信息收集-工具使用
- Layer
- Sublist3r
- subDomainsBrute
- whatweb
- dirbuster
- dirsearch
- 御劍
- ffuf
- wafw00f
- google hack
- Github信息泄露
Layer子域名挖掘機-子域名挖掘
-
啟動軟件

-
左側輸入域名和要掃描的端口
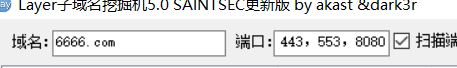
-
要使用自定義字典,將字典命名為dic.txt,放在程序的同目錄下,程序自動加載字典
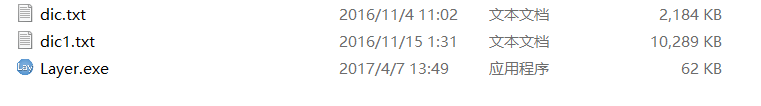
-
按下啟動鍵后等待
-
收集的子域名可以查看解析ip,開發端口,web服務器,狀態。點擊標題欄可以進行排序顯示

-
點擊右鍵可以打開網站,復制域名,ip等,還可導出
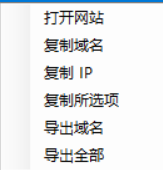
Sublist3r-子域名挖掘
下載鏈接 點我
-
使用python寫的子域名發現工具,使用OSINT技術(公開來源情報),搜索源包括有百度、Yahoo、Google、Bing、Ask、Netcraft等等除此之外使用通過查找SSL證書、DNS、暴力枚舉等這些手段去查找子域名。
-
工具代碼原理 點我
-
查看幫助信息
┌──(root?kali)-[/home/roott/桌面/st] └─# python Sublist3r/sublist3r.py -h usage: sublist3r.py [-h] -d DOMAIN [-b [BRUTEFORCE]] [-p PORTS] [-v [VERBOSE]] [-t THREADS] [-e ENGINES] [-o OUTPUT] [-n] OPTIONS: -h, --help show this help message and exit -d DOMAIN, --domain DOMAIN Domain name to enumerate it's subdomains -b [BRUTEFORCE], --bruteforce [BRUTEFORCE] Enable the subbrute bruteforce module -p PORTS, --ports PORTS Scan the found subdomains against specified tcp ports -v [VERBOSE], --verbose [VERBOSE] Enable Verbosity and display results in realtime -t THREADS, --threads THREADS Number of threads to use for subbrute bruteforce -e ENGINES, --engines ENGINES Specify a comma-separated list of search engines -o OUTPUT, --output OUTPUT Save the results to text file -n, --no-color Output without color Example: python Sublist3r/sublist3r.py -d google.com -d -domain要枚舉子域的域名 -b -bruteforce啟用subbrute bruteforce模塊 -p -ports根據特定的tcp端口掃描找到的子域 -v --verbose啟用詳細模式并實時顯示結果 -t -threads用于subbrute bruteforce的線程數 -e -engines 指定以逗號分隔的搜索引擎列表 -o -output將結果保存到文本文件 -n, --no-color無顏色輸出 -
運行
python Sublist3r/sublist3r.py -d qq.com -b -v -t 100
-
virustotal 報錯
問題不在于發送請求,似乎virustotal完全改變了網址
https://www.virustotal.com/ui/domains/{domain}/subdomains
這個導致了這個錯誤
在源文件中把上面地址,改為以下地址即可
https://www.virustotal.com/gui/domain/{{dommain}}/details
subDomainsBrute-子域名挖掘
下載鏈接 點我
-
用小字典遞歸地發現三級域名,四級域名、五級域名等域名。小字典就包括1萬5千條,大字典多達6萬3千條。默認使用Public DNS,114DNS、百度DNS、阿里DNS等
-
幫助信息
┌──(root?kali)-[/home/roott/桌面/st] └─# python subDomainsBrute/subDomainsBrute.py --h Usage: subDomainsBrute.py [options] target.com Options: --version show program's version number and exit -h, --help show this help message and exit -f FILE File contains new line delimited subs, default is subnames.txt. --full Full scan, NAMES FILE subnames_full.txt will be used to brute -i, --ignore-intranet Ignore domains pointed to private IPs -w, --wildcard Force scan after wildcard test fail -t THREADS, --threads=THREADS Num of scan threads, 200 by default -p PROCESS, --process=PROCESS Num of scan Process, 6 by default -o OUTPUT, --output=OUTPUT Output file name. default is {target}.txt --version 顯示版本號并退出 -h, --help 幫助 -f FILE 指定暴力猜解字典,默認使用subnames.txt. --full 全掃描,使用subnames_full.txt -i, --ignore-intranet 忽略不想采集的IP地址 -t THREADS, --threads=THREADS 掃描線程數,默認200 -p PROCESS, --process=PROCESS 掃描進程數,默認為6 -o OUTPUT, --output=OUTPUT 輸出文件名稱 {target}.txt -
