wargames bandit 一部分
wargames
bandit
L0-1
bandit0@bandit:~$ ls
readme
bandit0@bandit:~$ cat readme
boJ9jbbUNNfktd78OOpsqOltutMc3MY1
L1-2
“-"是linux參數(shù)的開頭,使用。/指定當(dāng)前目錄
bandit1@bandit:~$ ls
-
bandit1@bandit:~$ cat ./-
CV1DtqXWVFXTvM2F0k09SHz0YwRINYA9
L2-3
文件名中帶空格會(huì)識(shí)別為多個(gè)文件,使用雙引號(hào)
bandit2@bandit:~$ ls
spaces in this filename
bandit2@bandit:~$ cat "spaces in this filename"
UmHadQclWmgdLOKQ3YNgjWxGoRMb5luK
L3-4
linux中”.“開頭的文件和目錄會(huì)隱藏
bandit3@bandit:~$ ls
inhere
bandit3@bandit:~$ cat inhere/
cat: inhere/: Is a directory
bandit3@bandit:~$ cd inhere/
bandit3@bandit:~/inhere$ ls
bandit3@bandit:~/inhere$ ls -a
. .. .hidden
bandit3@bandit:~/inhere$ cat .hidden
pIwrPrtPN36QITSp3EQaw936yaFoFgAB
L4-5
使用命令:file ./* 查看當(dāng)前目錄下的所有文件類型
bandit4@bandit:~$ cd inhere/
bandit4@bandit:~/inhere$ ls
-file00 -file01 -file02 -file03 -file04 -file05 -file06 -file07 -file08 -file09
bandit4@bandit:~/inhere$ file ./*
./-file00: data
./-file01: data
./-file02: data
./-file03: data
./-file04: data
./-file05: data
./-file06: data
./-file07: ASCII text
./-file08: data
./-file09: data
bandit4@bandit:~/inhere$ cat ./-file07
koReBOKuIDDepwhWk7jZC0RTdopnAYKh
bandit4@bandit:~/inhere$
L5-6
find
- -size:文件大小,1033c,b代表512位元組的區(qū)塊,c是子元數(shù),k是kilo bytes ,我是二個(gè)位元組
- -type:文件類型,d目錄,f一般文件,l連接符號(hào),s socket, c字型裝置文件,b:區(qū)塊裝置文件,p:具名貯列
bandit5@bandit:~$ ls -a
. .. .bash_logout .bashrc inhere .profile
bandit5@bandit:~$ cd inhere/
bandit5@bandit:~/inhere$ ls -a
. maybehere02 maybehere06 maybehere10 maybehere14 maybehere18
.. maybehere03 maybehere07 maybehere11 maybehere15 maybehere19
maybehere00 maybehere04 maybehere08 maybehere12 maybehere16
maybehere01 maybehere05 maybehere09 maybehere13 maybehere17
bandit5@bandit:~/inhere$ find ./ -tupe f -size 1033c
find: unknown predicate `-tupe'
Try 'find --help' for more information.
