input is a public key
-inkey val Input private key file
-passin val Input file pass phrase source
-peerkey val Peer key file used in key derivation
-peerform PEM|DER|ENGINE Peer key format (DER/PEM/P12/ENGINE)
-certin Input is a cert with a public key
-rev Reverse the order of the input buffer
-sigfile infile Signature file (verify operation only)
-keyform PEM|DER|ENGINE Private key format (ENGINE, other values ignored)
Output options:
-out outfile Output file - default stdout
-asn1parse asn1parse the output data
-hexdump Hex dump output
-verifyrecover Verify with public key, recover original data
Signing/Derivation options:
-digest val Specify the digest algorithm when signing the raw input data
-pkeyopt val Public key options as opt:value
-pkeyopt_passin val Public key option that is read as a passphrase argument opt:passphrase
-kdf val Use KDF algorithm
-kdflen +int KDF algorithm output length
Random state options:
-rand val Load the given file(s) into the random number generator
-writerand outfile Write random data to the specified file
Provider options:
-provider-path val Provider load path (must be before 'provider' argument if required)
-provider val Provider to load (can be specified multiple times)
-propquery val Property query used when fetching algorithms
qzz@qzz-virtual-machine:~/command_history_repo$ openssl dgst -sha256 -sign private_key.pem -out ljp.sig ljp.txt
qzz@qzz-virtual-machine:~/command_history_repo$ openssl dgst -sha256 -verify public_key.pem -signature ljp.sig ljp.txt
Verified OK
qzz@qzz-virtual-machine:~/command_history_repo$ openssl pkeyutl -sign -inkey private_key.pem -in ljp.txt -out ljprsa.sig
qzz@qzz-virtual-machine:~/command_history_repo$ openssl pkeyutl -verify -in ljp.txt -sigfile ljprsa.sig -inkey private_key.pem
Signature Verified Successfully
qzz@qzz-virtual-machine:~/command_history_repo$ openssl ecparam -genkey -name SM2 -out sm2private_key.pem
qzz@qzz-virtual-machine:~/command_history_repo$ cat sm2private_key.pem
-----BEGIN SM2 PARAMETERS-----
BggqgRzPVQGCLQ==
-----END SM2 PARAMETERS-----
-----BEGIN PRIVATE KEY-----
MIGIAgEAMBQGCCqBHM9VAYItBggqgRzPVQGCLQRtMGsCAQEEIH636dijcYJaq//O
IWvUPFYao99gOxcZfNdSc/V9TSnCoUQDQgAEzpRJRb9tWhCq+sg9YjN+YoHzFGzH
JIXMEmHeQqe3SQ0xawbsr6A3aCdVBI69iVEdMSe0h6luK9Z7GmJ3s9HkEA==
-----END PRIVATE KEY-----
qzz@qzz-virtual-machine:~/command_history_repo$ openssl asn1parse -inform PEM -in sm2private_key.pem
0:d=0 hl=2 l= 8 prim: OBJECT :sm2
qzz@qzz-virtual-machine:~/command_history_repo$ openssl base64 -d -in sm2private_key.pem -out sm2private_key.der
qzz@qzz-virtual-machine:~/command_history_repo$ openssl asn1parse -inform DER -in sm2private_key.der
0:d=0 hl=2 l= 8 prim: OBJECT :sm2
qzz@qzz-virtual-machine:~/command_history_repo$ od -tx1 sm2private_key.der
0000000 06 08 2a 81 1c cf 55 01 82 2d
0000012
qzz@qzz-virtual-machine:~/command_history_repo$ openssl pkey -in sm2private_key.pem -text -noout
Private-Key: (256 bit)
priv:
7e:b7:e9:d8:a3:71:82:5a:ab:ff:ce:21:6b:d4:3c:
56:1a:a3:df:60:3b:17:19:7c:d7:52:73:f5:7d:4d:
29:c2
pub:
04:ce:94:49:45:bf:6d:5a:10:aa:fa:c8:3d:62:33:
7e:62:81:f3:14:6c:c7:24:85:cc:12:61:de:42:a7:
b7:49:0d:31:6b:06:ec:af:a0:37:68:27:55:04:8e:
bd:89:51:1d:31:27:b4:87:a9:6e:2b:d6:7b:1a:62:
77:b3:d1:e4:10
ASN1 OID: SM2
qzz@qzz-virtual-machine:~/command_history_repo$ openssl ecparam -help
Usage: ecparam [options]
General options:
-help Display this summary
-list_curves Prints a list of all curve 'short names'
-engine val Use engine, possibly a hardware device
-genkey Generate ec key
-in infile Input file - default stdin
-inform PEM|DER Input format - default PEM (DER or PEM)
-out outfile Output file - default stdout
-outform PEM|DER Output format - default PEM
Output options:
-text Print the ec parameters in text form
-noout Do not print the ec parameter
-param_enc val Specifies the way the ec parameters are encoded
Parameter options:
-check Validate the ec parameters
-check_named Check that named EC curve parameters have not been modified
-no_seed If 'explicit' parameters are chosen do not use the seed
-name val Use the ec parameters with specified 'short name'
-conv_form val Specifies the point conversion form
Random state options:
-rand val Load the given file(s) into the random number generator
-writerand outfile Write random data to the specified file
Provider options:
-provider-path val Provider load path (must be before 'provider' argument if required)
-provider val Provider to load (can be specified multiple times)
-propquery val Property query used when fetching algorithms
qzz@qzz-virtual-machine:~/command_history_repo$ openssl ec -in sm2private_key.pem -pubout -out sm2public_key.pem
read EC key
writing EC key
qzz@qzz-virtual-machine:~/command_history_repo$ cat sm2public_key.pem
-----BEGIN PUBLIC KEY-----
MFowFAYIKoEcz1UBgi0GCCqBHM9VAYItA0IABM6USUW/bVoQqvrIPWIzfmKB8xRs
xySFzBJh3kKnt0kNMWsG7K+gN2gnVQSOvYlRHTEntIepbivWexpid7PR5BA=
-----END PUBLIC KEY-----
qzz@qzz-virtual-machine:~/command_history_repo$ openssl asn1parse -inform PEM -in sm2public_key.pem
0:d=0 hl=2 l= 90 cons: SEQUENCE
2:d=1 hl=2 l= 20 cons: SEQUENCE
4:d=2 hl=2 l= 8 prim: OBJECT :sm2
14:d=2 hl=2 l= 8 prim: OBJECT :sm2
24:d=1 hl=2 l= 66 prim: BIT STRING
qzz@qzz-virtual-machine:~/command_history_repo$ openssl ec -help
Usage: ec [options]
General options:
-help Display this summary
-engine val Use engine, possibly a hardware device
Input options:
-in val Input file
-inform format Input format (DER/PEM/P12/ENGINE)