運行
python subDomainsBrute.py -t 20 baidu.com -o baidu.txt
掃描完成后會在py文件同目錄下生成txt文件
whatweb-cms識別
-
WhatWeb 可識別 Web 技術,包括內容管理系統(CMS),博客平臺,統計/分析包,Javascript 庫,服務器和嵌入式設備
-
常規使用
┌──(root?kali)-[/home/roott/桌面/st/subDomainsBrute] └─# whatweb baidu.com http://baidu.com [200 OK] Apache, Country[CHINA][CN], HTTPServer[Apache], IP[220.181.38.251], Meta-Refresh-Redirect[http://www.baidu.com/] http://www.baidu.com/ [200 OK] Cookies[BAIDUID,BDSVRTM,BD_HOME,BIDUPSID,H_PS_PSSID,PSTM], Country[CHINA][CN], Email[index@2.png,pop_tri@1x-f4a02fac82.png,qrcode-hover@2x-f9b106a848.png,qrcode@2x-daf987ad02.png,result@2.png], HTML5, HTTPServer[BWS/1.1], IP[39.156.66.18], JQuery, Meta-Refresh-Redirect[http://www.baidu.com/baidu.html?from=noscript], OpenSearch[/content-search.xml], Script[application/json,text/javascript], Title[百度一下,你就知道], UncommonHeaders[bdpagetype,bdqid,traceid], X-Frame-Options[sameorigin], X-UA-Compatible[IE=Edge,chrome=1,IE=edge] http://www.baidu.com/baidu.html?from=noscript [200 OK] Apache, Cookies[BAIDUID], Country[CHINA][CN], HTML5, HTTPServer[Apache], IP[39.156.66.18], Script, Title[百度一下,你就知道], X-UA-Compatible[IE=Edge] -
批量掃描
將域名寫入文件,用-i參數
┌──(root?kali)-[/home/roott/桌面] └─# whatweb -i 666 http://www.csdn.net [301 Moved Permanently] Country[HONG KONG][HK], HTTPServer[openresty], IP[39.106.226.142], OpenResty, RedirectLocation[https://www.csdn.net/], Title[301 Moved Permanently] http://www.baidu.com [200 OK] Cookies[BAIDUID,BDSVRTM,BD_HOME,BIDUPSID,H_PS_PSSID,PSTM], Country[CHINA][CN], Email[index@2.png,pop_tri@1x-f4a02fac82.png,qrcode-hover@2x-f9b106a848.png,qrcode@2x-daf987ad02.png,result@2.png], HTML5, HTTPServer[BWS/1.1], IP[39.156.66.18], JQuery, Meta-Refresh-Redirect[http://www.baidu.com/baidu.html?from=noscript], OpenSearch[/content-search.xml], Script[application/json,text/javascript], Title[百度一下,你就知道], UncommonHeaders[bdpagetype,bdqid,traceid], X-Frame-Options[sameorigin], X-UA-Compatible[IE=Edge,chrome=1,IE=edge] http://www.baidu.com/baidu.html?from=noscript [200 OK] Apache, Cookies[BAIDUID], Country[CHINA][CN], HTML5, HTTPServer[Apache], IP[39.156.66.18], Script, Title[百度一下,你就知道], X-UA-Compatible[IE=Edge] https://www.csdn.net/ [200 OK] Cookies[csrfToken,dc_session_id,uuid_tt_dd], Country[HONG KONG][HK], Django, Email[u002F2941f33f1bd6418ca4b13d3bbce5dd29@sentry.csdn.net], HTML5, HTTPServer[openresty], IP[39.106.226.142], JQuery[1.12.4], Script[text/javascript], Shopify, Strict-Transport-Security[max-age=31536000], Title[CSDN - 專業開發者社區], UncommonHeaders[x-response-time,x-content-type-options,x-download-options,x-readtime], X-XSS-Protection[1; mode=block] -