bandit5@bandit:~/inhere$ find ./ -type f -size 1033c
./maybehere07/.file2
bandit5@bandit:~/inhere$ cat ./maybehere07/.file2
DXjZPULLxYr17uwoI01bNLQbtFemEgo7
L6-7
提示信息,
2>/dev/null,linux在根目錄下查找會(huì)有很多權(quán)限的報(bào)錯(cuò)信息,使用這種方法將報(bào)錯(cuò)信息重定向

bandit6@bandit:~$ ls
bandit6@bandit:~$ find / -user bandit7 -group bandit6 -size 33c 2>/dev/null
/var/lib/dpkg/info/bandit7.password
bandit6@bandit:~$ cat /var/lib/dpkg/info/bandit7.password
HKBPTKQnIay4Fw76bEy8PVxKEDQRKTzs
L7-8
使用grep命令查找文件里符合條件的字符串
bandit7@bandit:~$ ls
data.txt
bandit7@bandit:~$ cat data.txt |grep millionth
millionth cvX2JJa4CFALtqS87jk27qwqGhBM9plV
L8-9
- sort:將文件每一行作為一個(gè)單位,相互比較,從首字符開始,一次按照ascii比較
- -u,輸出行中去除重復(fù)行
- -r,sort默認(rèn)排序是升序,-r是降序
- -o,排序結(jié)果輸出到原文件
- -n,按照數(shù)值排序,不會(huì)出現(xiàn)1,11,10這種,而是1,10,11
- -f,小寫字母轉(zhuǎn)換成大寫字母進(jìn)行排序,忽略大小寫
- uniq:可以去除排序過的文件中重復(fù)行
- -d,只顯示有重復(fù)的記錄,每個(gè)重復(fù)記錄出現(xiàn)一次
- -c,打印每行在文本中出現(xiàn)的次數(shù)
- -u,只顯示沒有重復(fù)的記錄
bandit8@bandit:~$ ls
data.txt
bandit8@bandit:~$ sort data.txt |uniq -u
UsvVyFSfZZWbi6wgC7dAFyFuR6jQQUhR
L9-10
-
string:用于打印文件中可打印的字符串
bandit9@bandit:~$ ls
data.txt
bandit9@bandit:~$ strings data.txt|grep "="
========== the*2i"4
=:G e
========== password
<I=zsGi
Z)========== is
A=|t&E
Zdb=
c^ LAh=3G
*SF=s
&========== truKLdjsbJ5g7yyJ2X2R0o3a5HQJFuLk
S=A.H&^
L10-11
-
base64:編碼
- -d,解碼
- -i,解碼時(shí)忽略非字母字符
bandit10@bandit:~$ ls
data.txt
bandit10@bandit:~$ base64 -d
.bash_logout .bashrc data.txt .profile
bandit10@bandit:~$ base64 -d data.txt
The password is IFukwKGsFW8MOq3IRFqrxE1hxTNEbUPR
bandit10@bandit:~$
L11-12
- rot13:相當(dāng)于前13個(gè)字母和后13個(gè)字母的順序進(jìn)行了調(diào)換
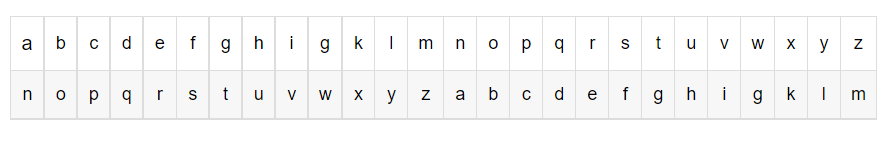
-
tr:可以對(duì)來自標(biāo)準(zhǔn)輸入的字符進(jìn)行替換,壓縮,刪除
echo "HELLO WORLD" | tr 'A-Z' 'a-z' hello world #替換
bandit11@bandit:~$ ls
data.txt
bandit11@bandit:~$ cat data.txt |tr 'a-zA-Z' 'n-za-mN-ZA-M'
The password is 5Te8Y4drgCRfCx8ugdwuEX8KFC6k2EUu
L12-13
-
file命令:用來識(shí)別文件類型,也可以識(shí)別編碼格式,通過文件的頭部信息,獲取文件類型
- -i,顯示mime類別
-
xxd:任意文件轉(zhuǎn)換為2進(jìn)制或者16進(jìn)制的形式
- -b,二進(jìn)制模式,這種模式下每個(gè)字符都是8個(gè)0/1,-r,-p在這個(gè)模式不起作用
- -r,把16進(jìn)制輸出的內(nèi)容轉(zhuǎn)換為原來的二進(jìn)制文件
- -p,以 postscript的連續(xù)十六進(jìn)制轉(zhuǎn)儲(chǔ)輸出,這也叫做純十六進(jìn)制轉(zhuǎn)儲(chǔ)
- -u,用大寫字母進(jìn)行輸出,默認(rèn)是小寫字母
-
.bin:萬能后綴
-
bunzip2:
-
gizp:壓縮程序,后綴.gz,對(duì)文本文件有%60-%70的壓縮率
- -d,解開壓縮文件
- -r,遞歸處理,將指定文件夾下的所有文件和子目錄,一并處理
- -l,列出壓縮文件相關(guān)信息
- -c,壓縮后的文件輸出到標(biāo)準(zhǔn)輸出設(shè)備,不改動(dòng)原文件
-
bzip2:用于創(chuàng)建和管理(解壓縮).bz2格式的壓縮包
- -z強(qiáng)制壓縮,壓縮指定文件,bzip2 filename或bzip2 -zfilename
- -d強(qiáng)制解壓縮,解壓指定文件,bzip2 -d filename.bz2或bzip2 filename.bz2
- -v,解壓縮的時(shí)候?qū)⒔Y(jié)果也輸出
- -k,保留輸入文件
-
tar:
# 查看
tar -tf aaa.tar.gz #不解壓的情況下,查看壓縮包內(nèi)容
# 壓縮
tar -cvf jpg.tar *.jpg #將目錄里所有jpg文件打包jpg.tar
tar -czf jpg.tar.gz *.jpg #將目錄里的所有jpg文件打包jpg.tar后,用gzip壓縮,命名jpg.tar.gz
tar -cjf jpg.tar.bz2 *.jpg#將所有的jpg文件打包后,用bzip2打包