-pubin Expect a public key in input file
-passin val Input file pass phrase source
-check check key consistency
-* Any supported cipher
-param_enc val Specifies the way the ec parameters are encoded
-conv_form val Specifies the point conversion form
Output options:
-out outfile Output file
-outform PEM|DER Output format - DER or PEM
-noout Don't print key out
-text Print the key
-param_out Print the elliptic curve parameters
-pubout Output public key, not private
-no_public exclude public key from private key
-passout val Output file pass phrase source
Provider options:
-provider-path val Provider load path (must be before 'provider' argument if required)
-provider val Provider to load (can be specified multiple times)
-propquery val Property query used when fetching algorithms
qzz@qzz-virtual-machine:~/command_history_repo$ openssl pkeyutl -encrypt -pubin -inkey sm2public_key.pem -in ljp.txt -out ljpsm2enc.bin
qzz@qzz-virtual-machine:~/command_history_repo$ openssl pkeyutl -decrypt -inkey sm2private_key.pem -in ljpsm2enc.bin -out ljpsm2dec.txt
qzz@qzz-virtual-machine:~/command_history_repo$ diff ljp.txt ljpsm2dec.txt
qzz@qzz-virtual-machine:~/command_history_repo$ openssl sm3 -sign sm2private_key.pem -out ljpsm2.sig ljp.txt
qzz@qzz-virtual-machine:~/command_history_repo$ openssl sm3 -verify sm2public_key.pem -signature ljpsm2.sig ljp.txt
Verified OK
qzz@qzz-virtual-machine:~/command_history_repo$ openssl pkeyutl -sign -in ljp.txt -inkey sm2private_key.pem -out ljpsm2.sig -rawin -digest sm3
qzz@qzz-virtual-machine:~/command_history_repo$ od -tx1 ljpsm2.sig
0000000 30 44 02 20 26 b9 bd 95 cc 3e a6 d5 e3 ad 82 cc
0000020 47 76 69 84 90 e7 f7 b6 80 0c c4 7e b3 8f 94 07
0000040 02 88 d6 67 02 20 1a 64 9f 7c e1 c7 9b c3 58 f3
0000060 a1 09 ff f9 34 6c 94 43 60 15 24 05 41 66 f1 b6
0000100 68 4c fd 31 bc 93
0000106
qzz@qzz-virtual-machine:~/command_history_repo$ openssl pkeyutl -verify -in ljp.txt -inkey sm2private_key.pem -sigfile ljpsm2.sig -rawin -digest sm3
Signature Verified Successfully
qzz@qzz-virtual-machine:~/command_history_repo$ openssl list -commands
asn1parse ca ciphers cmp
cms crl crl2pkcs7 dgst
dhparam dsa dsaparam ec
ecparam enc engine errstr
fipsinstall gendsa genpkey genrsa
help info kdf list
mac nseq ocsp passwd
pkcs12 pkcs7 pkcs8 pkey
pkeyparam pkeyutl prime rand
rehash req rsa rsautl
s_client s_server s_time sess_id
smime speed spkac srp
storeutl ts verify version
x509
qzz@qzz-virtual-machine:~/command_history_repo$
2.參考云班課相關(guān)教學(xué)視頻,在Ubuntu或openEuler中(推薦openEuler)中實(shí)踐課程課程思維導(dǎo)圖中GmSSL相關(guān)內(nèi)容,使用Markdown記錄詳細(xì)記錄實(shí)踐過程,每完成一項(xiàng)gitcommit一次。(5‘)
qzz@qzz-virtual-machine:~/GmSSL/build$ gmssl -version
gmssl: illegal option '-version'
usage: gmssl command [options]
command -help
Commands:
help Print this help message
version Print version
rand Generate random bytes
sm2keygen Generate SM2 keypair
sm2sign Generate SM2 signature
sm2verify Verify SM2 signature
sm2encrypt Encrypt with SM2 public key
sm2decrypt Decrypt with SM2 private key
sm3 Generate SM3 hash
sm3hmac Generate SM3 HMAC tag
sm3_pbkdf2 Hash password into key using PBKDF2 algoritm
sm3xmss_keygen Generate SM3-XMSS keypair
sm4_ecb Encrypt or decrypt with SM4 ECB
sm4_cbc Encrypt or decrypt with SM4 CBC
sm4_ctr Encrypt or decrypt with SM4 CTR
sm4_cfb Encrypt or decrypt with SM4 CFB
sm4_ofb Encrypt or decrypt with SM4 OFB
sm4_ccm Encrypt or decrypt with SM4 CCM
sm4_gcm Encrypt or decrypt with SM4 GCM
sm4_xts Encrypt or decrypt with SM4 XTS
sm4_cbc_sm3_hmac Encrypt or decrypt with SM4 CBC with SM3-HMAC
sm4_ctr_sm3_hmac Encrypt or decrypt with SM4 CTR with SM3-HMAC
sm4_cbc_mac Generate SM4 CBC-MAC
ghash Generate GHASH
zuc Encrypt or decrypt with ZUC
sm9setup Generate SM9 master secret
sm9keygen Generate SM9 private key
sm9sign Generate SM9 signature
sm9verify Verify SM9 signature
sm9encrypt SM9 public key encryption
sm9decrypt SM9 decryption
reqgen Generate certificate signing request (CSR)
reqsign Generate certificate from CSR
reqparse Parse and print a CSR
crlget Download the CRL of given certificate
crlgen Sign a CRL with CA certificate and private key
crlverify Verify a CRL with issuer's certificate
crlparse Parse and print CRL
certgen Generate a self-signed certificate
certparse Parse and print certificates
certverify Verify certificate chain
certrevoke Revoke certificate and output RevokedCertificate record
cmsparse Parse CMS (cryptographic message syntax) file
cmsencrypt Generate CMS EnvelopedData
cmsdecrypt Decrypt CMS EnvelopedData
cmssign Generate CMS SignedData
cmsverify Verify CMS SignedData
sdfinfo Print SDF device info
sdfdigest Generate SM3 hash with SDF device
sdfexport Export SM2 signing public key from SDF device
sdfsign Generate SM2 signature with SDF internal private key
sdfencrypt SM2/SM4-CBC hybrid encryption with SDF device
sdfdecrypt SM2/SM4-CBC hybrid decryption with SDF device
sdftest Test vendor's SDF library and device
tlcp_client TLCP client
tlcp_server TLCP server
tls12_client TLS 1.2 client
tls12_server TLS 1.2 server
tls13_client TLS 1.3 client
tls13_server TLS 1.3 server
run `gmssl <command> -help` to print help of the given command
qzz@qzz-virtual-machine:~/GmSSL/build$ gmssl version
GmSSL 3.1.2 Dev
qzz@qzz-virtual-machine:~/GmSSL/build$ cd
qzz@qzz-virtual-machine:~$ cd command_history_repo
qzz@qzz-virtual-machine:~/command_history_repo$ script log_gm.log
Script started, output log file is 'log_gm.log'.