詳細回顯掃描
-v參數,
┌──(root?kali)-[/home/roott/桌面] └─# whatweb -v baidu.com WhatWeb report for http://baidu.com Status : 200 OK Title : <None> IP : 220.181.38.251 Country : CHINA, CN Summary : HTTPServer[Apache], Apache, Meta-Refresh-Redirect[http://www.baidu.com/] Detected Plugins: [ Apache ] The Apache HTTP Server Project is an effort to develop and maintain an open-source HTTP server for modern operating systems including UNIX and Windows NT. The goal of this project is to provide a secure, efficient and extensible server that provides HTTP services in sync with the current HTTP standards. Google Dorks: (3) Website : http://httpd.apache.org/ [ HTTPServer ] HTTP server header string. This plugin also attempts to identify the operating system from the server header. String : Apache (from server string) [ Meta-Refresh-Redirect ] Meta refresh tag is a deprecated URL element that can be used to optionally wait x seconds before reloading the current page or loading a new page. More info: https://secure.wikimedia.org/wikipedia/en/wiki/Meta_refresh String : http://www.baidu.com/ HTTP Headers: HTTP/1.1 200 OK Date: Fri, 18 Mar 2022 12:35:27 GMT Server: Apache Last-Modified: Tue, 12 Jan 2010 13:48:00 GMT ETag: "51-47cf7e6ee8400" Accept-Ranges: bytes Content-Length: 81 Cache-Control: max-age=86400 Expires: Sat, 19 Mar 2022 12:35:27 GMT Connection: Close Content-Type: text/html WhatWeb report for http://www.baidu.com/ Status : 200 OK Title : 百度一下,你就知道 IP : 39.156.66.18 Country : CHINA, CN Summary : UncommonHeaders[bdpagetype,bdqid,traceid], HTML5, X-Frame-Options[sameorigin], HTTPServer[BWS/1.1], OpenSearch[/content-search.xml], X-UA-Compatible[IE=Edge,chrome=1,IE=edge], Cookies[BAIDUID,BDSVRTM,BD_HOME,BIDUPSID,H_PS_PSSID,PSTM], Script[application/json,text/javascript], Meta-Refresh-Redirect[http://www.baidu.com/baidu.html?from=noscript], JQuery, Email[index@2.png,pop_tri@1x-f4a02fac82.png,qrcode-hover@2x-f9b106a848.png,qrcode@2x-daf987ad02.png,result@2.png] Detected Plugins: [ Cookies ] Display the names of cookies in the HTTP headers. The values are not returned to save on space. String : BAIDUID String : BIDUPSID String : PSTM String : BAIDUID String : BDSVRTM String : BD_HOME String : H_PS_PSSID [ Email ] Extract email addresses. Find valid email address and syntactically invalid email addresses from mailto: link tags. We match syntactically invalid links containing mailto: to catch anti-spam email addresses, eg. bob at gmail.com. This uses the simplified email regular expression from http://www.regular-expressions.info/email.html