KMS的幾個開源實現匯總
搜索關鍵詞
open source key management server
“key management server”
KMIP
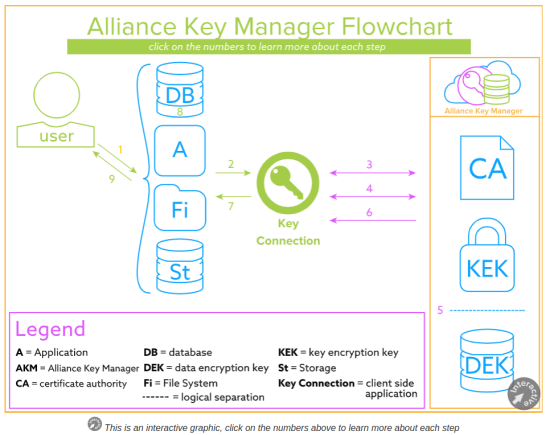
集中密鑰工作流程
https://www.townsendsecurity.com/products/centralized-encryption-key-management
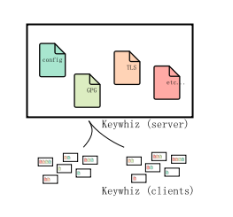
Keywhiz
https://square.github.io/keywhiz/
https://gitee.com/mirrors/keywhiz/tree/master
Keywhiz makes managing secrets easier and more secure. Keywhiz servers in a cluster centrally store secrets encrypted in a database. Clients use mutually authenticated TLS (mTLS) to retrieve secrets they have access to. Authenticated users administer Keywhiz via CLI. To enable workflows, Keywhiz has automation APIs over mTLS.
Keywhiz 是管理和分配隱私信息的系統,適用于面向服務的架構(SOA)。
每個組織的服務或者系統都要求有密碼或者其他的隱私信息:
TLS 認證或者密鑰
GPG 密鑰
API tokens
數據庫證書
通常是把隱私信息放到配置文件,代碼的后面,還有就是復制文件放到服務器以外的地方。前者容易泄漏,后者很難追蹤。
Keywhiz 提供了一個簡單而又安全的方式來管理這些隱私信息。Keywhiz 服務器在集中的集群中存儲這些信息,數據庫加密后存儲。客戶端使用TLS(mTLS) 來訪問那些信息。認證用戶通過 CLI 或者 web app UI 管理 Keywhiz。為了使用工作流,Keywhiz 基于 mTLS自動化 APIs,支持簡單的隱私信息生成插件。
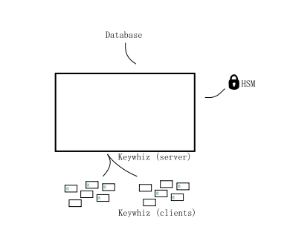
Vault
https://learn.hashicorp.com/vault
HashiCorp Vault作為集中化的私密信息管理工具,具有以下特點:
存儲私密信息。 不僅可以存放現有的私密信息,還可以動態生成用于管理第三方資源的私密信息。所有存放的數據都是加密的,任何動態生成的私密信息都有租期,并且到期會自動回收。
滾動更新密鑰。用戶可以隨時更新存放的私密信息。Vault提供了加密即服務(encryption-as-a-service)的功能,可以隨時將密鑰滾動到新的密鑰版本,同時保留對使用過去密鑰版本加密的值進行解密的能力。 對于動態生成的秘密,可配置的最大租賃壽命確保密鑰滾動易于實施。
審計日志。 保管庫存儲所有經過身份驗證的客戶端交互的詳細審核日志:身份驗證,令牌創建,私密信息訪問,私密信息撤銷等。 可以將審核日志發送到多個后端以確保冗余副本。
另外,HaishiCorp Vault提供了多種方式來管理私密信息。用戶可以通過命令行、HTTP API等集成到應用中來獲取私密信息。
作者:ThoughtWorks
鏈接:https://www.jianshu.com/p/f34bf6ee3ac3
來源:簡書
著作權歸作者所有。商業轉載請聯系作者獲得授權,非商業轉載請注明出處。
https://zhuanlan.zhihu.com/p/69971600 Hashicorp vault 簡明配置教程
http://jiagoushi.pro/adopting-hashicorp-vault-day-zero
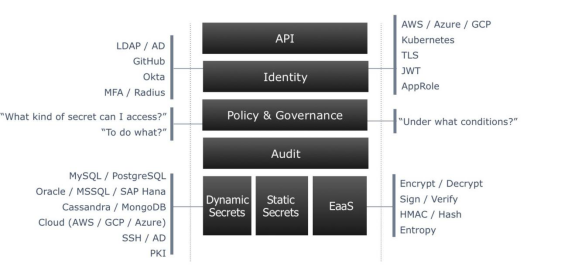
KLMS KMIP
KLMS over KMIP is good and easy to use solution for key management. This is an open source solution written in Java. See the below link for reference. http://www.ibm.com/developerworks/library/se-kmip4j/
The package named stubInterface will contains all the api required to use KLMS over KMIP.