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl help
usage: gmssl command [options]
command -help
Commands:
help Print this help message
version Print version
rand Generate random bytes
sm2keygen Generate SM2 keypair
sm2sign Generate SM2 signature
sm2verify Verify SM2 signature
sm2encrypt Encrypt with SM2 public key
sm2decrypt Decrypt with SM2 private key
sm3 Generate SM3 hash
sm3hmac Generate SM3 HMAC tag
sm3_pbkdf2 Hash password into key using PBKDF2 algoritm
sm3xmss_keygen Generate SM3-XMSS keypair
sm4_ecb Encrypt or decrypt with SM4 ECB
sm4_cbc Encrypt or decrypt with SM4 CBC
sm4_ctr Encrypt or decrypt with SM4 CTR
sm4_cfb Encrypt or decrypt with SM4 CFB
sm4_ofb Encrypt or decrypt with SM4 OFB
sm4_ccm Encrypt or decrypt with SM4 CCM
sm4_gcm Encrypt or decrypt with SM4 GCM
sm4_xts Encrypt or decrypt with SM4 XTS
sm4_cbc_sm3_hmac Encrypt or decrypt with SM4 CBC with SM3-HMAC
sm4_ctr_sm3_hmac Encrypt or decrypt with SM4 CTR with SM3-HMAC
sm4_cbc_mac Generate SM4 CBC-MAC
ghash Generate GHASH
zuc Encrypt or decrypt with ZUC
sm9setup Generate SM9 master secret
sm9keygen Generate SM9 private key
sm9sign Generate SM9 signature
sm9verify Verify SM9 signature
sm9encrypt SM9 public key encryption
sm9decrypt SM9 decryption
reqgen Generate certificate signing request (CSR)
reqsign Generate certificate from CSR
reqparse Parse and print a CSR
crlget Download the CRL of given certificate
crlgen Sign a CRL with CA certificate and private key
crlverify Verify a CRL with issuer's certificate
crlparse Parse and print CRL
certgen Generate a self-signed certificate
certparse Parse and print certificates
certverify Verify certificate chain
certrevoke Revoke certificate and output RevokedCertificate record
cmsparse Parse CMS (cryptographic message syntax) file
cmsencrypt Generate CMS EnvelopedData
cmsdecrypt Decrypt CMS EnvelopedData
cmssign Generate CMS SignedData
cmsverify Verify CMS SignedData
sdfinfo Print SDF device info
sdfdigest Generate SM3 hash with SDF device
sdfexport Export SM2 signing public key from SDF device
sdfsign Generate SM2 signature with SDF internal private key
sdfencrypt SM2/SM4-CBC hybrid encryption with SDF device
sdfdecrypt SM2/SM4-CBC hybrid decryption with SDF device
sdftest Test vendor's SDF library and device
tlcp_client TLCP client
tlcp_server TLCP server
tls12_client TLS 1.2 client
tls12_server TLS 1.2 server
tls13_client TLS 1.3 client
tls13_server TLS 1.3 server
run `gmssl <command> -help` to print help of the given command
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl version
GmSSL 3.1.2 Dev
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl sm3 -help
usage: sm3 [-hex|-bin] [-pubkey pem [-id str]] [-in file|-in_str str] [-out file]
Options
-hex Output hash value as hex string (by default)
-bin Output hash value as binary
-pubkey pem Signer's SM2 public key
When `-pubkey` is specified, hash with SM2 Z value
-id str SM2 Signer's ID string
-id_hex hex SM2 Signer's ID in hex format
`-id` and `-id_hex` should be used with `-pubkey`
`-id` and `-id_hex` should not be used together
If `-pubkey` is specified without `-id` or `id_hex`,
the default ID string '1234567812345678' is used
-in_str str To be hashed string
-in file | stdin To be hashed file path
`-in_str` and `-in` should not be used together
If neither `-in` nor `-in_str` specified, read from stdin
-out file | stdout Output file path. If not specified, output to stdout
Examples
gmssl sm3 -in_str abc
gmssl sm3 -in_str abc -bin
gmssl sm3 -in /path/to/file
gmssl sm3 -pubkey sm2pubkey.pem -id alice -in /path/to/file -bin
When reading from stdin, make sure the trailing newline character is removed
Linux/Mac:
echo -n abc | gmssl sm3
Windows:
C:\> echo |set/p="abc" | gmssl sm3
qzz@qzz-virtual-machine:~/command_history_repo$ echo -n "ljp" | gmssl sm3
778f6133eb1cc6cb09f59fe7833d0c7a9fac8cbe8e0097042105953a10709fd6
qzz@qzz-virtual-machine:~/command_history_repo$ echo -n "ljp" | gmssl sm3 -hex
778f6133eb1cc6cb09f59fe7833d0c7a9fac8cbe8e0097042105953a10709fd6
qzz@qzz-virtual-machine:~/command_history_repo$ echo -n "ljp" | gmssl sm3 -bin
w?a3??? ???=
qzz@qzz-virtual-machine:~/command_history_repo$ echo -n "ljp" | gmssl sm3 -bin | od -tx1 gmssl sm3 -bin | od -tx1
0000000 77 8f 61 33 eb 1c c6 cb 09 f5 9f e7 83 3d 0c 7a
0000020 9f ac 8c be 8e 00 97 04 21 05 95 3a 10 70 9f d6
0000040
qzz@qzz-virtual-machine:~/command_history_repo$ echo -n "ljp" > ljp.txt