tar -cZf jpg.tar.Z *.jpg # 所有的jpg文件打包,使用compress壓縮,生成一個(gè)umcompress壓縮過的包
#解壓
tar -xvf file.tar #解壓tar包
tar -xzvf file.tar.gz #解壓tar.gz
tar -xjvf file.tar.bz2# 解壓tar.bz2
tar -xZvf file.tar.Z #解壓tar.Z

bandit12@bandit:~$ ls
data.txt
bandit12@bandit:~$
bandit12@bandit:~$ mkdir /tmp/mm
bandit12@bandit:~$ cp data.txt /tmp/mm
bandit12@bandit:~$ cd /tmp/mm
bandit12@bandit:/tmp/mm$ ls
data.txt
bandit12@bandit:/tmp/mm$ xxd -r data.txt > data.bin
bandit12@bandit:/tmp/mm$ ls
data.bin data.txt
bandit12@bandit:/tmp/mm$ file data.bin
data.bin: gzip compressed data, was "data2.bin", last modified: Thu May 7 18:14:30 2020, max compression, from Unix
bandit12@bandit:/tmp/mm$ mv data.bin data.gz
bandit12@bandit:/tmp/mm$ gzip -d data.gz
bandit12@bandit:/tmp/mm$ file data
data: bzip2 compressed data, block size = 900k
bandit12@bandit:/tmp/mm$ mv data data.bz2
bandit12@bandit:/tmp/mm$ bzip -d data.bz2
-bash: bzip: command not found
bandit12@bandit:/tmp/mm$ bunzip2 -d data.bz2
bandit12@bandit:/tmp/mm$ file data
data: gzip compressed data, was "data4.bin", last modified: Thu May 7 18:14:30 2020, max compression, from Unix
bandit12@bandit:/tmp/mm$ mv data data.gz
bandit12@bandit:/tmp/mm$ gzip -d data.gz
bandit12@bandit:/tmp/mm$ file data
data: POSIX tar archive (GNU)
bandit12@bandit:/tmp/mm$ mv data data.tar
bandit12@bandit:/tmp/mm$ tar -xvf data.tar
data5.bin
bandit12@bandit:/tmp/mm$ file data5.bin
data5.bin: POSIX tar archive (GNU)
bandit12@bandit:/tmp/mm$ mv data5.bin data5.tar
bandit12@bandit:/tmp/mm$ tar -xvf data5.tar
data6.bin
bandit12@bandit:/tmp/mm$ file data6.bin
data6.bin: bzip2 compressed data, block size = 900k
bandit12@bandit:/tmp/mm$ mv data6.bin data6.bz2
bandit12@bandit:/tmp/mm$ bunzip2 -d data6.bz2
bandit12@bandit:/tmp/mm$ file data
data: cannot open `data' (No such file or directory)
bandit12@bandit:/tmp/mm$ file data6
data6: POSIX tar archive (GNU)
bandit12@bandit:/tmp/mm$ mv data6 data6.tar
bandit12@bandit:/tmp/mm$ tar -xvf data6.tar
data8.bin
bandit12@bandit:/tmp/mm$ file data8
data8: cannot open `data8' (No such file or directory)
bandit12@bandit:/tmp/mm$ file data8.bin
data8.bin: gzip compressed data, was "data9.bin", last modified: Thu May 7 18:14:30 2020, max compression, from Unix
bandit12@bandit:/tmp/mm$ mv data8.bin data8.gz
bandit12@bandit:/tmp/mm$ gzip -d data8.gz
bandit12@bandit:/tmp/mm$ ls
data5.tar data6.tar data8 data.tar data.txt
bandit12@bandit:/tmp/mm$ cat data8
The password is 8ZjyCRiBWFYkneahHwxCv3wb2a1ORpYL
L13-14
ssh:
- ssh -i sshkey.private bandit14@127.0.0.1,使用私鑰文件
bandit13@bandit:~$ ssh -i sshkey.private bandit14@127.0.0.1
bandit14@bandit:~$ cat /etc/bandit_pass/bandit14
4wcYUJFw0k0XLShlDzztnTBHiqxU3b3e
L14-15
- telnet
- nc
bandit14@bandit:~$ telnet localhost 30000
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
^
Wrong! Please enter the correct current password
Connection closed by foreign host.