for valid email address matching. String : index@2.png,pop_tri@1x-f4a02fac82.png,qrcode-hover@2x-f9b106a848.png,qrcode@2x-daf987ad02.png,result@2.png [ HTML5 ] HTML version 5, detected by the doctype declaration [ HTTPServer ] HTTP server header string. This plugin also attempts to identify the operating system from the server header. String : BWS/1.1 (from server string) [ JQuery ] A fast, concise, JavaScript that simplifies how to traverse HTML documents, handle events, perform animations, and add AJAX. Website : http://jquery.com/ [ Meta-Refresh-Redirect ] Meta refresh tag is a deprecated URL element that can be used to optionally wait x seconds before reloading the current page or loading a new page. More info: https://secure.wikimedia.org/wikipedia/en/wiki/Meta_refresh String : http://www.baidu.com/baidu.html?from=noscript [ OpenSearch ] This plugin identifies open search and extracts the URL. OpenSearch is a collection of simple formats for the sharing of search results. String : /content-search.xml [ Script ] This plugin detects instances of script HTML elements and returns the script language/type. String : application/json,text/javascript [ UncommonHeaders ] Uncommon HTTP server headers. The blacklist includes all the standard headers and many non standard but common ones. Interesting but fairly common headers should have their own plugins, eg. x-powered-by, server and x-aspnet-version. Info about headers can be found at www.http-stats.com String : bdpagetype,bdqid,traceid (from headers) [ X-Frame-Options ] This plugin retrieves the X-Frame-Options value from the HTTP header. - More Info: http://msdn.microsoft.com/en-us/library/cc288472%28VS.85%29. aspx String : sameorigin [ X-UA-Compatible ] This plugin retrieves the X-UA-Compatible value from the HTTP header and meta http-equiv tag. - More Info: http://msdn.microsoft.com/en-us/library/cc817574.aspx String : IE=edge String : IE=Edge,chrome=1 HTTP Headers: HTTP/1.1 200 OK Bdpagetype: 1 Bdqid: 0xeab2f9da0007f83d Cache-Control: private Content-Encoding: gzip Content-Type: text/html;charset=utf-8 Date: Fri, 18 Mar 2022 12:35:29 GMT Expires: Fri, 18 Mar 2022 12:35:29 GMT P3p: CP=" OTI DSP COR IVA OUR IND COM " P3p: CP=" OTI DSP COR IVA OUR IND COM " Server: BWS/1.1 Set-Cookie: BAIDUID=843ACE191CAF5BDF641FA4856CEF748E:FG=1; expires=Thu, 31-Dec-37 23:55:55 GMT; max-age=2147483647; path=/; domain=.baidu.com Set-Cookie: BIDUPSID=843ACE191CAF5BDF641FA4856CEF748E; expires=Thu, 31-Dec-37 23:55:55 GMT; max-age=2147483647; path=/; domain=.baidu.com Set-Cookie: PSTM=1647606929; expires=Thu, 31-Dec-37 23:55:55 GMT; max-age=2147483647; path=/; domain=.baidu.com Set-Cookie: BAIDUID=843ACE191CAF5BDF760373BF08C47CC4:FG=1; max-age=31536000; expires=Sat, 