qzz@qzz-virtual-machine:~/command_history_repo$ od -tx1 -tc ljp.txt
0000000 6c 6a 70
l j p
0000003
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl sm3 -in ljp.txt -out ljp.sm3
qzz@qzz-virtual-machine:~/command_history_repo$ cat ljp.sm3
778f6133eb1cc6cb09f59fe7833d0c7a9fac8cbe8e0097042105953a10709fd6
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl sm2keygen -pass 1234 -out sm2.pem -pubout sm2pub.pem
qzz@qzz-virtual-machine:~/command_history_repo$ ls
123.bin ljp2.txt ljpsm2.sig r2.bin
123.txt ljp.b64 ljp.sm3 sm2.pem
1.txt ljprsadec.txt ljp.txt sm2private_key.der
bitstring.der ljprsaenc.bin log_gm.log sm2private_key.pem
bitstring.pem ljprsa.sig log_op.log sm2public_key.pem
ftr2.txt ljp.sig private_key.pem sm2pub.pem
ftr.enc ljpsm2dec.txt public_key.pem
ftr.txt ljpsm2enc.bin r1.bin
qzz@qzz-virtual-machine:~/command_history_repo$ echo -n "ljp" | gmssl sm3 -pubkey sm2pub.pem -id 1234567812345678
395a8f8799eaa39414450b5d478d6013ab7decc175ee033be8b309bb3569ddf1
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl sm3hmac -help
usage: sm3hmac -key hex [-in file | -in_str str] [-bin|-hex] [-out file]
Options
-key hex Hex string of the MAC key
-in_str str Input as text string
-in file | stdin Input file path
`-in_str` and `-in` should not be used together
If neither `-in` nor `-in_str` specified, read from stdin
-hex Output MAC-tag as hex string (by default)
-bin Output MAC-tag as binary
`-hex` and `-bin` should not be used together
-out file | stdout Output file path. If not specified, output to stdout
Examples
KEY_HEX=`gmssl rand -outlen 16 -hex`
gmssl sm3hmac -key $KEY_HEX -in_str abc
gmssl sm3hmac -key $KEY_HEX -in_str abc -bin
gmssl sm3hmac -key $KEY_HEX -in /path/to/file
When reading from stdin, make sure the trailing newline character is removed
Linux/Mac:
echo -n abc | gmssl sm3hmac -key $KEY_HEX
Windows:
C:\> echo |set/p="abc" | gmssl sm3hmac -key 11223344556677881122334455667788
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl rand -help
usage: rand [-hex] [-rdrand|-rdseed] -outlen num [-out file]
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl rand -hex -outlen 16
0DBA79514636C16358890BDD7D4F439D
qzz@qzz-virtual-machine:~/command_history_repo$ echo -n "ljp" | gmssl sm3hmac -key E5E9CE4A122AEF1B0302032F56B2BFAB
908d34c4ab3ec5330f229c0a66b249134a1613418e8e4b8c90ee9026e7625e5a
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl sm4 -help
gmssl: illegal option 'sm4'
usage: gmssl command [options]
command -help
Commands:
help Print this help message
version Print version
rand Generate random bytes
sm2keygen Generate SM2 keypair
sm2sign Generate SM2 signature
sm2verify Verify SM2 signature
sm2encrypt Encrypt with SM2 public key
sm2decrypt Decrypt with SM2 private key
sm3 Generate SM3 hash
sm3hmac Generate SM3 HMAC tag
sm3_pbkdf2 Hash password into key using PBKDF2 algoritm
sm3xmss_keygen Generate SM3-XMSS keypair
sm4_ecb Encrypt or decrypt with SM4 ECB
sm4_cbc Encrypt or decrypt with SM4 CBC
sm4_ctr Encrypt or decrypt with SM4 CTR
sm4_cfb Encrypt or decrypt with SM4 CFB
sm4_ofb Encrypt or decrypt with SM4 OFB
sm4_ccm Encrypt or decrypt with SM4 CCM
sm4_gcm Encrypt or decrypt with SM4 GCM
sm4_xts Encrypt or decrypt with SM4 XTS
sm4_cbc_sm3_hmac Encrypt or decrypt with SM4 CBC with SM3-HMAC
sm4_ctr_sm3_hmac Encrypt or decrypt with SM4 CTR with SM3-HMAC
sm4_cbc_mac Generate SM4 CBC-MAC
ghash Generate GHASH
zuc Encrypt or decrypt with ZUC
sm9setup Generate SM9 master secret
sm9keygen Generate SM9 private key
sm9sign Generate SM9 signature
sm9verify Verify SM9 signature
sm9encrypt SM9 public key encryption
sm9decrypt SM9 decryption
reqgen Generate certificate signing request (CSR)
reqsign Generate certificate from CSR
reqparse Parse and print a CSR
crlget Download the CRL of given certificate
crlgen Sign a CRL with CA certificate and private key
crlverify Verify a CRL with issuer's certificate
crlparse Parse and print CRL
certgen Generate a self-signed certificate
certparse Parse and print certificates
certverify Verify certificate chain
certrevoke Revoke certificate and output RevokedCertificate record
cmsparse Parse CMS (cryptographic message syntax) file
cmsencrypt Generate CMS EnvelopedData
cmsdecrypt Decrypt CMS EnvelopedData
cmssign Generate CMS SignedData
cmsverify Verify CMS SignedData
sdfinfo Print SDF device info