KLMS: Key Lifecycle Management Systems
KMIP: Key Management Interoperability Protocol

PyKMIP
https://github.com/OpenKMIP 開源實現
PyKMIP is a Python implementation of the Key Management Interoperability Protocol (KMIP), an OASIS communication standard for the management of objects stored and maintained by key management systems. KMIP defines how key management operations and operation data should be encoded and communicated between client and server applications. Supported operations include the full CRUD key management lifecycle, including operations for managing object metadata and for conducting cryptographic operations. Supported object types include:
symmetric/asymmetric encryption keys
passwords/passphrases
certificates
opaque data blobs, and more
https://hub.docker.com/r/jzendle/kmip-server
客戶端的幾個命令例子
.. py:method:: create(algorithm, length, operation_policy_name=None, name=None, cryptographic_usage_mask=None)
Create a symmetric key on a KMIP appliance.
.. py:method:: create_key_pair(algorithm, length, operation_policy_name=None, public_name=None, public_usage_mask=None, private_name=None, private_usage_mask=None)
Create an asymmetric key pair on a KMIP appliance.
.. py:method:: decrypt(data, uid=None, cryptographic_parameters=None, iv_counter_nonce=None)
Decrypt data using the specified decryption key and parameters.
.. py:method:: delete_attribute(unique_identifier=None, **kwargs)
Delete an attribute from a managed object.
.. py:method:: encrypt(data, uid=None, cryptographic_parameters=None, iv_counter_nonce=None)
Encrypt data using the specified encryption key and parameters.
.. py:method:: get(uid=None, key_wrapping_specification=None)
Get a managed object from a KMIP appliance.
.. py:method:: get_attributes(uid=None, attribute_names=None)
Get the attributes associated with a managed object.
keytransparency
https://gitee.com/mirrors_google/keytransparency/blob/master/docs/design.md
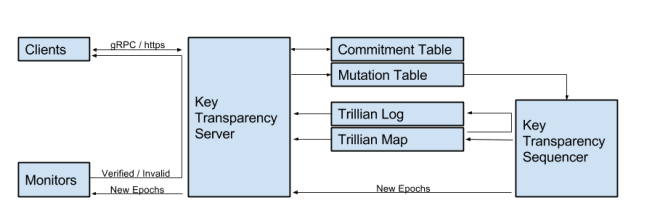
Scenarios
Key Transparency ensures, with mathematical certainty, that account owners can see all the public keys that have been used to authenticate their account or send them messages.
This assured-system architecture is useful in a variety of scenarios from end-to-end encryption to enterprise account management. Any scenario that involves authenticating users with public keys (eg. U2F) can significantly benefit from Key Transparency.