bandit14@bandit:~$ telnet localhost 30000
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
4wcYUJFw0k0XLShlDzztnTBHiqxU3b3e
Correct!
BfMYroe26WYalil77FoDi9qh59eK5xNr
bandit14@bandit:~$ nc localhost 30000
4wcYUJFw0k0XLShlDzztnTBHiqxU3b3e
Correct!
BfMYroe26WYalil77FoDi9qh59eK5xNr
L15-16
- ncat
bandit15@bandit:~$ ncat --ssl localhost 30001
BfMYroe26WYalil77FoDi9qh59eK5xNr
Correct!
cluFn7wTiGryunymYOu4RcffSxQluehd
L16-17
- ssh密鑰權(quán)限
bandit16@bandit:~$ nmap -sV localhost -p 31000-32000
Starting Nmap 7.40 ( https://nmap.org ) at 2022-03-28 10:26 CEST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.00024s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
31046/tcp open echo
31518/tcp open ssl/echo
31691/tcp open echo
31790/tcp open ssl/unknown
31960/tcp open echo
# 根據(jù)提示使用nmap掃描端口識(shí)別服務(wù)
bandit16@bandit:~$ ncat --ssl localhost 31518
cluFn7wTiGryunymYOu4RcffSxQluehd
cluFn7wTiGryunymYOu4RcffSxQluehd
bandit16@bandit:~$ ncat --ssl localhost 31790
cluFn7wTiGryunymYOu4RcffSxQluehd
Correct!
# 測(cè)試31790端口,返回一段ssh密鑰
-----BEGIN RSA PRIVATE KEY-----
MIIEogIBAAKCAQEAvmOkuifmMg6HL2YPIOjon6iWfbp7c3jx34YkYWqUH57SUdyJ
imZzeyGC0gtZPGujUSxiJSWI/oTqexh+cAMTSMlOJf7+BrJObArnxd9Y7YT2bRPQ
Ja6Lzb558YW3FZl87ORiO+rW4LCDCNd2lUvLE/GL2GWyuKN0K5iCd5TbtJzEkQTu
DSt2mcNn4rhAL+JFr56o4T6z8WWAW18BR6yGrMq7Q/kALHYW3OekePQAzL0VUYbW
JGTi65CxbCnzc/w4+mqQyvmzpWtMAzJTzAzQxNbkR2MBGySxDLrjg0LWN6sK7wNX
x0YVztz/zbIkPjfkU1jHS+9EbVNj+D1XFOJuaQIDAQABAoIBABagpxpM1aoLWfvD
KHcj10nqcoBc4oE11aFYQwik7xfW+24pRNuDE6SFthOar69jp5RlLwD1NhPx3iBl
J9nOM8OJ0VToum43UOS8YxF8WwhXriYGnc1sskbwpXOUDc9uX4+UESzH22P29ovd
d8WErY0gPxun8pbJLmxkAtWNhpMvfe0050vk9TL5wqbu9AlbssgTcCXkMQnPw9nC
YNN6DDP2lbcBrvgT9YCNL6C+ZKufD52yOQ9qOkwFTEQpjtF4uNtJom+asvlpmS8A
vLY9r60wYSvmZhNqBUrj7lyCtXMIu1kkd4w7F77k+DjHoAXyxcUp1DGL51sOmama
+TOWWgECgYEA8JtPxP0GRJ+IQkX262jM3dEIkza8ky5moIwUqYdsx0NxHgRRhORT
8c8hAuRBb2G82so8vUHk/fur85OEfc9TncnCY2crpoqsghifKLxrLgtT+qDpfZnx
SatLdt8GfQ85yA7hnWWJ2MxF3NaeSDm75Lsm+tBbAiyc9P2jGRNtMSkCgYEAypHd