18-Mar-23 12:35:29 GMT; domain=.baidu.com; path=/; version=1; comment=bd Set-Cookie: BDSVRTM=10; path=/ Set-Cookie: BD_HOME=1; path=/ Set-Cookie: H_PS_PSSID=36067_35106_31253_36021_34812_35911_34584_36120_36074_36109_35984_35320_26350_36101_36062; path=/; domain=.baidu.com Traceid: 1647606929262280909816911854265428342845 X-Frame-Options: sameorigin X-Ua-Compatible: IE=Edge,chrome=1 Connection: close Transfer-Encoding: chunked WhatWeb report for http://www.baidu.com/baidu.html?from=noscript Status : 200 OK Title : 百度一下,你就知道 IP : 39.156.66.18 Country : CHINA, CN Summary : HTML5, HTTPServer[Apache], Apache, X-UA-Compatible[IE=Edge], Cookies[BAIDUID], Script Detected Plugins: [ Apache ] The Apache HTTP Server Project is an effort to develop and maintain an open-source HTTP server for modern operating systems including UNIX and Windows NT. The goal of this project is to provide a secure, efficient and extensible server that provides HTTP services in sync with the current HTTP standards. Google Dorks: (3) Website : http://httpd.apache.org/ [ Cookies ] Display the names of cookies in the HTTP headers. The values are not returned to save on space. String : BAIDUID [ HTML5 ] HTML version 5, detected by the doctype declaration [ HTTPServer ] HTTP server header string. This plugin also attempts to identify the operating system from the server header. String : Apache (from server string) [ Script ] This plugin detects instances of script HTML elements and returns the script language/type. [ X-UA-Compatible ] This plugin retrieves the X-UA-Compatible value from the HTTP header and meta http-equiv tag. - More Info: http://msdn.microsoft.com/en-us/library/cc817574.aspx String : IE=Edge HTTP Headers: HTTP/1.1 200 OK Accept-Ranges: bytes Cache-Control: max-age=86400 Content-Encoding: gzip Content-Length: 1131 Content-Type: text/html Date: Fri, 18 Mar 2022 12:35:35 GMT Etag: "b83-59bafefa98680" Expires: Sat, 19 Mar 2022 12:35:35 GMT Last-Modified: Thu, 09 Jan 2020 07:27:06 GMT P3p: CP=" OTI DSP COR IVA OUR IND COM " Server: Apache Set-Cookie: BAIDUID=931BB16E756618D76A155B2EB8A4263B:FG=1; expires=Sat, 18-Mar-23 12:35:35 GMT; max-age=31536000; path=/; domain=.baidu.com; version=1 Vary: Accept-Encoding,User-Agent Connection: close -
強度掃描控制
--aggression,-a掃描等級控制,1,3,4設置不同的級別,默認為1,