|
Scenario |
Description |
|
Encrypted Messaging |
Key Transparency is ideal for user friendly end-to-end encrypted messaging. By making key management analogous to device management, users do not have to learn any new concepts, and no additional UI beyond device management is needed. Key management fits seamlessly into existing account life-cycle flows, and users are protected without requiring them to take additional actions. |
|
Encrypted Storage |
Key Transparency can also be used to securely rotate the keys used for encrypted storage systems such as upspin.io |
|
PGP Encrypted Email |
Key Transparency was initially built to solve the problem of public key lookup for PGP email encryption. KT has the potential to make PGP significantly more usable than the existing web-of-trust model. |
|
Insider Risk |
Key Transparency removes the ability of privileged users to modify other user accounts without detection. This protects the privileged user from manipulation and ensures system safety even if the privileged user's account is compromised. |
|
Post Compromise Security Audit |
By relying on mathematics, Key Transparency significantly reduces the trusted computing base (TCB) of an authentication system. This makes reasoning about the security properties of an enterprise under attack much easier. The system administrator can have certainty that the authentication records for all accounts are intact, and that users will be able to quickly correct any account compromise. |
|
Cloud Adoption |
By employing a zero-trust architecture, Key Transparency provides efficient evidence to relying parties that the authentication system is operating correctly on an ongoing basis. This can increase cloud product adoption by removing one system from the list of systems that are difficult for customers to audit and control. |
使用場景例子upspin.io
To illustrate the relationship between these components, here is the sequence of requests a client exchanges with the servers to read the file augie@upspin.io/Images/Augie/large.jpg:
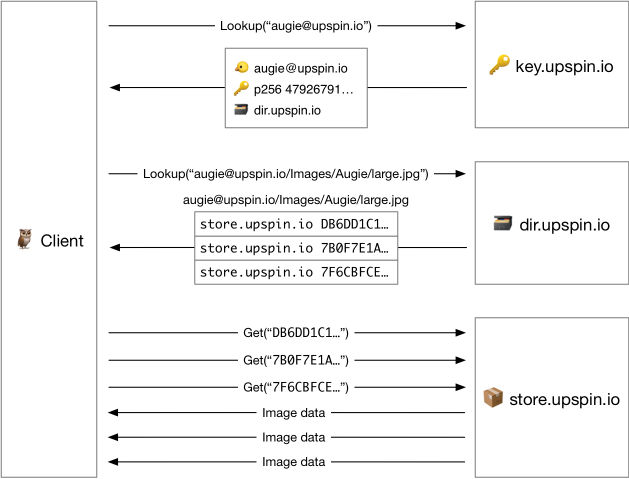
The client asks the key server for the record describing the owner of the file, which is the user name at the beginning of the file name (augie@upspin.io). The key server’s response contains the name of the directory server holding that user’s tree (dir.upspin.io) and Augie’s public key.
The client asks the directory server for the directory entry describing the file. The response contains a list of block references, which include the name of the store server (store.upspin.io).
The client can then ask the store server for each of the blocks, pipelining the requests for efficiency.
The client decrypts the blocks (using Augie’s public key) and concatenates them to assemble the file.
https://upspin.io/doc/security.md
As far as Upspin is concerned, a user is an email address, authenticated by an elliptic curve key pair used for signing and encrypting. We anticipate that the user will rotate keys over time, but we also assume that they will retain all old key pairs for use in decrypting old content, and will accept losing that access to that content if they lose all copies of their keys.
密鑰輪換
|
upspin cmd operation |
public,secret.upspinkey |
secret2.upspinkey |
keyserver |
signatures |
wraps |
|
initial key |
k1 |
- |
k1 |
k1, - |
k1 |
|
new key |
k2 |
k1 |
k1 |
k1, - |
k1 |
|
countersign |
k2 |
k1 |
k1 |
k2, k1 |
k1 |
|
rotate |
k2 |
k1 |
k2 |
k2, k1 |
k1 |
|
share -fix |
k2 |
k1 |
k2 |
k2, k1 |
k2 |
K8S的kms
https://kubernetes.io/zh/docs/tasks/administer-cluster/kms-provider/
KMS 加密驅動使用封套加密模型來加密 etcd 中的數據。 數據使用數據加密密鑰(DEK)加密;每次加密都生成一個新的 DEK。 這些 DEK 經一個密鑰加密密鑰(KEK)加密后在一個遠端的 KMS 中存儲和管理。 KMS 驅動使用 gRPC 與一個特定的 KMS 插件通信。這個 KMS 插件作為一個 gRPC 服務器被部署在 Kubernetes 主服務器的同一個主機上,負責與遠端 KMS 的通信。
Hadoop KMS / Ranger KMS
Ranger KMS is based on Hadoop KMS developed by the Apache community. The main difference between Hadoop KMS and Ranger KMS is that the Hadoop KMS stores keys in a file-based Java keystore where as Ranger allows you to store keys in a secure database. The centralized administration of the Ranger KMS is provided through the Ranger admin portal.
There are three main functions within the Ranger KMS: Key management, Access control policies for key management, and audit. To know how to set up and configure Ranger KMS, visit our knowledge center.
https://www.pianshen.com/article/2354126360/
Ranger KMS加密HDFS的配置和權限設置