HCctNi/FwjulhttFx/rHYKhLidZDFYeiE/v45bN4yFm8x7R/b0iE7KaszX+Exdvt
SghaTdcG0Knyw1bpJVyusavPzpaJMjdJ6tcFhVAbAjm7enCIvGCSx+X3l5SiWg0A
R57hJglezIiVjv3aGwHwvlZvtszK6zV6oXFAu0ECgYAbjo46T4hyP5tJi93V5HDi
Ttiek7xRVxUl+iU7rWkGAXFpMLFteQEsRr7PJ/lemmEY5eTDAFMLy9FL2m9oQWCg
R8VdwSk8r9FGLS+9aKcV5PI/WEKlwgXinB3OhYimtiG2Cg5JCqIZFHxD6MjEGOiu
L8ktHMPvodBwNsSBULpG0QKBgBAplTfC1HOnWiMGOU3KPwYWt0O6CdTkmJOmL8Ni
blh9elyZ9FsGxsgtRBXRsqXuz7wtsQAgLHxbdLq/ZJQ7YfzOKU4ZxEnabvXnvWkU
YOdjHdSOoKvDQNWu6ucyLRAWFuISeXw9a/9p7ftpxm0TSgyvmfLF2MIAEwyzRqaM
77pBAoGAMmjmIJdjp+Ez8duyn3ieo36yrttF5NSsJLAbxFpdlc1gvtGCWW+9Cq0b
dxviW8+TFVEBl1O4f7HVm6EpTscdDxU+bCXWkfjuRb7Dy9GOtt9JPsX8MBTakzh3
vBgsyi/sN3RqRBcGU40fOoZyfAMT8s1m/uYv52O6IgeuZ/ujbjY=
-----END RSA PRIVATE KEY-----
bandit16@bandit:~$ mkdir /tmp/y
bandit16@bandit:~$ cd /tmp/y
bandit16@bandit:/tmp/y$ touch 1.priv
bandit16@bandit:/tmp/y$ vim 1.priv
bandit16@bandit:/tmp/y$ vim 1.priv
bandit16@bandit:/tmp/y$ ssh -i 1.priv bandit17@localhost
Could not create directory '/home/bandit16/.ssh'.
The authenticity of host 'localhost (127.0.0.1)' can't be established.
ECDSA key fingerprint is SHA256:98UL0ZWr85496EtCRkKlo20X3OPnyPSB5tB5RPbhczc.
Are you sure you want to continue connecting (yes/no)? yes
Failed to add the host to the list of known hosts (/home/bandit16/.ssh/known_hosts).
This is a OverTheWire game server. More information on http://www.overthewire.org/wargames
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0644 for '1.priv' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key "1.priv": bad permissions
bandit17@localhost's password:
bandit16@bandit:/tmp/y$ ls -l
total 4
-rw-r--r-- 1 bandit16 root 1675 Mar 28 11:38 1.priv
bandit16@bandit:/tmp/y$ chmod 600 1.priv
bandit16@bandit:/tmp/y$ ls -l
total 4
-rw------- 1 bandit16 root 1675 Mar 28 11:38 1.priv
bandit16@bandit:/tmp/y$ ssh -i 1.priv bandit17@localhost
Could not create directory '/home/bandit16/.ssh'.
The authenticity of host 'localhost (127.0.0.1)' can't be established.