┌──(root?kali)-[/home/roott/桌面] └─# whatweb -a 3 www.baidu.com http://www.baidu.com [200 OK] Cookies[BAIDUID,BDSVRTM,BD_HOME,BIDUPSID,H_PS_PSSID,PSTM], Country[CHINA][CN], Email[index@2.png,pop_tri@1x-f4a02fac82.png,qrcode-hover@2x-f9b106a848.png,qrcode@2x-daf987ad02.png,result@2.png], HTML5, HTTPServer[BWS/1.1], IP[39.156.66.18], JQuery, Meta-Refresh-Redirect[http://www.baidu.com/baidu.html?from=noscript], OpenSearch[/content-search.xml], Script[application/json,text/javascript], Title[百度一下,你就知道], UncommonHeaders[bdpagetype,bdqid,traceid], X-Frame-Options[sameorigin], X-UA-Compatible[IE=Edge,chrome=1,IE=edge] http://www.baidu.com/baidu.html?from=noscript [200 OK] Apache, Cookies[BAIDUID], Country[CHINA][CN], HTML5, HTTPServer[Apache], IP[39.156.66.18], Script, Title[百度一下,你就知道], X-UA-Compatible[IE=Edge] -
快速掃描內網主機
└─# whatweb --no-errors -t 255 192.168.1.0/24 http://192.168.1.1 [302 Found] Boa-WebServer[0.94.13], Country[RESERVED][ZZ], HTTPServer[Boa/0.94.13], IP[192.168.1.1], RedirectLocation[/cgi-bin/index2.asp], Title[302 Moved Temporarily], X-Frame-Options[SAMEORIGIN] http://192.168.1.1/cgi-bin/index2.asp [200 OK] Country[RESERVED][ZZ], IP[192.168.1.1], JQuery[1.8.3], MetaGenerator[Microsoft FrontPage 5.0], PasswordField[Password], Script[javascript,text/JavaScript], Title[Login], X-Frame-Options[SAMEORIGIN] -
掃描結果導出
在目錄下出現baidu.xml文件,還可導出其他格式
┌──(root?kali)-[/home/roott/桌面] └─# whatweb www.baidu.com --log-xml=baidu.xml --log-brief=FILE 簡單的記錄,每個網站只記錄一條返回信息 --log-verbose=FILE 詳細輸出 --log-xml=FILE 返回xml格式的日志 --log-json=FILE 以json格式記錄日志 --log-json-verbose=FILE 記錄詳細的json日志 --log-magictree=FILE xml的樹形結構 --log-object=FILE ruby對象格式 --log-mongo-database mongo數據庫格式
dirbuster-子目錄
-
配置文件 /usr/share/dirbuster
-
標注
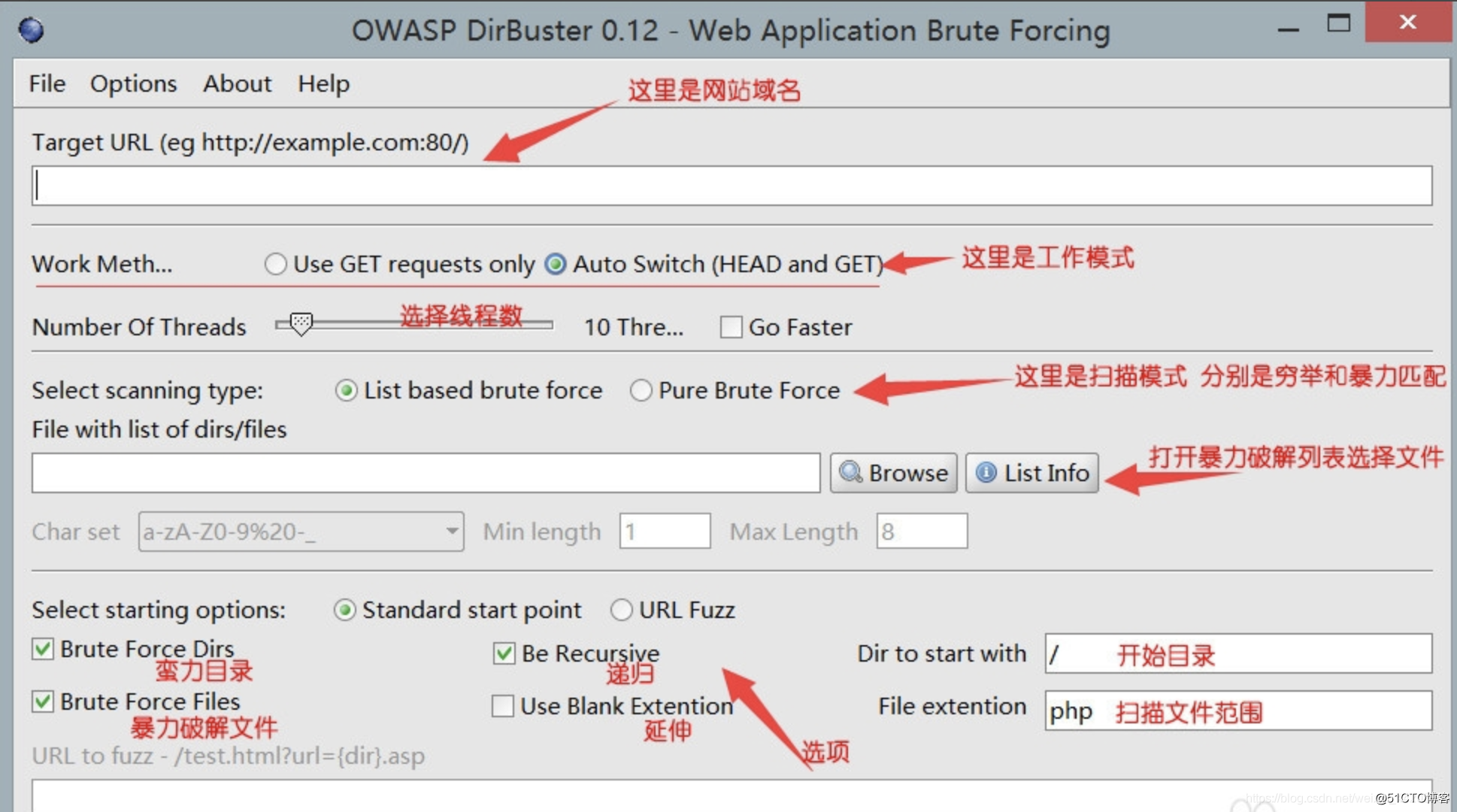
-
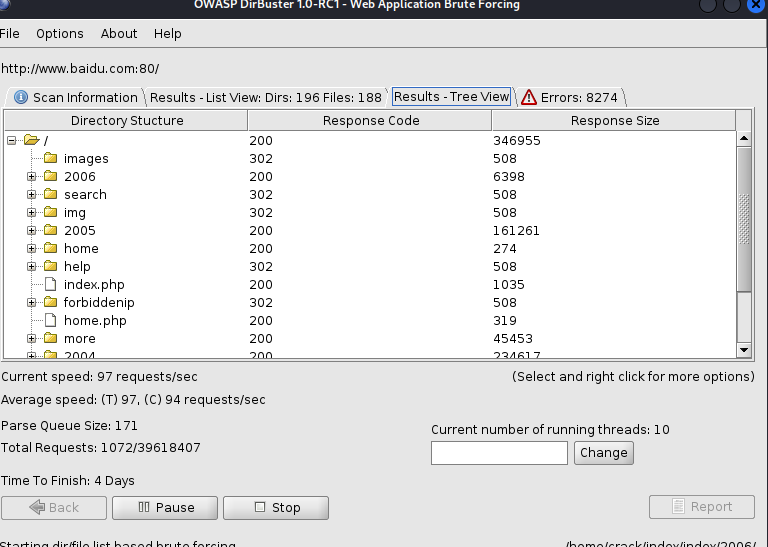
查看掃描出的文件
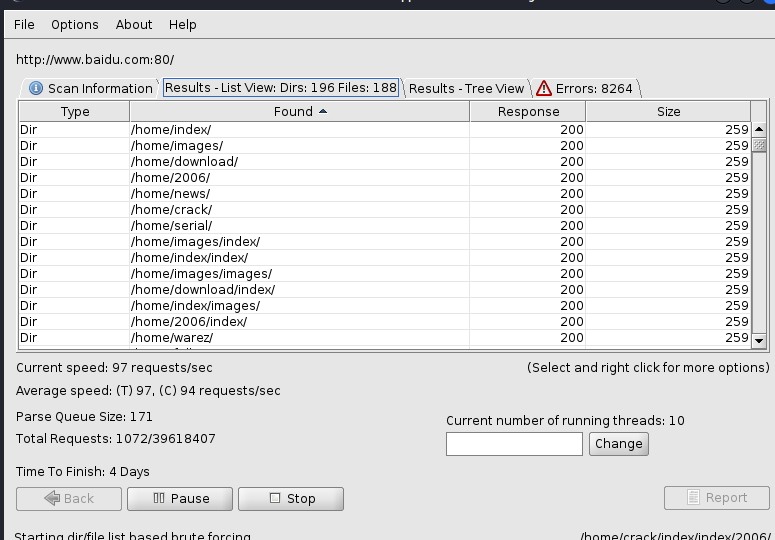
- 查看樹狀
- 掃描完成后可以導出報告
dirsearch-子目錄
-
配置文件
/etc/dirsearch/default.conf
-
常用參數
- -u 指定網址
- -e 指定網站語言
- -w 指定字典
- -t 線程
- -r 遞歸目錄(跑出目錄后,繼續跑目錄下面的目錄)
- --random-agent 隨機一個User-agent 對每一個請求
- -i,包含狀態,逗號分割 200,300
- -x,排除狀態 ,逗號分割 301,500-599
- -h
-
實踐
使用--random-agent,隨機改變User-agent
1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/63.0.3239.132 Safari/537.36 OPR/50.0.2762.58 2 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/63.0.3239.132 Safari/537.36 3 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_13_1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/63.0.3239.84 Safari/537.36不使用User-agent
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
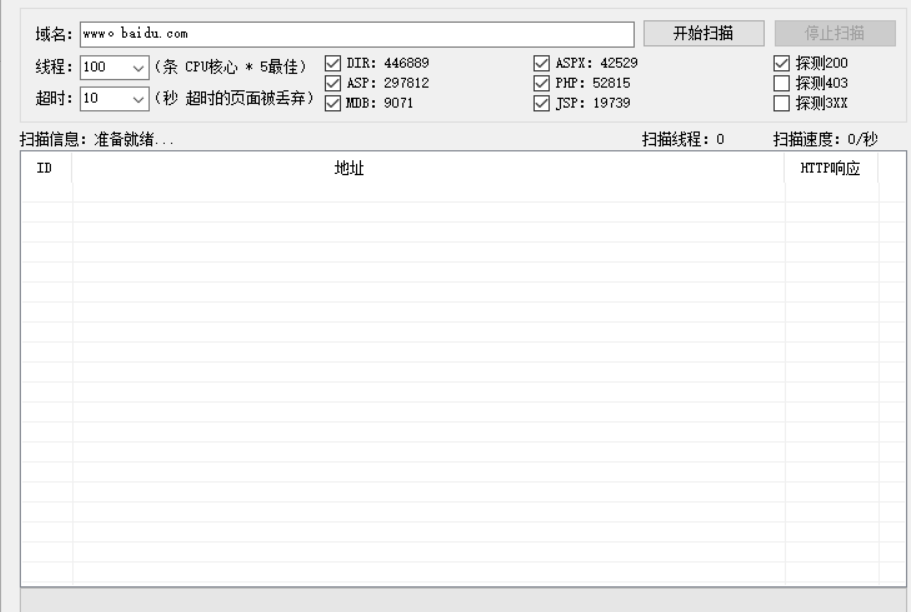
御劍
可以選擇,線程,超時,使用的字典,顯示的狀態碼等
字典放在同目錄下的配置文件
ffuf(太過強大,暫未掌握)
- Go 編寫的模糊測試器
? -u url地址/后面家FUZZ
? -w 設置字典,指定多個字典用 , 分隔
? -c 將響應狀態碼用顏色區分,windows下無法實現該效果。
? -t 線程率,默認40
? -p 請求延時: 0.1、0.2s
? -ac 自動校準fuzz結果
? -H Header頭,格式為 “Name: Value”
? -X HTTP method to use
? -d POST data
? -r 跟隨重定向
? -recursion num 遞歸掃描
? -x 設置代理 http 或 socks5://127.0.0.1:8080
? -s 不打印附加信息,簡潔輸出
? -e 設置腳本語言 -e .asp,.php,.html,.txt等
? -o 輸出文本
? -of 輸出格式文件,支持html、json、md、csv、或者all
-
簡單的網站目錄掃描
ffuf -u http://site.com/FUZZ -w ./wordlist.txt FUZZ指定爆破位置 -
需要遞歸的目錄掃描