sdfdigest Generate SM3 hash with SDF device
sdfexport Export SM2 signing public key from SDF device
sdfsign Generate SM2 signature with SDF internal private key
sdfencrypt SM2/SM4-CBC hybrid encryption with SDF device
sdfdecrypt SM2/SM4-CBC hybrid decryption with SDF device
sdftest Test vendor's SDF library and device
tlcp_client TLCP client
tlcp_server TLCP server
tls12_client TLS 1.2 client
tls12_server TLS 1.2 server
tls13_client TLS 1.3 client
tls13_server TLS 1.3 server
run `gmssl <command> -help` to print help of the given command
qzz@qzz-virtual-machine:~/command_history_repo$ $ gmssl rand -help
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl sm4
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl rand -help
usage: rand [-hex] [-rdrand|-rdseed] -outlen num [-out file]
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl rand -outlen 16 -out key.bin
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl rand -outlen 16 -out iv.bin
qzz@qzz-virtual-machine:~/command_history_repo$ ls
123.bin iv.bin ljpsm2dec.txt public_key.pem
123.txt key.bin ljpsm2enc.bin r1.bin
1.txt ljp2.txt ljpsm2.sig r2.bin
bitstring.der ljp.b64 ljp.sm3 sm2.pem
bitstring.pem ljprsadec.txt ljp.txt sm2private_key.der
ftr2.txt ljprsaenc.bin log_gm.log sm2private_key.pem
ftr.enc ljprsa.sig log_op.log sm2public_key.pem
ftr.txt ljp.sig private_key.pem sm2pub.pem
qzz@qzz-virtual-machine:~/command_history_repo$ od -tx1 key.bin
0000000 46 15 91 a9 87 81 c2 40 d9 6d da f3 b5 36 be 15
0000020
qzz@qzz-virtual-machine:~/command_history_repo$ od -tx1 iv.bin
0000000 3c 5a ba 03 26 2c 80 98 ca 7e c9 01 fa 84 45 7a
0000020
qzz@qzz-virtual-machine:~/command_history_repo$ echo -n "ljp" | gmssl sm4 -cbc -encrypt -key $(xxd -p -c 32 key.bin) -iv $(xxd -p -c 32 iv.bin) -out ljpsm4.cbc
gmssl: illegal option 'sm4'
usage: gmssl command [options]
command -help
Commands:
help Print this help message
version Print version
rand Generate random bytes
sm2keygen Generate SM2 keypair
sm2sign Generate SM2 signature
sm2verify Verify SM2 signature
sm2encrypt Encrypt with SM2 public key
sm2decrypt Decrypt with SM2 private key
sm3 Generate SM3 hash
sm3hmac Generate SM3 HMAC tag
sm3_pbkdf2 Hash password into key using PBKDF2 algoritm
sm3xmss_keygen Generate SM3-XMSS keypair
sm4_ecb Encrypt or decrypt with SM4 ECB
sm4_cbc Encrypt or decrypt with SM4 CBC
sm4_ctr Encrypt or decrypt with SM4 CTR
sm4_cfb Encrypt or decrypt with SM4 CFB
sm4_ofb Encrypt or decrypt with SM4 OFB
sm4_ccm Encrypt or decrypt with SM4 CCM
sm4_gcm Encrypt or decrypt with SM4 GCM
sm4_xts Encrypt or decrypt with SM4 XTS
sm4_cbc_sm3_hmac Encrypt or decrypt with SM4 CBC with SM3-HMAC
sm4_ctr_sm3_hmac Encrypt or decrypt with SM4 CTR with SM3-HMAC
sm4_cbc_mac Generate SM4 CBC-MAC
ghash Generate GHASH
zuc Encrypt or decrypt with ZUC
sm9setup Generate SM9 master secret
sm9keygen Generate SM9 private key
sm9sign Generate SM9 signature
sm9verify Verify SM9 signature
sm9encrypt SM9 public key encryption
sm9decrypt SM9 decryption
reqgen Generate certificate signing request (CSR)
reqsign Generate certificate from CSR
reqparse Parse and print a CSR
crlget Download the CRL of given certificate
crlgen Sign a CRL with CA certificate and private key
crlverify Verify a CRL with issuer's certificate
crlparse Parse and print CRL
certgen Generate a self-signed certificate
certparse Parse and print certificates
certverify Verify certificate chain
certrevoke Revoke certificate and output RevokedCertificate record
cmsparse Parse CMS (cryptographic message syntax) file
cmsencrypt Generate CMS EnvelopedData
cmsdecrypt Decrypt CMS EnvelopedData
cmssign Generate CMS SignedData
cmsverify Verify CMS SignedData
sdfinfo Print SDF device info
sdfdigest Generate SM3 hash with SDF device
sdfexport Export SM2 signing public key from SDF device
sdfsign Generate SM2 signature with SDF internal private key
sdfencrypt SM2/SM4-CBC hybrid encryption with SDF device
sdfdecrypt SM2/SM4-CBC hybrid decryption with SDF device
sdftest Test vendor's SDF library and device
tlcp_client TLCP client
tlcp_server TLCP server
tls12_client TLS 1.2 client
tls12_server TLS 1.2 server
tls13_client TLS 1.3 client
tls13_server TLS 1.3 server
run `gmssl <command> -help` to print help of the given command
qzz@qzz-virtual-machine:~/command_history_repo$ $ gmssl sm4 -cbc -decrypt -key $(xxd -p -c 32 key.bin) -iv $(xxd -p -c 32 iv.bin) -in ljpsm4.cbc