ECDSA key fingerprint is SHA256:98UL0ZWr85496EtCRkKlo20X3OPnyPSB5tB5RPbhczc.
Are you sure you want to continue connecting (yes/no)? yes
Failed to add the host to the list of known hosts (/home/bandit16/.ssh/known_hosts).
This is a OverTheWire game server. More information on http://www.overthewire.org/wargames
L17-18
diff:比較文本的區(qū)別,密碼在new里,所以new在前面,第一條就是密碼
bandit17@bandit:~$ ls
passwords.new passwords.old
bandit17@bandit:~$ diff
.bandit16.password .bashrc passwords.old .ssh/
.bash_logout passwords.new .profile
bandit17@bandit:~$ diff
.bandit16.password .bashrc passwords.old .ssh/
.bash_logout passwords.new .profile
bandit17@bandit:~$ diff passwords.new passwords.old
42c42
< kfBf3eYk5BPBRzwjqutbbfE887SVc5Yd
---
> w0Yfolrc5bwjS4qw5mq1nnQi6mF03bii
bandit17@bandit:~$
L18-19
連接后會(huì)自動(dòng)斷開,將讀取命令跟在連接命令后面
┌──(root?kali)-[~]
└─# ssh bandit18@bandit.labs.overthewire.org -p 2220 cat readme
This is a OverTheWire game server. More information on http://www.overthewire.org/wargames
bandit18@bandit.labs.overthewire.org's password:
IueksS7Ubh8G3DCwVzrTd8rAVOwq3M5x
L19-20
-
euid:有效用戶id,用于系統(tǒng)決定用戶對(duì)系統(tǒng)資源的權(quán)限
-
setuid:只有可以執(zhí)行的二進(jìn)制程序才能設(shè)定setuid權(quán)限,并且命令執(zhí)行者要對(duì)程序有執(zhí)行x權(quán)限,命令執(zhí)行者在執(zhí)行該程序時(shí)獲得所有者的身份,setuid權(quán)限只在執(zhí)行過程中有效
# 設(shè)定setuid的方法 # 4代表SUID,2代表GID,1代表Sticky BIT,7代表全部設(shè)置 chmod 4750 filename or chmod u+s filename # 取消 chmod 0777 filename or chmod u-s filename

bandit19@bandit:~$ ./bandit20-do cat /etc/bandit_pass/bandit20
GbKksEFF4yrVs6il55v6gwY5aVje5f0j
# 在執(zhí)行時(shí)擁有所有者權(quán)限,直接查看
L20-21
-
tmux:會(huì)話和窗口的分離
-
job control:工作管理
-
nc:
# 常用參數(shù)
-l,表示監(jiān)聽模式,監(jiān)聽并接收連接
-p,指定端口
-s,指定發(fā)送數(shù)據(jù)的源 IP 地址
-u,使用udp協(xié)議連接,默認(rèn)為tcp
-v,輸出出錯(cuò)或交互信息
-w,超時(shí)秒數(shù),后面跟數(shù)字
-z,掃描時(shí)不發(fā)送任何數(shù)據(jù)
-k,強(qiáng)制保持連接
測(cè)試TCP/UDP端口
nc -z -v 127.0.0.1 22
nc -z -u -v 127.0.0.1 22
#監(jiān)聽端口
nc -l 888 -v
#連接端口
nc -vz -w 5 127.0.0.2 888

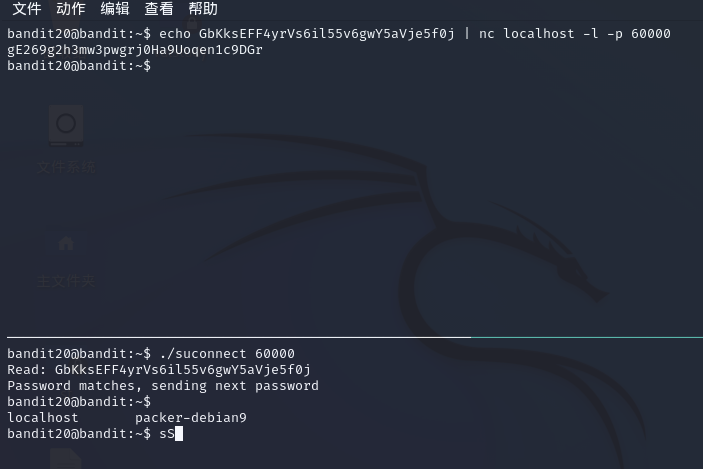
bandit20@bandit:~$ echo GbKksEFF4yrVs6il55v6gwY5aVje5f0j | nc localhost -l -p 50000
gE269g2h3mw3pwgrj0Ha9Uoqen1c9DGr
bandit20@bandit:~$ ./suconnect 50000
Read: GbKksEFF4yrVs6il55v6gwY5aVje5f0j
Password matches, sending next password
L21-22
bandit21@bandit:~$ cd /etc/cron.d
bandit21@bandit:/etc/cron.d$ ls
cronjob_bandit15_root cronjob_bandit22 cronjob_bandit24