ffuf -u http://site.com/FUZZ -w ./wordlist.txt -recursion -recursion-depth 1 -recursion 指定進行遞歸掃描。默認不遞歸 -recursion-depth 指定遞歸的深度。默認是1 -
掃描敏感文件
ffuf -u http://site.com/FUZZ -w ./wordlist.txt -e .bak -e 掃描指定后綴的文件 -
多個字典掃描
ffuf -u http://FUZZDOMAIN/FUZZDIR -w ./domain.txt:FUZZDOMAIN,./wordlist.txt:FUZZDIR 執行多個字典時,采用順序模式 -
文件中獲取
ffuf -request /request.txt -w ./wordlist.txt -request指定需要讀取的文件 -
fuzz子域名
ffuf -w hosts.txt -u https://example.org/ -H "Host: FUZZ" -mc 200
wafw00f
- 幫助信息
Usage: wafw00f url1 [url2 [url3 ... ]]
example: wafw00f http://www.victim.org/
Options:
-h, --help show this help message and exit
-v, --verbose Enable verbosity, multiple -v options increase verbosity
# 啟用詳細程度,多個 -v 選項會增加詳細程度
-a, --findall Find all WAFs which match the signatures, do not stop testing on the first one
# 查找與簽名匹配的所有 WAF,不要停止測試第一個
-r, --noredirect Do not follow redirections given by 3xx responses
# 不要遵循 3xx 響應給出的重定向
-t TEST, --test=TEST Test for one specific WAF
# 測試一種特定的 WAF
-o OUTPUT, --output=OUTPUT
Write output to csv, json or text file depending on file extension. For stdout, specify - as filename.
# 根據文件擴展名將輸出寫入 csv、json 或文本文件。 對于標準輸出,指定 - 作為文件名。
-i INPUT, --input-file=INPUT
Read targets from a file. Input format can be csv,json or text. For csv and json, a `url` column name or element is required.
# 從文件中讀取目標。 輸入格式可以是 csv、json 或文本。 對于 csv 和 json,需要一個 `url` 列名或元素
-l, --list List all WAFs that WAFW00F is able to detect
#列出 WAFW00F 能夠檢測到的所有 WAF
-p PROXY, --proxy=PROXY
Use an HTTP proxy to perform requests, examples:
http://hostname:8080, socks5://hostname:1080,
http://user:pass@hostname:8080
# http代理
-V, --version Print out the current version of WafW00f and exit.
# 打印出當前版本的 WafW00f 并退出
-H HEADERS, --headers=HEADERS
Pass custom headers via a text file to overwrite the
default header set.
# 通過文本文件傳遞自定義標題以覆蓋默認標題集。
-
原理
-
發送正常的http請求并分析響應;這樣來確定WAF。
-
如果失敗了,它將發送多個(可能是惡意的)http請求,并使用簡單的邏輯來推斷出它是哪個WAF。
-
如果還是不成功,它將分析先前返回的響應,并使用另一種簡單算法來猜測WAF或安全方案是否正在主動響應我們的攻擊
-
-
掃描單個
┌──(root?kali)-[/home/roott/桌面/st] └─# wafw00f http://www.qq.com -
掃描多個
┌──(root?kali)-[/home/roott/桌面/st] └─# wafw00f http://www.qq.com http://www.baidu.com
google hack
-
? 用法
- Site:特定域名下進行搜索。
- Domain:查詢自身網站的外部鏈接。
- Inurl:指令用于搜索查詢詞出現在url中的頁面。
- Intitle:進行搜索含關鍵字的標題。
- Info:查找指定站點的一些基本信息。
- Filetype:只搜索某些特定類型的文件格式。
- Link:返回所有和xxxxxxx做了鏈接的URL
- Index:返回的網頁中在正文部分包含關鍵詞。
- Define:搜索某個詞語的定義
- And:利用and表示前后兩個關鍵詞是“與”的邏輯關系
- cache:緩存里的內容
github信息泄露
in:name test #倉庫標題搜索含有關鍵字test
in:description test #倉庫描述搜索含有關鍵字
in:readme test #Readme文件搜素含有關鍵字
stars:>3000 test #stars數量大于3000的搜索關鍵字
stars:1000..3000 test #stars數量大于1000小于3000的搜索關鍵字
forks:>1000 test #forks數量大于1000的搜索關鍵字
forks:1000..3000 test #forks數量大于1000小于3000的搜索關鍵字
size:>=5000 test #指定倉庫大于5000k(5M)的搜索關鍵字