ljp
$: command not found
Command 'ljp' not found, did you mean:
command 'jp' from deb jp (0.1.3-3ubuntu0.1)
command 'lp' from deb cups-client (2.4.1op1-1ubuntu4.12)
command 'lp' from deb lprng (3.8.B-5)
command 'lgp' from deb simh (3.8.1-6.1)
command 'lmp' from deb lammps (20220106.git7586adbb6a+ds1-2)
command 'lcp' from deb lsh-client (2.1-13)
Try: sudo apt install <deb name>
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl sm4 -cbc -decrypt -key $(xxd -p -c 32 key.bin) -iv $(xxd -p -c 32 iv.bin) -in ljpsm4.cbc
ljp
gmssl: illegal option 'sm4'
usage: gmssl command [options]
command -help
Commands:
help Print this help message
version Print version
rand Generate random bytes
sm2keygen Generate SM2 keypair
sm2sign Generate SM2 signature
sm2verify Verify SM2 signature
sm2encrypt Encrypt with SM2 public key
sm2decrypt Decrypt with SM2 private key
sm3 Generate SM3 hash
sm3hmac Generate SM3 HMAC tag
sm3_pbkdf2 Hash password into key using PBKDF2 algoritm
sm3xmss_keygen Generate SM3-XMSS keypair
sm4_ecb Encrypt or decrypt with SM4 ECB
sm4_cbc Encrypt or decrypt with SM4 CBC
sm4_ctr Encrypt or decrypt with SM4 CTR
sm4_cfb Encrypt or decrypt with SM4 CFB
sm4_ofb Encrypt or decrypt with SM4 OFB
sm4_ccm Encrypt or decrypt with SM4 CCM
sm4_gcm Encrypt or decrypt with SM4 GCM
sm4_xts Encrypt or decrypt with SM4 XTS
sm4_cbc_sm3_hmac Encrypt or decrypt with SM4 CBC with SM3-HMAC
sm4_ctr_sm3_hmac Encrypt or decrypt with SM4 CTR with SM3-HMAC
sm4_cbc_mac Generate SM4 CBC-MAC
ghash Generate GHASH
zuc Encrypt or decrypt with ZUC
sm9setup Generate SM9 master secret
sm9keygen Generate SM9 private key
sm9sign Generate SM9 signature
sm9verify Verify SM9 signature
sm9encrypt SM9 public key encryption
sm9decrypt SM9 decryption
reqgen Generate certificate signing request (CSR)
reqsign Generate certificate from CSR
reqparse Parse and print a CSR
crlget Download the CRL of given certificate
crlgen Sign a CRL with CA certificate and private key
crlverify Verify a CRL with issuer's certificate
crlparse Parse and print CRL
certgen Generate a self-signed certificate
certparse Parse and print certificates
certverify Verify certificate chain
certrevoke Revoke certificate and output RevokedCertificate record
cmsparse Parse CMS (cryptographic message syntax) file
cmsencrypt Generate CMS EnvelopedData
cmsdecrypt Decrypt CMS EnvelopedData
cmssign Generate CMS SignedData
cmsverify Verify CMS SignedData
sdfinfo Print SDF device info
sdfdigest Generate SM3 hash with SDF device
sdfexport Export SM2 signing public key from SDF device
sdfsign Generate SM2 signature with SDF internal private key
sdfencrypt SM2/SM4-CBC hybrid encryption with SDF device
sdfdecrypt SM2/SM4-CBC hybrid decryption with SDF device
sdftest Test vendor's SDF library and device
tlcp_client TLCP client
tlcp_server TLCP server
tls12_client TLS 1.2 client
tls12_server TLS 1.2 server
tls13_client TLS 1.3 client
tls13_server TLS 1.3 server
run `gmssl <command> -help` to print help of the given command
Command 'ljp' not found, did you mean:
command 'lcp' from deb lsh-client (2.1-13)
command 'lp' from deb cups-client (2.4.1op1-1ubuntu4.12)
command 'lp' from deb lprng (3.8.B-5)
command 'jp' from deb jp (0.1.3-3ubuntu0.1)
command 'lgp' from deb simh (3.8.1-6.1)
command 'lmp' from deb lammps (20220106.git7586adbb6a+ds1-2)
Try: sudo apt install <deb name>
qzz@qzz-virtual-machine:~/command_history_repo$ KEY=$(xxd -p -c 32 key.bin)
qzz@qzz-virtual-machine:~/command_history_repo$ echo $KEY
461591a98781c240d96ddaf3b536be15
qzz@qzz-virtual-machine:~/command_history_repo$ IV=$(xxd -p -c 32 iv.bin)
qzz@qzz-virtual-machine:~/command_history_repo$ echo $IV
3c5aba03262c8098ca7ec901fa84457a
qzz@qzz-virtual-machine:~/command_history_repo$ echo -n "ljp" | gmssl sm4 -cbc -encrypt -key $KEY -iv $IV -out ljpsm4.cbc2
gmssl: illegal option 'sm4'
usage: gmssl command [options]
command -help
Commands:
help Print this help message
version Print version
rand Generate random bytes
sm2keygen Generate SM2 keypair
sm2sign Generate SM2 signature
sm2verify Verify SM2 signature
sm2encrypt Encrypt with SM2 public key
sm2decrypt Decrypt with SM2 private key
sm3 Generate SM3 hash
sm3hmac Generate SM3 HMAC tag
sm3_pbkdf2 Hash password into key using PBKDF2 algoritm
sm3xmss_keygen Generate SM3-XMSS keypair
sm4_ecb Encrypt or decrypt with SM4 ECB
sm4_cbc Encrypt or decrypt with SM4 CBC