cronjob_bandit17_root cronjob_bandit23 cronjob_bandit25_root
bandit21@bandit:/etc/cron.d$ cat cronjob_bandit22
@reboot bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null
* * * * * bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null
bandit21@bandit:/etc/cron.d$ cat /usr/bin/cronjob_bandit22.sh
#!/bin/bash
chmod 644 /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
cat /etc/bandit_pass/bandit22 > /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
bandit21@bandit:/etc/cron.d$ cat /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
Yk7owGAcWjwMVRwrTesJEwB7WVOiILLI
L22-23
- shell腳本:
bandit22@bandit:/etc/cron.d$ cat cronjob_bandit23
@reboot bandit23 /usr/bin/cronjob_bandit23.sh &> /dev/null
* * * * * bandit23 /usr/bin/cronjob_bandit23.sh &> /dev/null
bandit22@bandit:/etc/cron.d$ cat /usr/bin/cronjob_bandit23.sh
#!/bin/bash
myname=$(whoami)
mytarget=$(echo I am user $myname | md5sum | cut -d ' ' -f 1)
echo "Copying passwordfile /etc/bandit_pass/$myname to /tmp/$mytarget"
cat /etc/bandit_pass/$myname > /tmp/$mytarget
cat: /tmp/1d56a3657814db050a3311acd0cbddc2: No such file or directory
bandit22@bandit:/etc/cron.d$ echo I am user bandit23 | md5sum
8ca319486bfbbc3663ea0fbe81326349 -
bandit22@bandit:/etc/cron.d$ cat /tmp/8ca319486bfbbc3663ea0fbe81326349
jc1udXuA1tiHqjIsL8yaapX5XIAI6i0n
L23-24

#先看腳本
bandit23@bandit:~$ cd /etc/cron.d
bandit23@bandit:/etc/cron.d$ ls
cronjob_bandit15_root cronjob_bandit22 cronjob_bandit24
cronjob_bandit17_root cronjob_bandit23 cronjob_bandit25_root
bandit23@bandit:/etc/cron.d$ cat cronjob_bandit24
@reboot bandit24 /usr/bin/cronjob_bandit24.sh &> /dev/null
* * * * * bandit24 /usr/bin/cronjob_bandit24.sh &> /dev/null
bandit23@bandit:/etc/cron.d$ cat /usr/bin/cronjob_bandit24.sh
#!/bin/bash
myname=$(whoami)
cd /var/spool/$myname
echo "Executing and deleting all scripts in /var/spool/$myname:"
for i in * .*;
do
if [ "$i" != "." -a "$i" != ".." ];
then
echo "Handling $i"
owner="$(stat --format "%U" ./$i)"
if [ "${owner}" = "bandit23" ]; then
timeout -s 9 60 ./$i
fi
rm -f ./$i
fi
done
bandit23@bandit:/var/spool/bandit24$ vim pass24
#!/bin/bash
cat /etc/bandit_pass/bandit24 > /tmp/pass24
chmod 777 pass24
bandit23@bandit:/var/spool/bandit24$ cat /tmp/pass24
UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ


 浙公網(wǎng)安備 33010602011771號(hào)
浙公網(wǎng)安備 33010602011771號(hào)