pushed:>2019-02-12 test #發布時間大于2019-02-12的搜索關鍵字
created:>2019-02-12 test #創建時間大于2019-02-12的搜索關鍵字
user:test #用戶名搜素
license:apache-2.0 test #明確倉庫的 LICENSE 搜索關鍵字
language:java test #在java語言的代碼中搜索關鍵字
user:test in:name test #組合搜索,用戶名test的標題含有test的
-
使用github進行郵件配置信息收集
site:Github.com smtp site:Github.com smtp @qq.com site:Github.com smtp @126.com site:Github.com smtp @163.com site:Github.com smtp @sina.com.cn site:Github.com smtp password site:Github.com String password smtp 我們也可以鎖定域名搜索結合廠商域名 靈活運用例如搜百度的 site:Github.com smtp @baidu.com -
github數據庫收集
site:Github.com sa password site:Github.com root password site:Github.com User ID=’sa’;Password site:Github.com inurl:sql -
svn信息收集
site:Github.com svn site:Github.com svn username site:Github.com svn password site:Github.com svn username password -
綜合信息收集
site:Github.com password site:Github.com ftp ftppassword site:Github.com 密碼 site:Github.com 內部
masscan-端口掃描
-
TCP 端口進行掃描,使用 SYN 掃描的方式,不建立一個完全的 TCP 連接,而是首先發送一個 SYN 數據包到目標端口,然后等待接收。如果接收到 SYN-ACK 包,則說明該端口是開放的,此時發送一個 RST 結束建立過程即可;否則,若目標返回 RST,則端口不開放
-
幫助
1、單獨的IPv4地址 2、類似"10.0.0.1-10.0.0.233"的范圍地址 3、CIDR地址 類似于"0.0.0.0/0",多個目標可以用都好隔開 -p <ports,--ports <ports>> 指定端口進行掃描 --banners 獲取banner信息,支持少量的協議 --rate <packets-per-second> 指定發包的速率 -c <filename>, --conf <filename> 讀取配置文件進行掃描 --echo 將當前的配置重定向到一個配置文件中 -e <ifname> , --adapter <ifname> 指定用來發包的網卡接口名稱 --adapter-ip <ip-address> 指定發包的IP地址 --adapter-port <port> 指定發包的源端口 --adapter-mac <mac-address> 指定發包的源MAC地址 --router-mac <mac address> 指定網關的MAC地址 --exclude <ip/range> IP地址范圍黑名單,防止masscan掃描 --excludefile <filename> 指定IP地址范圍黑名單文件 --includefile,-iL <filename> 讀取一個范圍列表進行掃描 --ping 掃描應該包含ICMP回應請求 --append-output 以附加的形式輸出到文件 --iflist 列出可用的網絡接口,然后退出 --retries 發送重試的次數,以1秒為間隔 --nmap 打印與nmap兼容的相關信息 --http-user-agent <user-agent> 設置user-agent字段的值 --show [open,close] 告訴要顯示的端口狀態,默認是顯示開放端口 --noshow [open,close] 禁用端口狀態顯示 --pcap <filename> 將接收到的數據包以libpcap格式存儲 --regress 運行回歸測試,測試掃描器是否正常運行 --ttl <num> 指定傳出數據包的TTL值,默認為255 --wait <seconds> 指定發送完包之后的等待時間,默認為10秒 --offline 沒有實際的發包,主要用來測試開銷 -sL 不執行掃描,主要是生成一個隨機地址列表 --readscan <binary-files> 讀取從-oB生成的二進制文件,可以轉化為XML或者JSON格式. --connection-timeout <secs> 抓取banners時指定保持TCP連接的最大秒數,默認是30秒。 -
簡單使用
-
單端口掃描
masscan 192.168.1.0/24 -p443 -
多端口掃描
masscan 10.11.0.0/16 -p80,443 -
掃描一系列端口
masscan 10.11.0.0/16 -p22-25 -
快速掃描
默認為一秒100個包,-rate
masscan 10.11.0.0/16 --top-ports 100 -rate 100000 -
排除目標
masscan 10.11.0.0/16 --top-ports 100 --excluedefile exclude.txt -
保存掃描結果
masscan 10.11.0.0/16 --top-ports 100 > result.txt -
支持的輸出格式
-oX filename : 將掃描結果保存到xml格式的文件中 -oG filename : 將掃描結果保存到grepable格式的文件中 -oJ filename : 將掃描結果保存到json格式的文件中 -
掃描十大端口
masscan 10.11.0.0/16 -top-ten -rate 100000


 浙公網安備 33010602011771號
浙公網安備 33010602011771號