sm4_ctr Encrypt or decrypt with SM4 CTR
sm4_cfb Encrypt or decrypt with SM4 CFB
sm4_ofb Encrypt or decrypt with SM4 OFB
sm4_ccm Encrypt or decrypt with SM4 CCM
sm4_gcm Encrypt or decrypt with SM4 GCM
sm4_xts Encrypt or decrypt with SM4 XTS
sm4_cbc_sm3_hmac Encrypt or decrypt with SM4 CBC with SM3-HMAC
sm4_ctr_sm3_hmac Encrypt or decrypt with SM4 CTR with SM3-HMAC
sm4_cbc_mac Generate SM4 CBC-MAC
ghash Generate GHASH
zuc Encrypt or decrypt with ZUC
sm9setup Generate SM9 master secret
sm9keygen Generate SM9 private key
sm9sign Generate SM9 signature
sm9verify Verify SM9 signature
sm9encrypt SM9 public key encryption
sm9decrypt SM9 decryption
reqgen Generate certificate signing request (CSR)
reqsign Generate certificate from CSR
reqparse Parse and print a CSR
crlget Download the CRL of given certificate
crlgen Sign a CRL with CA certificate and private key
crlverify Verify a CRL with issuer's certificate
crlparse Parse and print CRL
certgen Generate a self-signed certificate
certparse Parse and print certificates
certverify Verify certificate chain
certrevoke Revoke certificate and output RevokedCertificate record
cmsparse Parse CMS (cryptographic message syntax) file
cmsencrypt Generate CMS EnvelopedData
cmsdecrypt Decrypt CMS EnvelopedData
cmssign Generate CMS SignedData
cmsverify Verify CMS SignedData
sdfinfo Print SDF device info
sdfdigest Generate SM3 hash with SDF device
sdfexport Export SM2 signing public key from SDF device
sdfsign Generate SM2 signature with SDF internal private key
sdfencrypt SM2/SM4-CBC hybrid encryption with SDF device
sdfdecrypt SM2/SM4-CBC hybrid decryption with SDF device
sdftest Test vendor's SDF library and device
tlcp_client TLCP client
tlcp_server TLCP server
tls12_client TLS 1.2 client
tls12_server TLS 1.2 server
tls13_client TLS 1.3 client
tls13_server TLS 1.3 server
run `gmssl <command> -help` to print help of the given command
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl sm4 -cbc -decrypt -key $KEY -iv $IV -in ljpsm4.cbc2
gmssl: illegal option 'sm4'
usage: gmssl command [options]
command -help
Commands:
help Print this help message
version Print version
rand Generate random bytes
sm2keygen Generate SM2 keypair
sm2sign Generate SM2 signature
sm2verify Verify SM2 signature
sm2encrypt Encrypt with SM2 public key
sm2decrypt Decrypt with SM2 private key
sm3 Generate SM3 hash
sm3hmac Generate SM3 HMAC tag
sm3_pbkdf2 Hash password into key using PBKDF2 algoritm
sm3xmss_keygen Generate SM3-XMSS keypair
sm4_ecb Encrypt or decrypt with SM4 ECB
sm4_cbc Encrypt or decrypt with SM4 CBC
sm4_ctr Encrypt or decrypt with SM4 CTR
sm4_cfb Encrypt or decrypt with SM4 CFB
sm4_ofb Encrypt or decrypt with SM4 OFB
sm4_ccm Encrypt or decrypt with SM4 CCM
sm4_gcm Encrypt or decrypt with SM4 GCM
sm4_xts Encrypt or decrypt with SM4 XTS
sm4_cbc_sm3_hmac Encrypt or decrypt with SM4 CBC with SM3-HMAC
sm4_ctr_sm3_hmac Encrypt or decrypt with SM4 CTR with SM3-HMAC
sm4_cbc_mac Generate SM4 CBC-MAC
ghash Generate GHASH
zuc Encrypt or decrypt with ZUC
sm9setup Generate SM9 master secret
sm9keygen Generate SM9 private key
sm9sign Generate SM9 signature
sm9verify Verify SM9 signature
sm9encrypt SM9 public key encryption
sm9decrypt SM9 decryption
reqgen Generate certificate signing request (CSR)
reqsign Generate certificate from CSR
reqparse Parse and print a CSR
crlget Download the CRL of given certificate
crlgen Sign a CRL with CA certificate and private key
crlverify Verify a CRL with issuer's certificate
crlparse Parse and print CRL
certgen Generate a self-signed certificate
certparse Parse and print certificates
certverify Verify certificate chain
certrevoke Revoke certificate and output RevokedCertificate record
cmsparse Parse CMS (cryptographic message syntax) file
cmsencrypt Generate CMS EnvelopedData
cmsdecrypt Decrypt CMS EnvelopedData
cmssign Generate CMS SignedData
cmsverify Verify CMS SignedData
sdfinfo Print SDF device info
sdfdigest Generate SM3 hash with SDF device
sdfexport Export SM2 signing public key from SDF device
sdfsign Generate SM2 signature with SDF internal private key
sdfencrypt SM2/SM4-CBC hybrid encryption with SDF device
sdfdecrypt SM2/SM4-CBC hybrid decryption with SDF device
sdftest Test vendor's SDF library and device
tlcp_client TLCP client
tlcp_server TLCP server
tls12_client TLS 1.2 client
tls12_server TLS 1.2 server
tls13_client TLS 1.3 client
tls13_server TLS 1.3 server
run `gmssl <command> -help` to print help of the given command
qzz@qzz-virtual-machine:~/command_history_repo$ diff ljpsm4.cbc ljpsm4.cbc2
diff: ljpsm4.cbc: No such file or directory
diff: ljpsm4.cbc2: No such file or directory
qzz@qzz-virtual-machine:~/command_history_repo$ echo -n "ljp" | gmssl sm4_cbc -encrypt -key $(xxd -p -c 32 key.bin) -iv $(xxd -p -c 32 iv.bin) -out ljpsm4.cbc
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl sm4_cbc -decrypt -key $(xxd -p -c 32 key.bin) -iv $(xxd -p -c 32 iv.bin) -in ljpsm4.cbc
qzz@qzz-virtual-machine:~/command_history_repo$ echo -n "ljp" | gmssl sm4_cbc -encrypt -key $KEY -iv $IV -out ljpsm4.cbc2bc2
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl sm4_cbc -decrypt -key $KEY -iv $IV -in ljpsm4.cbc2
ljpqzz@qzz-virtual-machine:~/command_history_repo$ diff ljpsm4.cbc ljpsm4.cbc2
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl sm4_cbc -encrypt -key $(xxd -p -c 32 key.bin) -iv $(xxd -p -c 32 iv.bin) -in ljp.txt -out ljpsm4.cbc3
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl sm4_cbc -decrypt -key $(xxd -p -c 32 key.bin) -iv $(xxd -p -c 32 iv.bin) -in ljpsm4.cbc3
ljpqzz@qzz-virtual-machine:~/command_history_repo$ diff ljpsm4.cbc ljpsm4.cbc3
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl sm2keygen -pass 1234 -out sm2.pem -pubout sm2pub.pem
qzz@qzz-virtual-machine:~/command_history_repo$ cat sm2.pem
-----BEGIN ENCRYPTED PRIVATE KEY-----
MIIBBjBhBgkqhkiG9w0BBQ0wVDA0BgkqhkiG9w0BBQwwJwQQEwkDLMILI5JFOPVt
OmKd+AIDAQAAAgEQMAsGCSqBHM9VAYMRAjAcBggqgRzPVQFoAgQQPp9v7aXrmqhA
z+8ZDk6VywSBoC9WkZz++E+JK56RE0FTl6hlEnGBSR/8LVnS/FjmxtkxnXcQsgDt
zd83oaNoL6gtC/vyPSNecZALkYWa8V62RUoHfV+5RwNC0C0mBa8hW1puhVxqca5N
5rrNqajB+40AMW4s2yHTz9ZotFhpqwbLZyq600K5xPiiBRRryzxa3QoQDhQAtz2R
k3y+ZP0nHuQAV00di7YalYLJEmTyqqY0P9k=
-----END ENCRYPTED PRIVATE KEY-----
qzz@qzz-virtual-machine:~/command_history_repo$ cat sm2pub.pem
-----BEGIN PUBLIC KEY-----
MFkwEwYHKoZIzj0CAQYIKoEcz1UBgi0DQgAEfO2tIPOl4+ru/AOxqEHIR58R9WjL
iCcwdUAJGBvvxDoCz2tIbjG+PP+btOFzxTBPKJ5uY2AzL15innuHwltGXw==
-----END PUBLIC KEY-----
qzz@qzz-virtual-machine:~/command_history_repo$ echo ljp | gmssl sm2sign -key sm2.pem -pass 1234 -out sm2.sig #-id 1234567812345678
qzz@qzz-virtual-machine:~/command_history_repo$ od -tx1 sm2.sig
0000000 30 44 02 20 0b 55 9e 6d e3 3e 28 c6 9e 87 12 49
0000020 b4 0a aa a3 20 05 79 41 f5 6d 0f 80 cc bf f1 98
0000040 d4 ae 58 36 02 20 69 59 57 d3 5a 8f eb 27 f8 96
0000060 c7 d8 9e 12 4c df 94 2d 8f 5c 37 54 9c 9d 20 bf
0000100 ba da 9f eb f4 5a
0000106
qzz@qzz-virtual-machine:~/command_history_repo$ echo ljp | gmssl sm2verify -pubkey sm2pub.pem -sig sm2.sig -id 1234567812345678
verify : success
qzz@qzz-virtual-machine:~/command_history_repo$ echo ljp | gmssl sm2encrypt -pubkey sm2pub.pem -out sm2.der
qzz@qzz-virtual-machine:~/command_history_repo$ od -tx1 sm2.der
0000000 30 6d 02 21 00 d6 8b 6c 19 79 33 d6 c7 46 97 50
0000020 e6 6a e6 aa 9e 28 d7 1d 0c 01 6c 49 61 d9 27 d4
0000040 85 23 34 b8 cd 02 20 77 c8 cd fc 5d 87 8a 38 f7
0000060 73 f9 98 38 ad 70 19 b3 47 6a d3 6f 96 d4 e2 00
0000100 61 7d 7b f2 c5 3d 8f 04 20 45 67 bf 6e c1 bc 1b
0000120 8a 26 9a 57 af 0c 17 ad 47 ed f0 26 71 ca a8 76
0000140 32 2e c3 cb 1b d2 65 6e 42 04 04 29 08 ca 11
0000157
qzz@qzz-virtual-machine:~/command_history_repo$ gmssl sm2decrypt -key sm2.pem -pass 1234 -in sm2.der
ljp
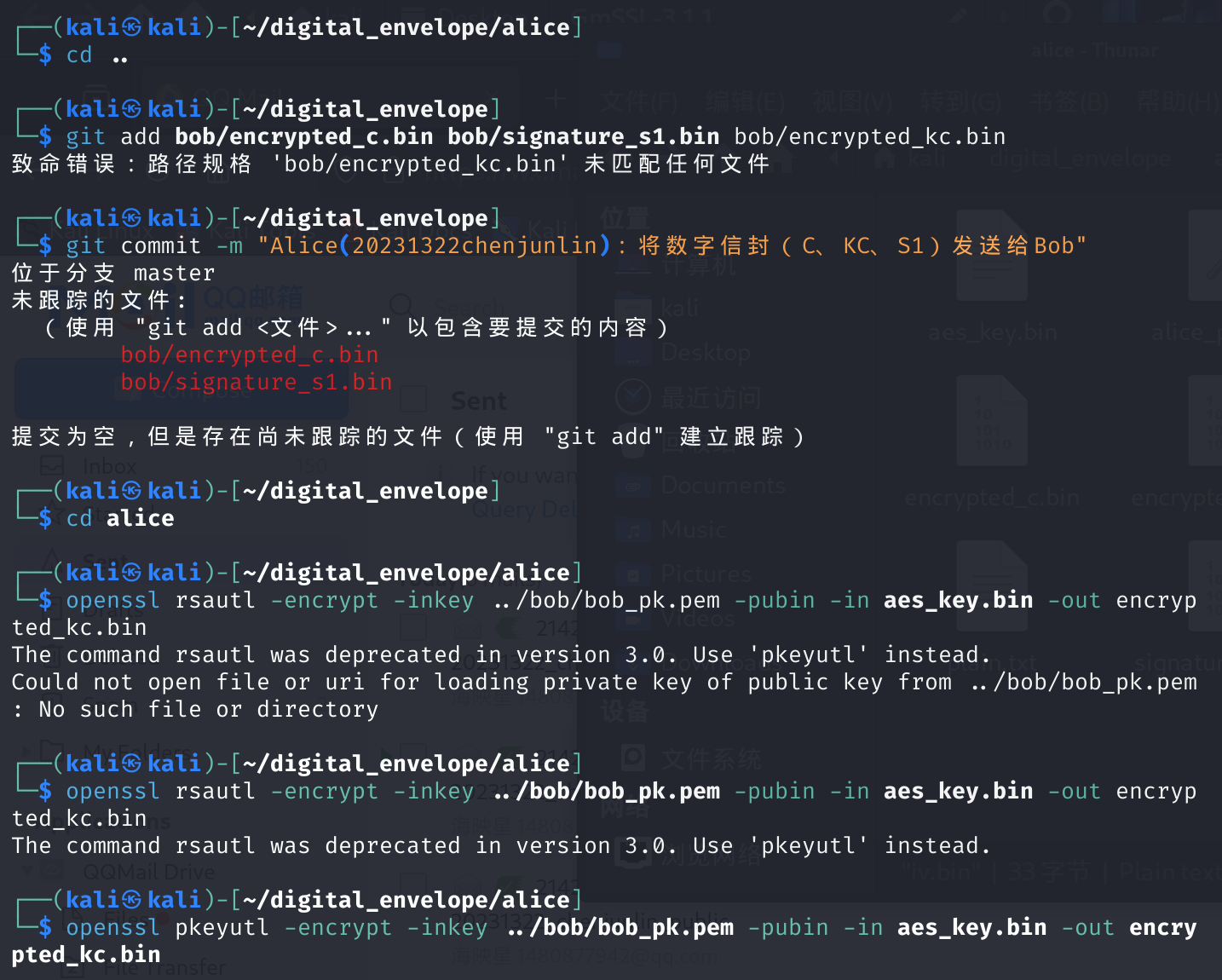
3.兩人一組,在Ubuntu或openEuler中(推薦openEuler)中使用OpenSSL命令實(shí)現(xiàn)帶簽名的數(shù)字信封協(xié)議。使用OpenSSL時(shí)Alice發(fā)送,Bob接收。Ailice,Bob在實(shí)驗(yàn)中要替換為自己的8位學(xué)號(hào)+姓名。使用Markdown記錄詳細(xì)記錄實(shí)踐過程,每完成一項(xiàng)gitcommit一次。(10分)
- Alice,Bob生成自己的公私鑰匙對(duì),記作:(PKa,SKa),(PKb,SKb),Alice,Bob分別擁有:(PKa,SKa,PKb),(PKb,SKb,PKa),實(shí)驗(yàn)中把公鑰文件拷?給對(duì)方
- Alice發(fā)給Bob的明文plain.txt,內(nèi)容為自己的姓名學(xué)號(hào)
- Alice:sm4key使用gmsslrand產(chǎn)生,16字節(jié),記作k
- Alice:Sm4Enc(k,P)= C
- Alice:Sm2Enc(PKb,k)= KC
- Alice:Sm2Sign(SKa,C)= S1
- Alice:數(shù)字信封 C||KC||S1發(fā)給Bob
- Bob:Sm2Very(PKa,S1)
- Bob:Sm2Dec(SKb,KC)=k
- Bob:Sm4Dec(k,C)= P
![c97bd702080380bc6a987876815aeb29]()





4.兩人一組,在Ubuntu或openEuler中(推薦openEuler)中使用GmSSL命令實(shí)現(xiàn)帶簽名的數(shù)字信封協(xié)議。使用GmSSL,Bob發(fā)送,Alice接收。Ailice,Bob在實(shí)驗(yàn)中要替換為自己的8位學(xué)號(hào)+姓名。使用Markdown記錄詳細(xì)記錄實(shí)踐過程,每完成一項(xiàng)gitcommit一次。(10分)



提交運(yùn)行命令,已托管到git




 浙公網(wǎng)安備 33010602011771號(hào)
浙公網(wǎng)安備 33010602011771號(hào)